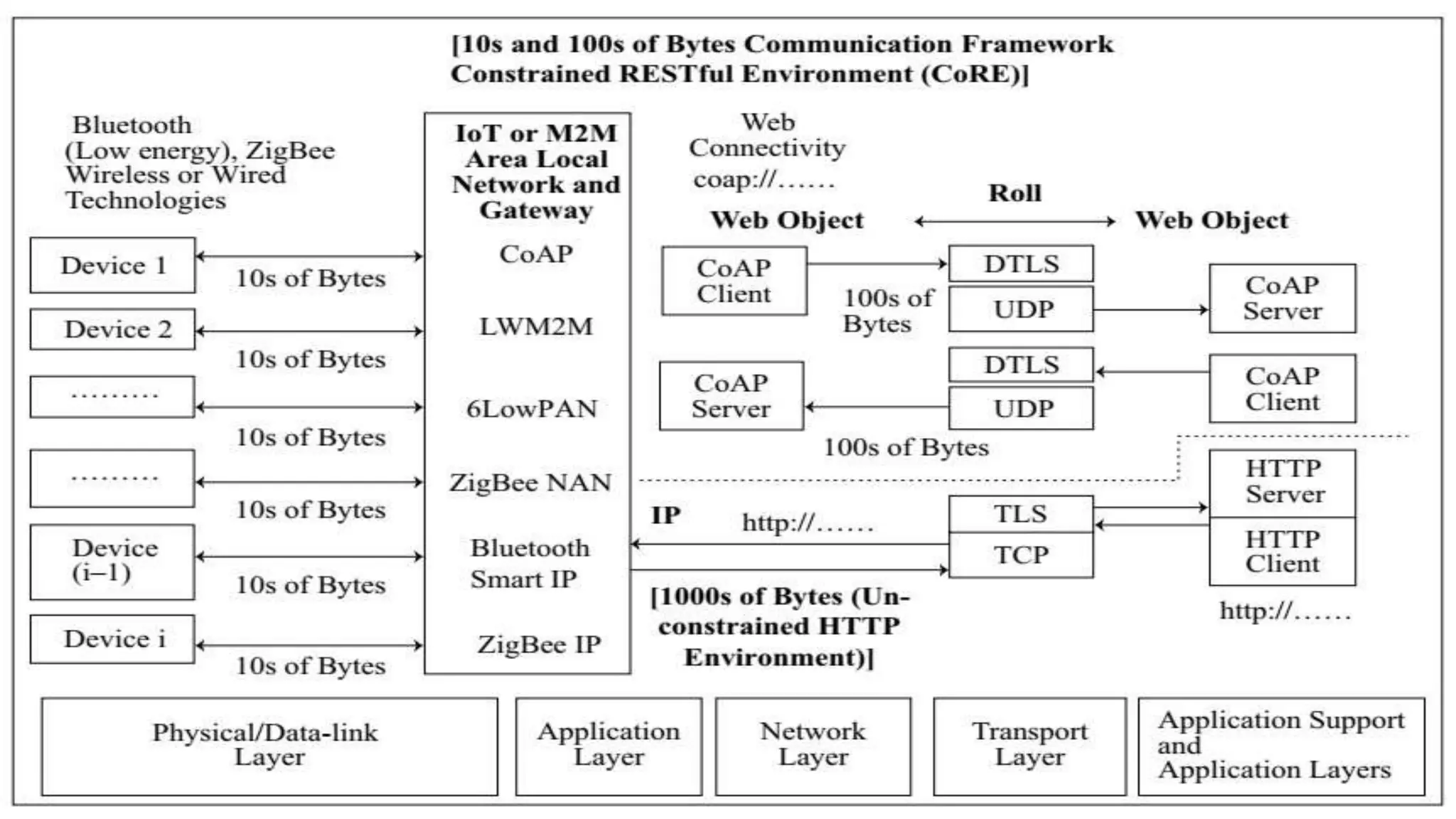
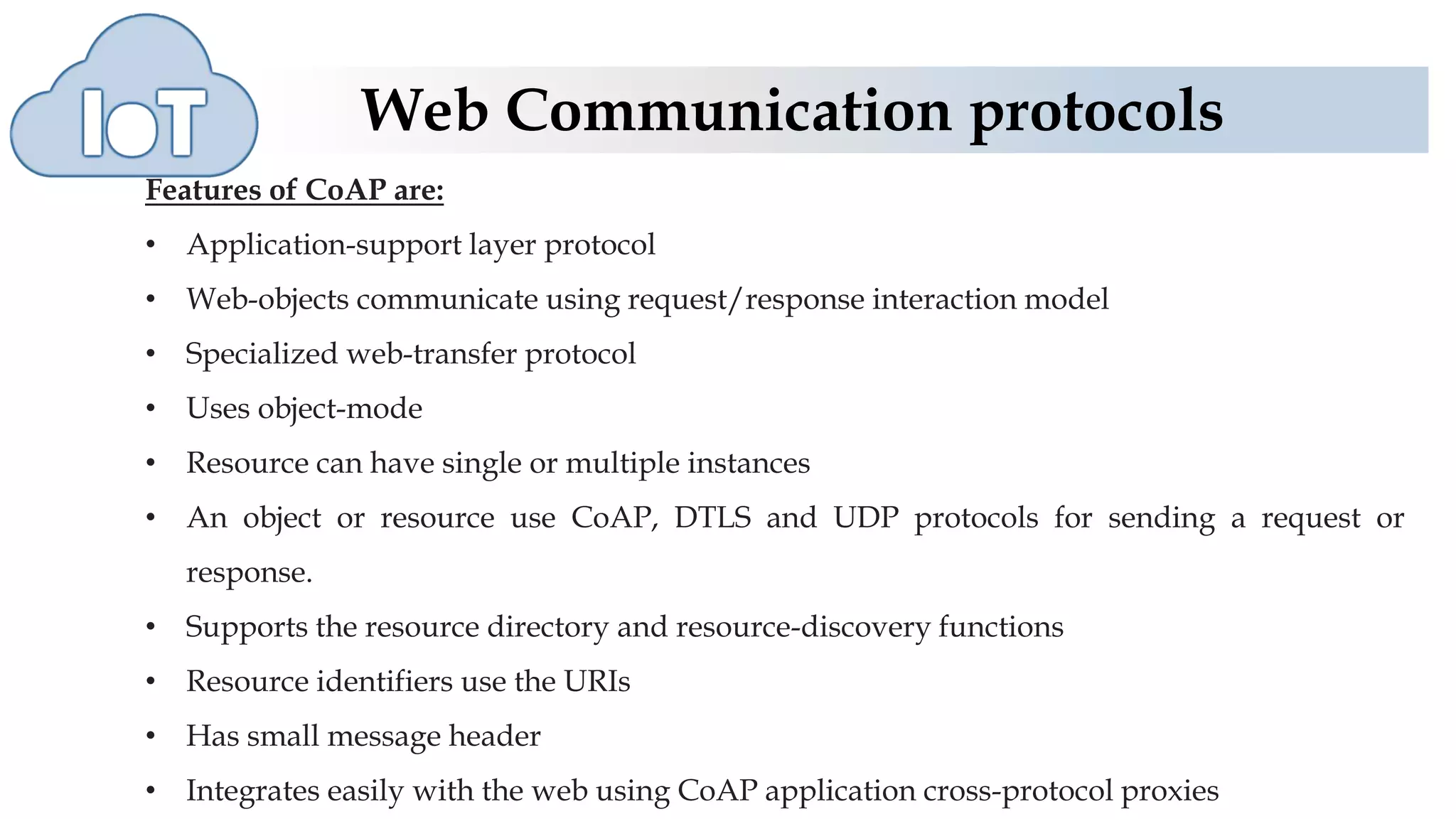
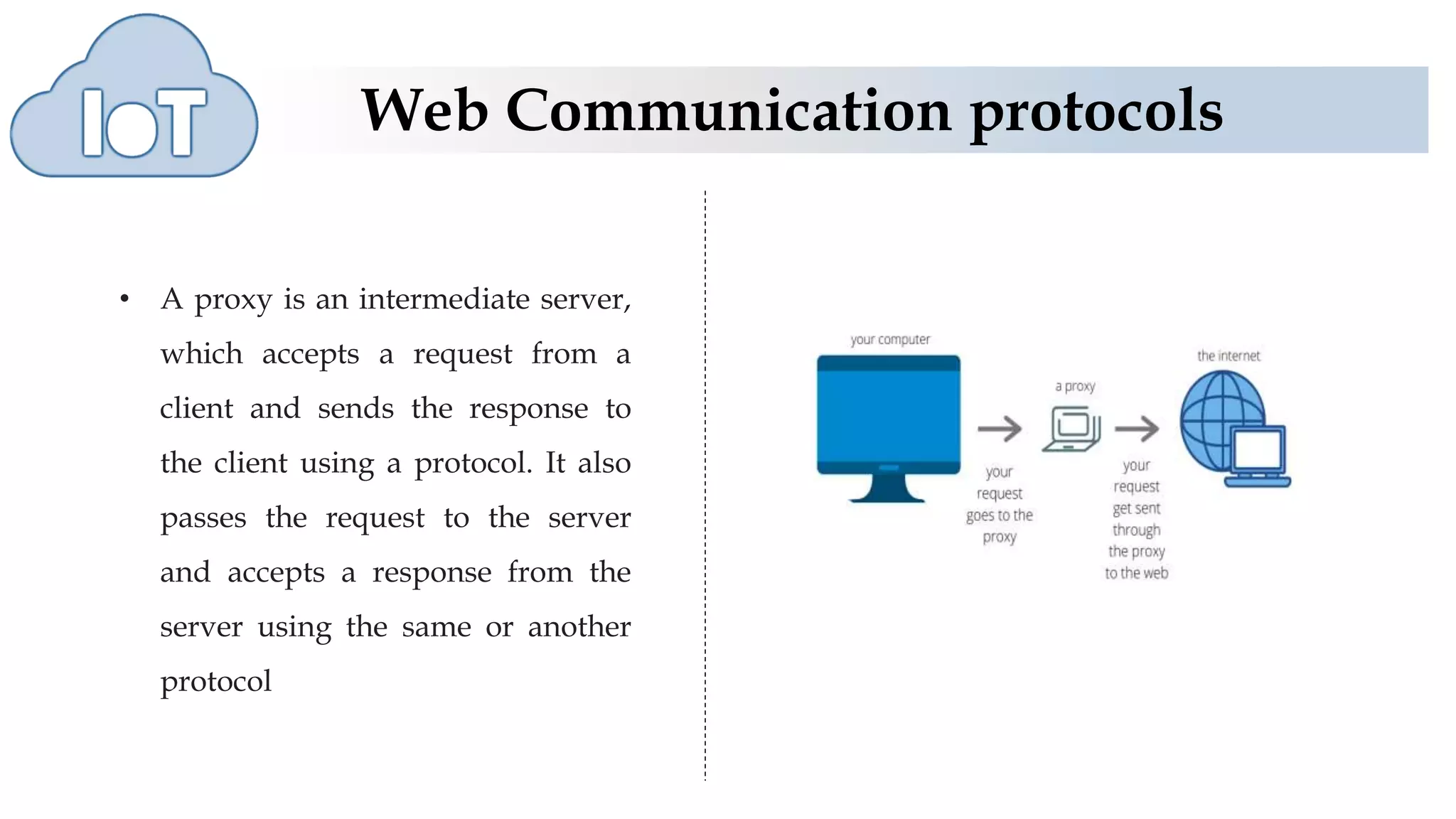
