My Youtube Channel:-
https://www.youtube.com/channel/UCTSeqoJEf28oJB7cqfkq7ZQ
This presentation explains how to implement secure user authentication in a Node.js and Express backend using JSON Web Tokens (JWT) and MongoDB as the database.
It covers the complete authentication workflow, from user registration and password hashing to token generation and route protection.
Key topics include:
Understanding Authentication vs Authorization
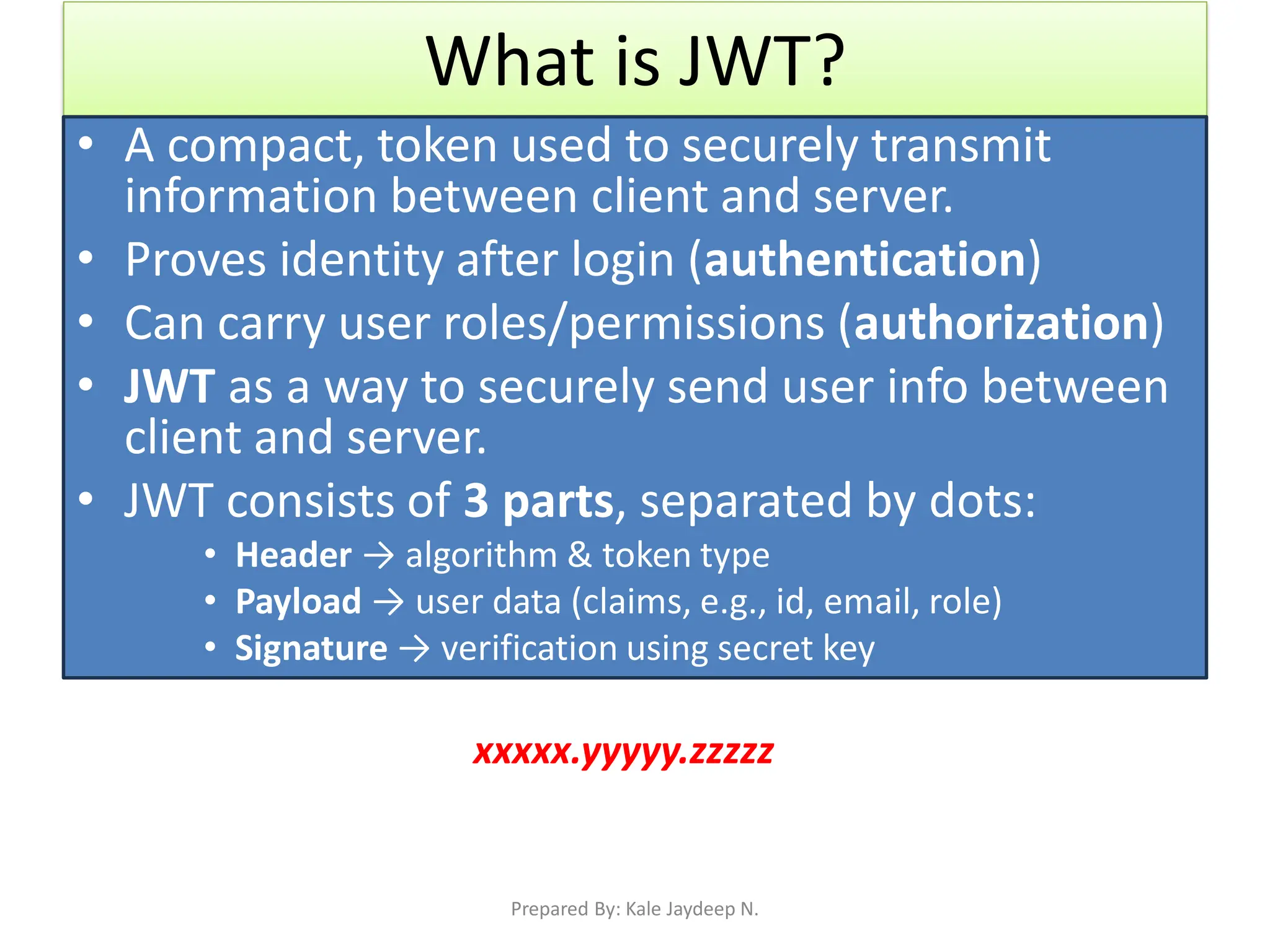
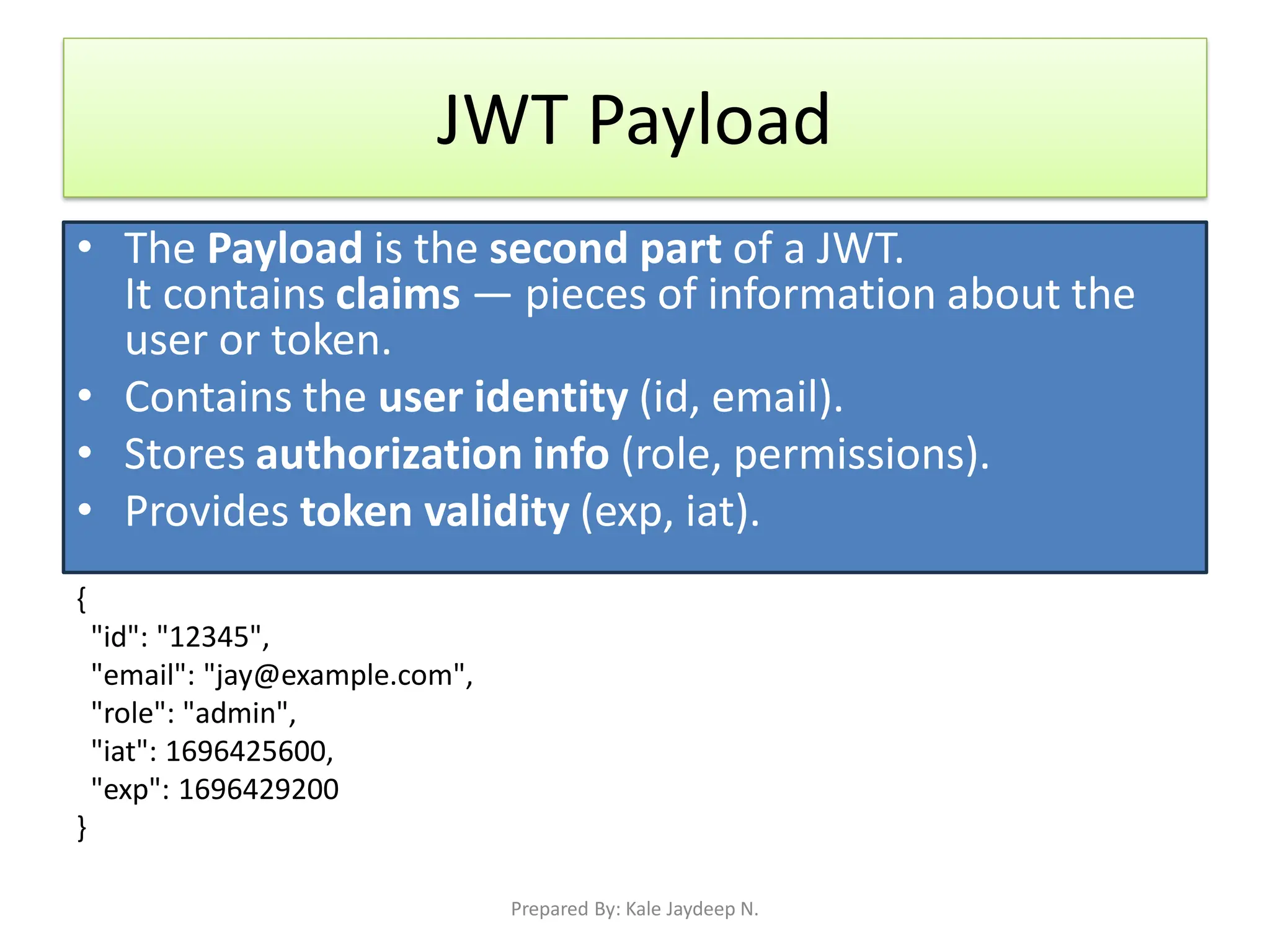
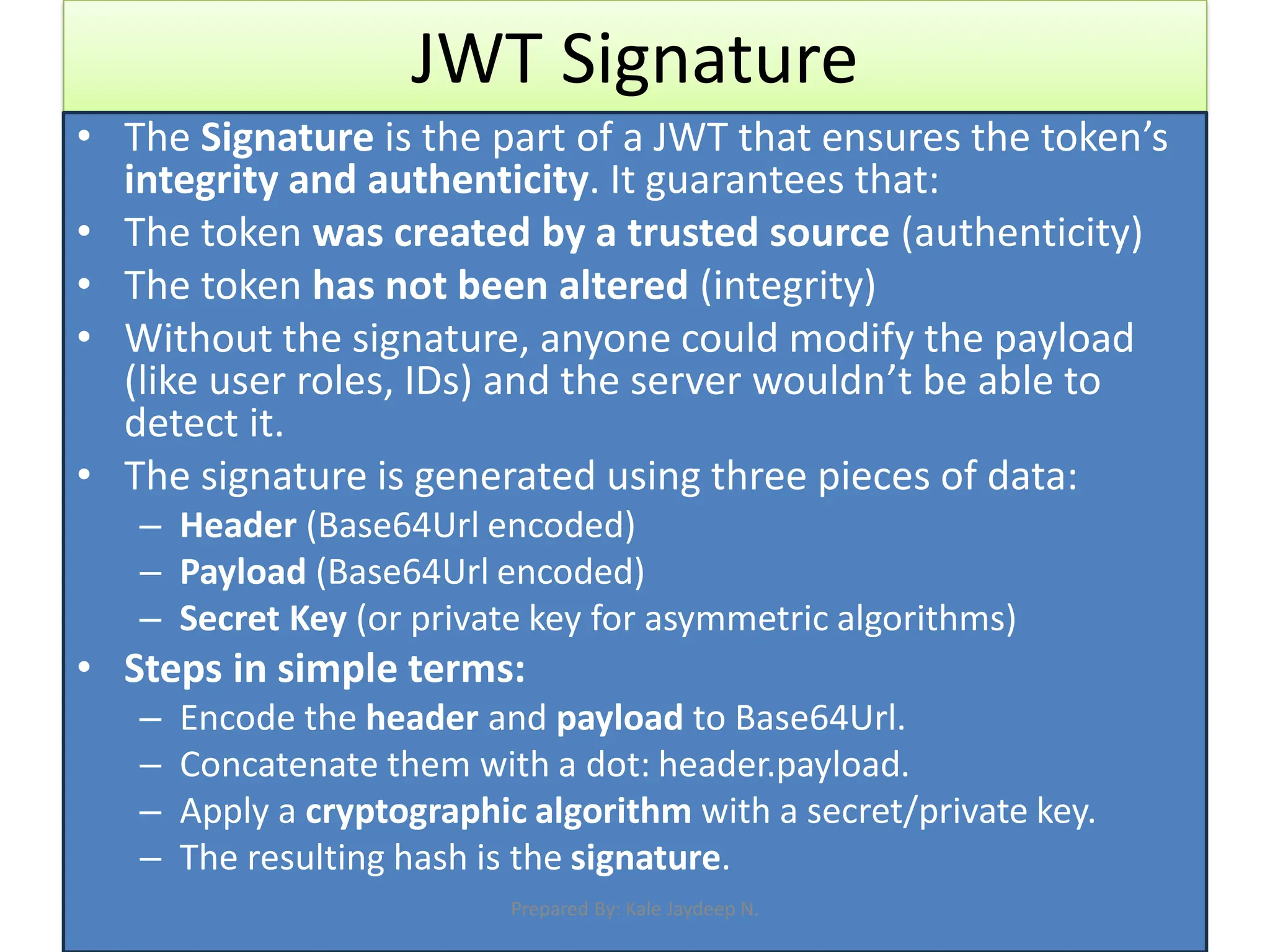
What is JWT and how it works (Header, Payload, Signature)
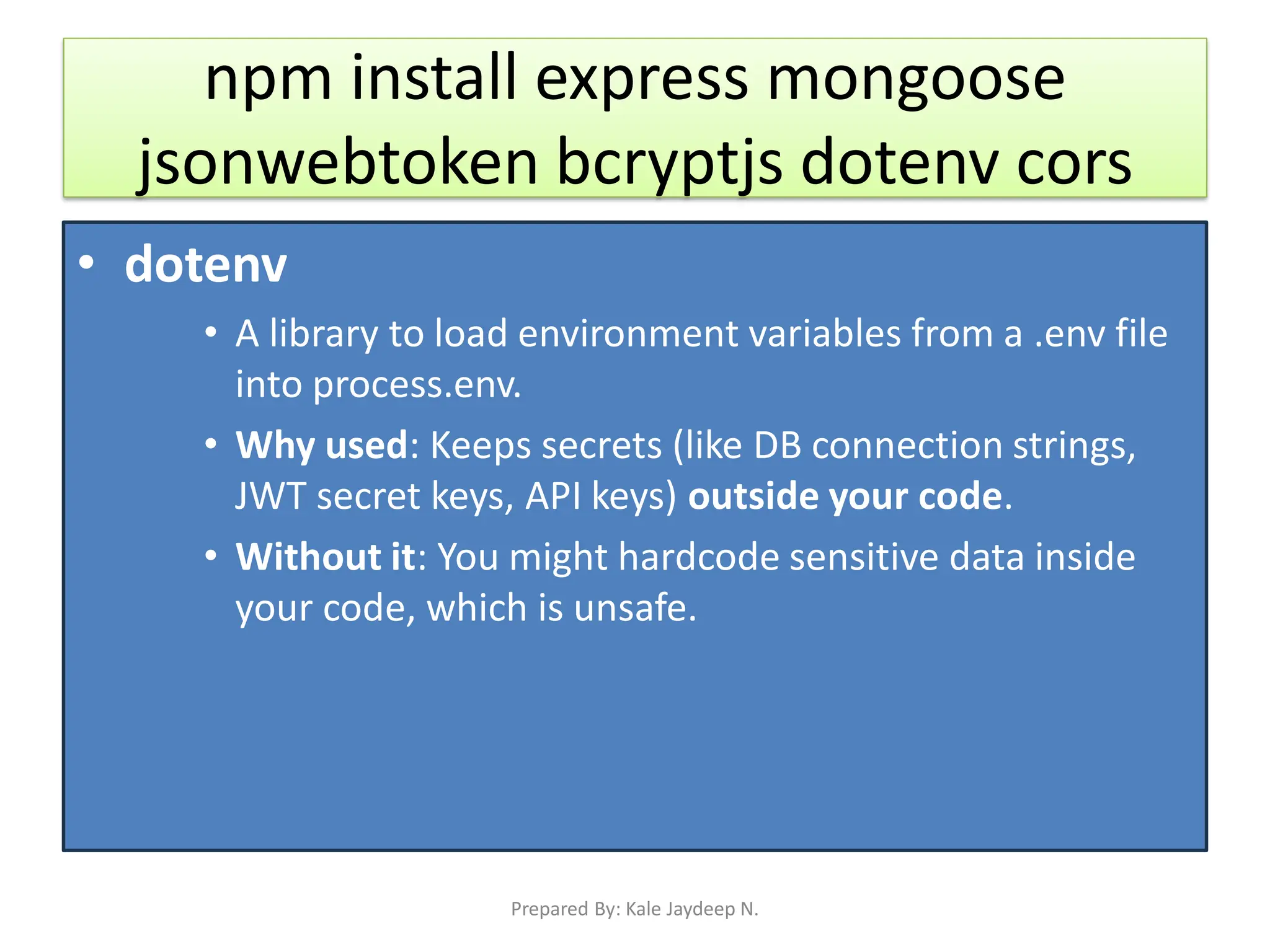
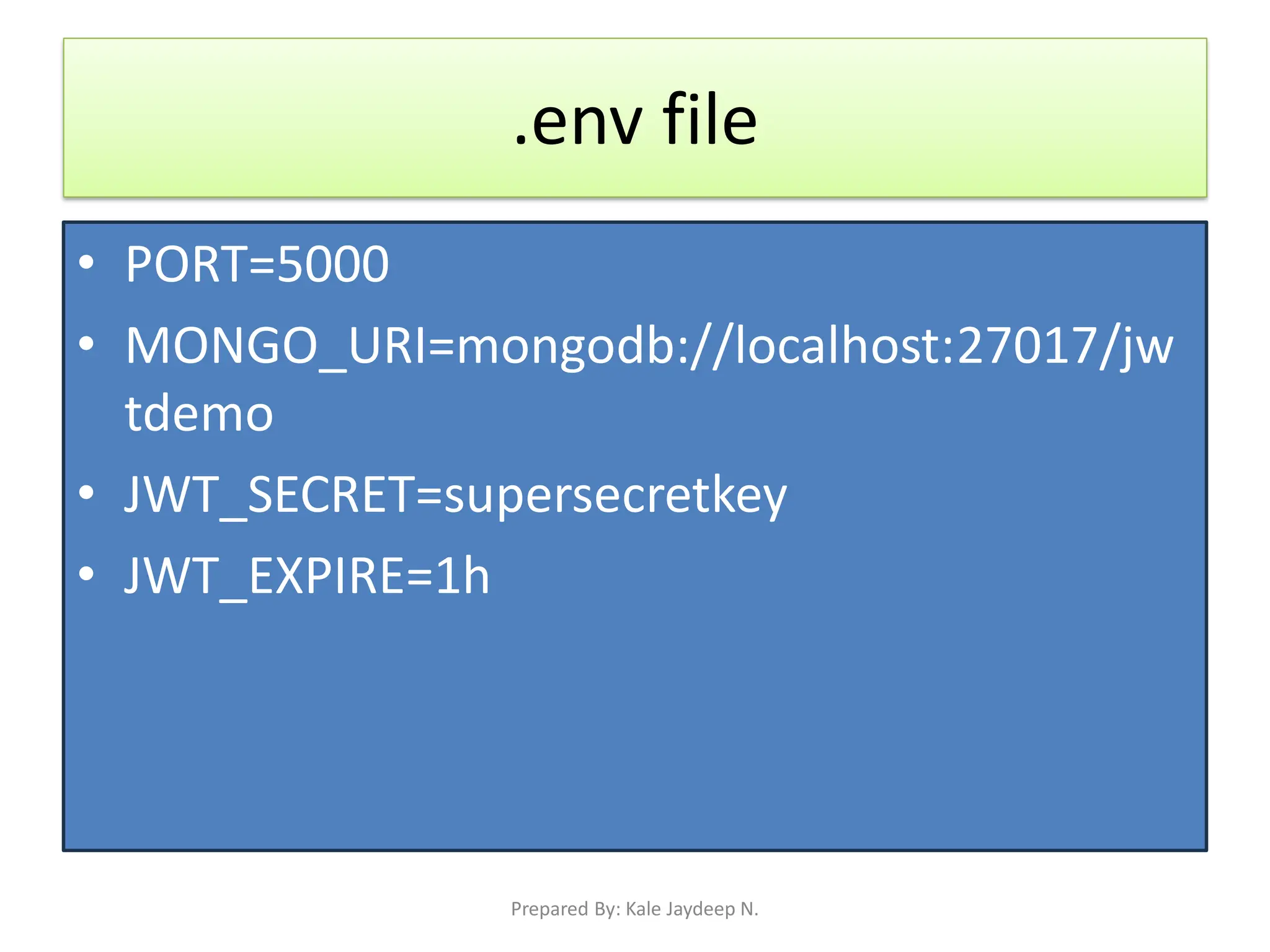
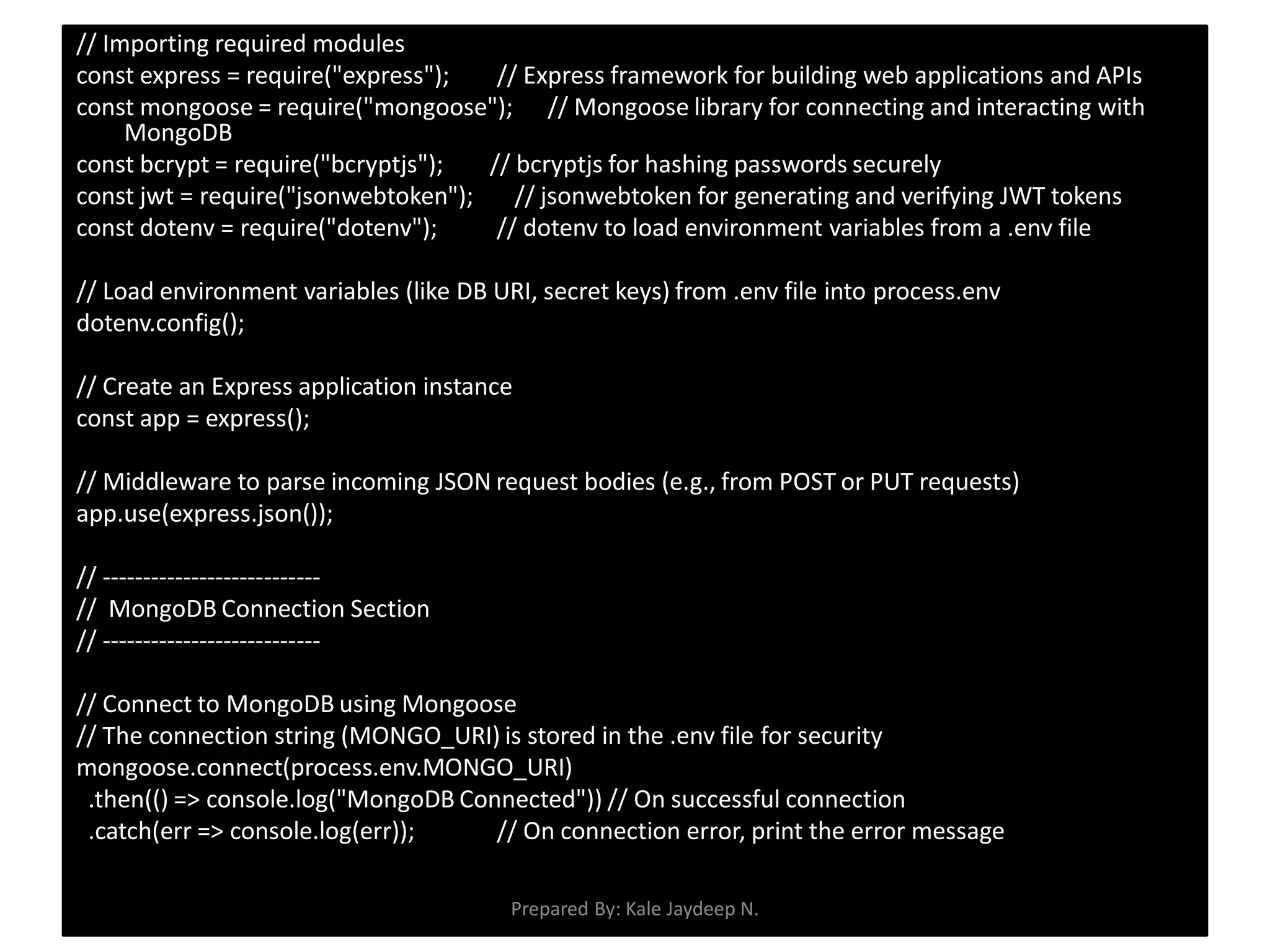
Environment setup using dotenv, mongoose, and bcryptjs
