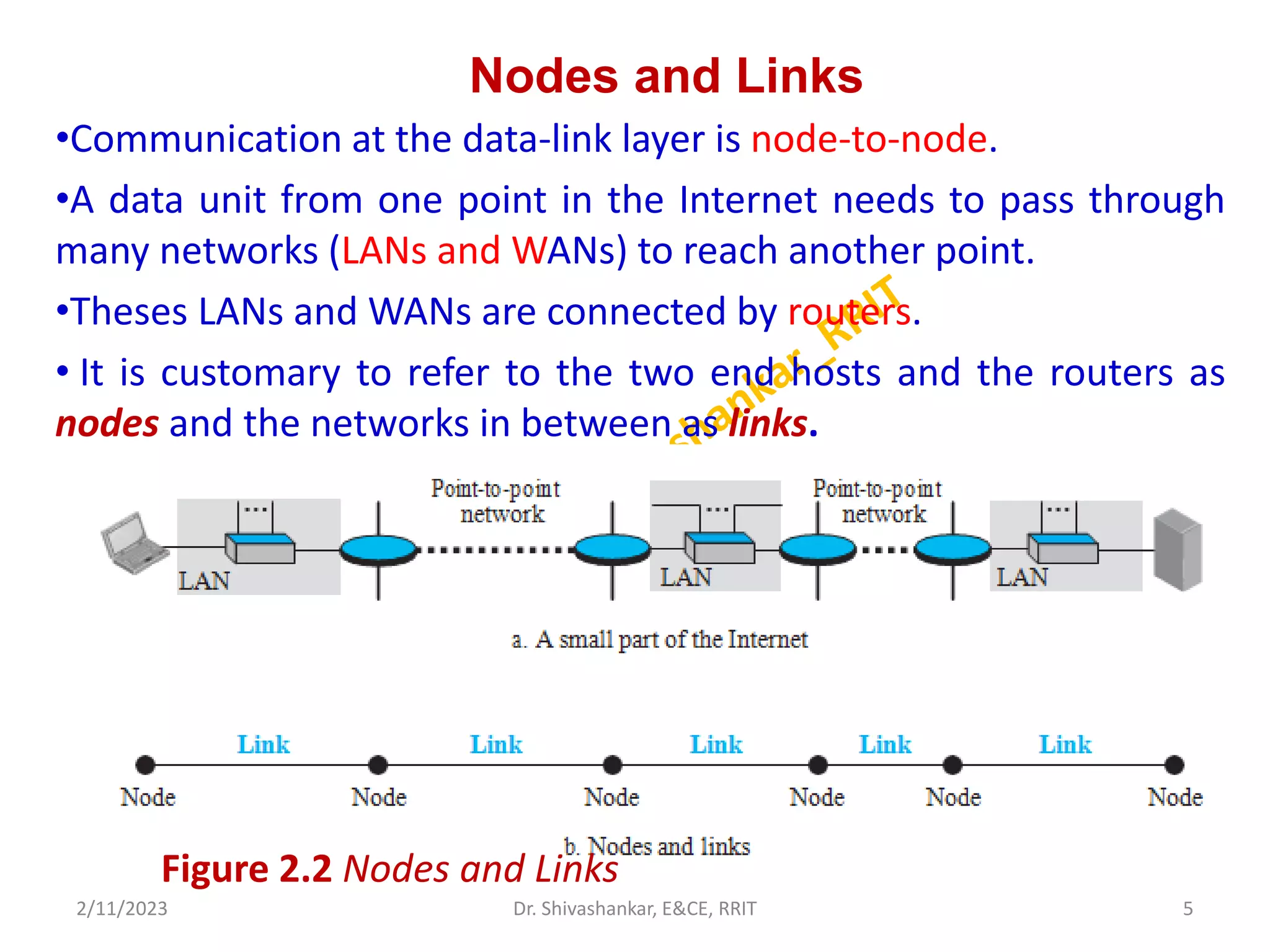
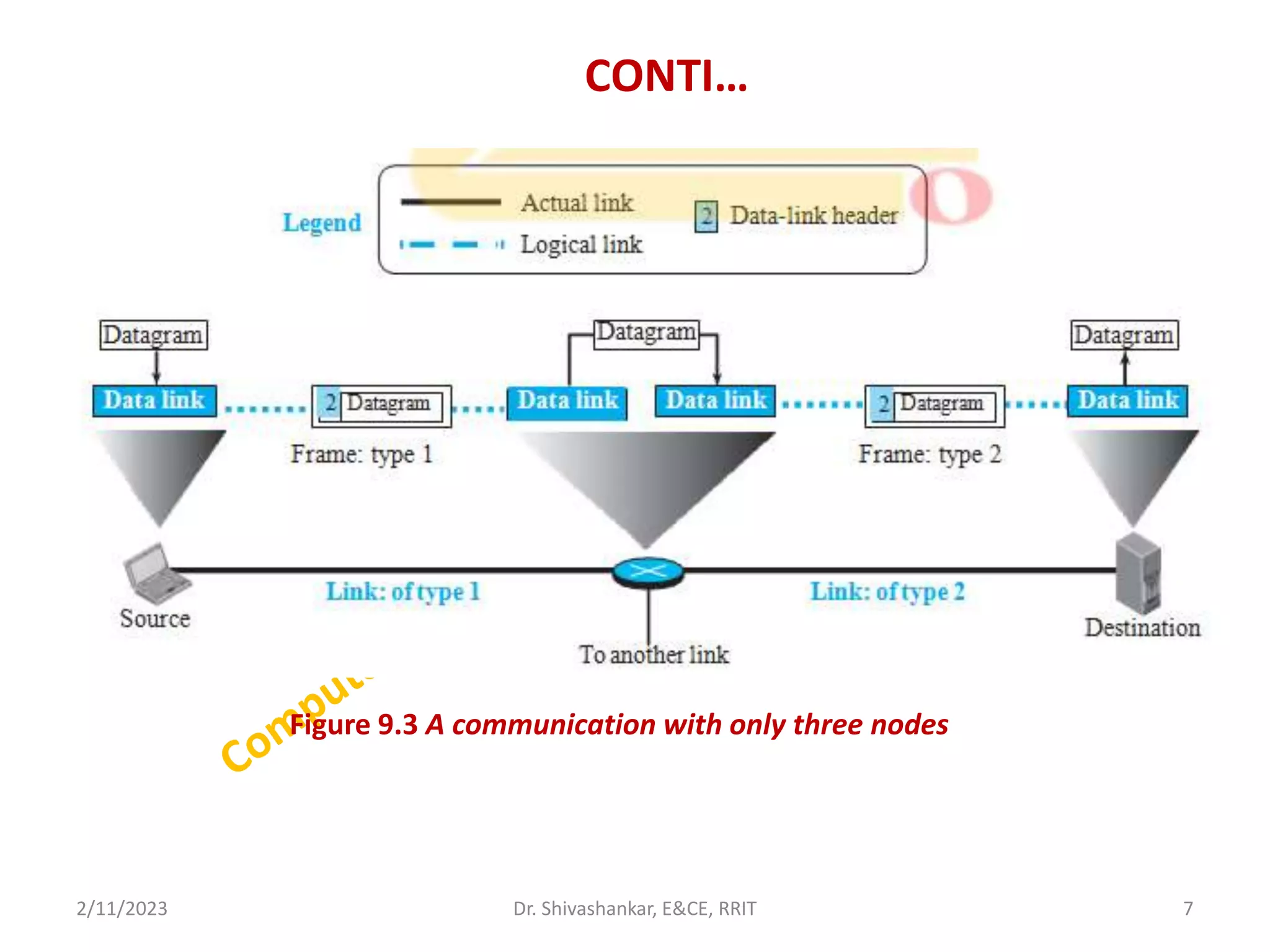
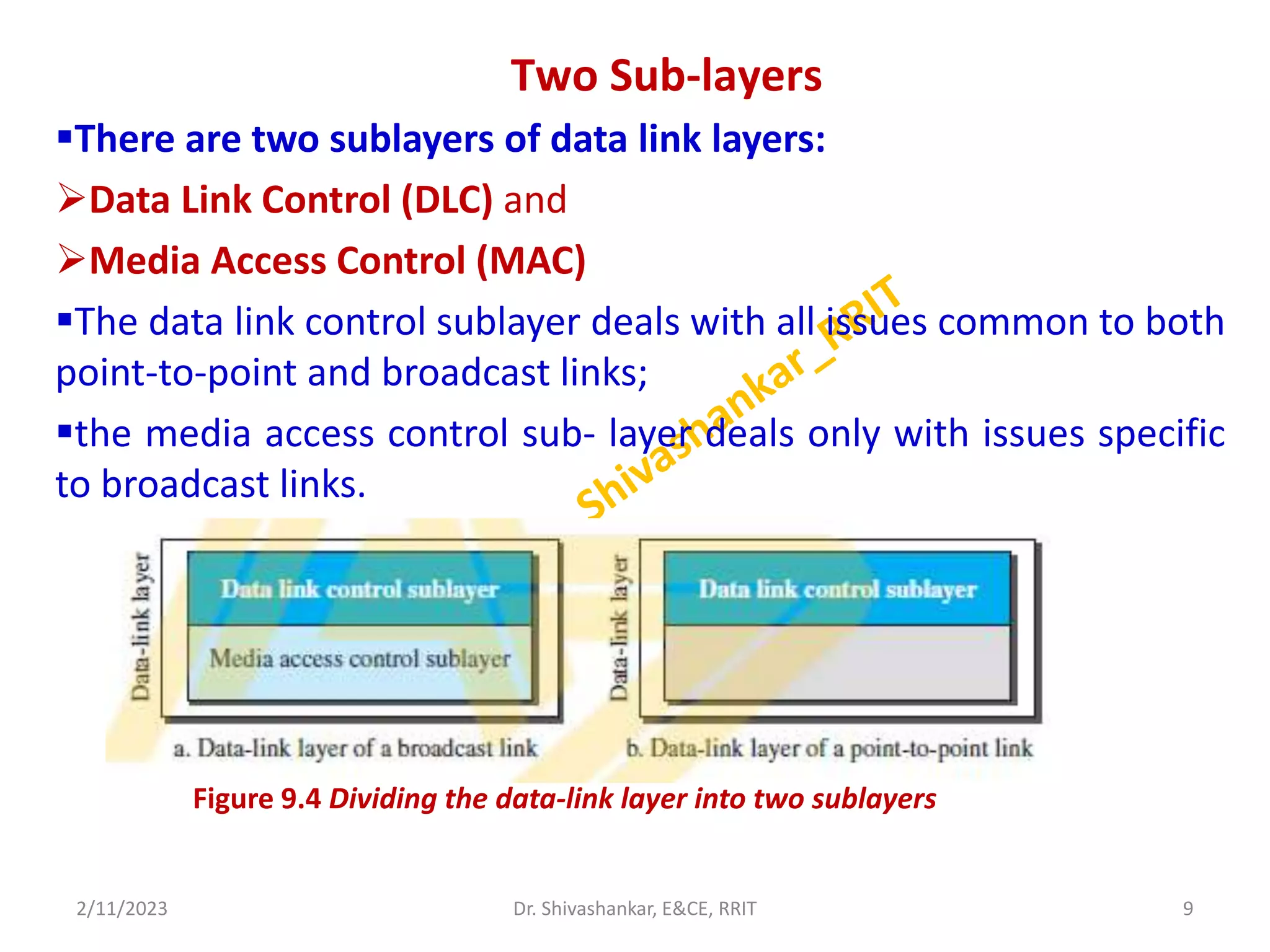
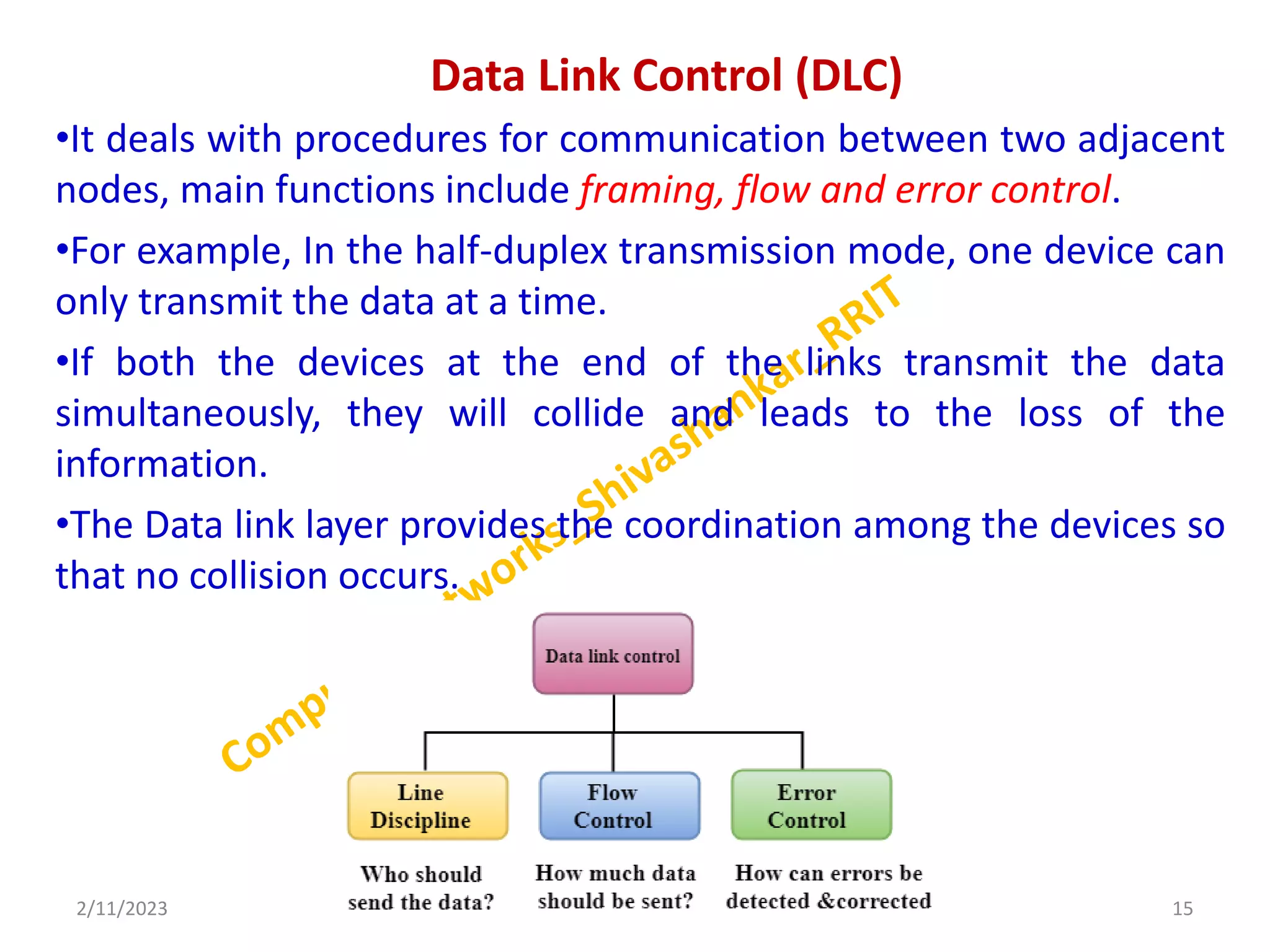
