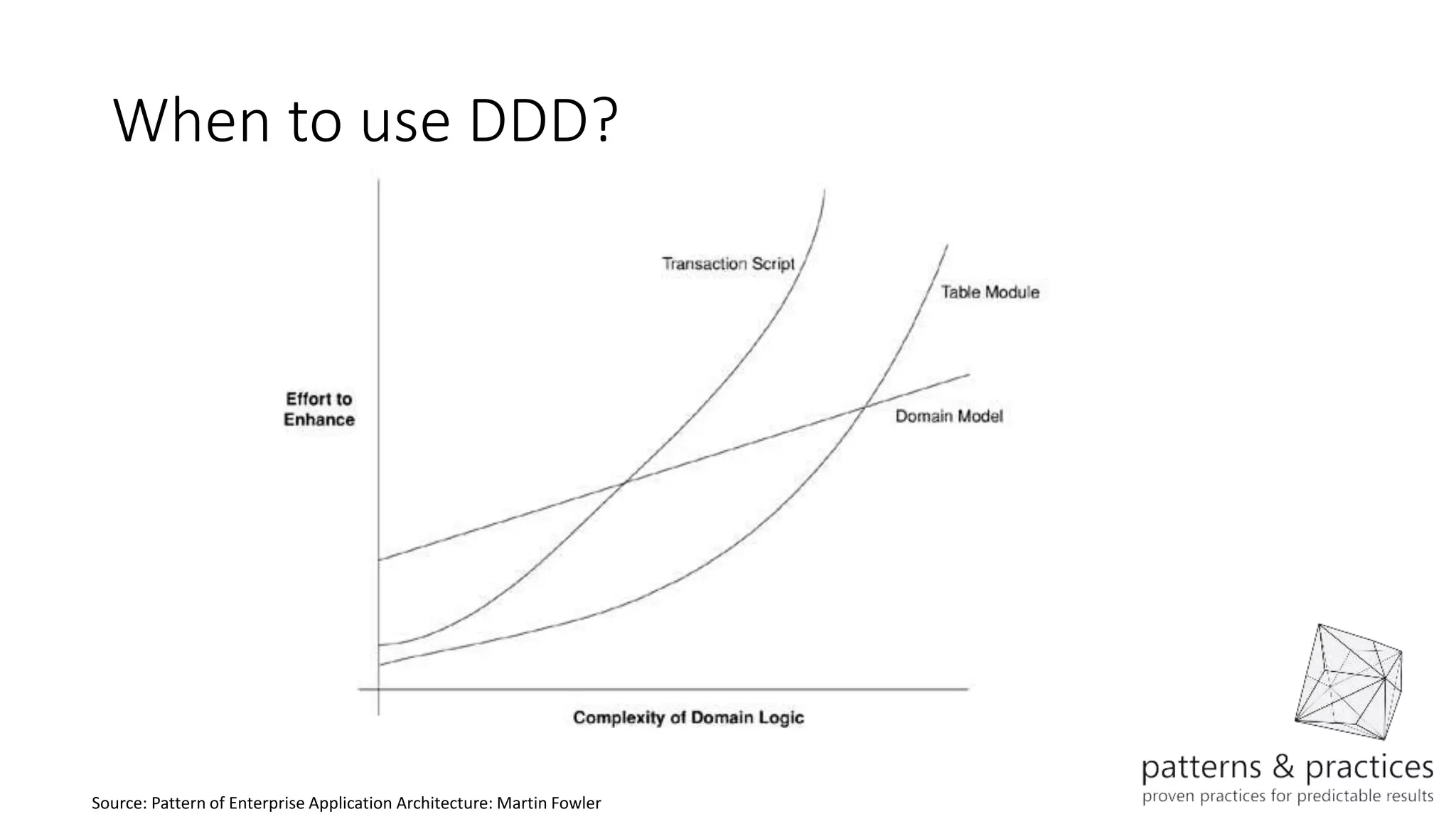
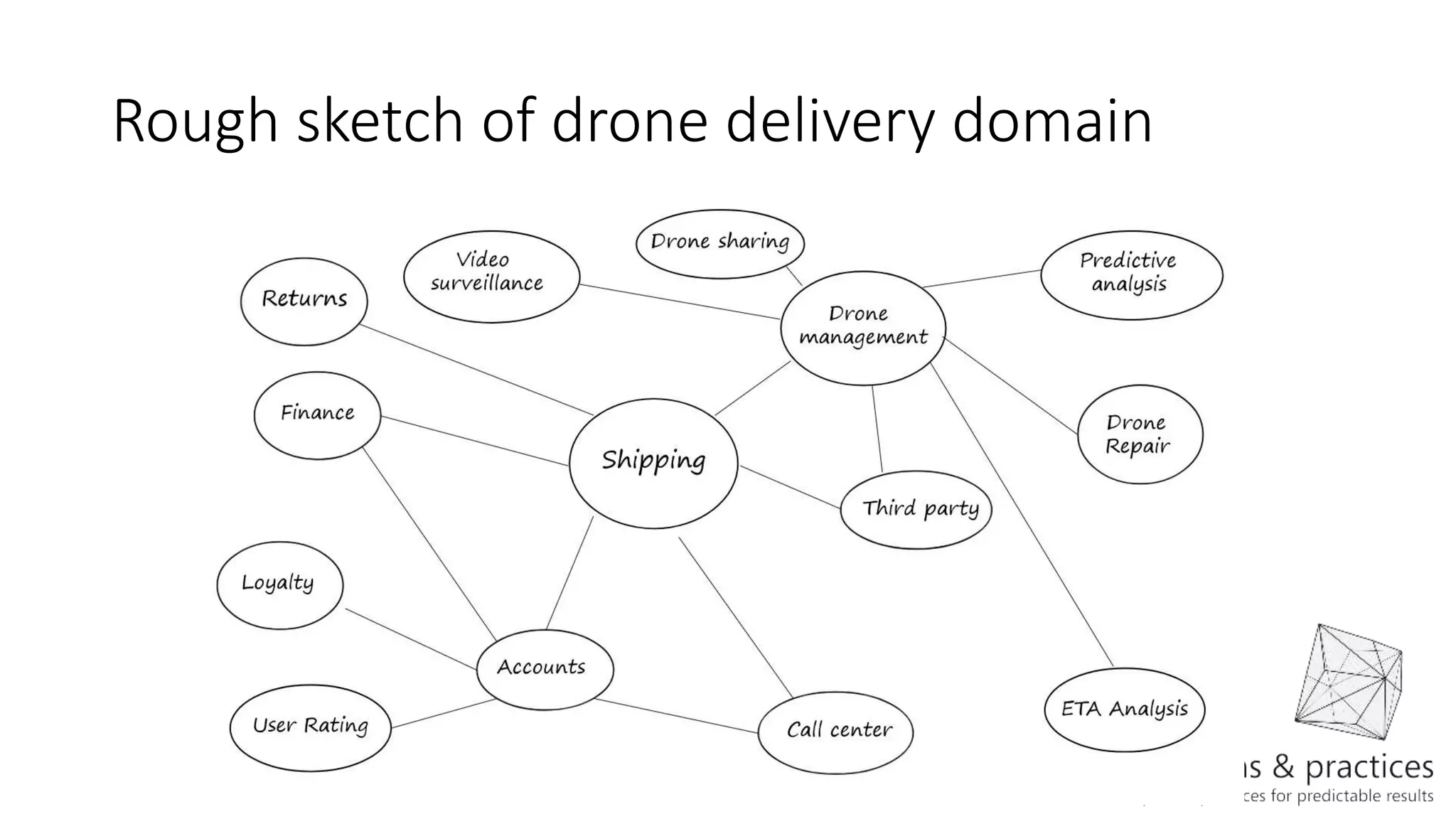
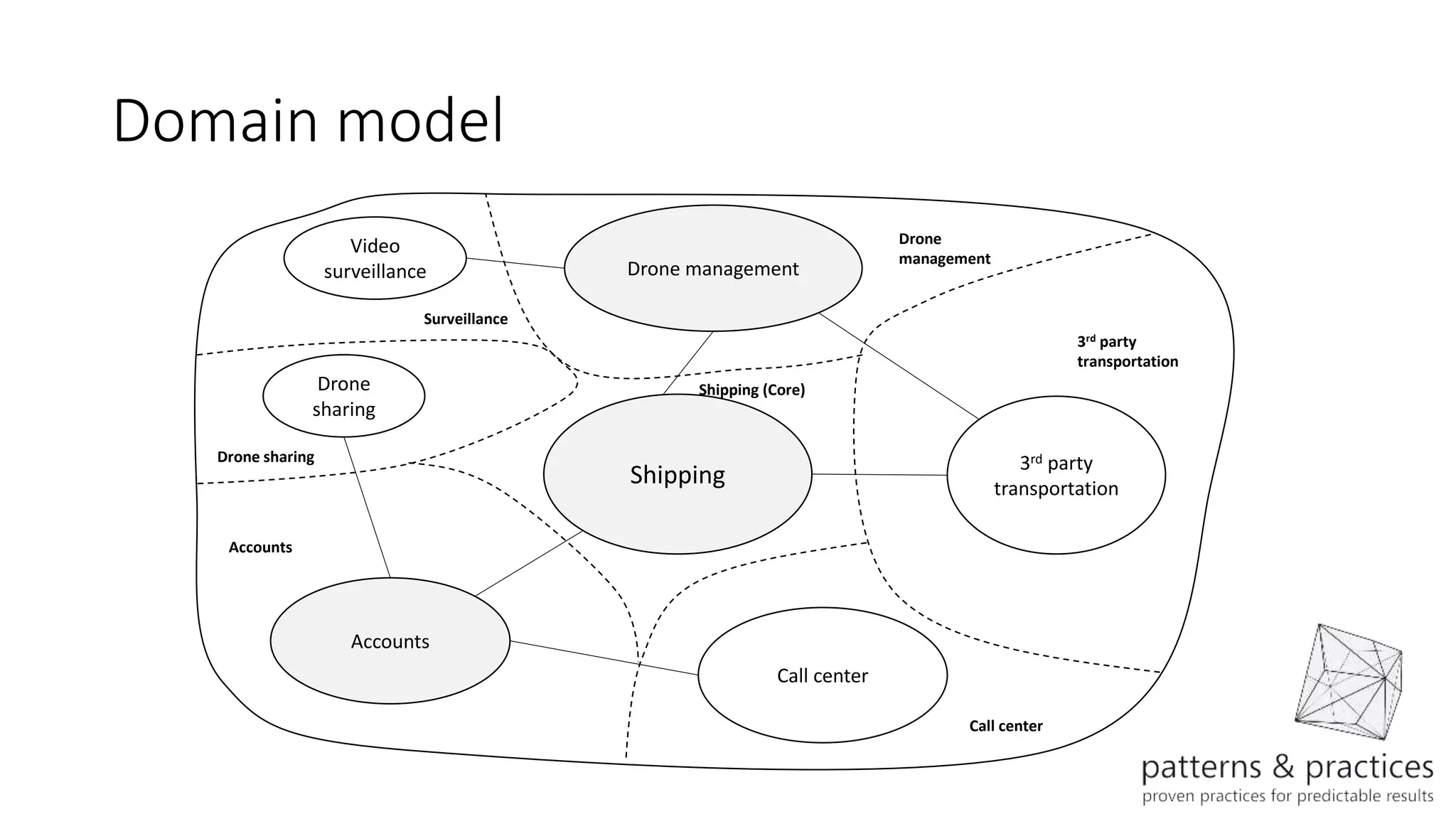
