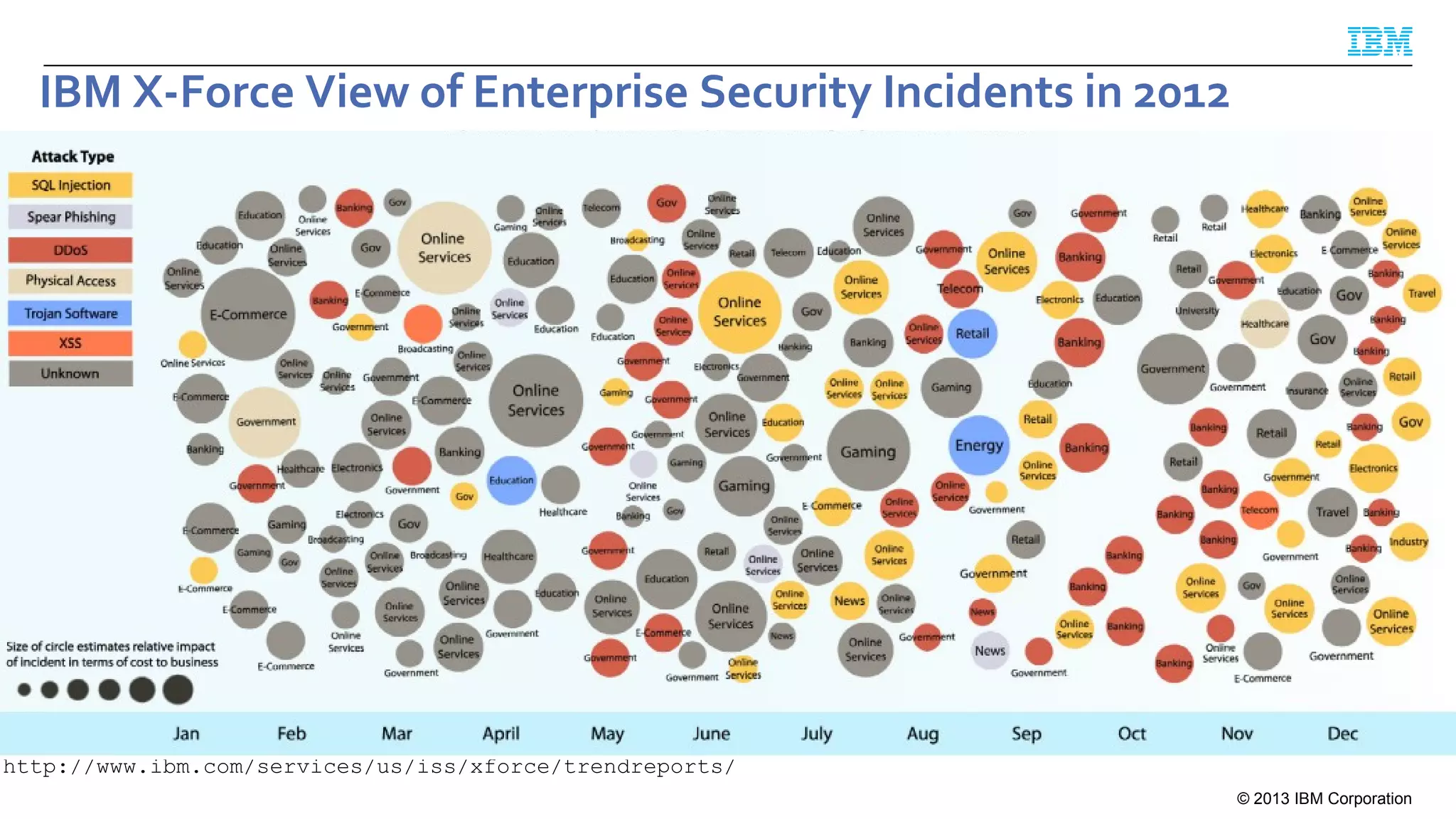
