This document provides an overview of a presentation on practical exploitation and cyberstalking. The presentation introduces tools like Metasploit and Social Engineering Toolkit (SET) and demonstrates how they can be used for both legal and illegal purposes, like cyberstalking. It discusses how easy it is to profile and target individuals online to steal identities or spread misinformation. The document emphasizes that while hacking can be fun, the implications of cyberstalking should be taken seriously due to its potential real-world consequences.















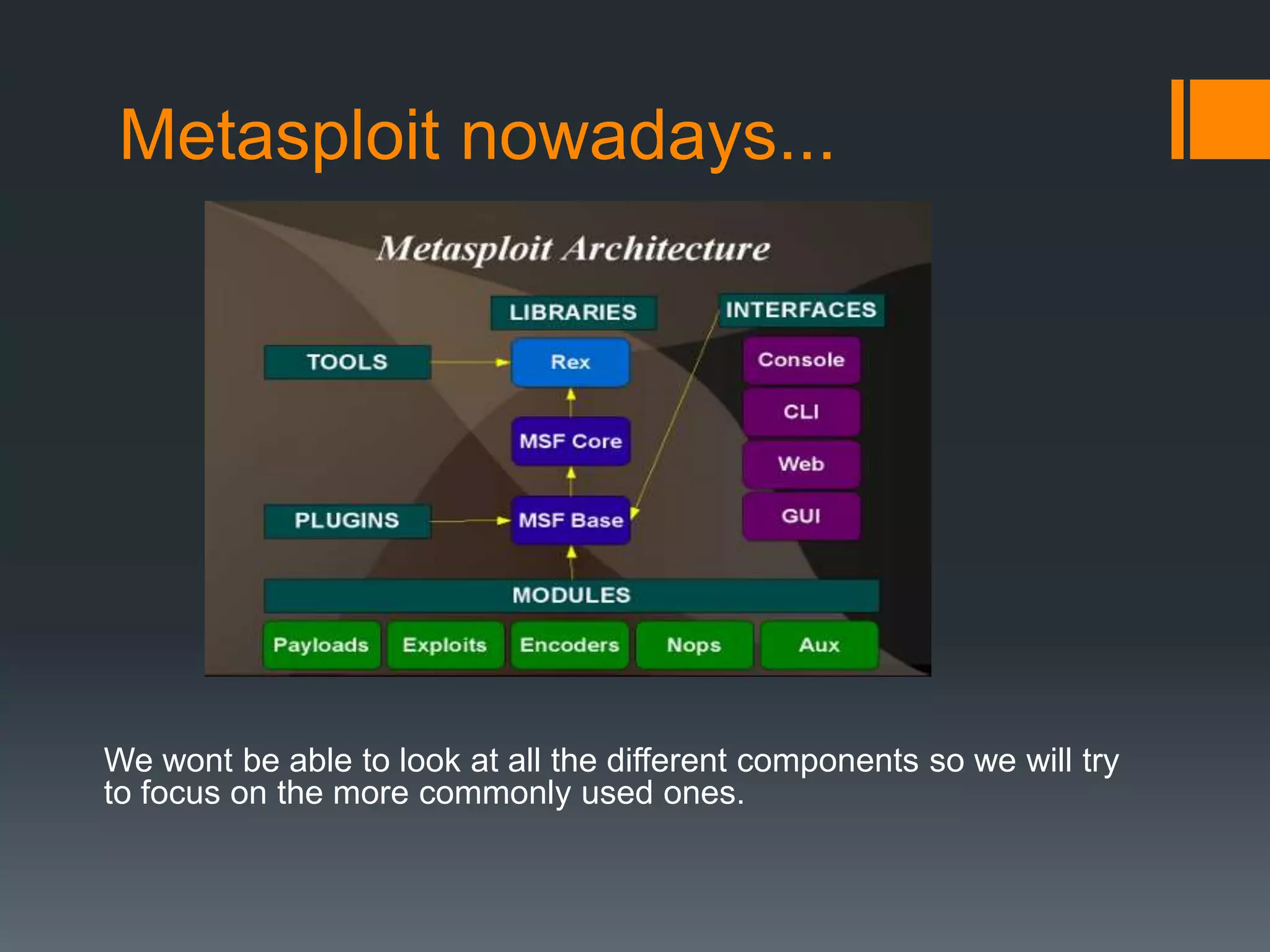




![Metasploit – Main ModulesExploits – Main module – used to pwn shit! :]Encoders – Used to transform raw versions of payloadsPayload – Used to connect to the shit u pwn!](https://image.slidesharecdn.com/practicalexploitationandsocialengineering-110705120836-phpapp02/75/Practical-exploitation-and-social-engineering-51-2048.jpg)