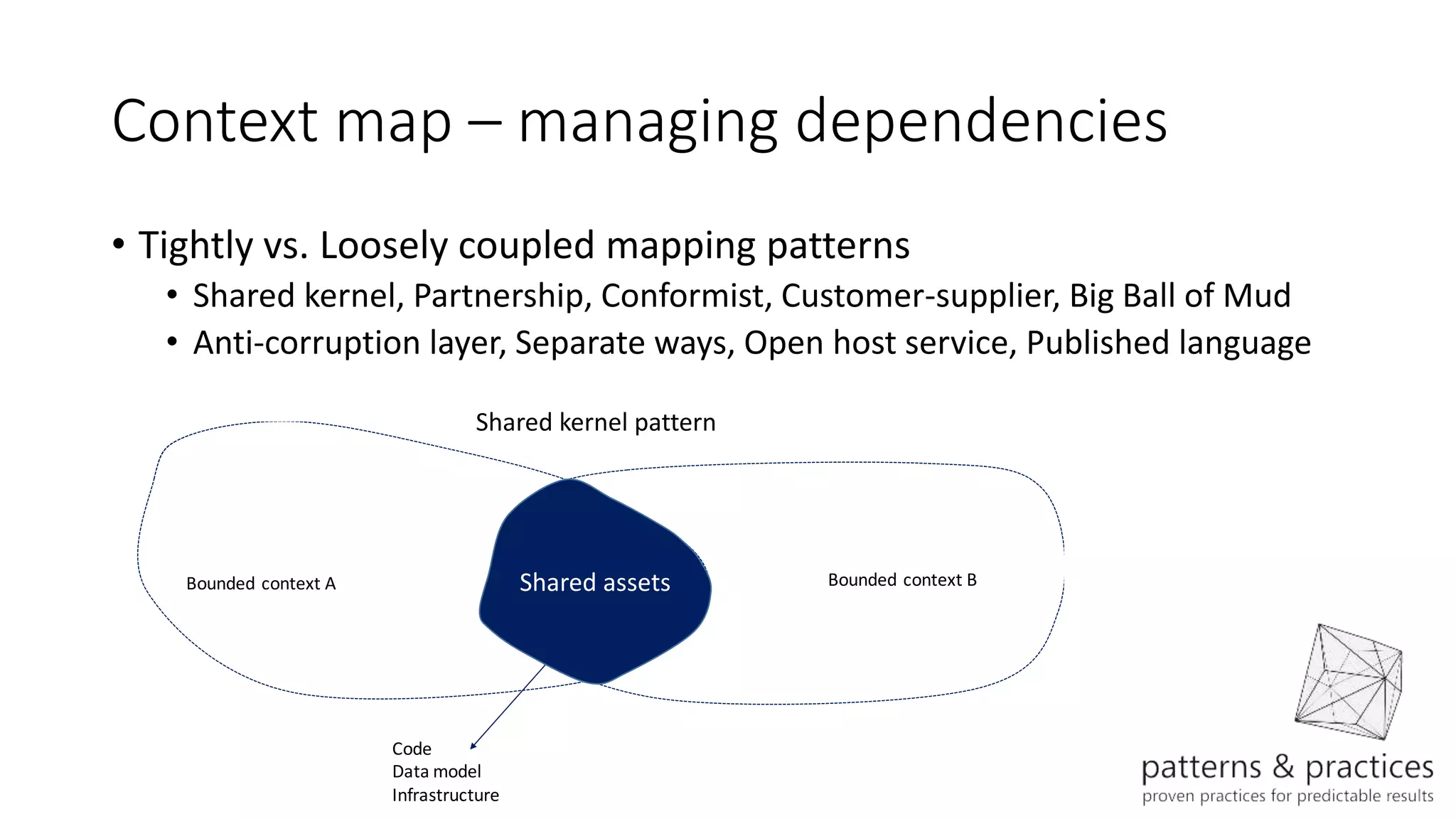
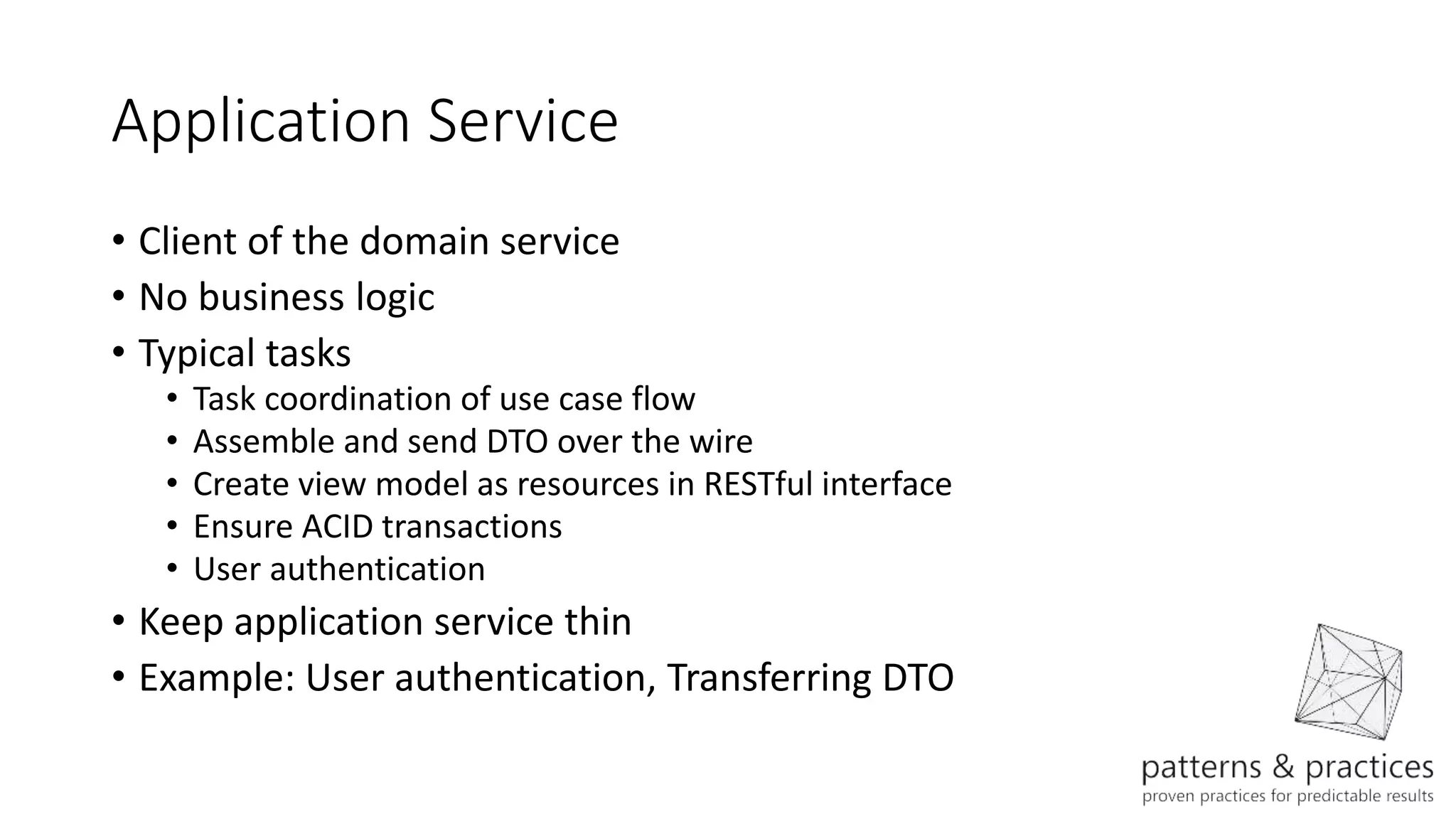
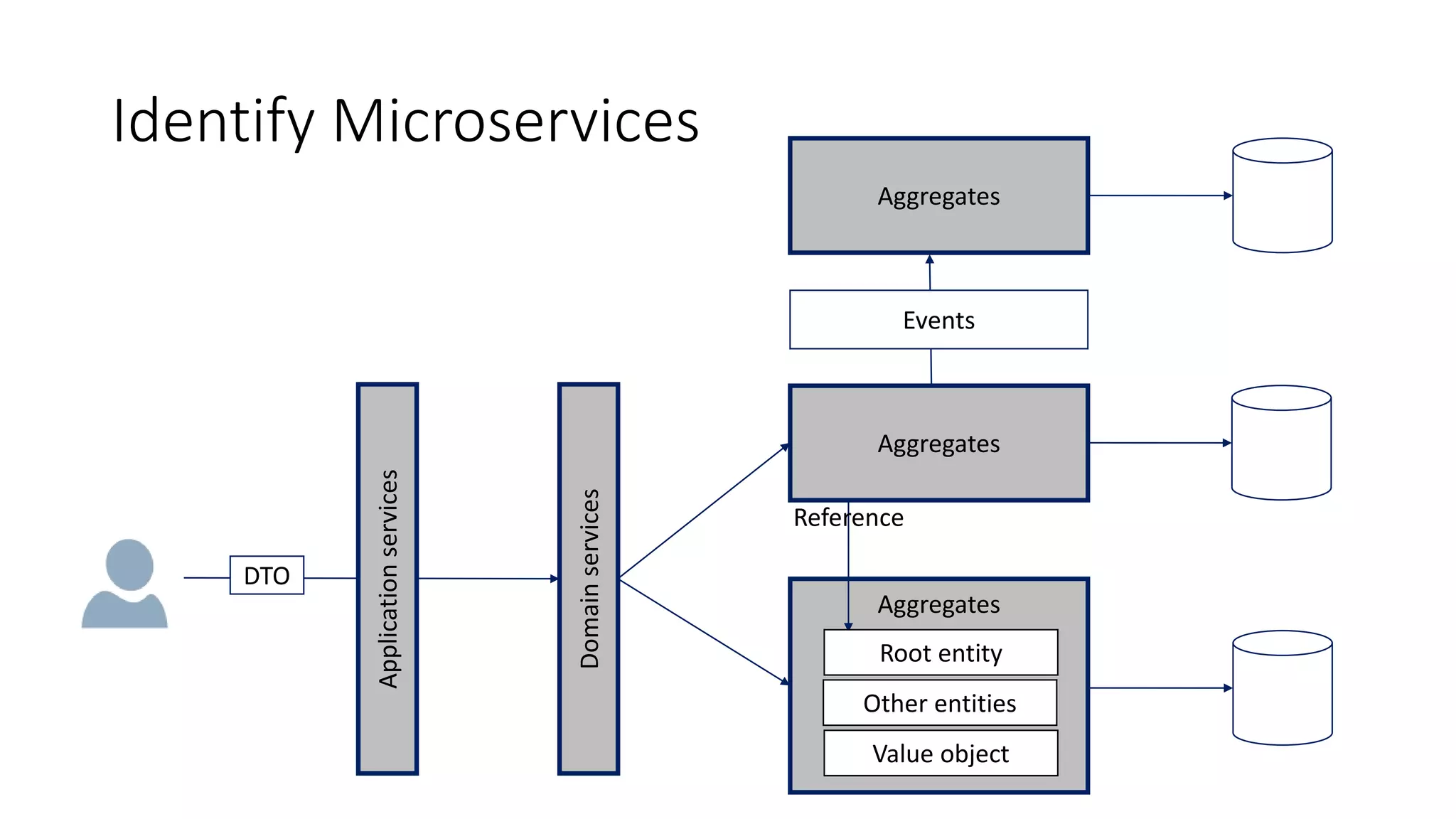