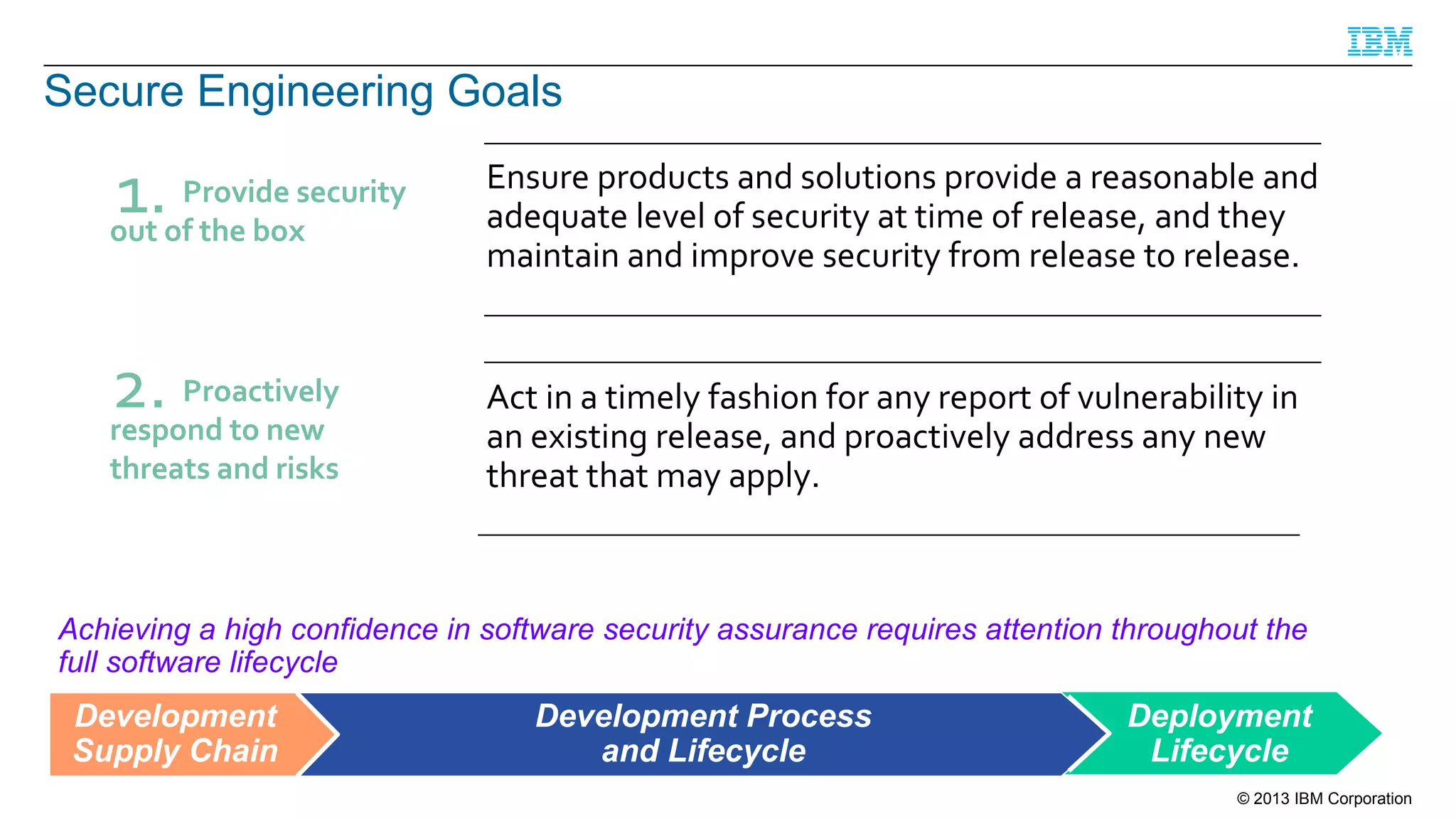