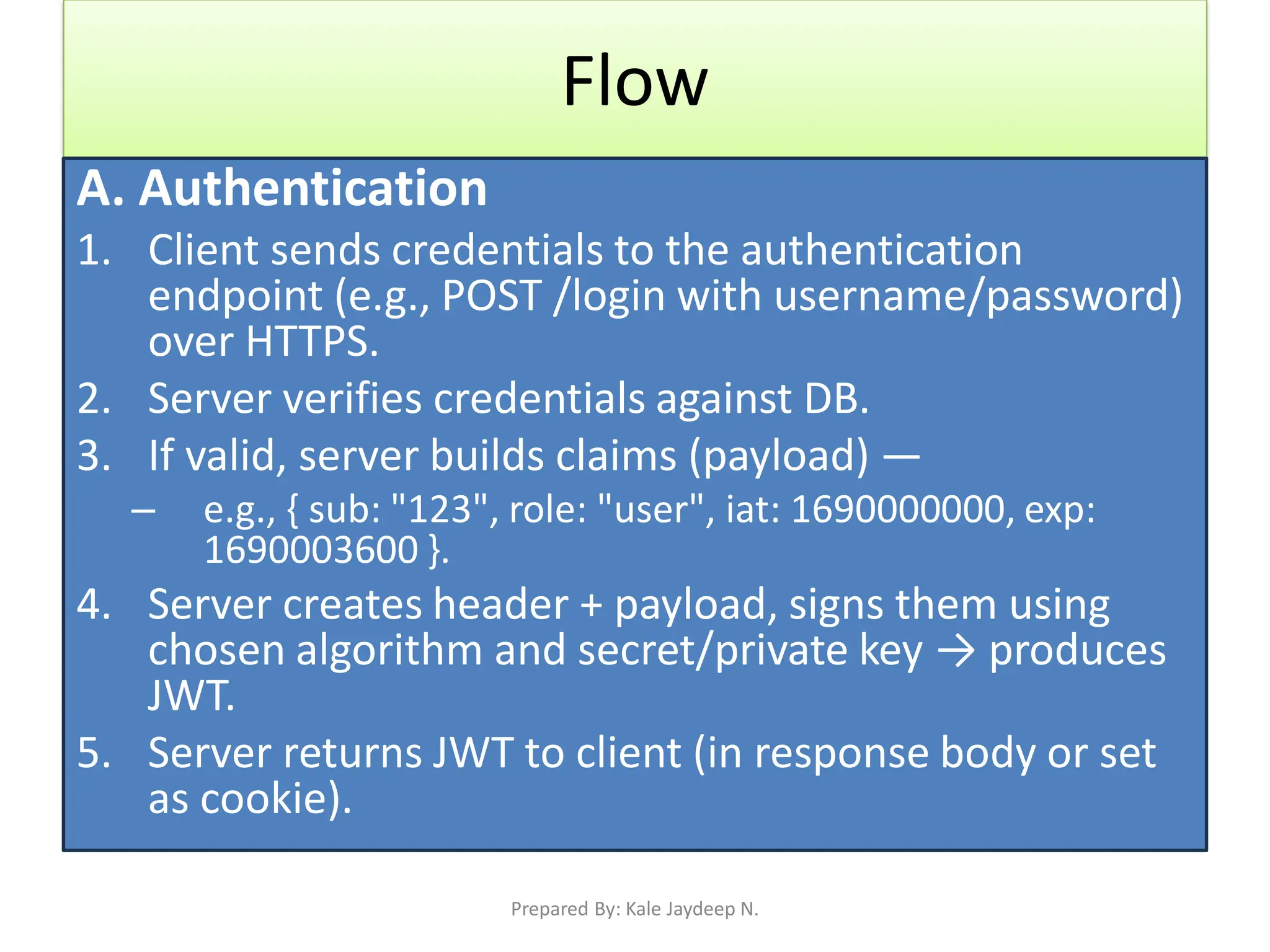
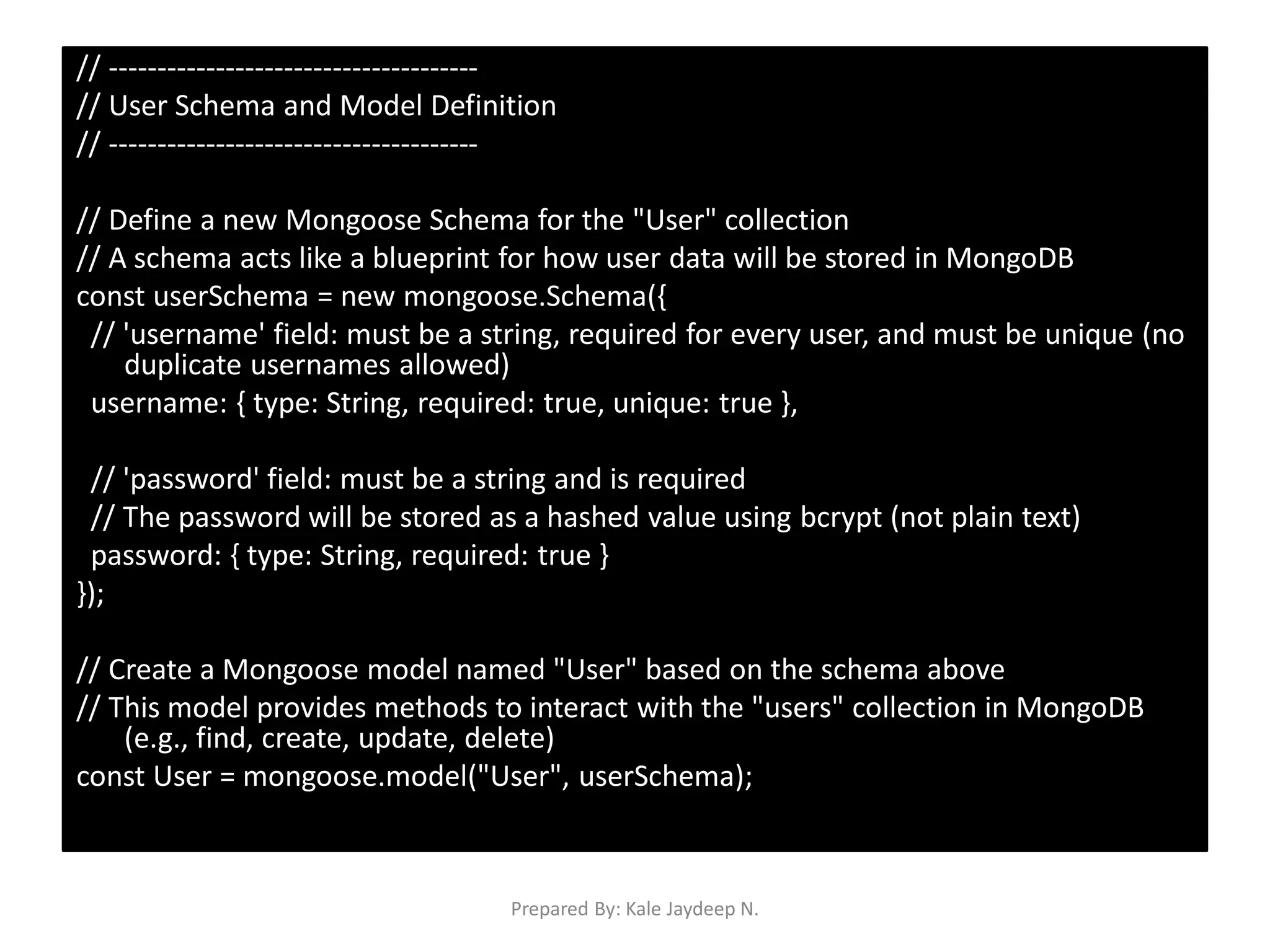
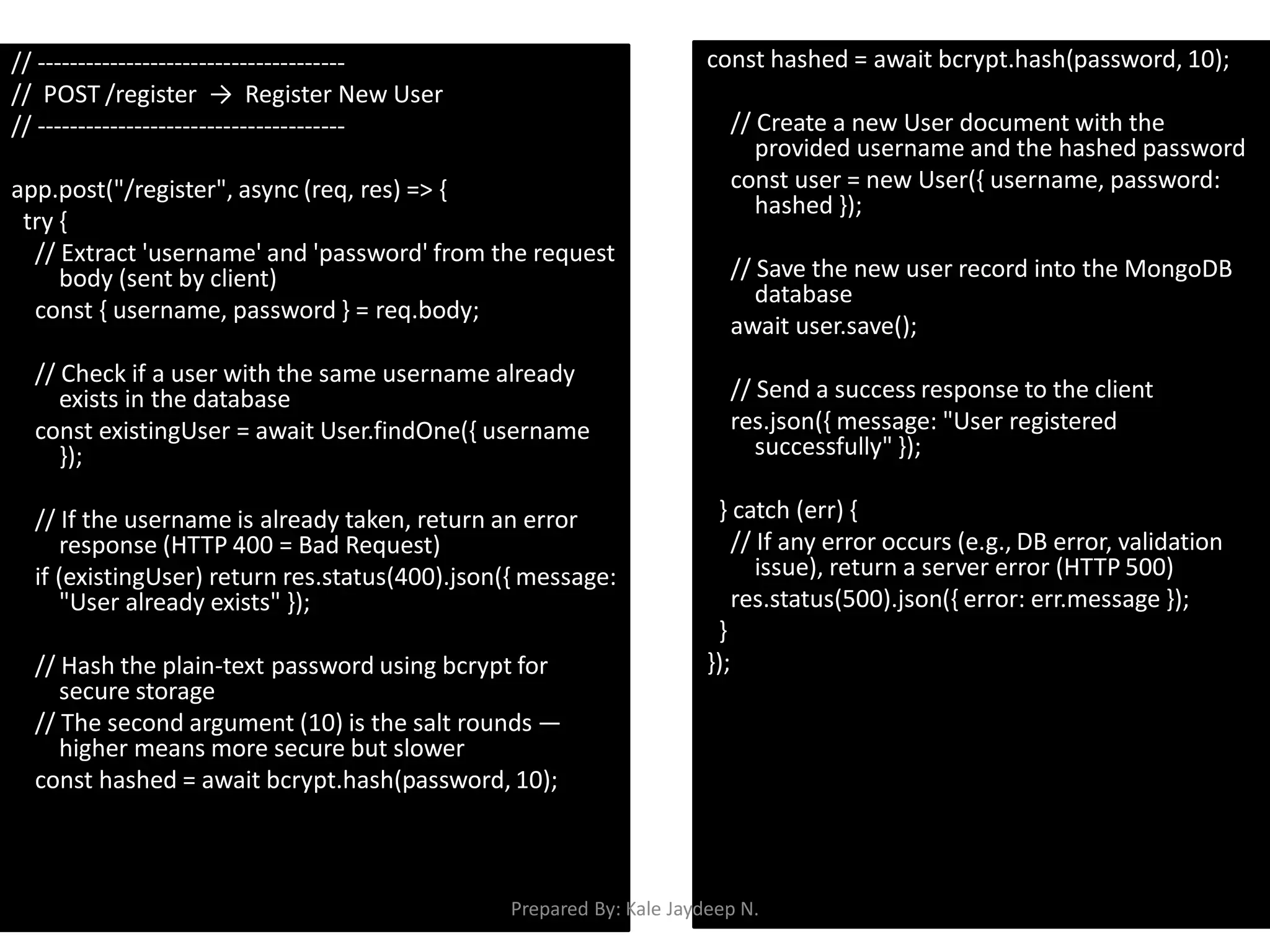
Creating Register and Login APIs with password hashing
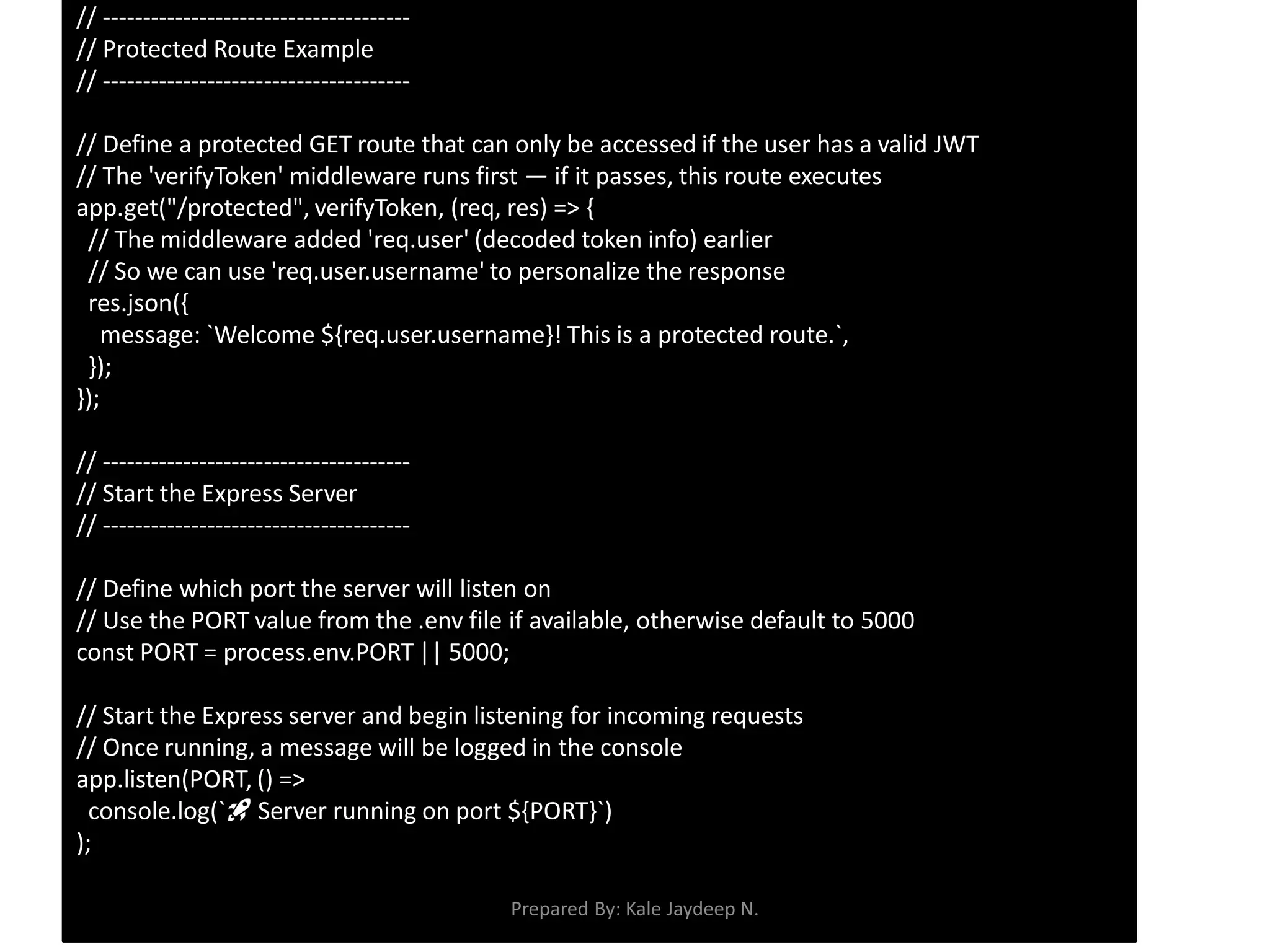
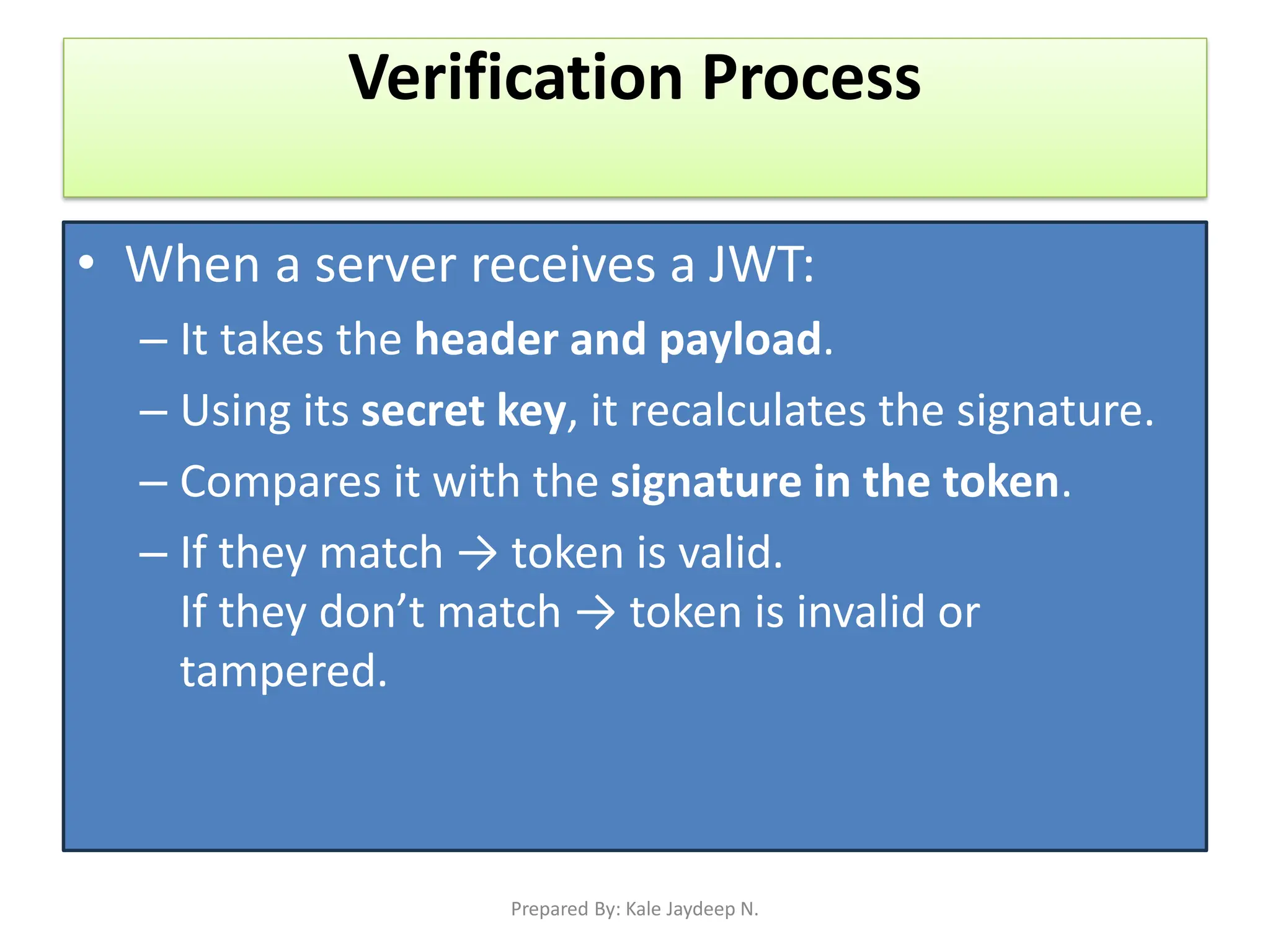
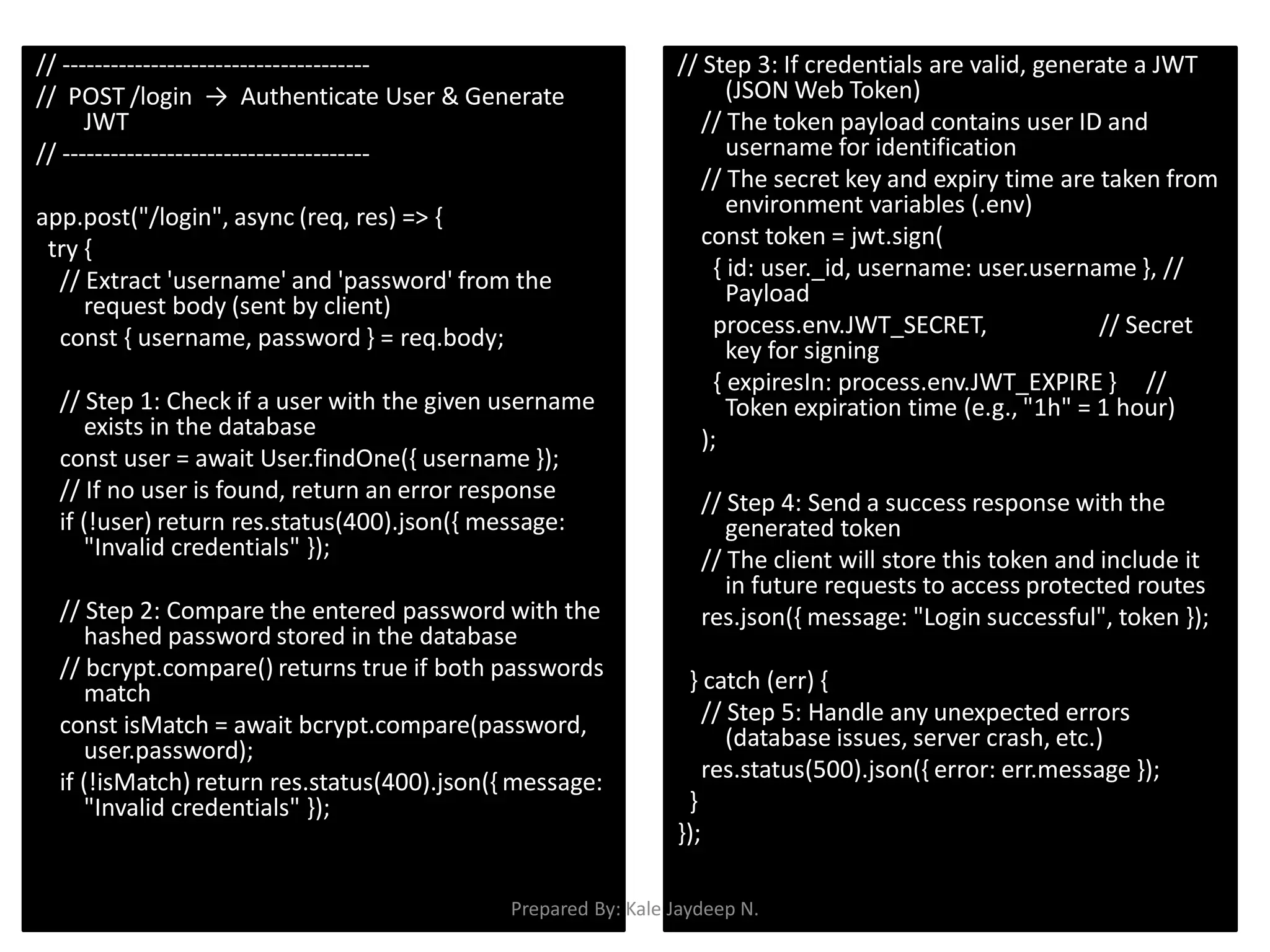
Generating and verifying JWT tokens
Protecting routes using middleware
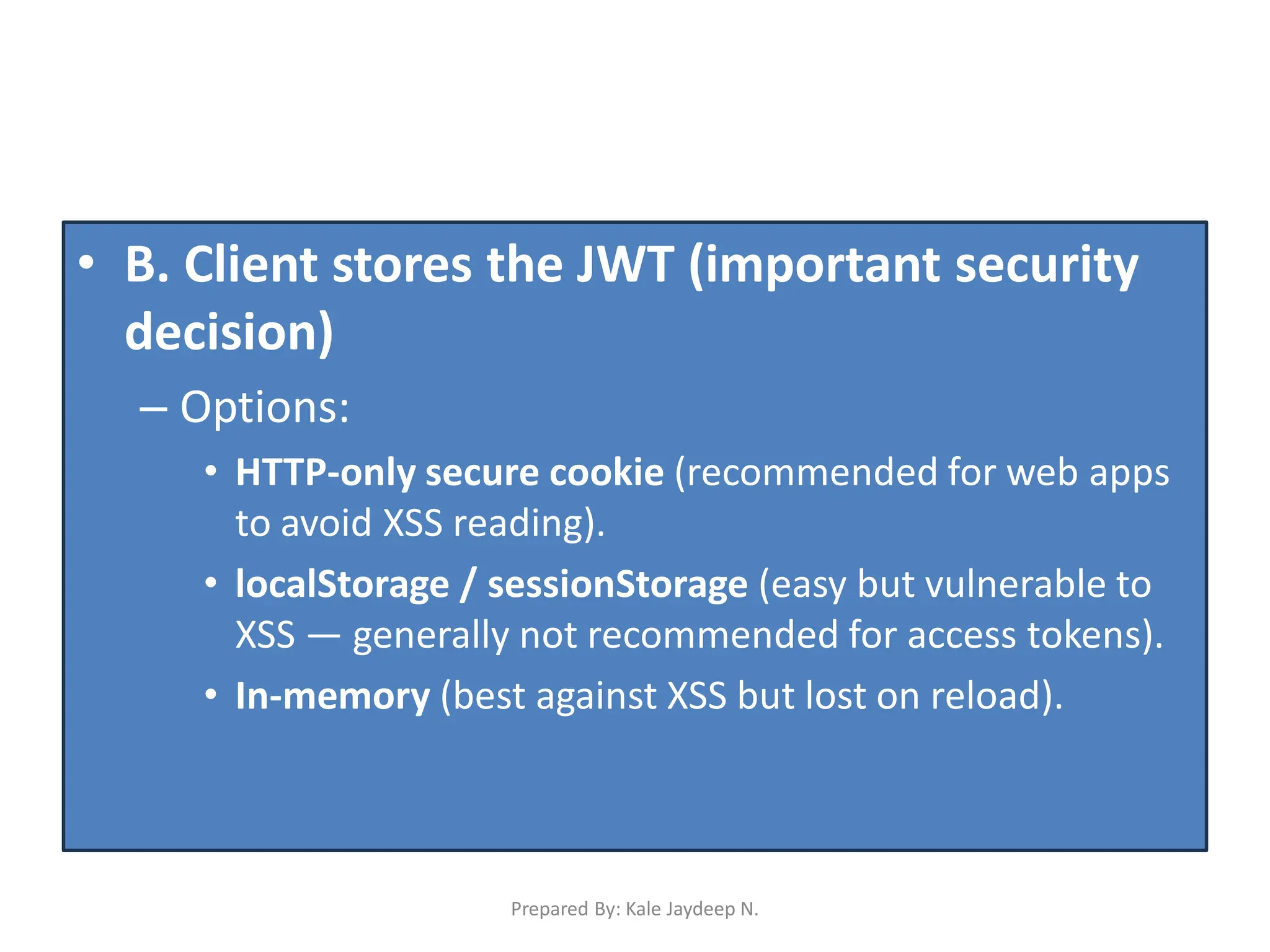