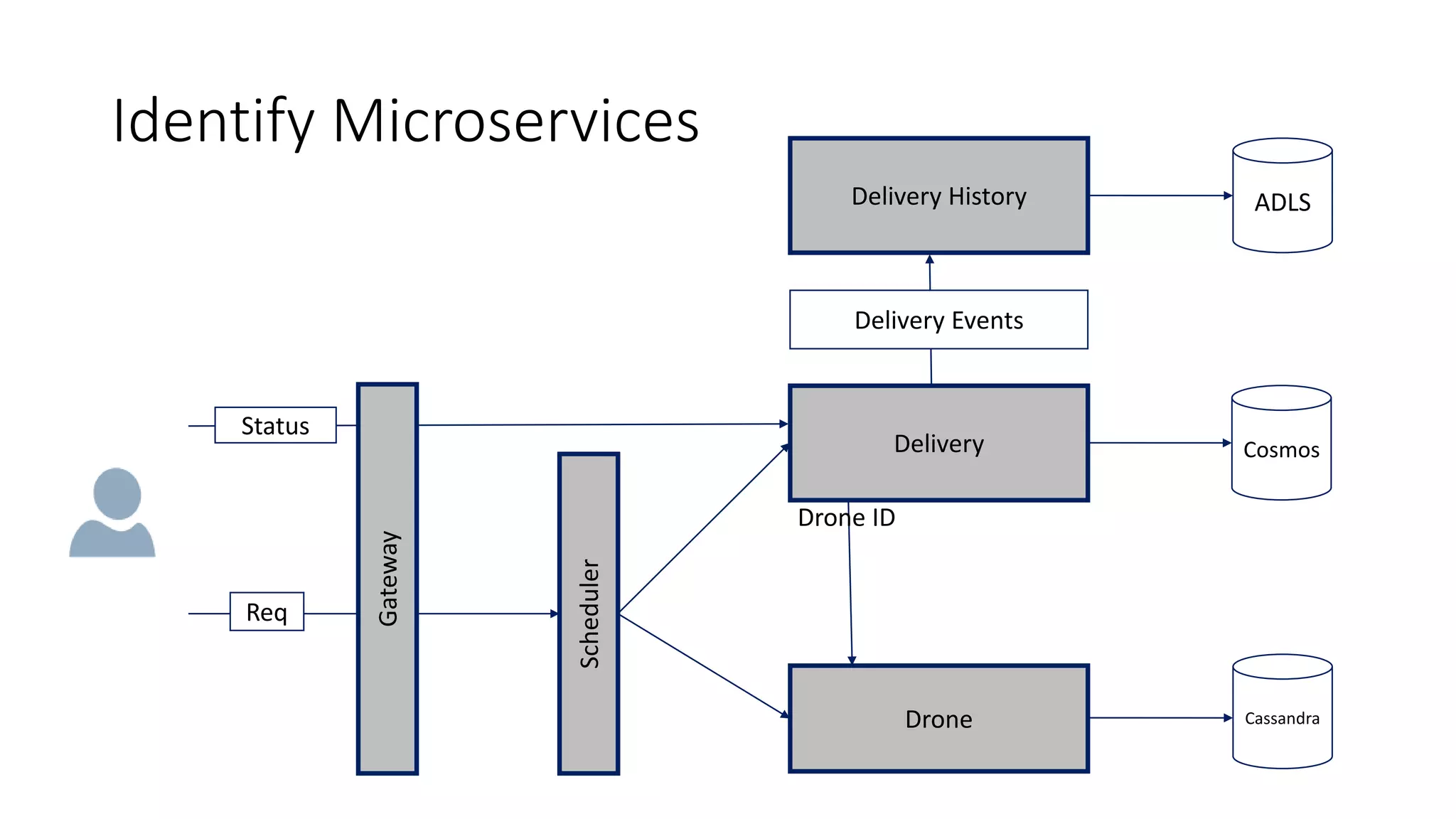
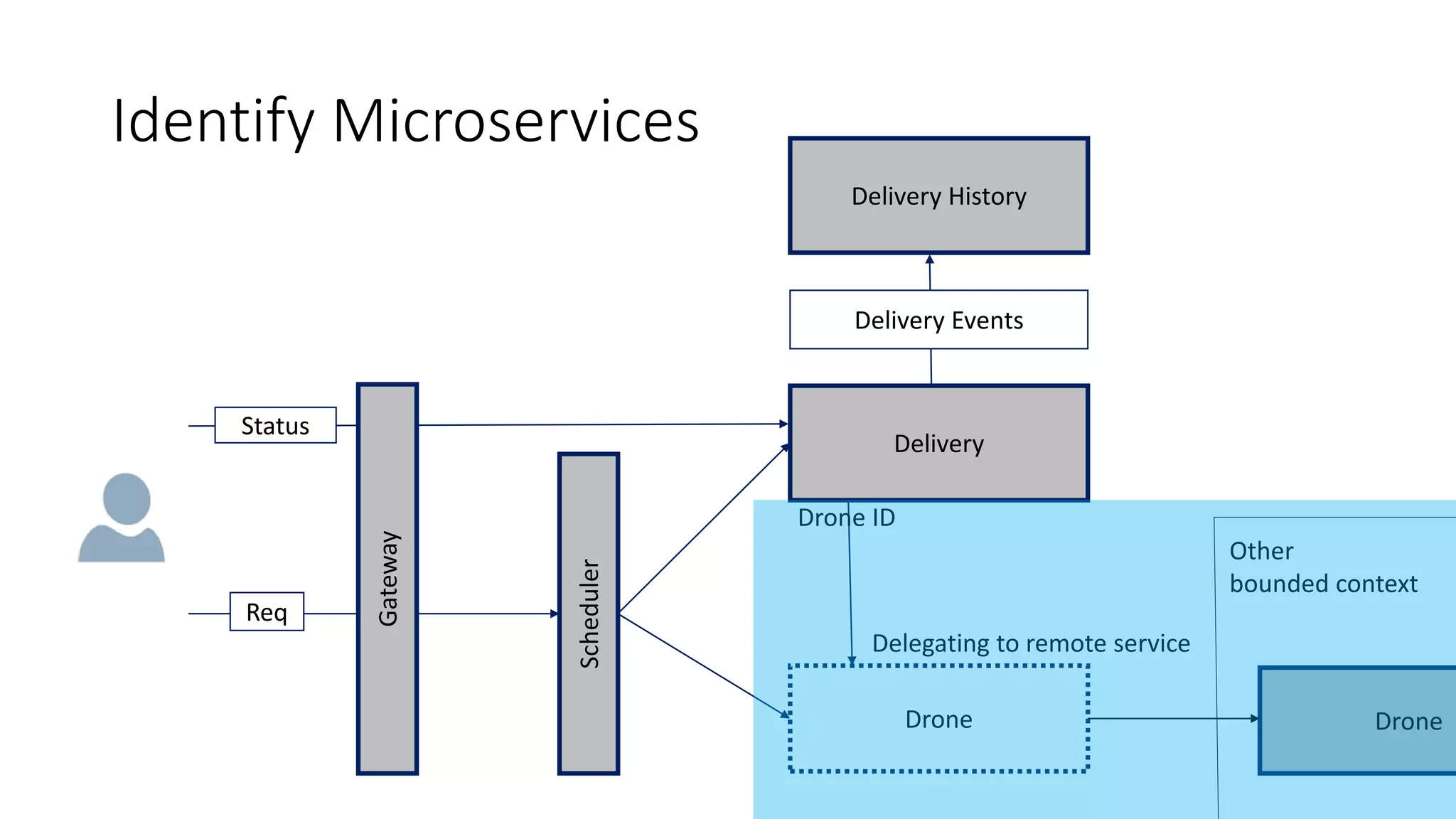
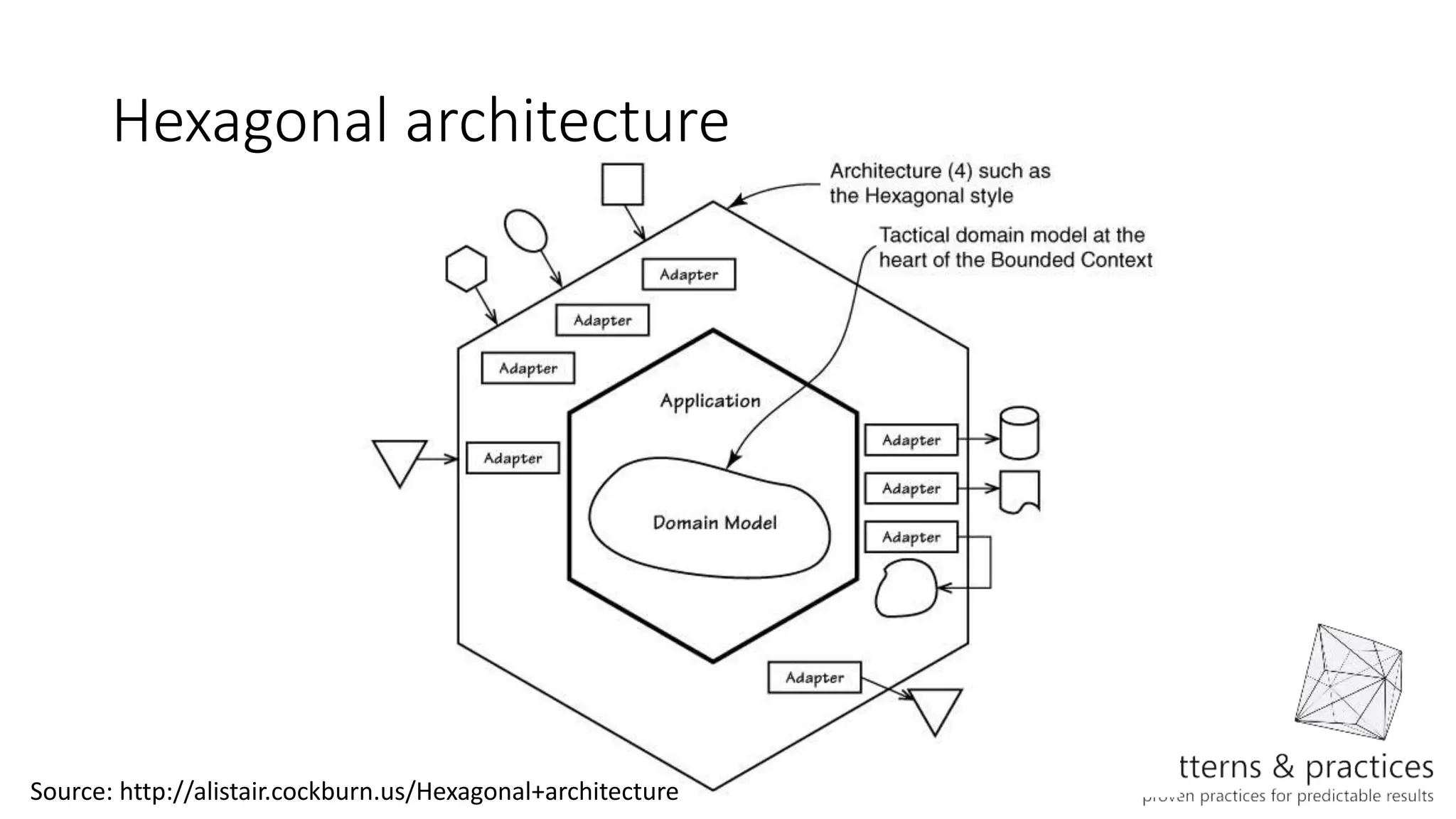
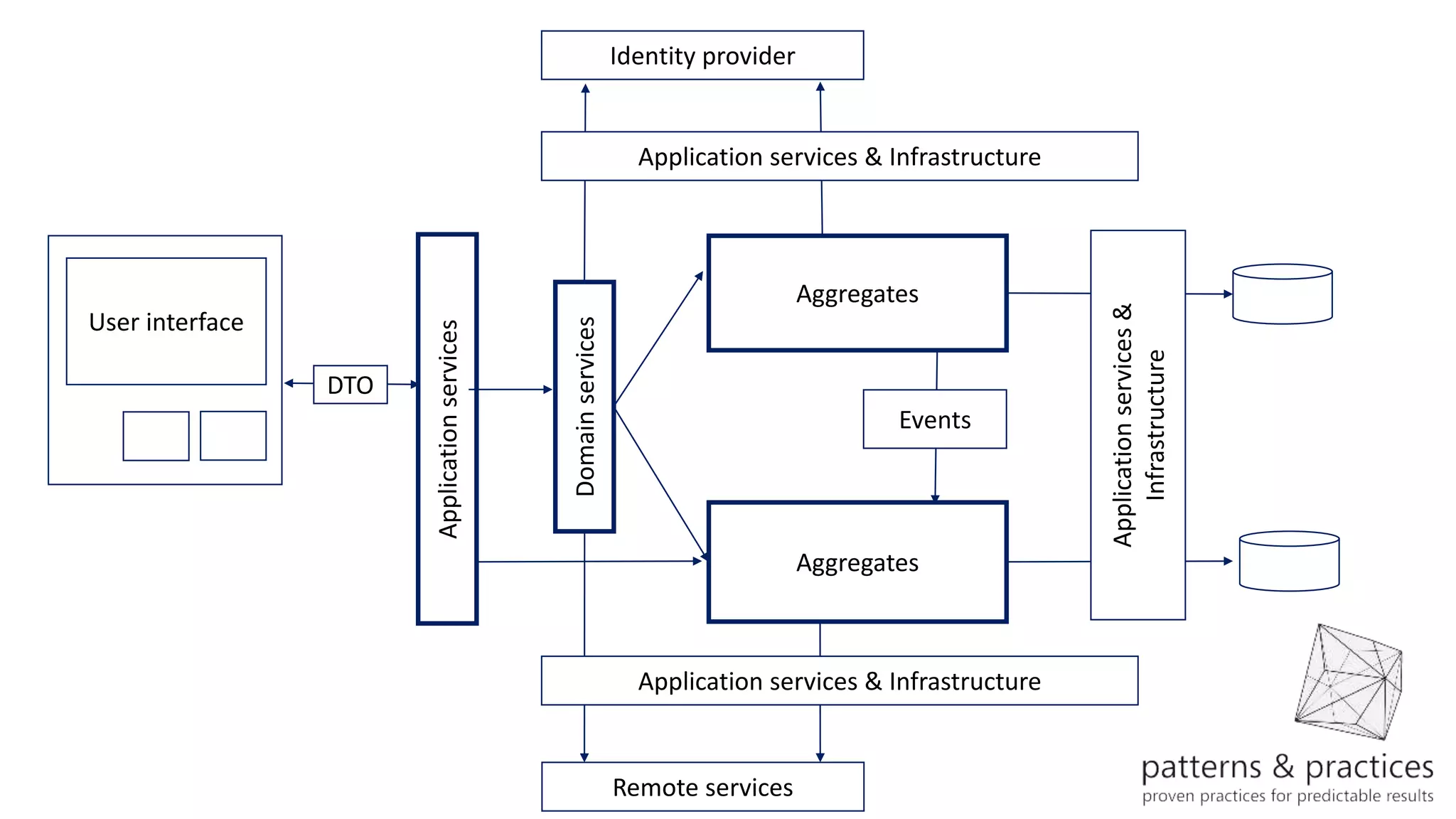