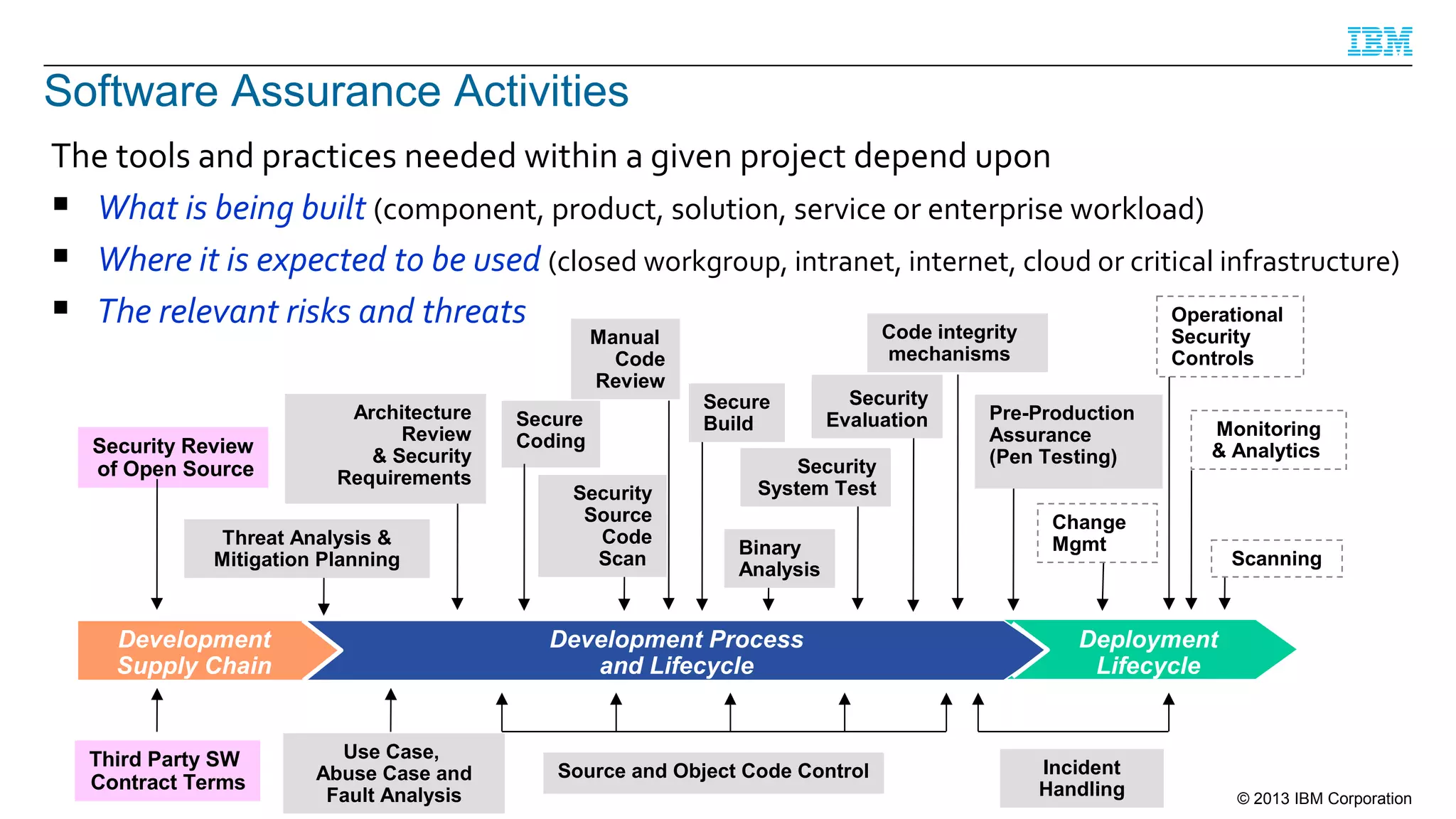
