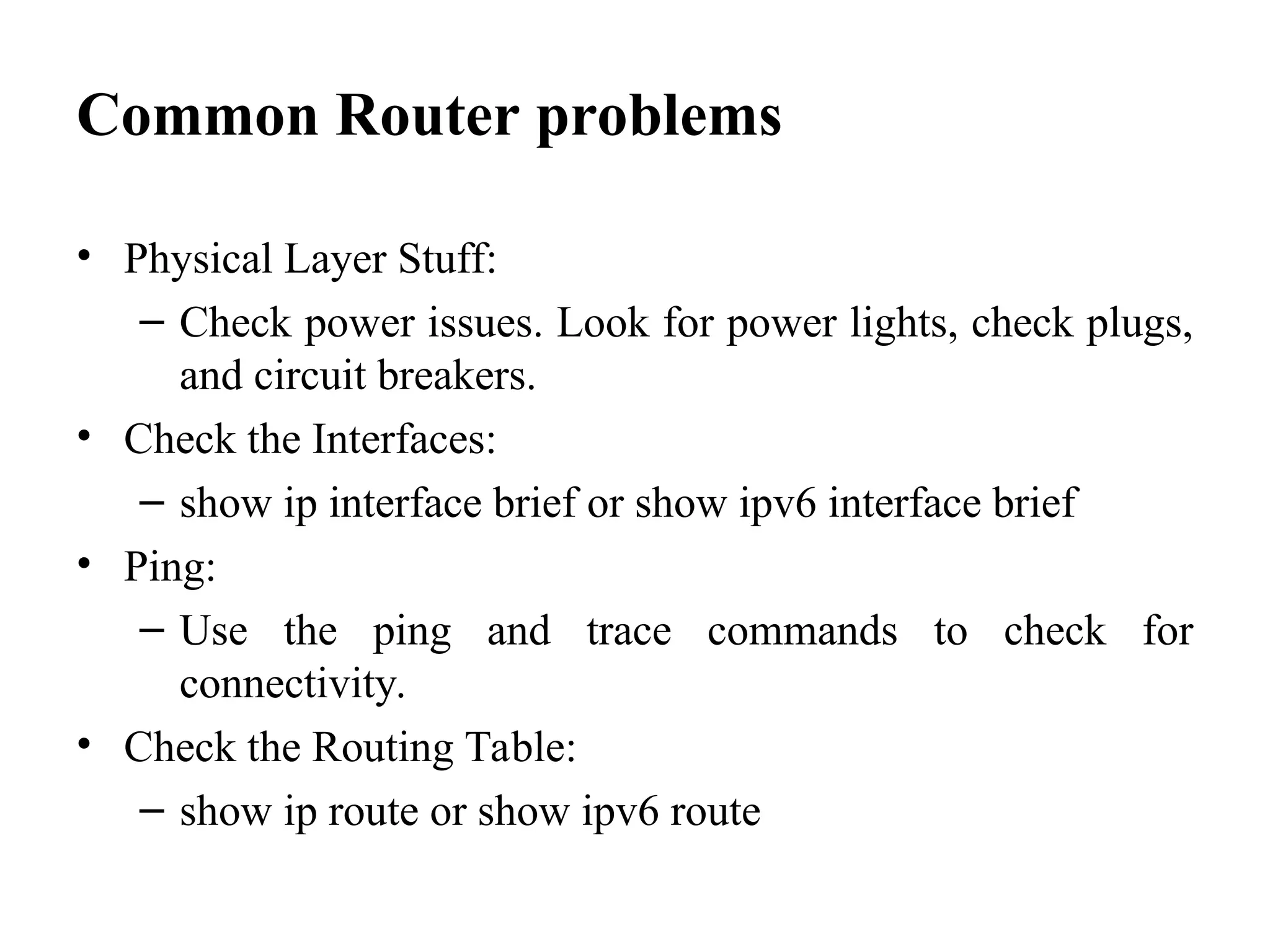
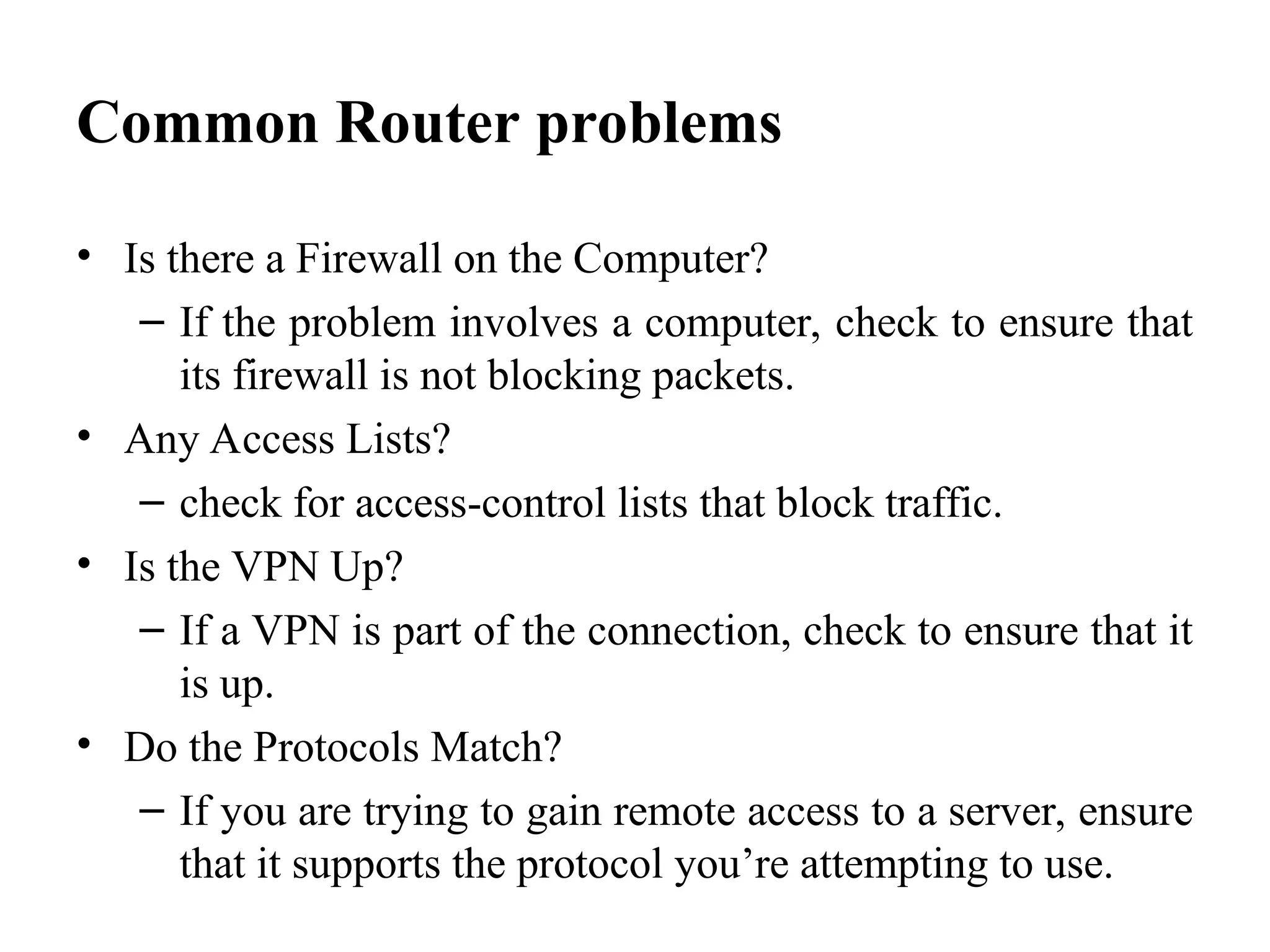
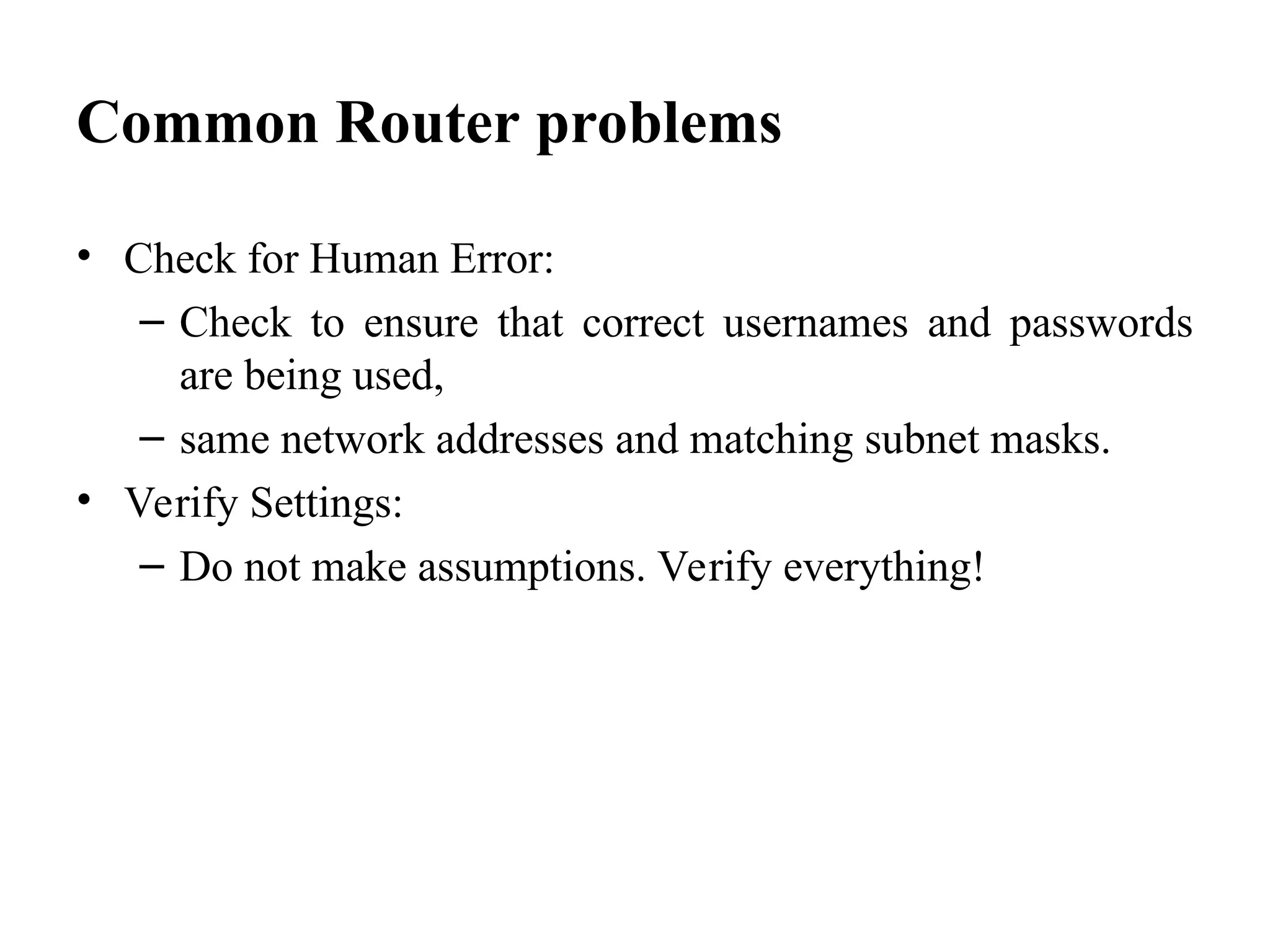