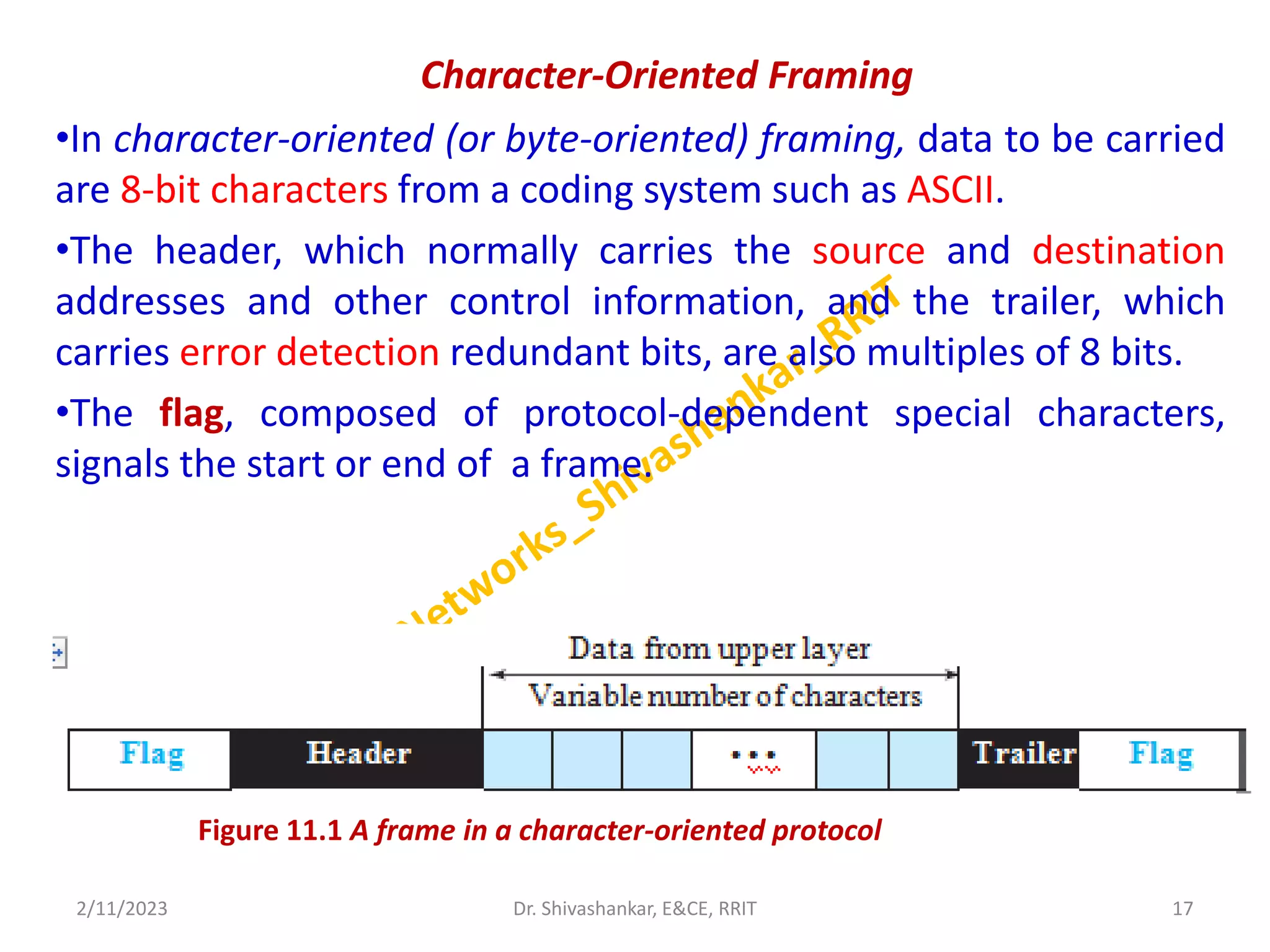
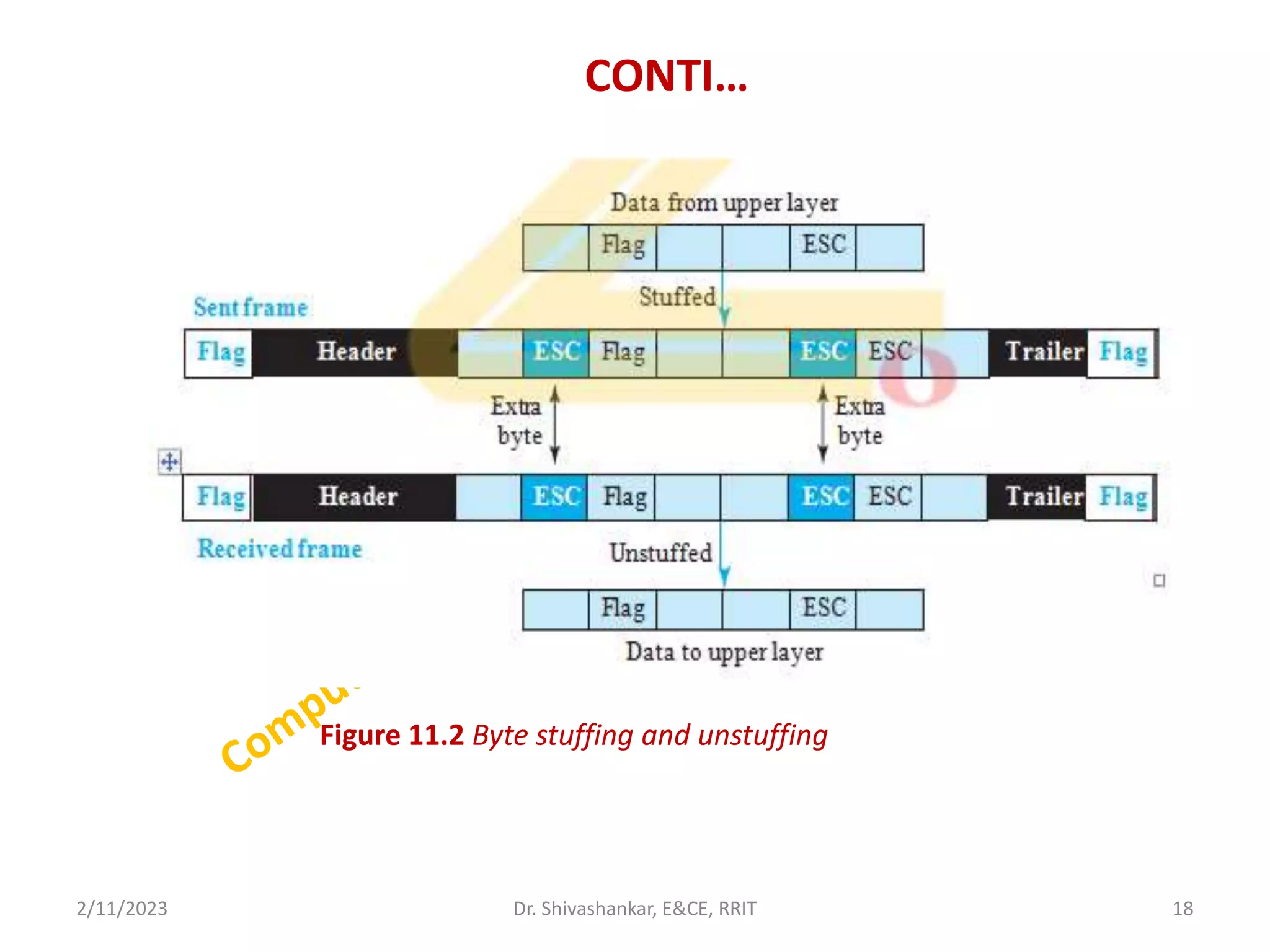
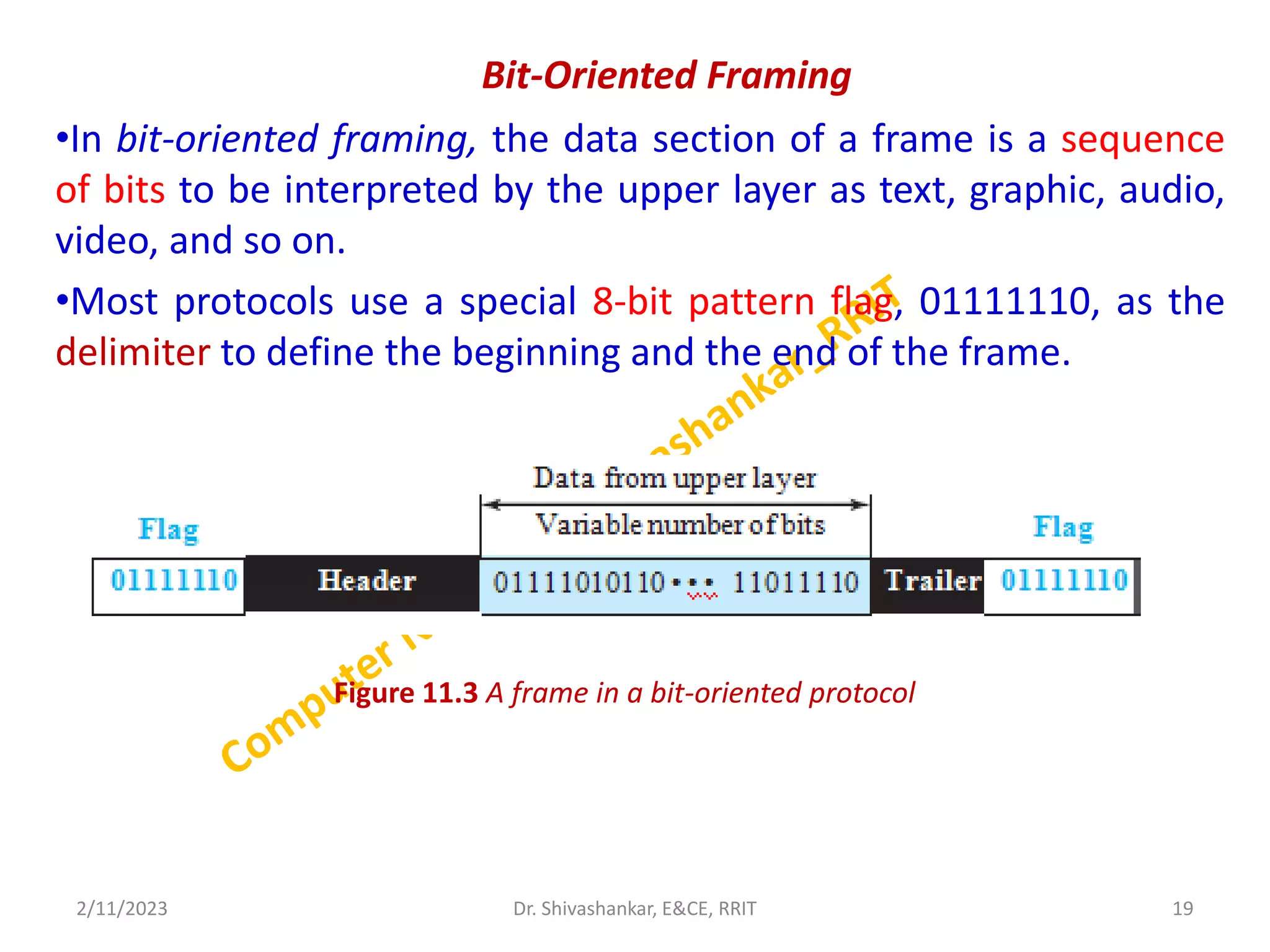
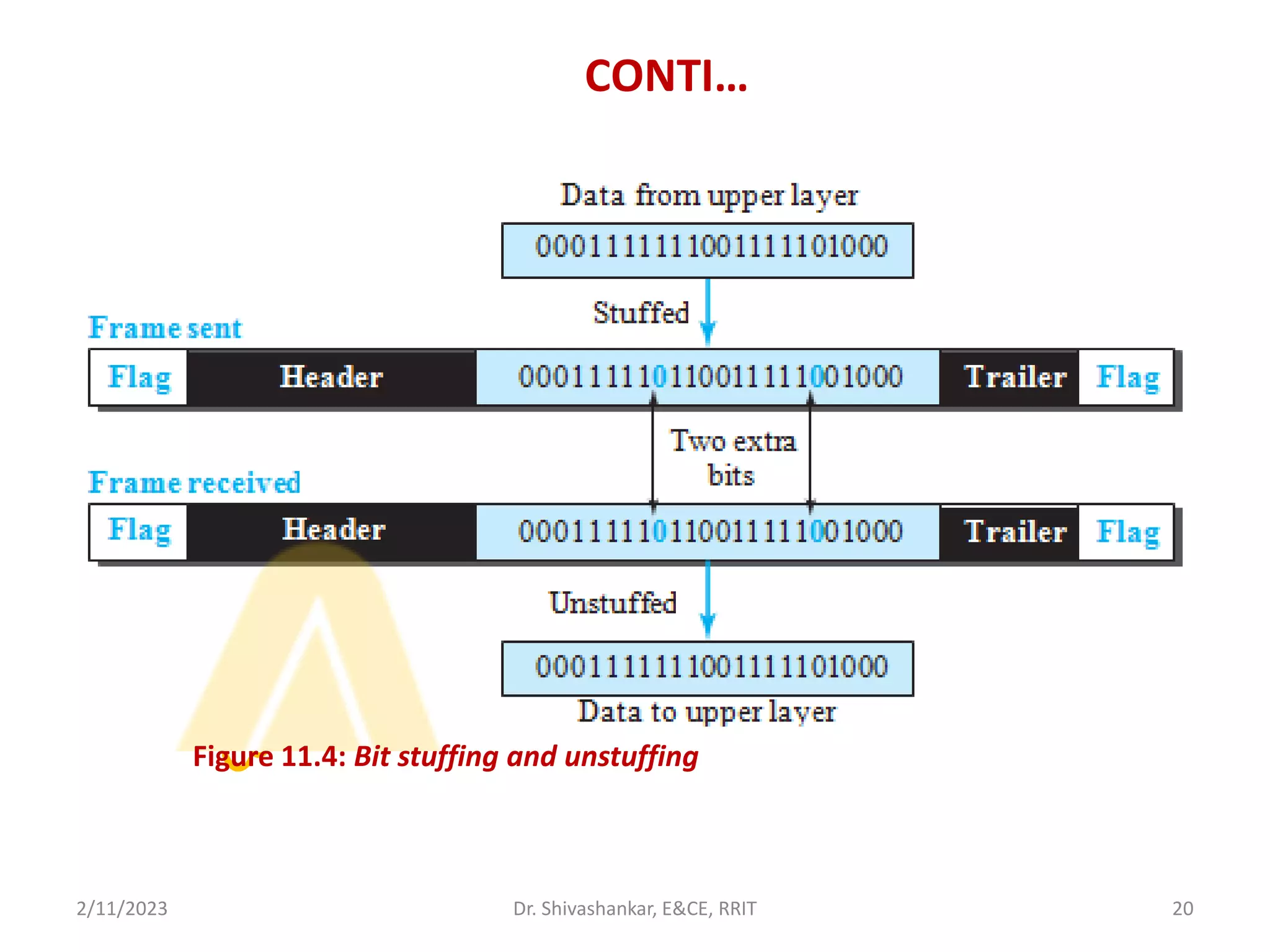