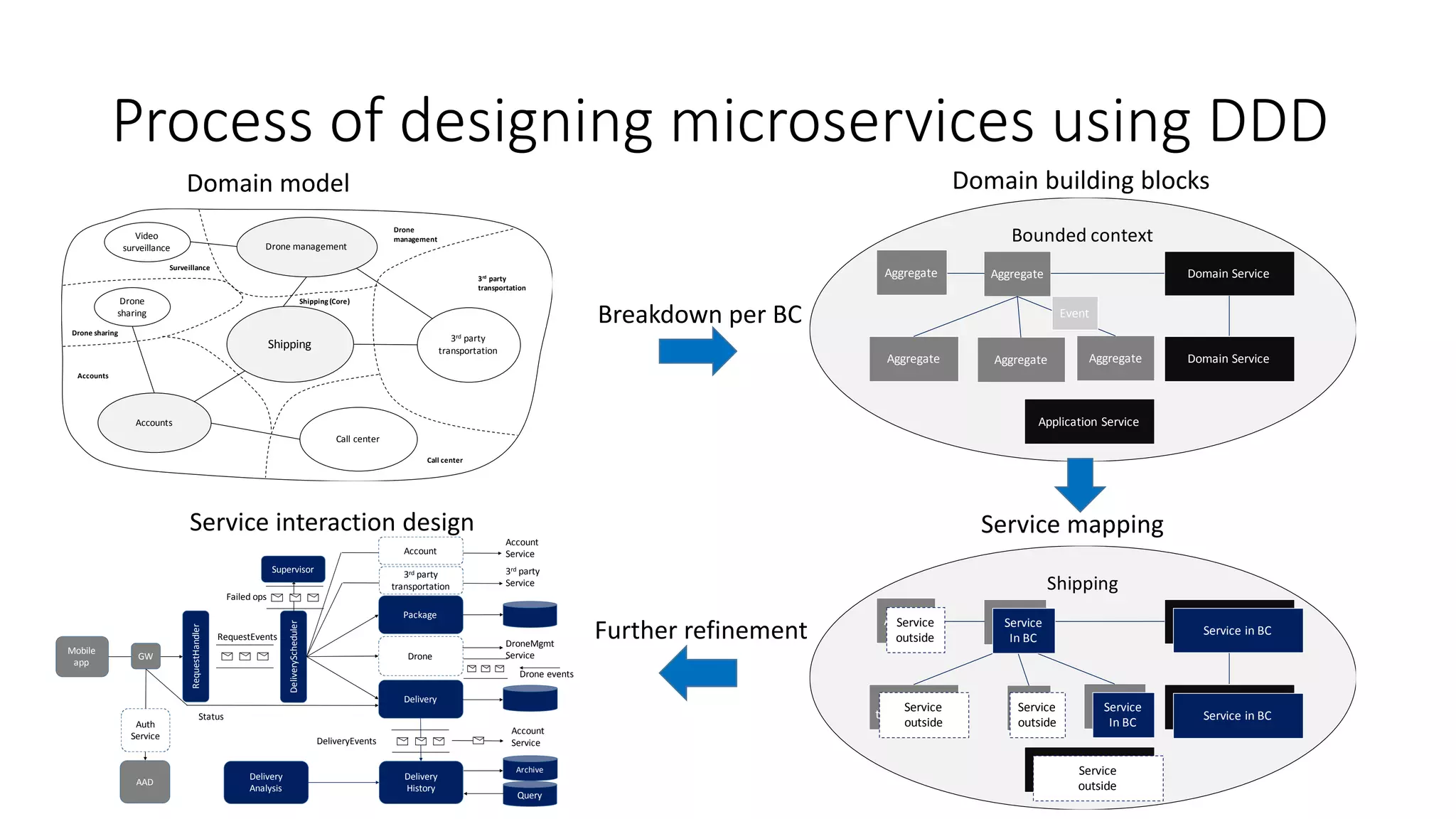
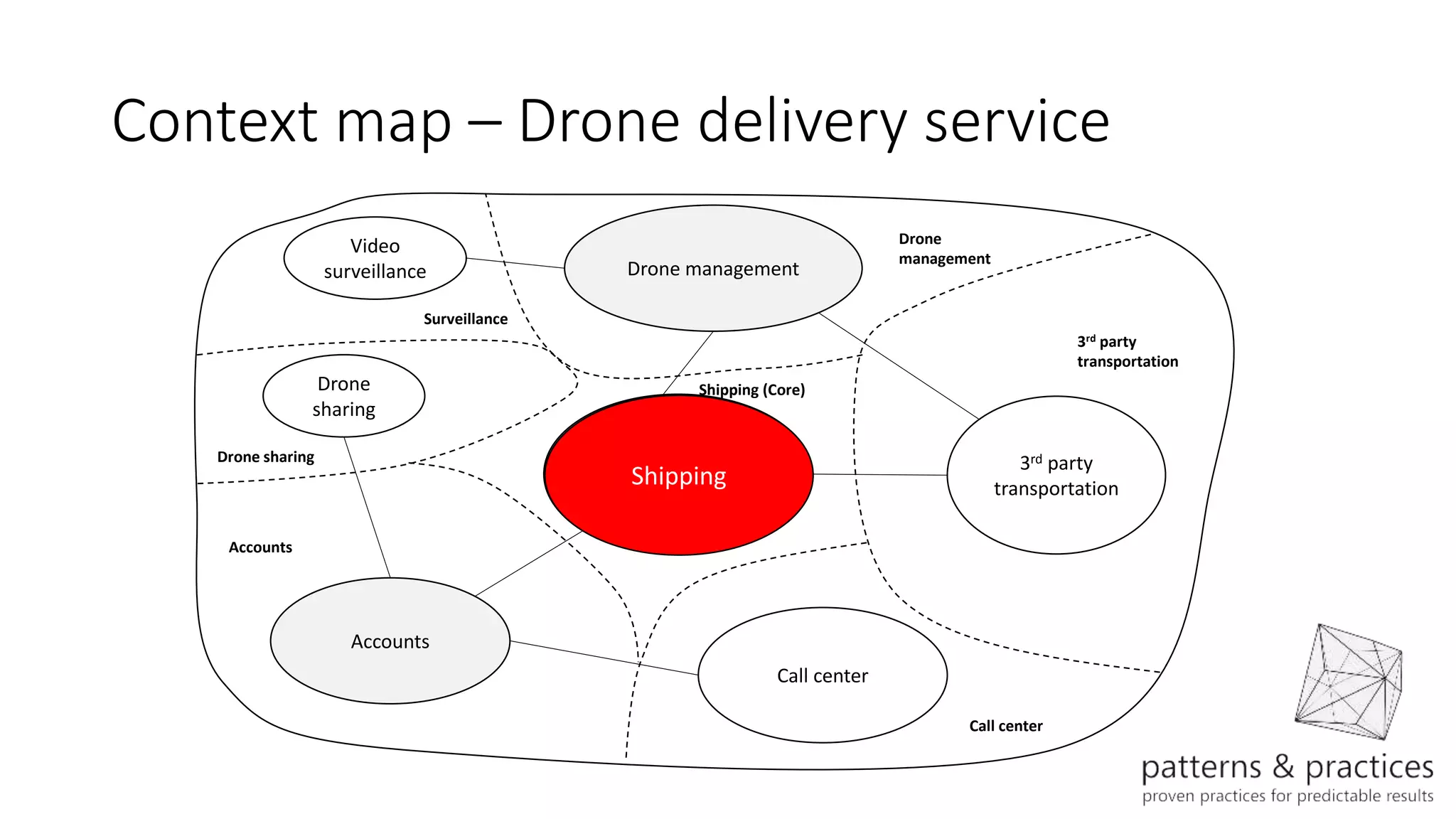
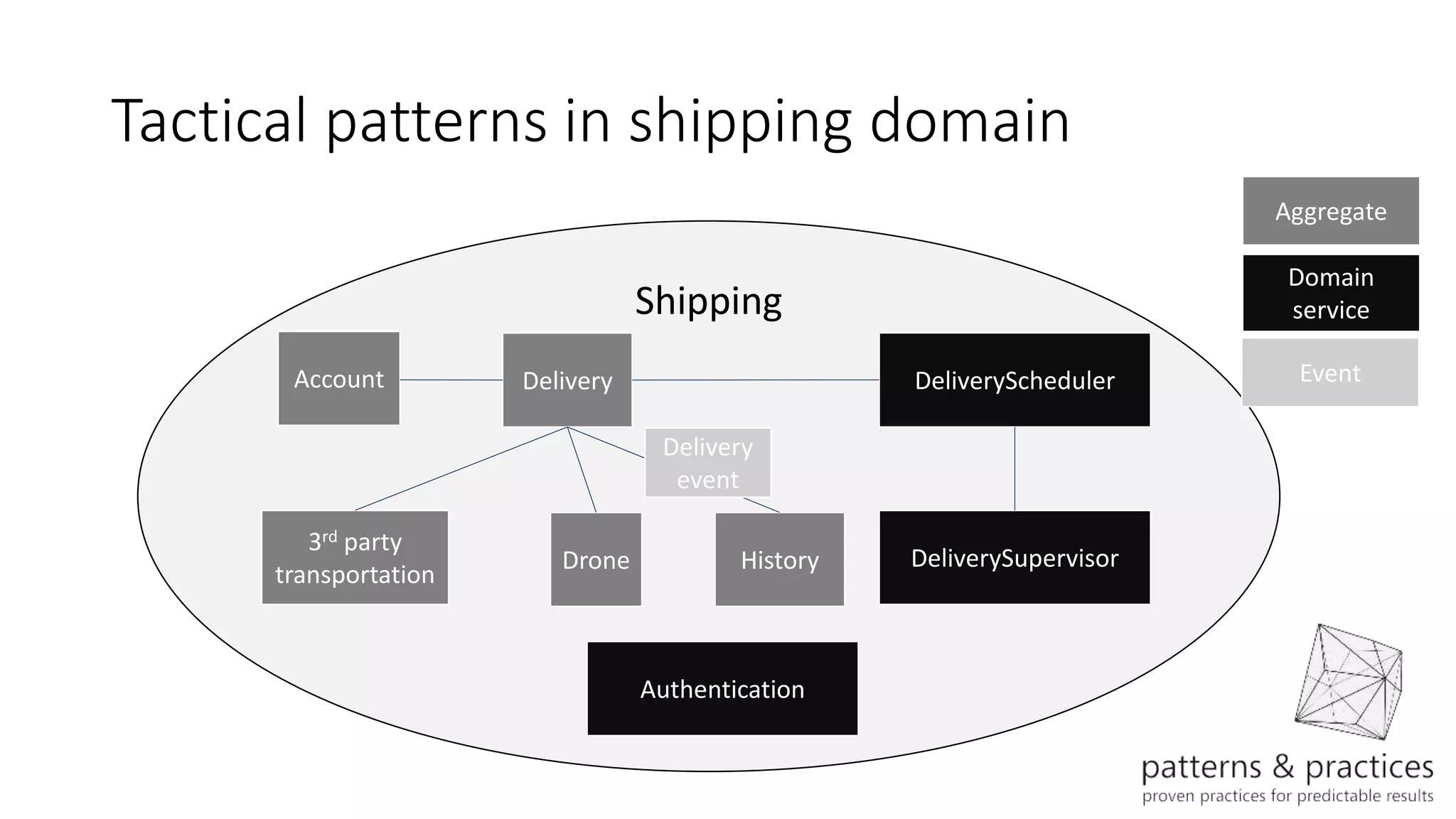