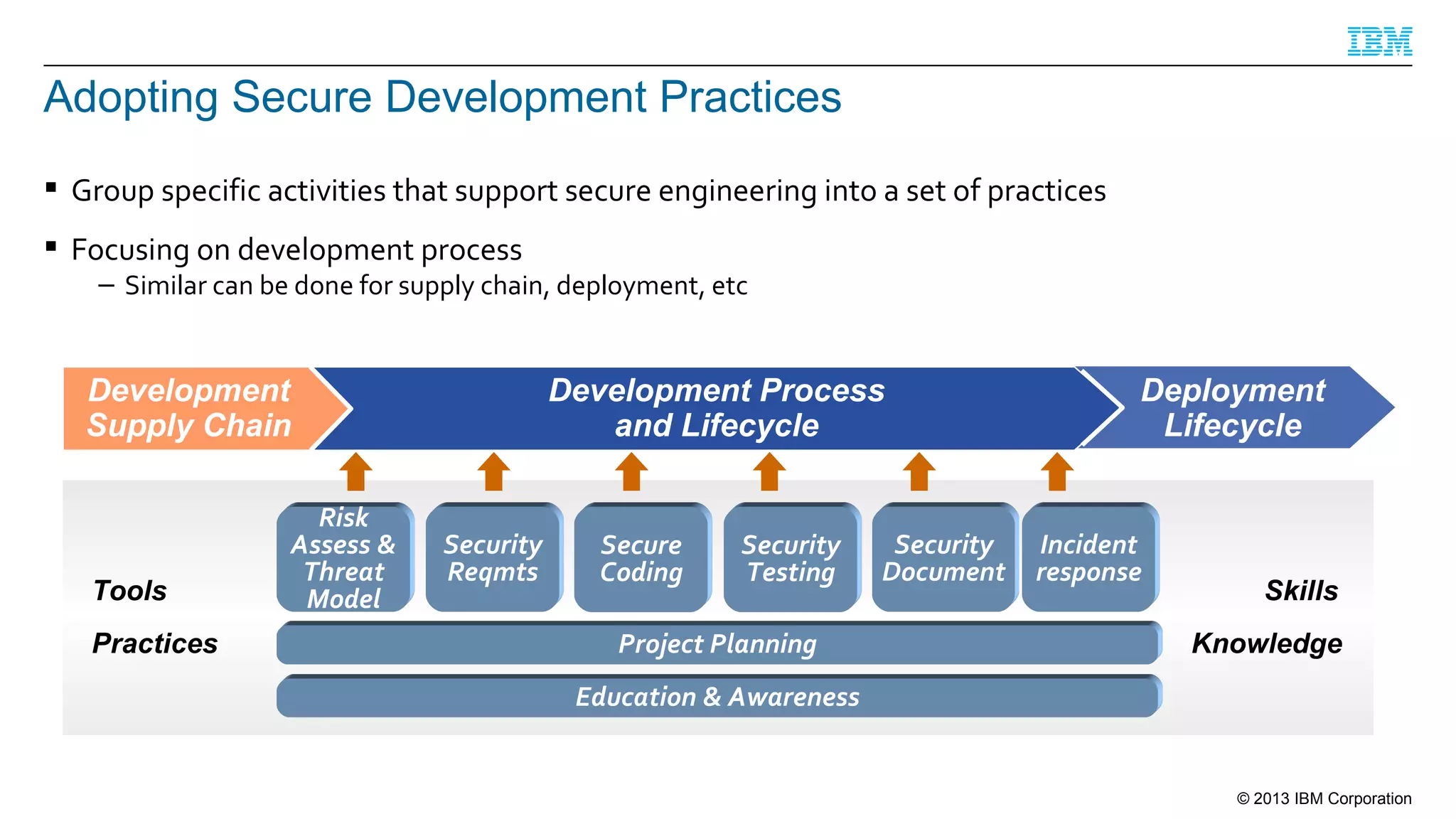