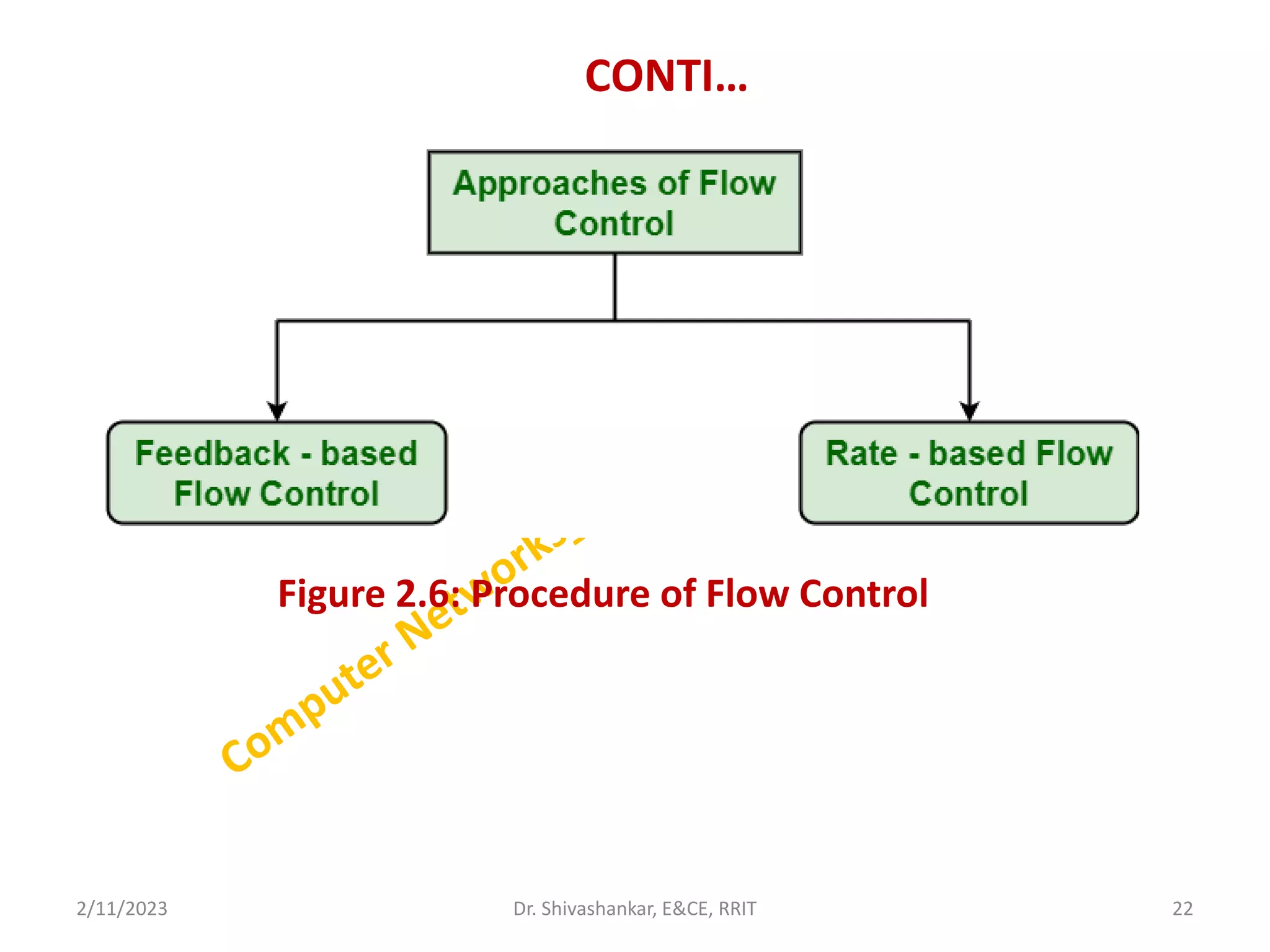
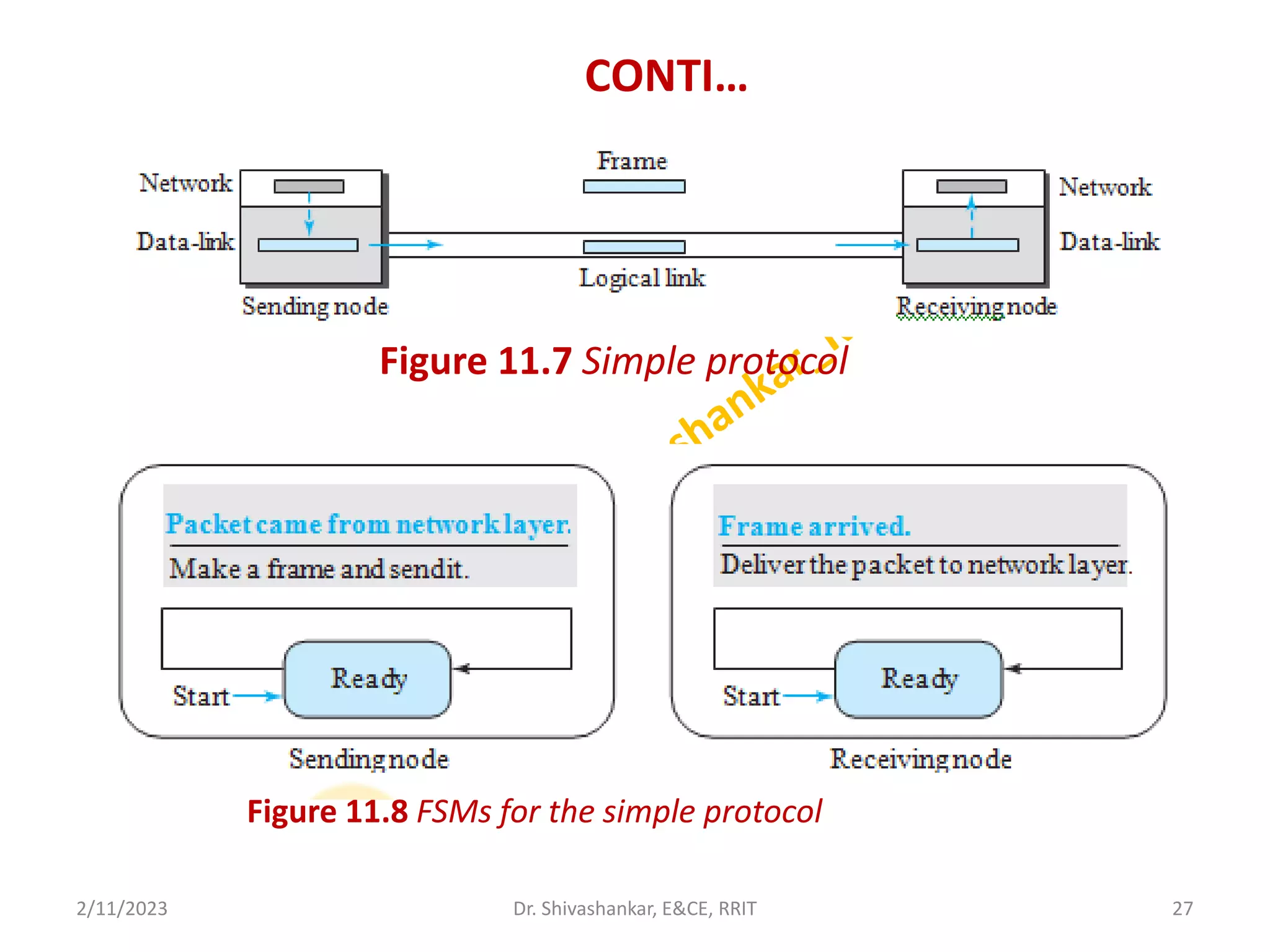
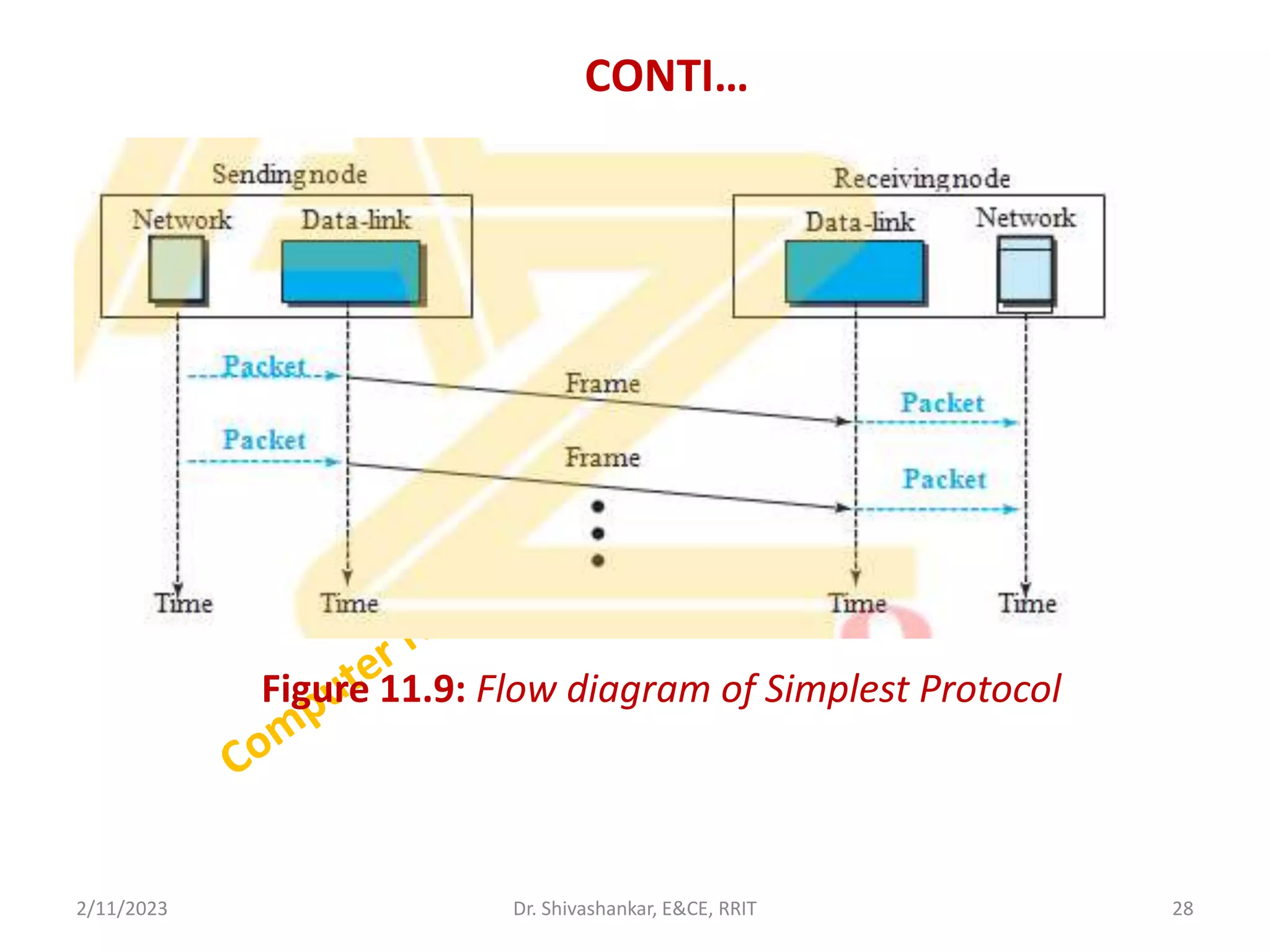
