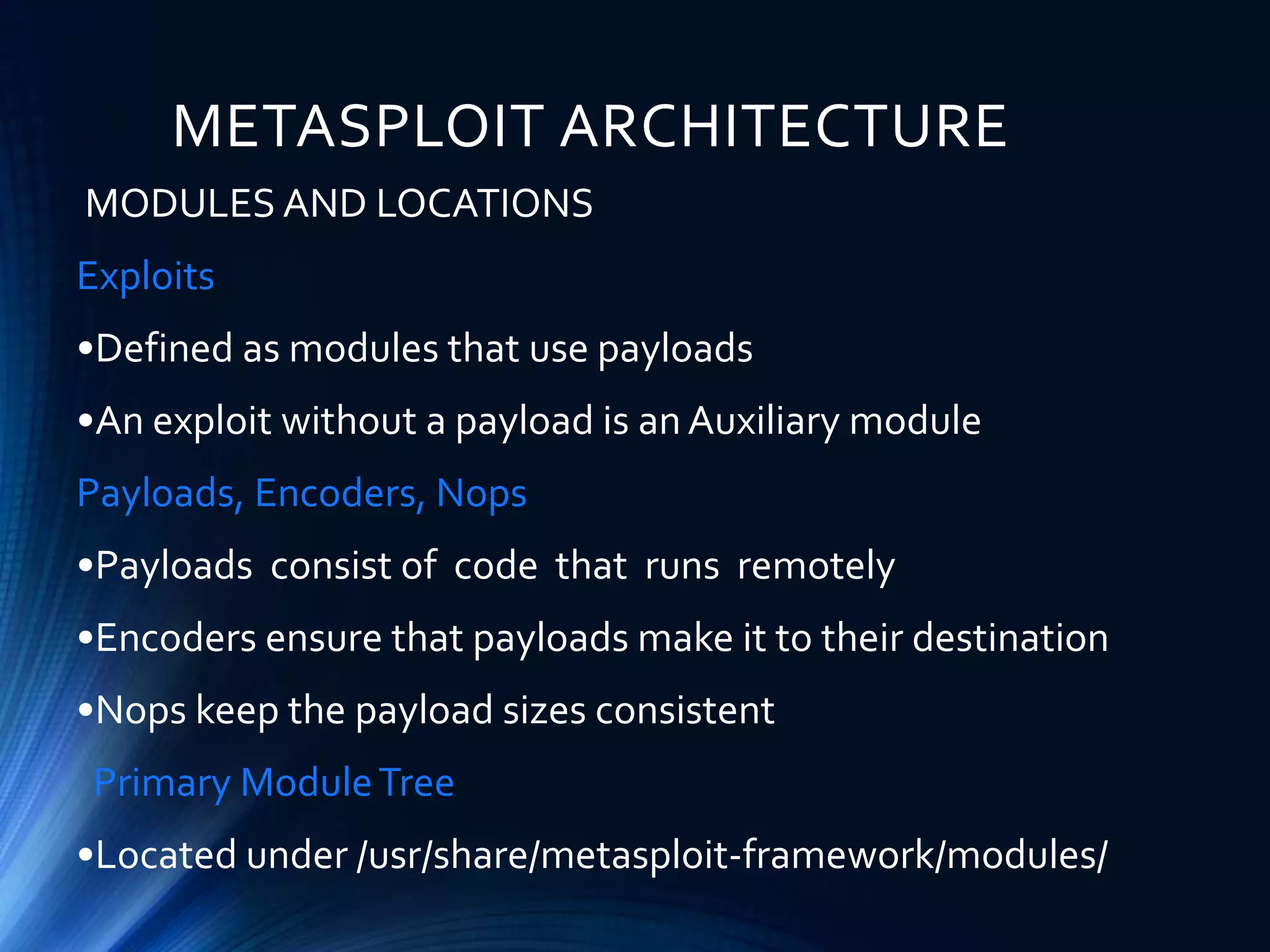
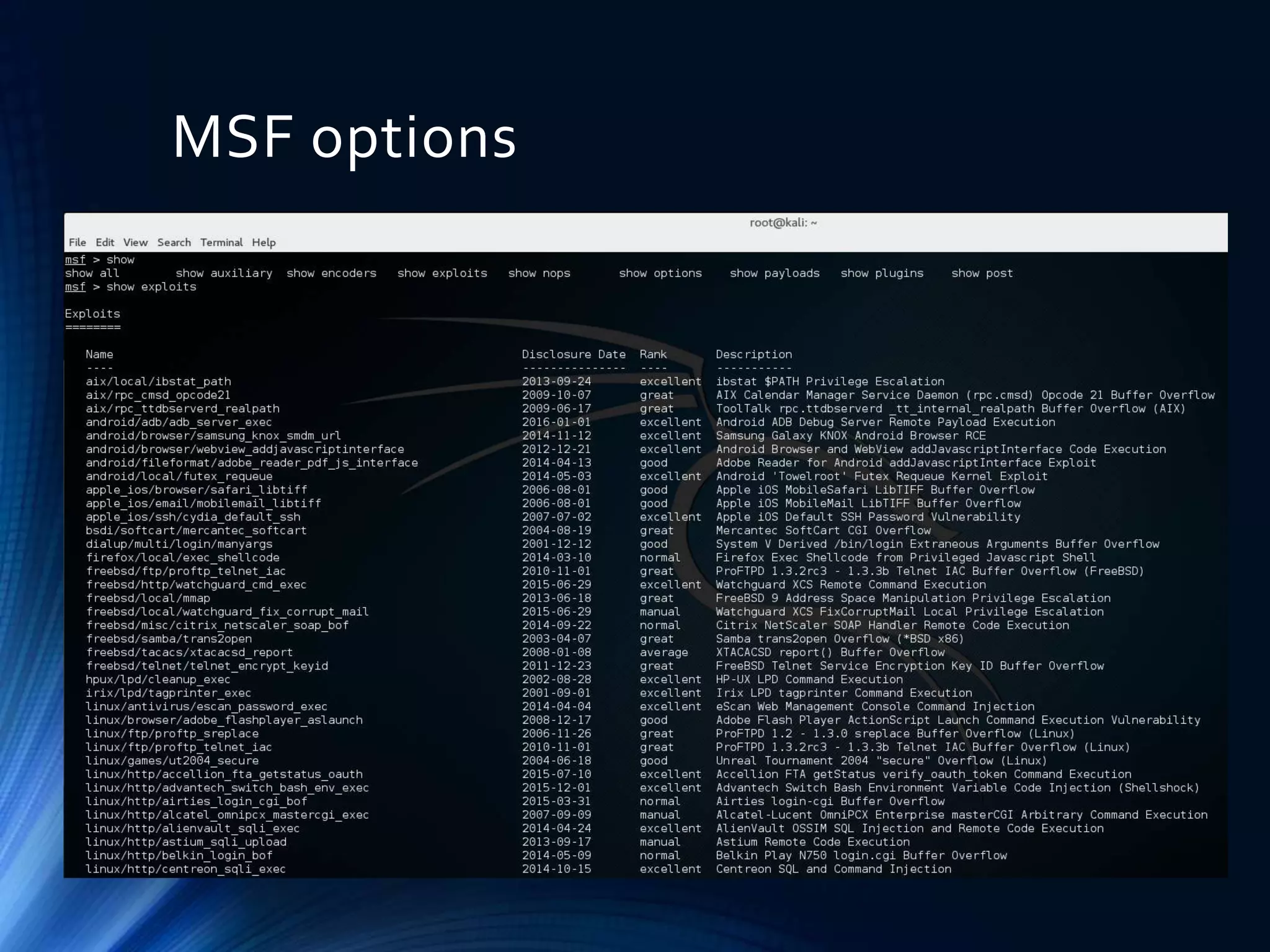
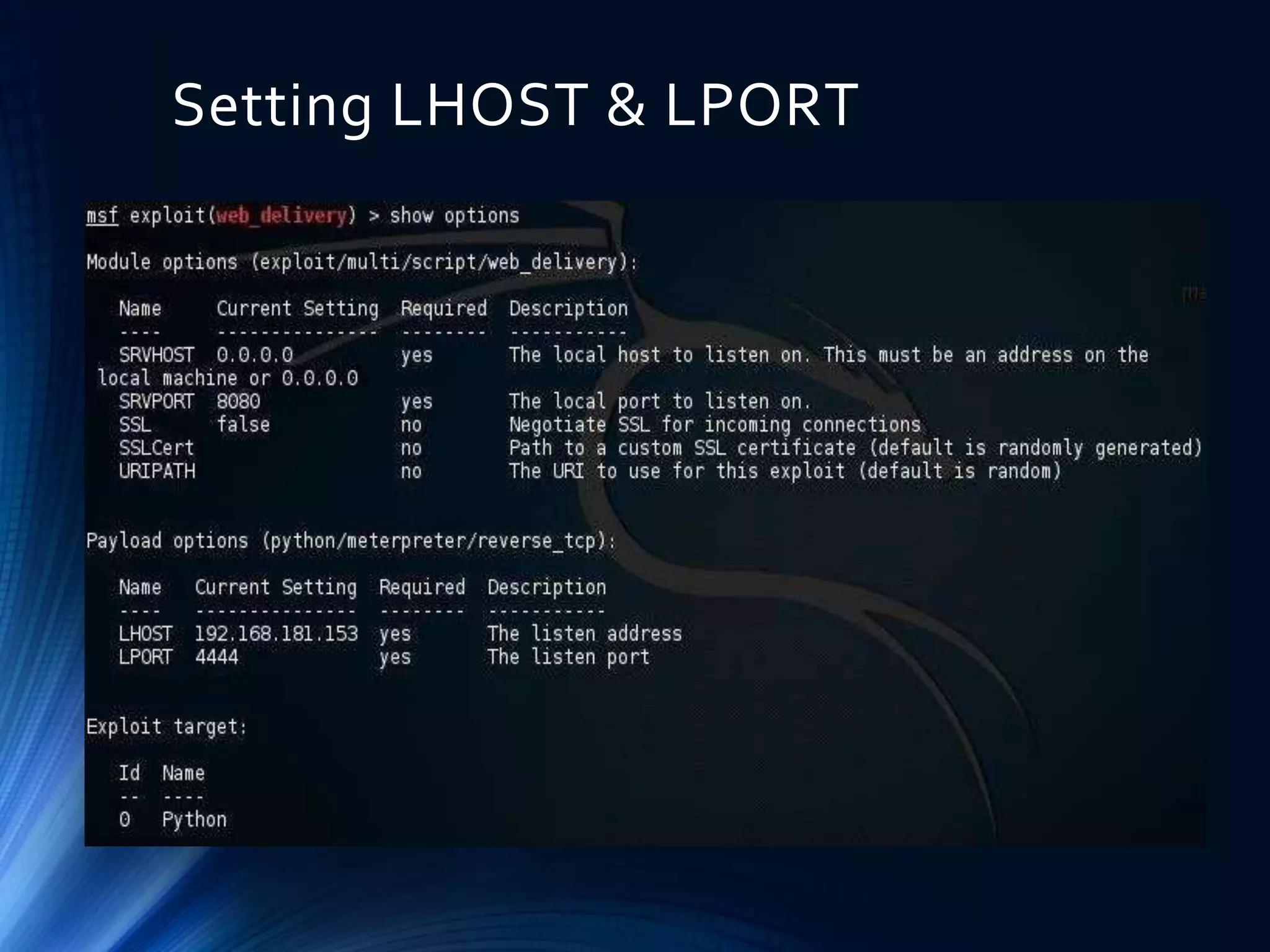
Metasploit is an open source framework for penetration testing that allows users to perform vulnerability scanning, exploit development, and post-exploitation. It provides tools for information gathering, vulnerability scanning, pre-exploitation and post-exploitation tasks. Metasploit has modules for exploits and payloads that are used together, with payloads being the code executed on the target and encoders ensuring payloads reach their destination. The msfconsole interface provides centralized access to Metasploit's options like finding vulnerabilities through open ports and setting the listener, payload, and target for exploitation. Meterpreter is an advanced payload included in Metasploit that has additional features for tasks like keylogging and taking screenshots.