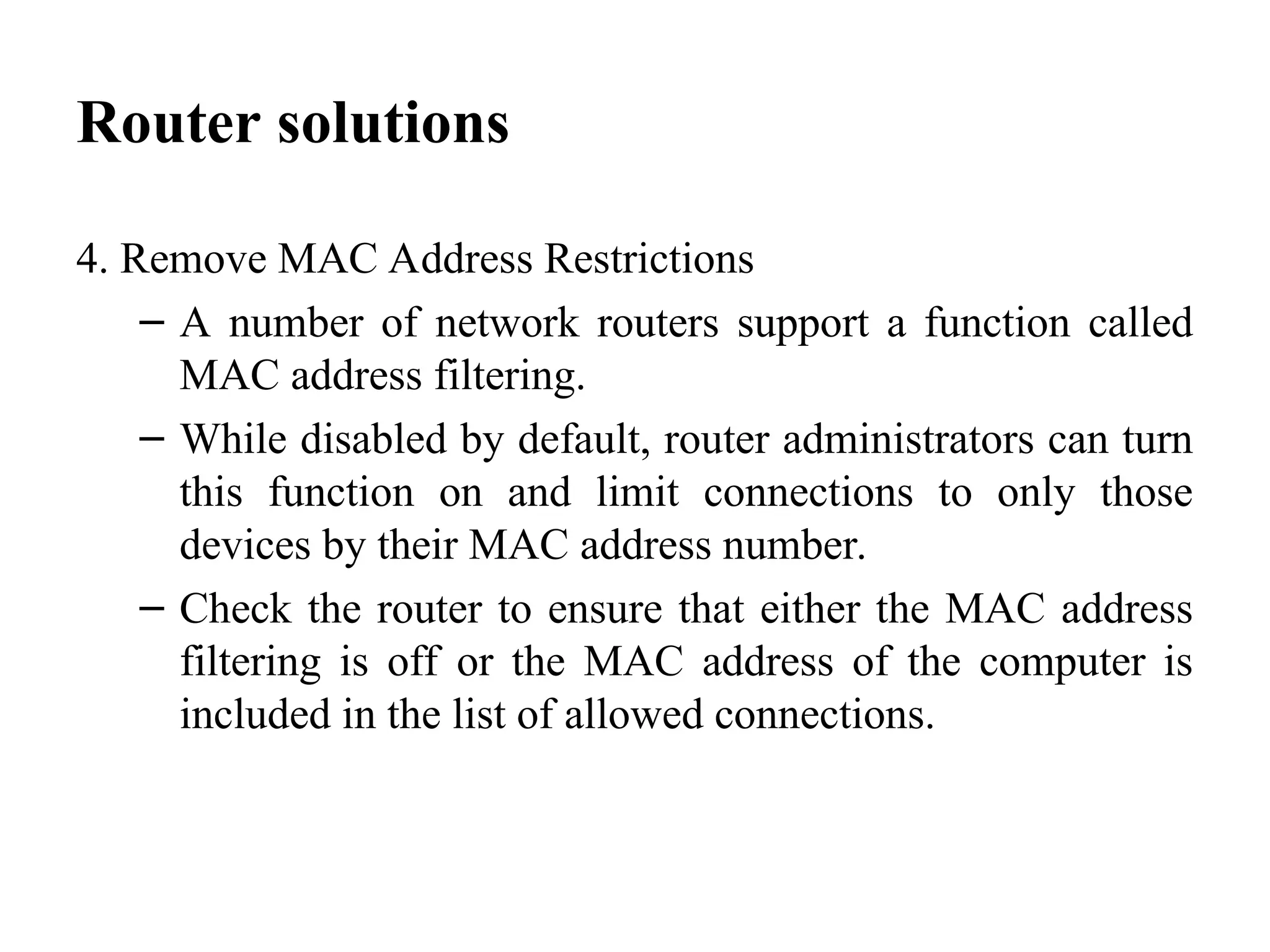
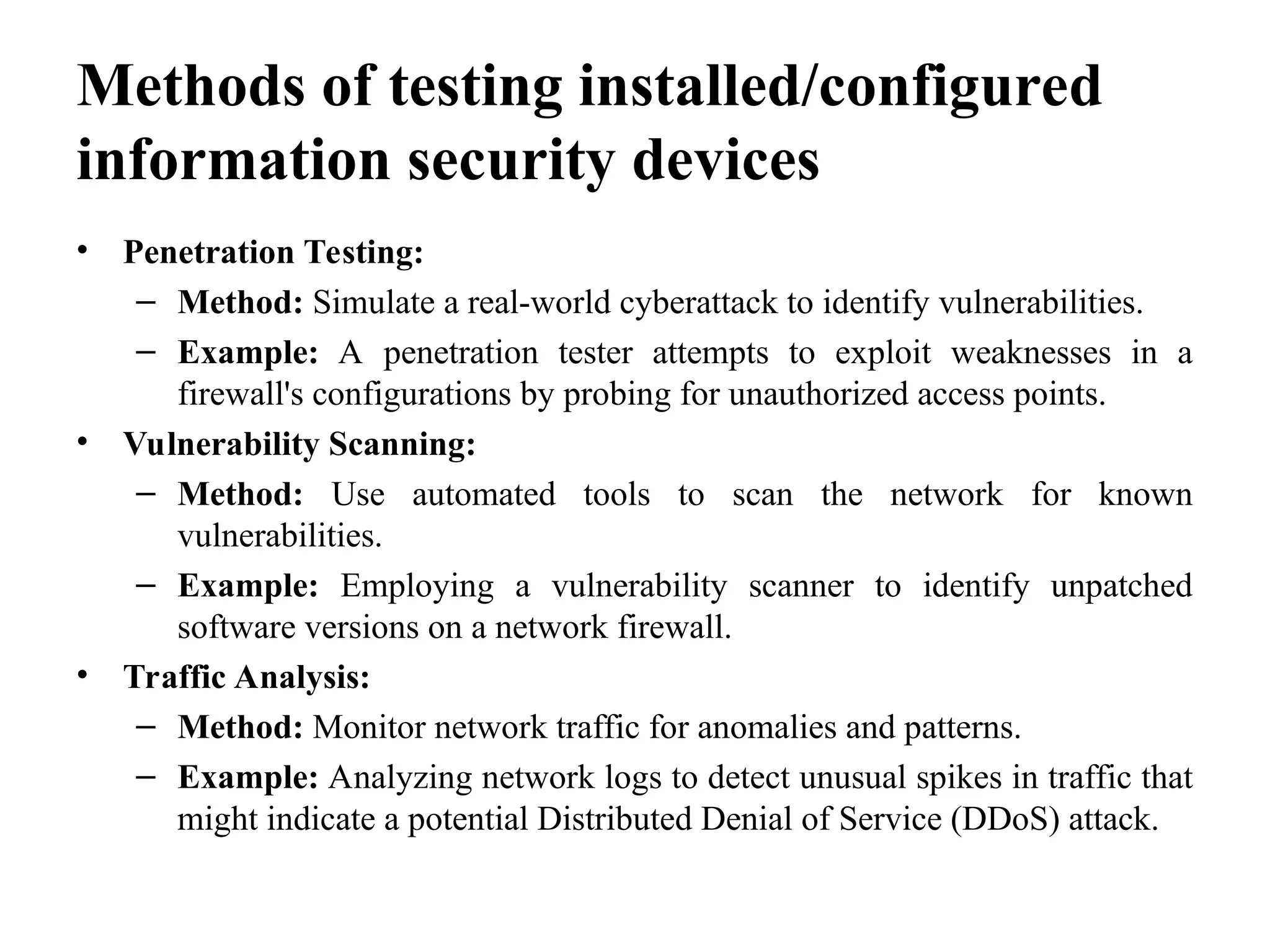
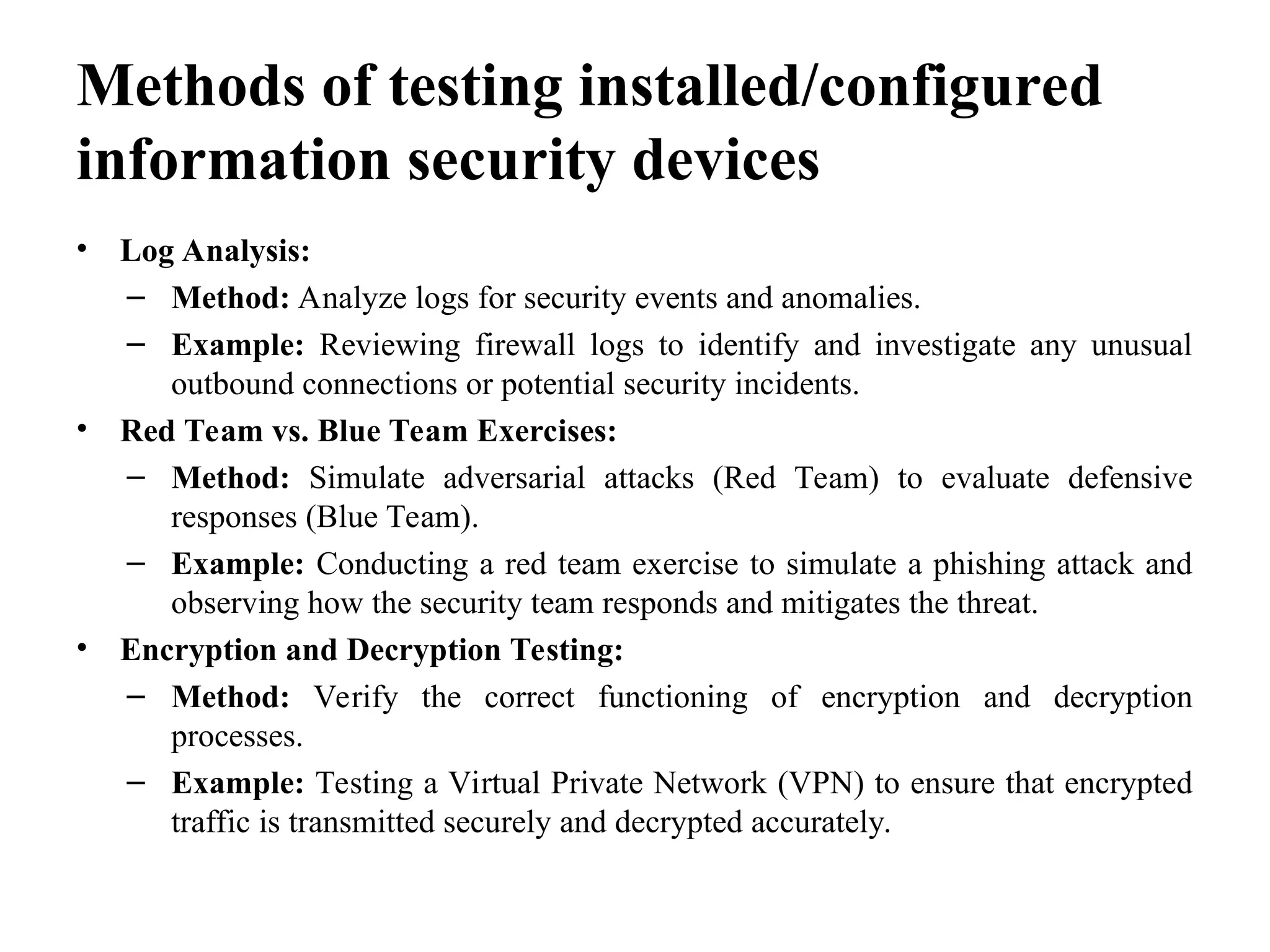
The document outlines common issues and solutions in installing and configuring information security devices, such as device compatibility, incorrect configuration, and lack of training, alongside methods for resolution like thorough planning and regular updates. It also provides troubleshooting steps for firewall and router problems, including testing connectivity and checking configurations. Additionally, it discusses methods for testing the effectiveness of installed security devices, including penetration testing, vulnerability scanning, and user authentication testing.