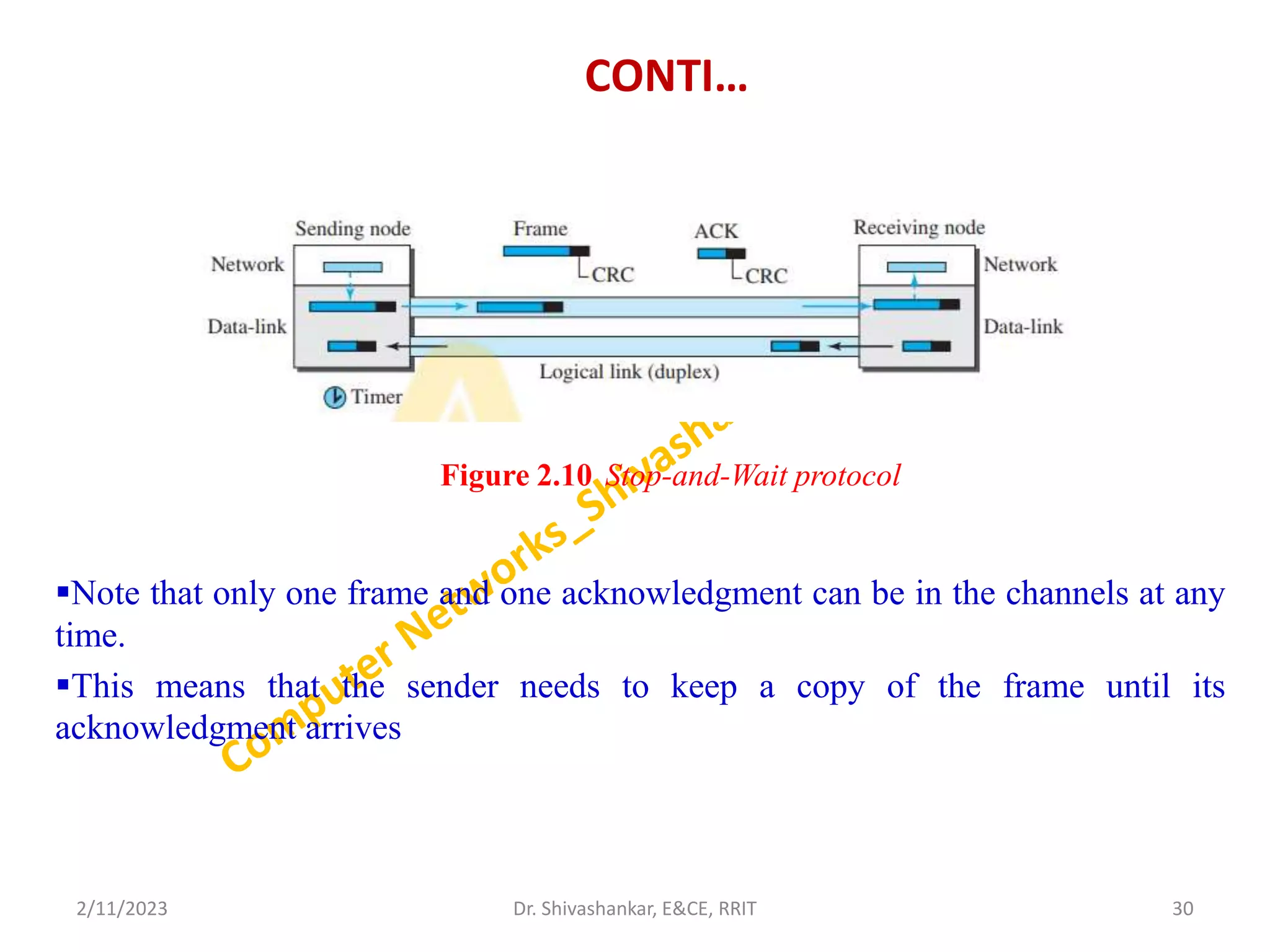
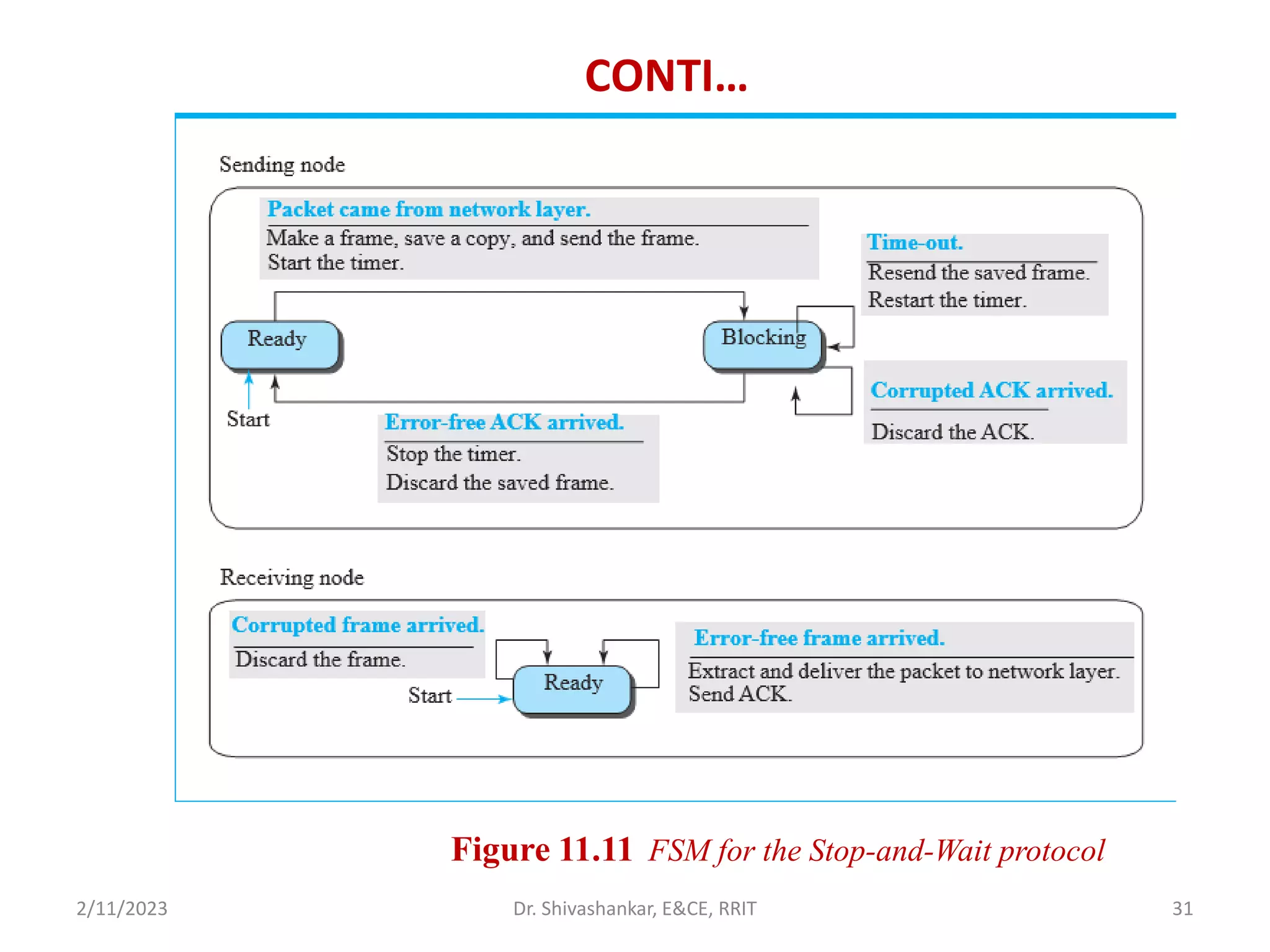
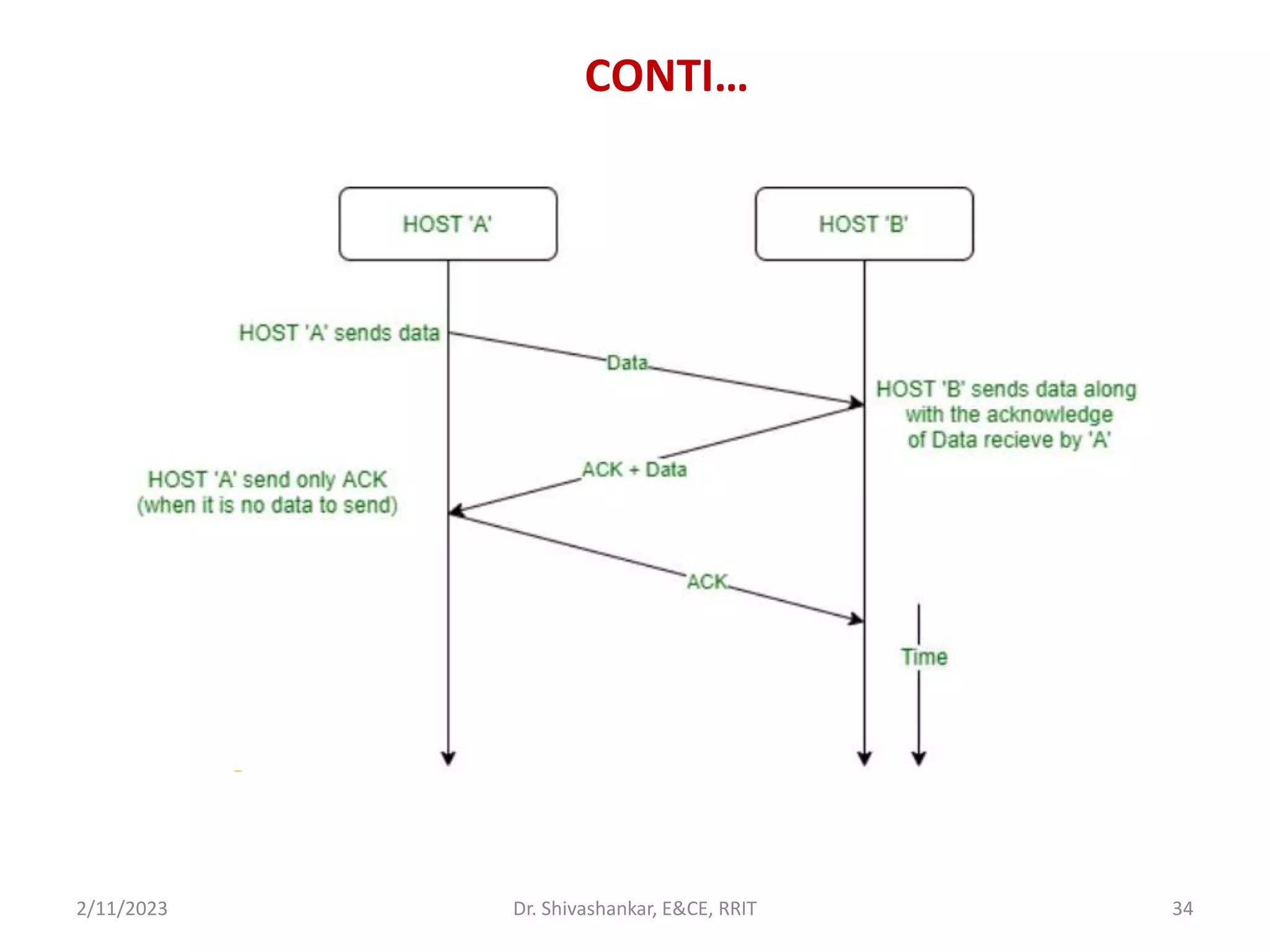
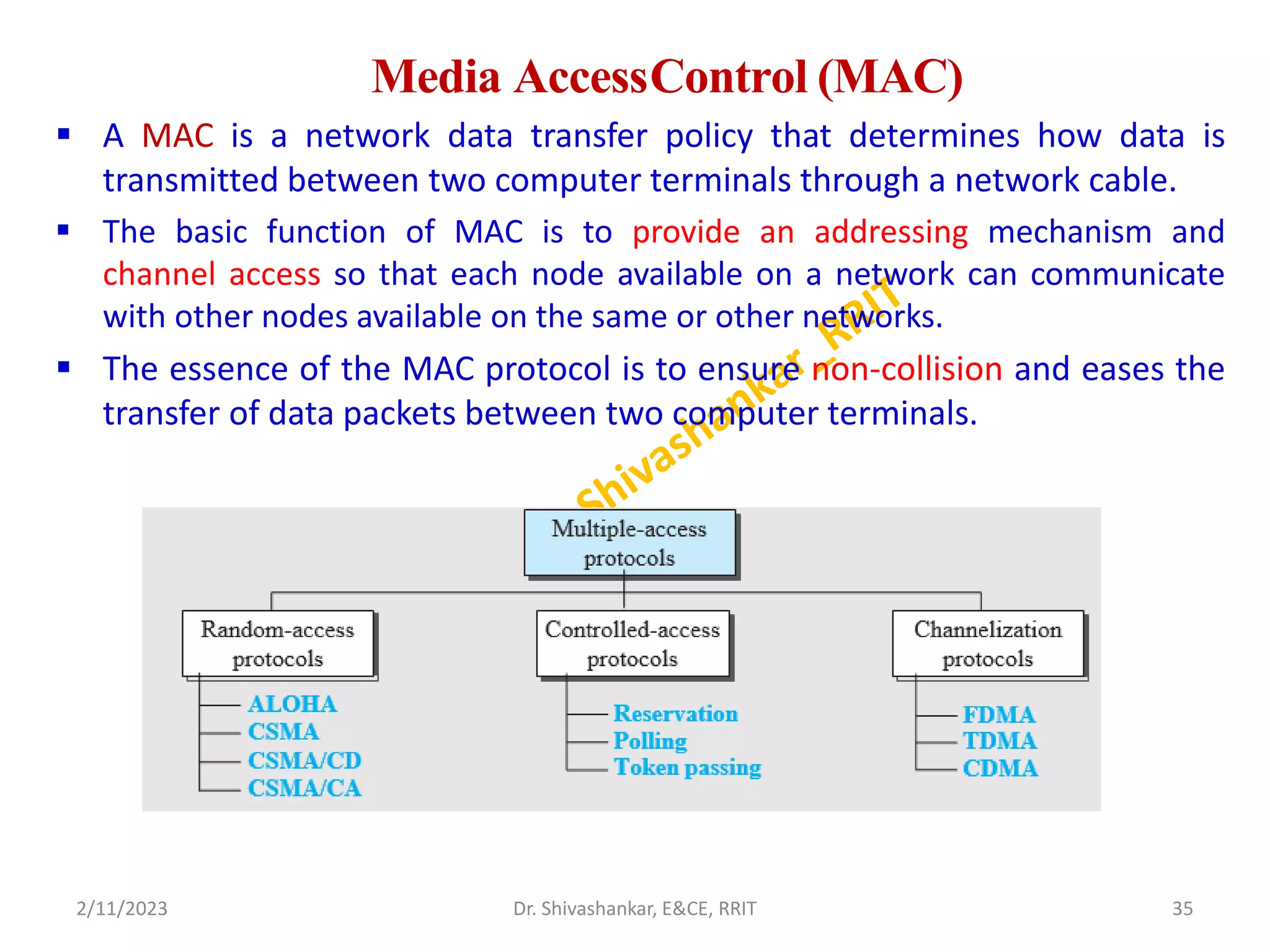