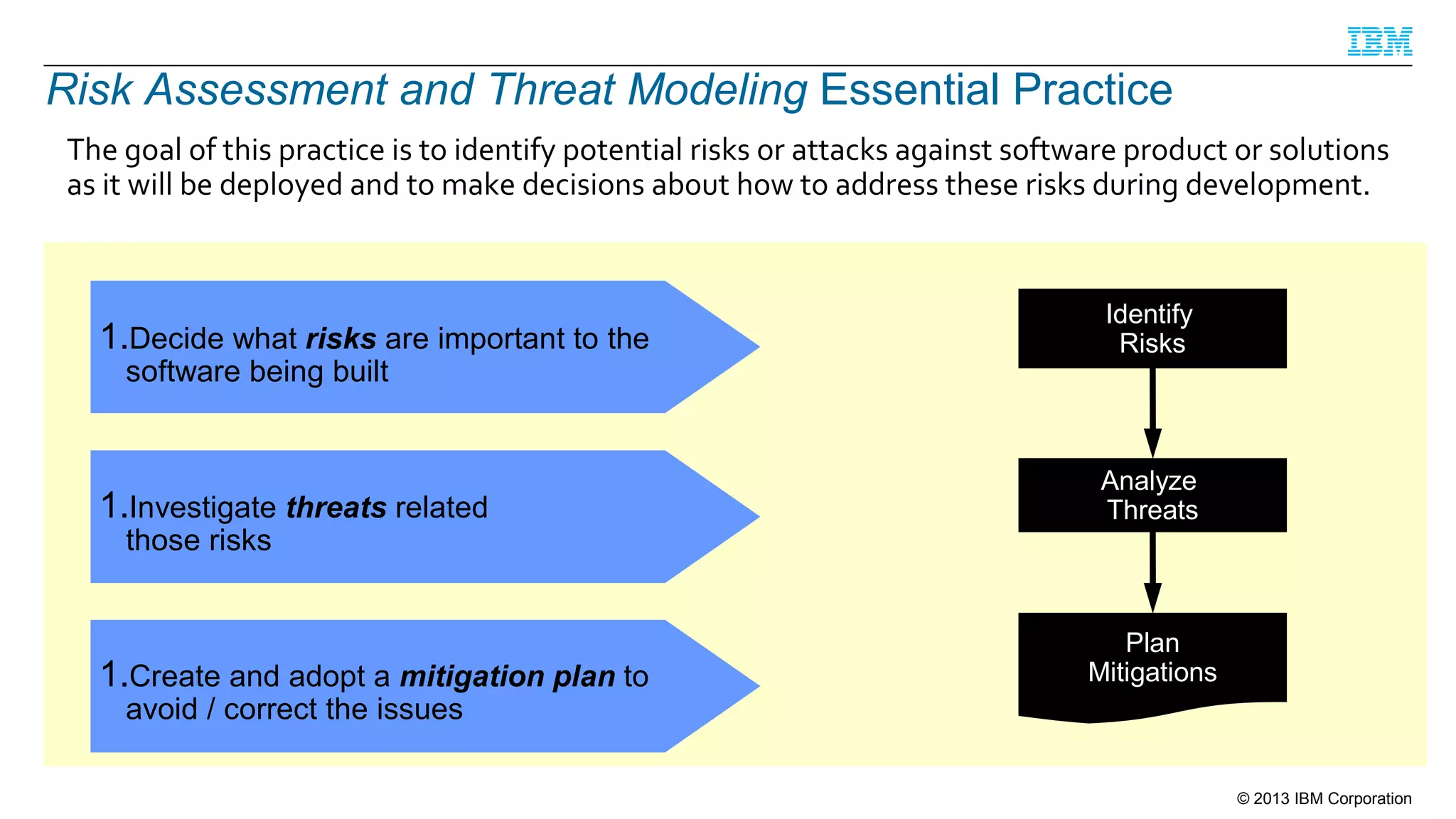