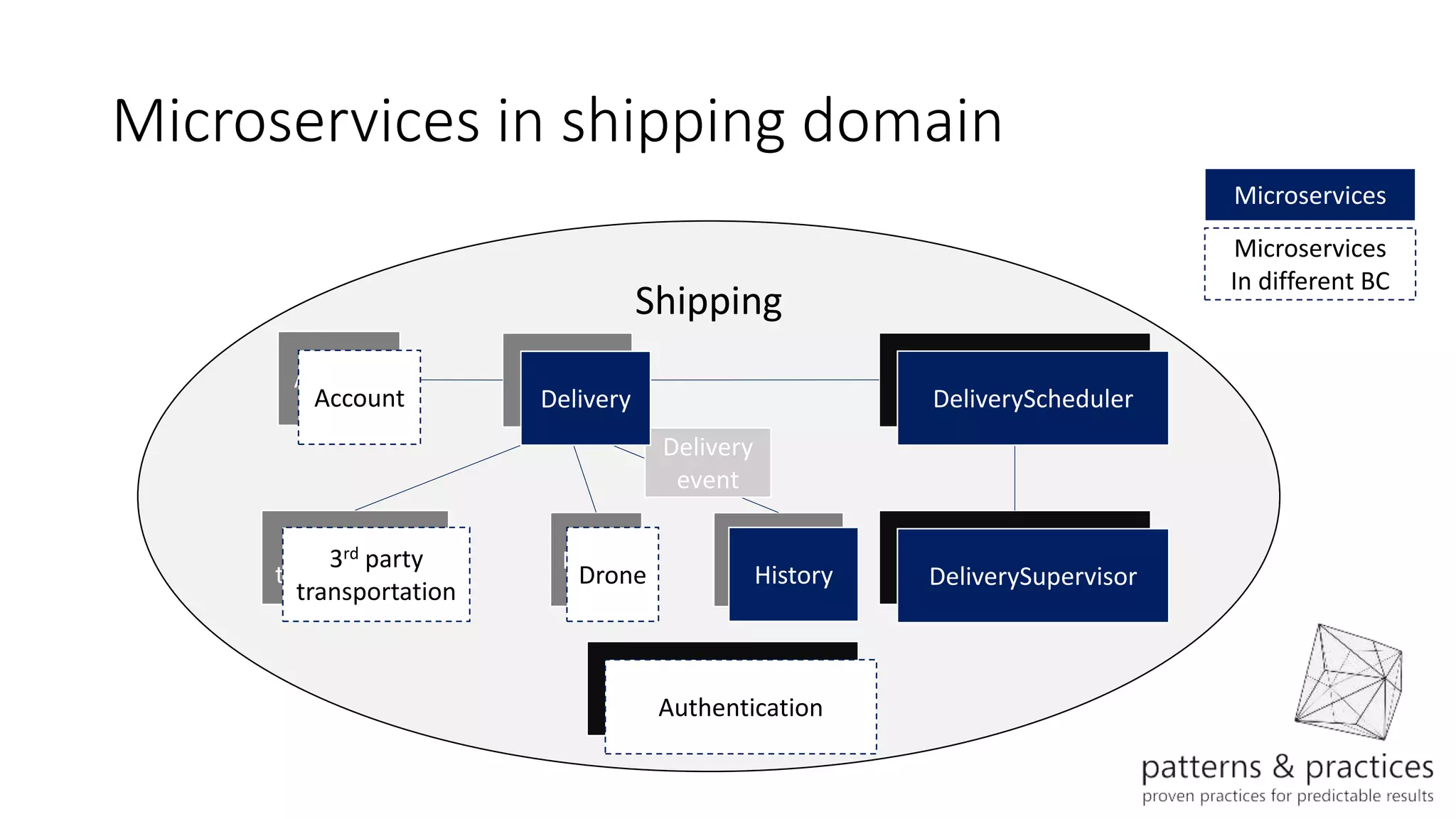
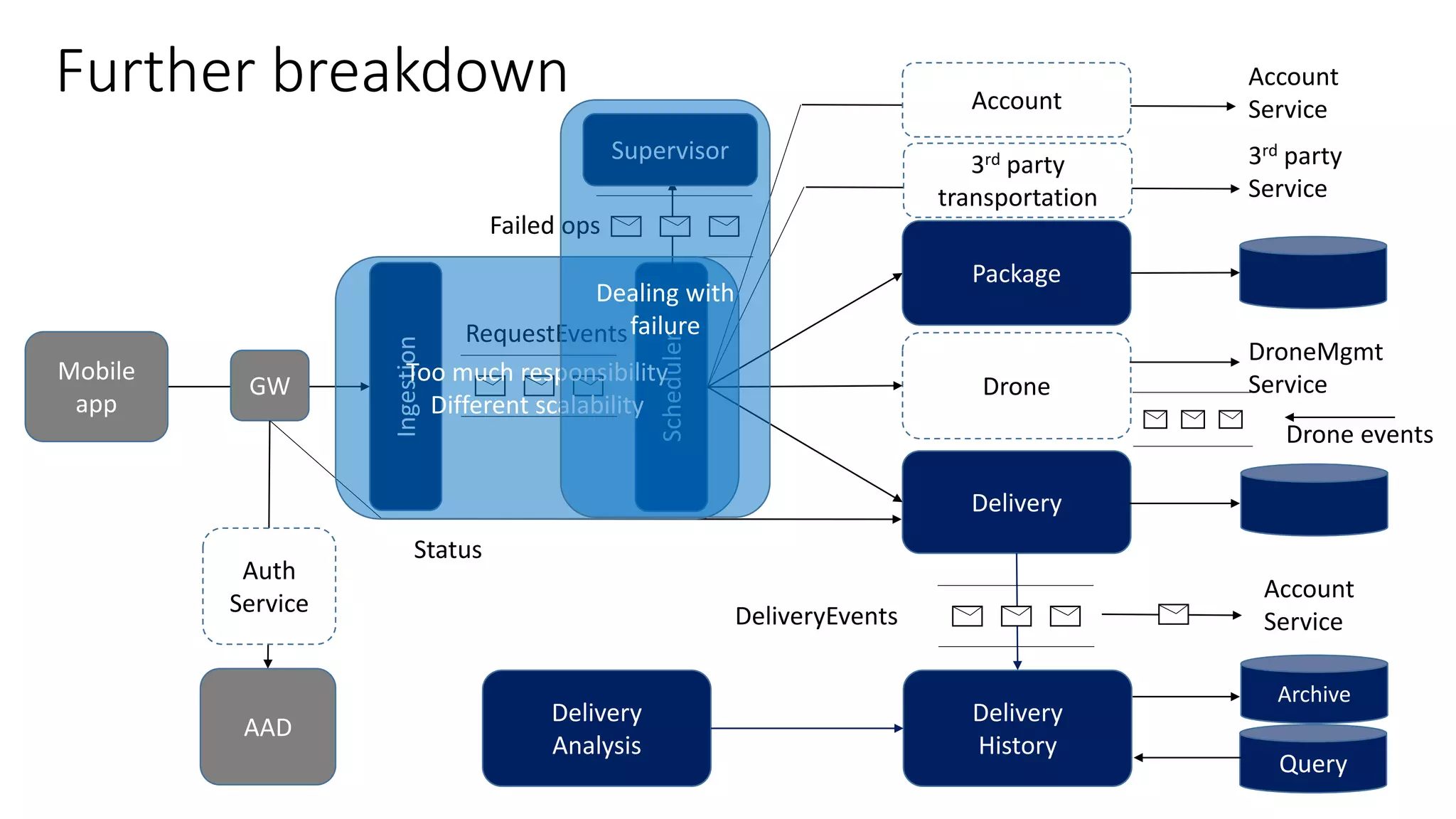
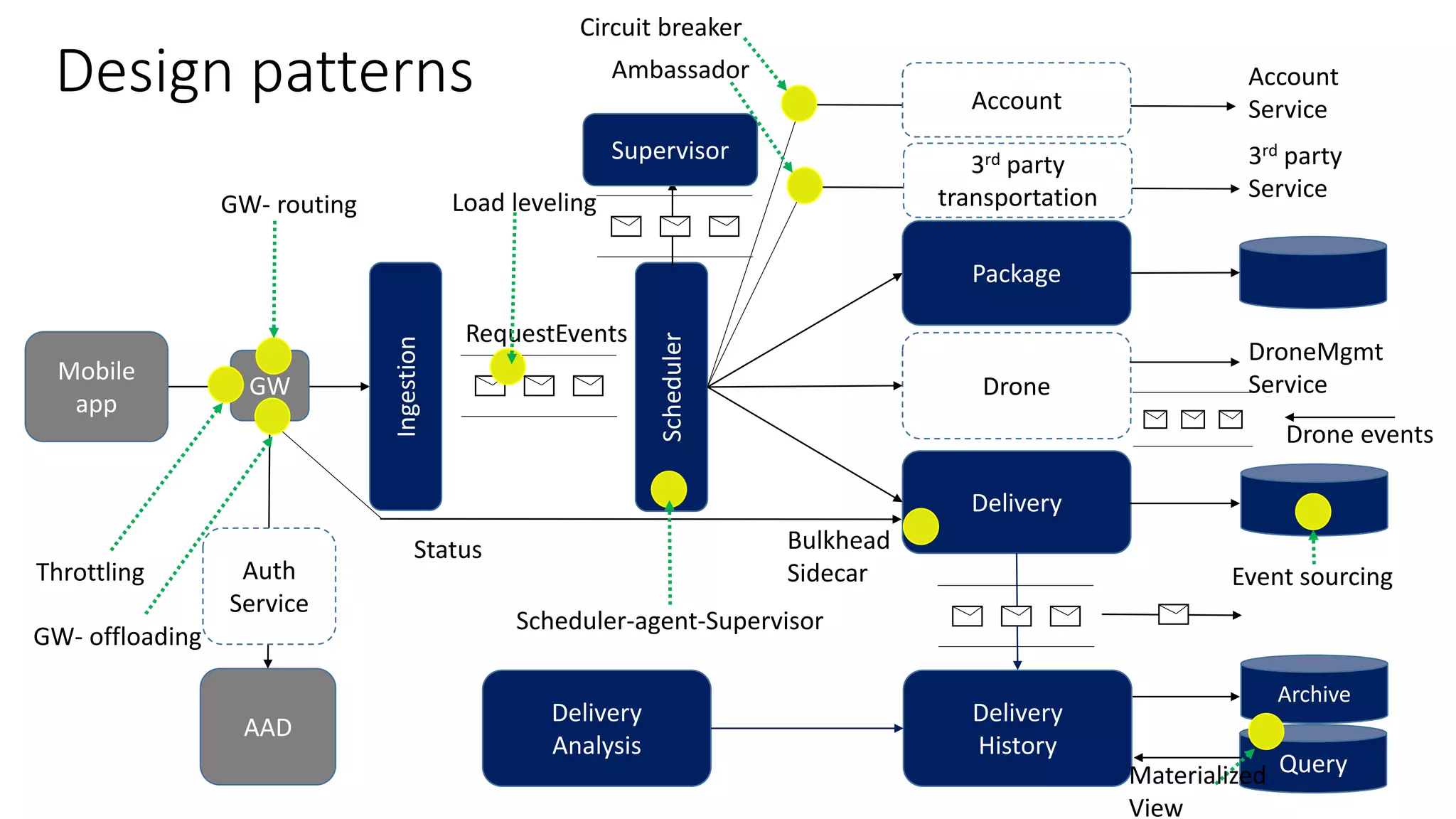
The document discusses modeling microservices using Domain-Driven Design (DDD) for a drone delivery domain. It covers DDD concepts like bounded context, tactical patterns, and identifies microservices from aggregates and domain services. It then models the drone delivery domain applying DDD, identifying bounded contexts, domain model, and refining them into microservices for the shipping bounded context.