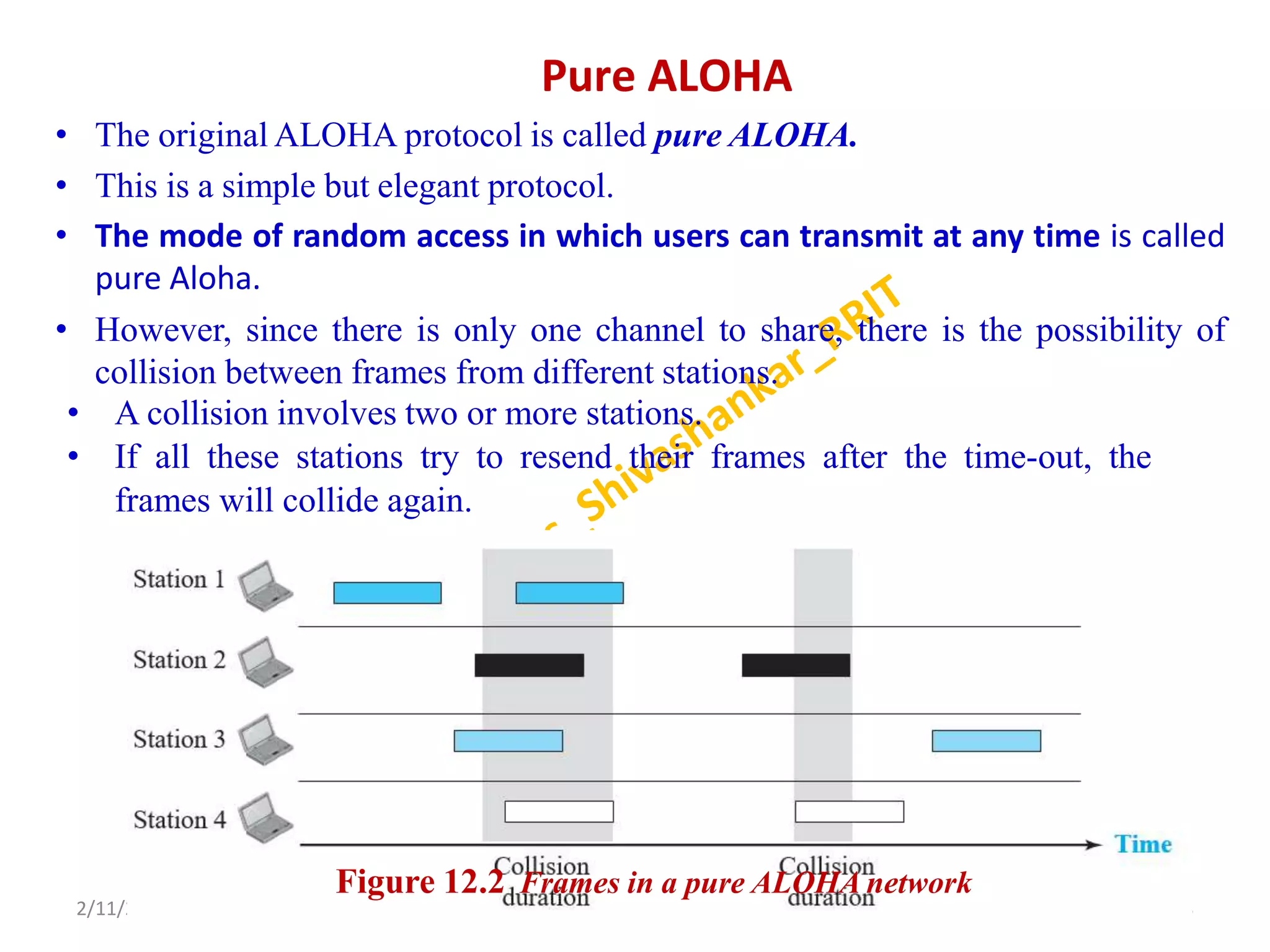
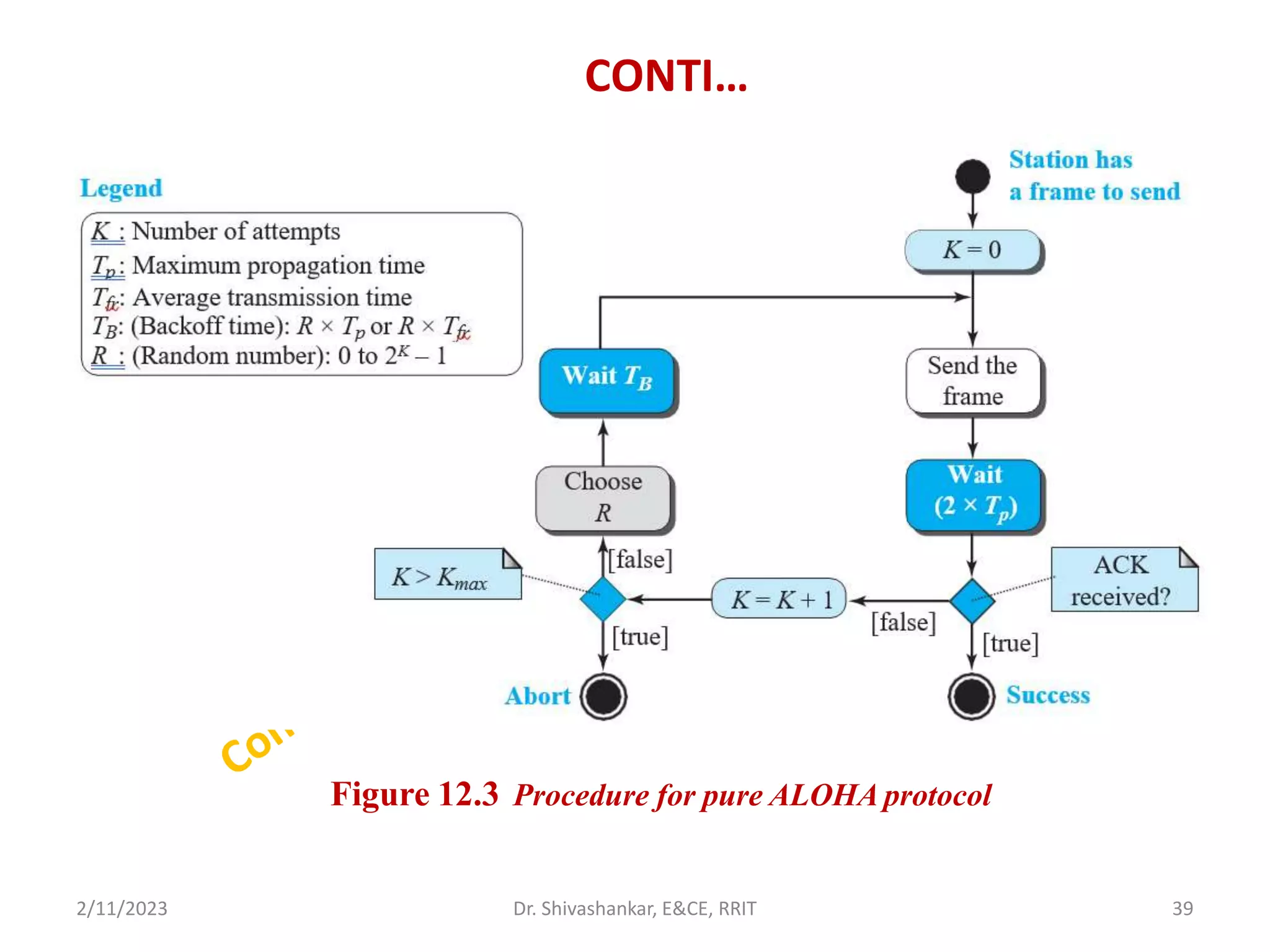
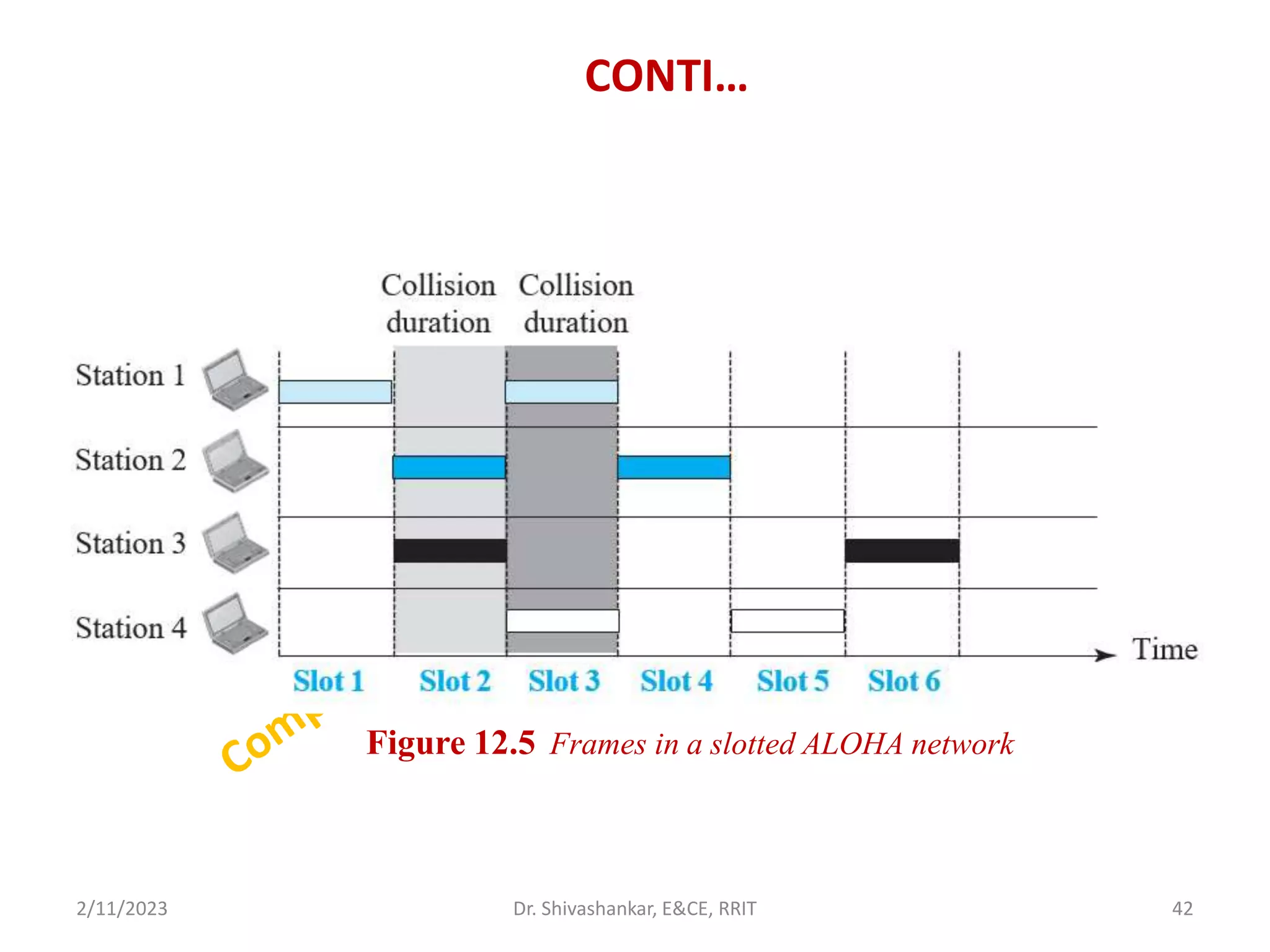
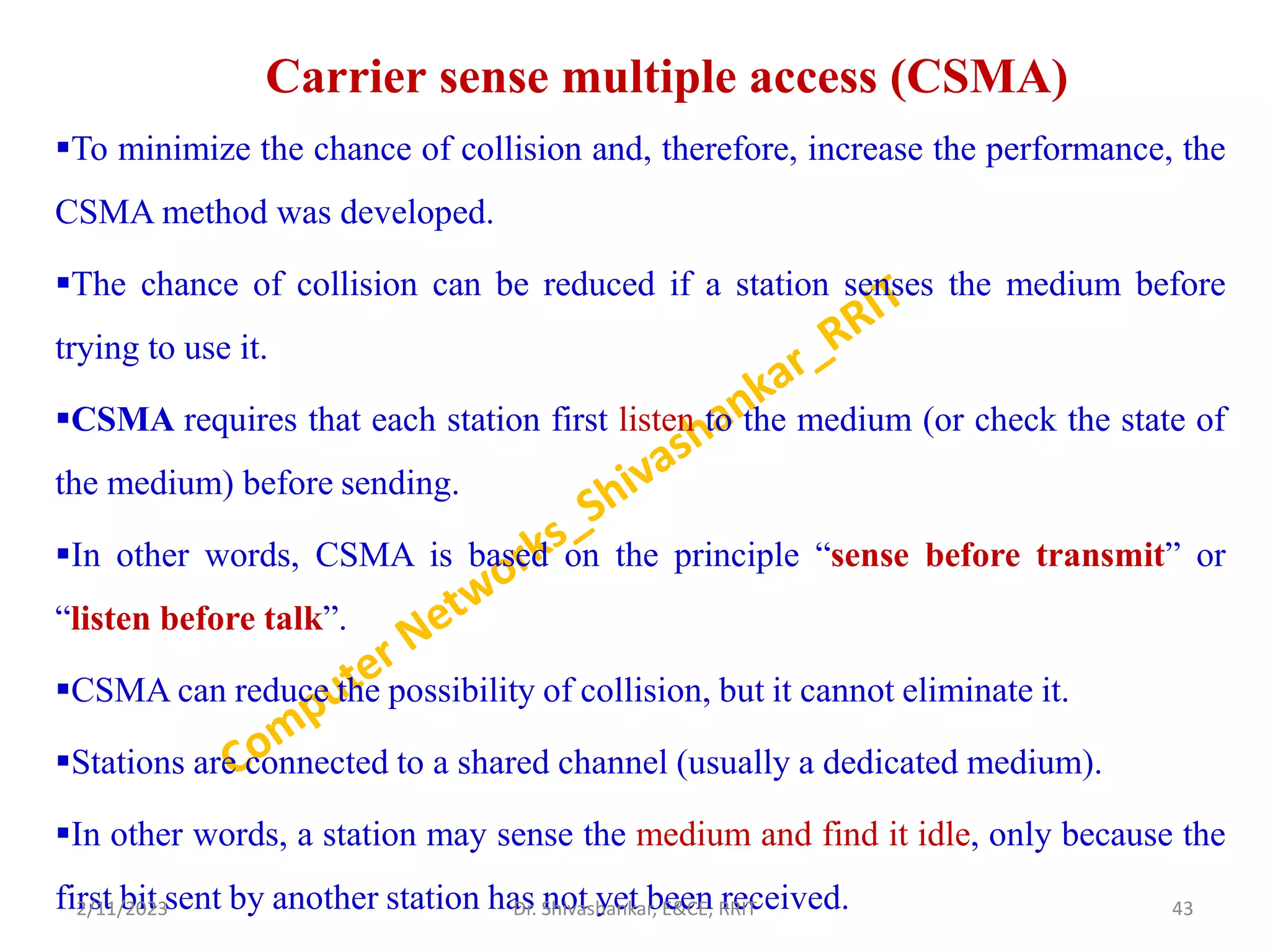