Secure storage of tokens (HTTP-only cookies, headers)
Real-world best practices for securing APIs
This presentation is ideal for:
Students learning the MERN Stack
Developers exploring API Security and Token-based Authentication
Anyone preparing for backend development interviews or academic presentations
By the end of this presentation, viewers will understand how to build a secure authentication system for modern web applications using Node.js, Express, MongoDB, and JWT.



![// --------------------------------------
// Middleware: verifyToken()
// Purpose: To protect routes by verifying JWT tokens
// --------------------------------------
function verifyToken(req, res, next) {
// Step 1: Retrieve the 'Authorization' header from the
incoming request
// The format should be: Authorization: Bearer
<token>
const authHeader = req.headers["authorization"];
// Step 2: Extract the token part (the string after
'Bearer ')
// If no header is present, 'token' will be undefined
const token = authHeader && authHeader.split(" ")[1];
// e.g., "Bearer abc.def.ghi" → "abc.def.ghi"
// Step 3: If no token is provided, deny access with
status 401 (Unauthorized)
if (!token) return res.status(401).json({ message: "No
token provided" });
// Step 4: Verify the token using the secret key
stored in the environment variable
// jwt.verify() checks the token's signature and
expiration
jwt.verify(token, process.env.JWT_SECRET, (err,
decoded) => {
// If verification fails (invalid or expired token),
return 403 (Forbidden)
if (err) return res.status(403).json({ message:
"Invalid token" });
// Step 5: If token is valid, 'decoded' contains the
payload (e.g., user ID, username)
// Attach the decoded data to the request object
so it can be used in the next middleware or
route
req.user = decoded;
// Step 6: Continue to the next middleware or the
protected route handler
next();
});
}
Prepared By: Kale Jaydeep N.](https://image.slidesharecdn.com/jwtauthenticationassignment-251102042308-53b7d057/75/JWT_Authentication_MERN_Stack_Assignment-pdf-17-2048.jpg)