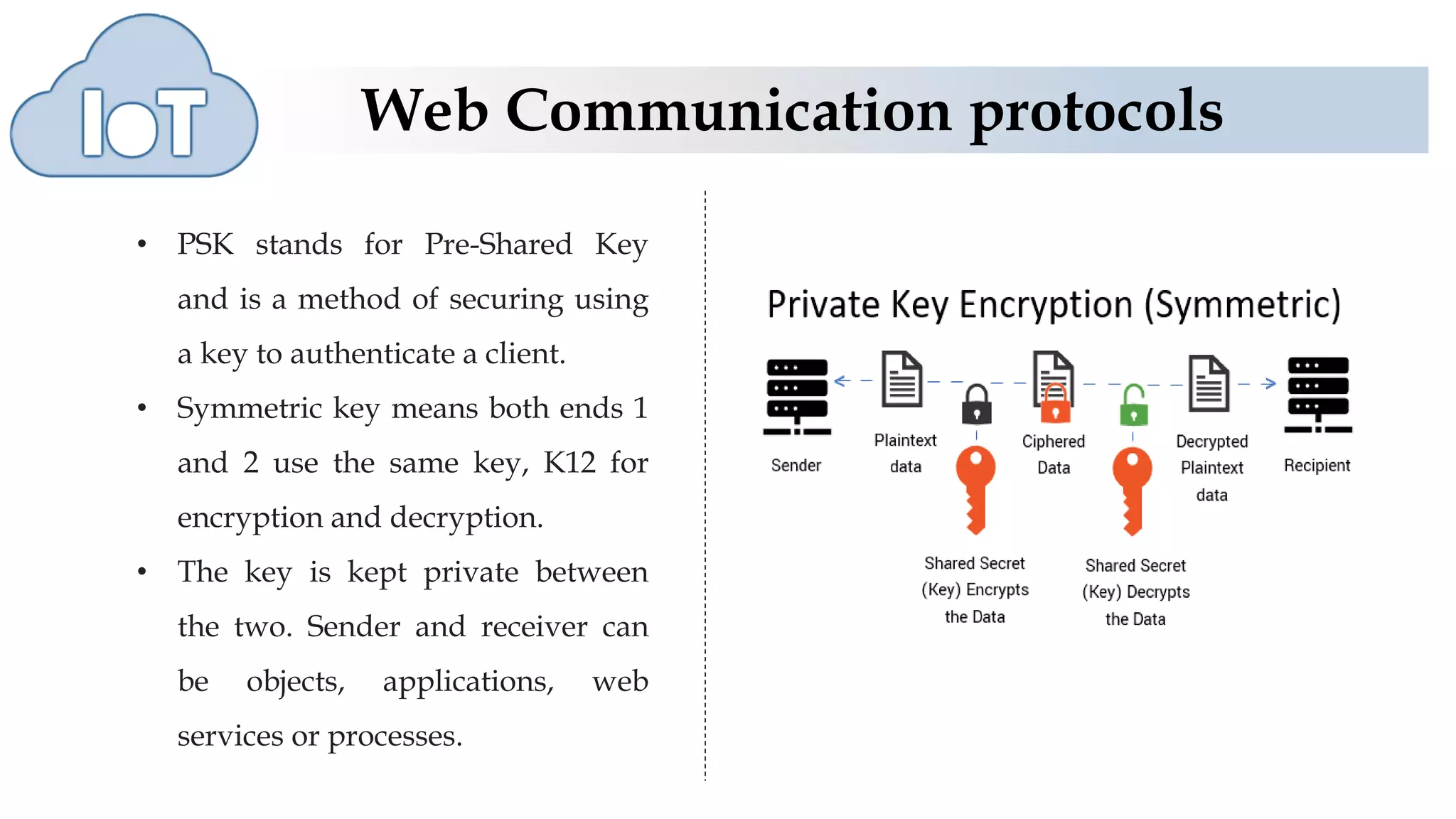
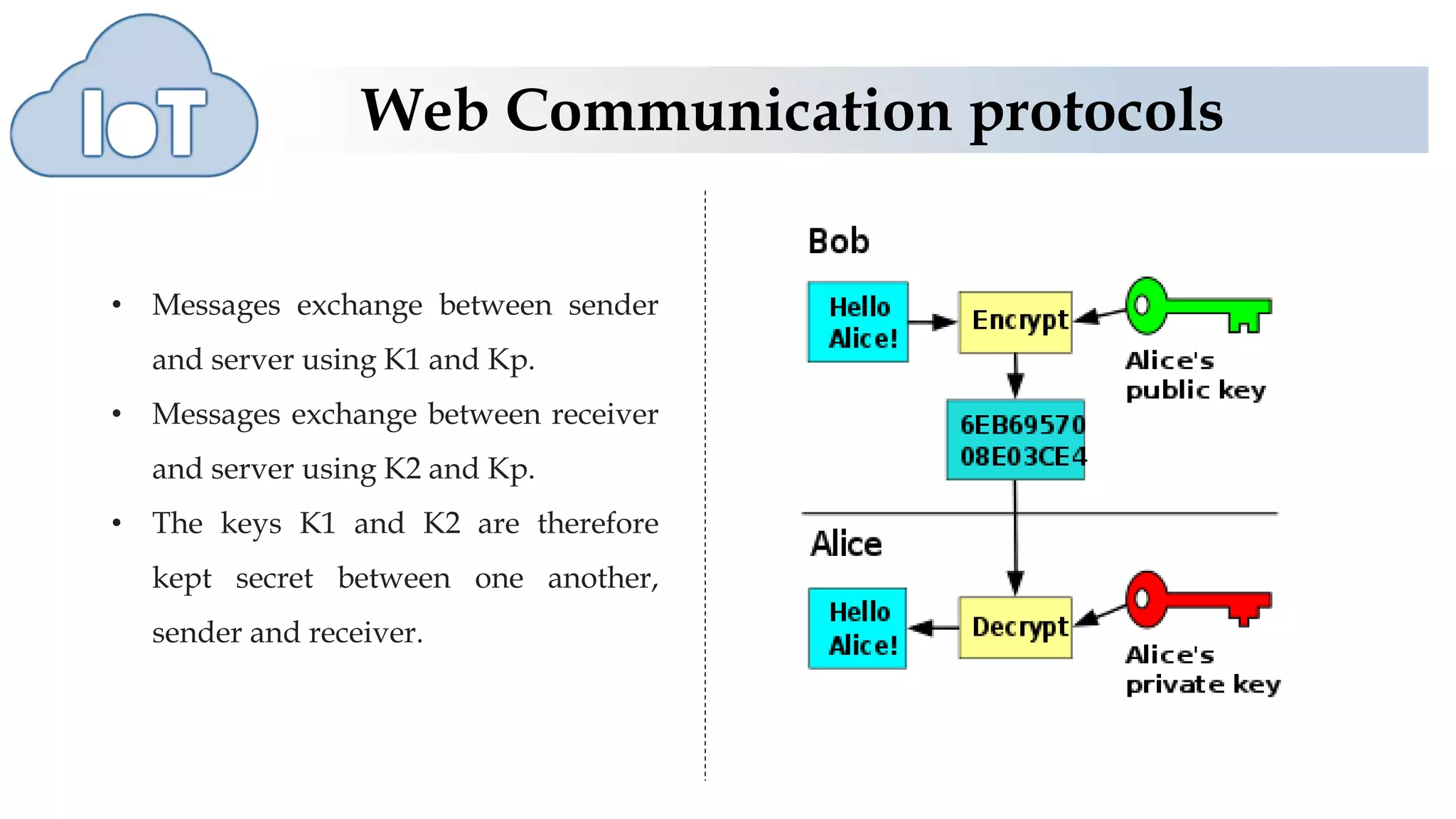
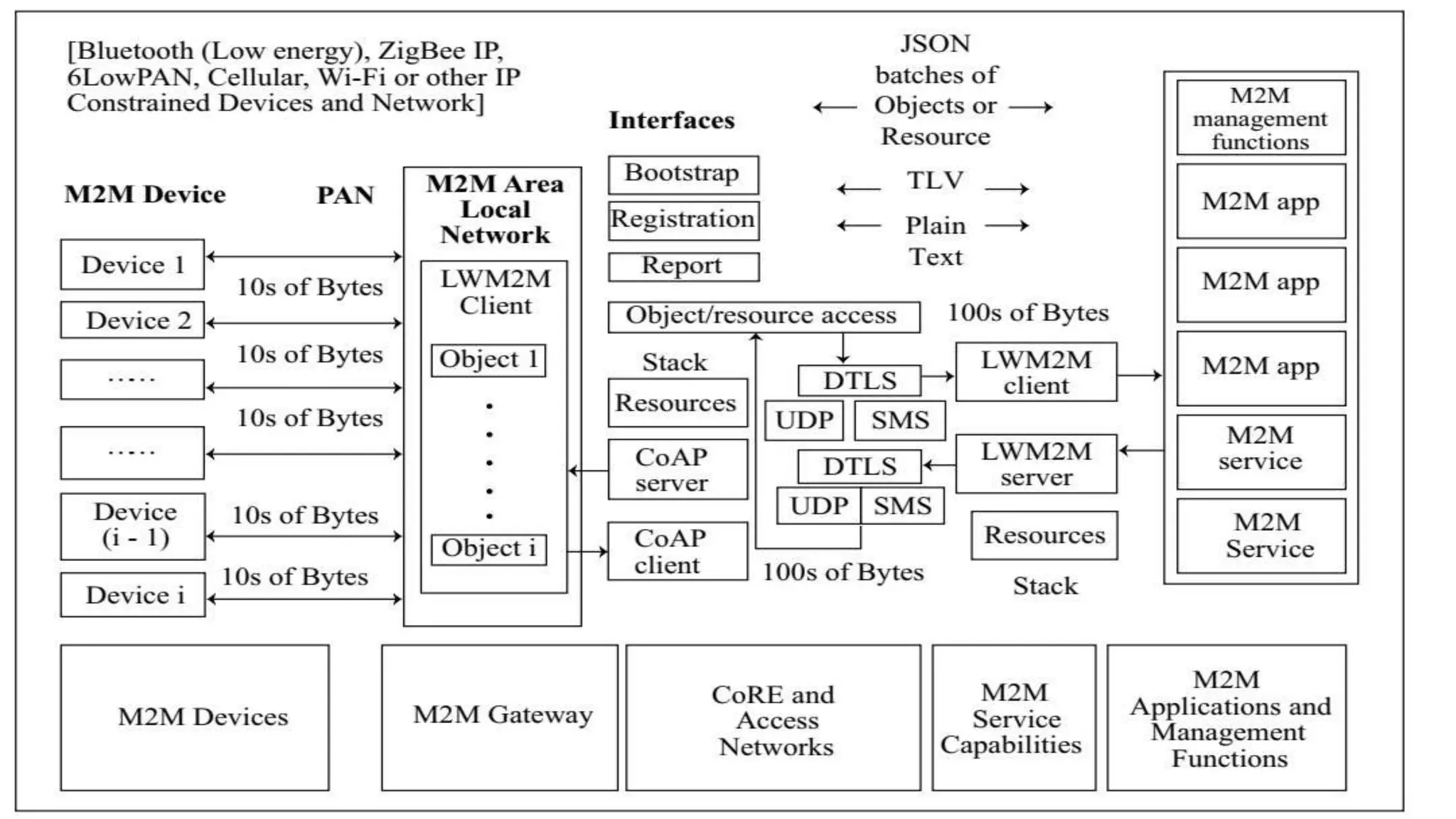
This document discusses various web communication protocols used for connectivity of devices over constrained and unconstrained environments. It describes protocols like CoAP, DTLS, JSON and TLV formats that allow small devices with limited resources to communicate securely over the web. CoAP is a specialized web transfer protocol that uses request/response model and supports resource discovery. DTLS provides security services like integrity, authentication and confidentiality for UDP-based applications. JSON and TLV are compact data formats used for message transmission.