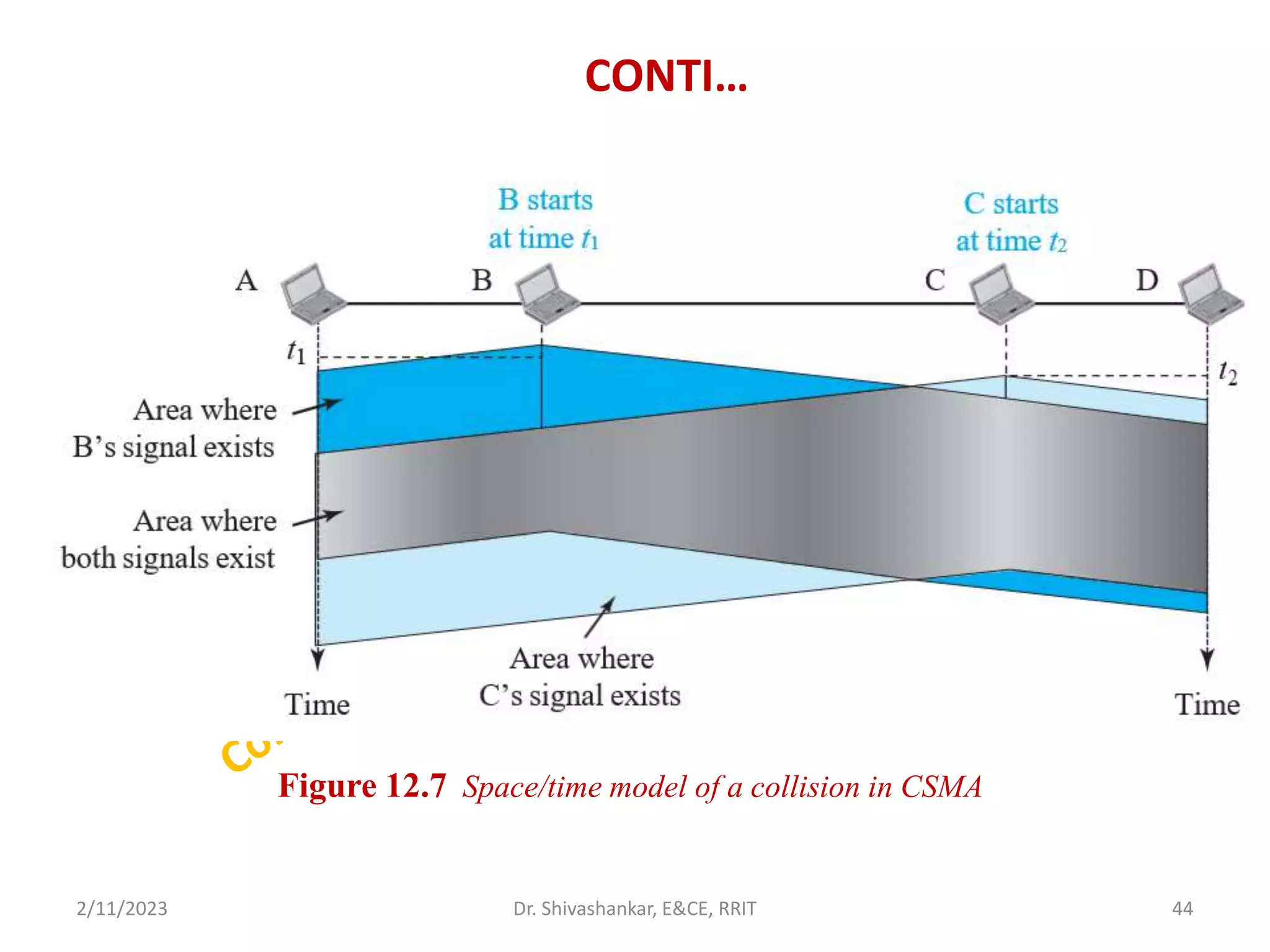
The document describes a computer networks course taught by Dr. Shivashankar. The course aims to help students understand networking concepts and protocols at different layers. It will cover topics like network architectures, protocols, configurations, and analyzing simple networks. The module on the data link layer is discussed in detail, including framing, flow control, error control, and protocols like stop-and-wait.