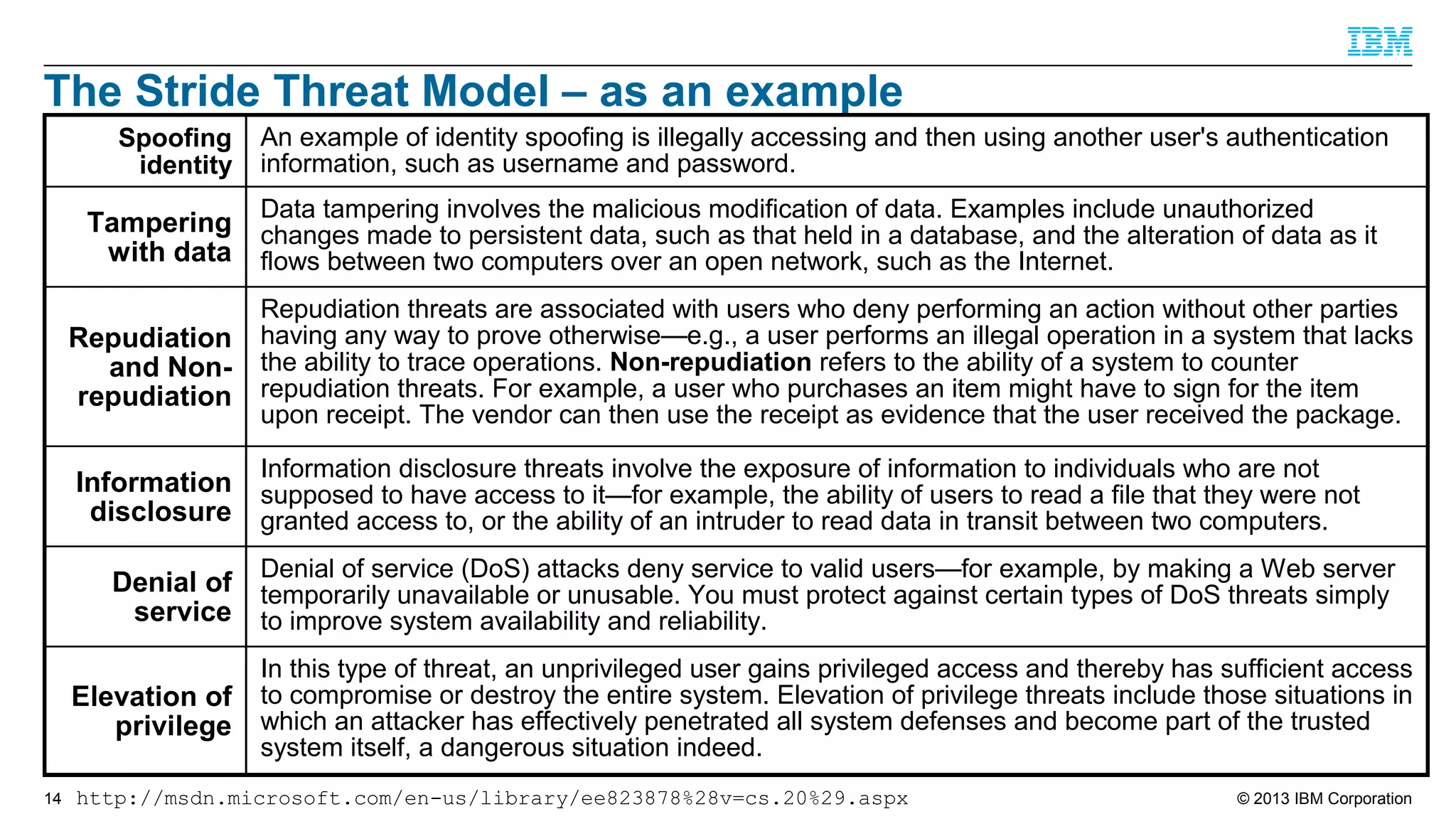
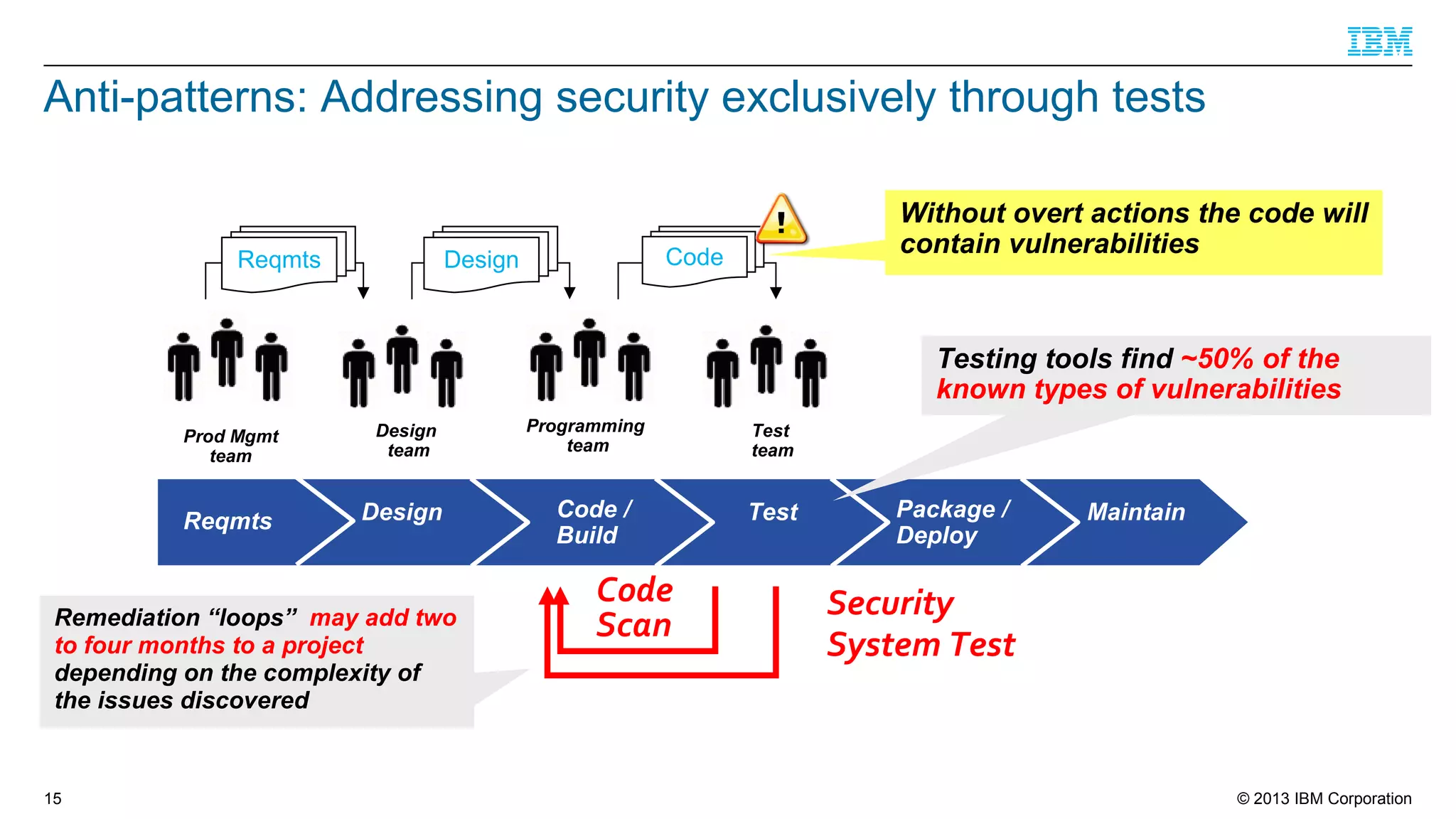
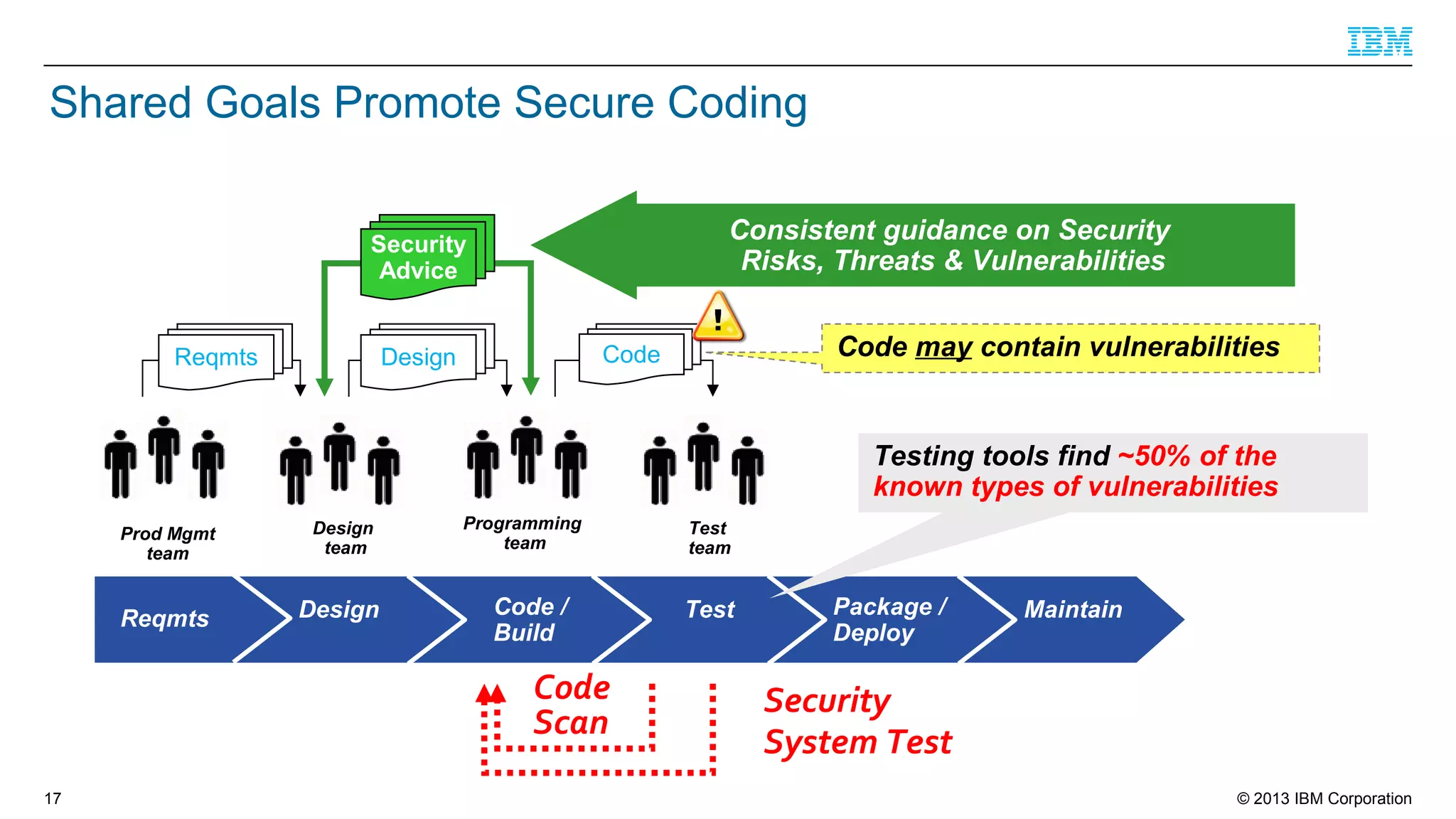
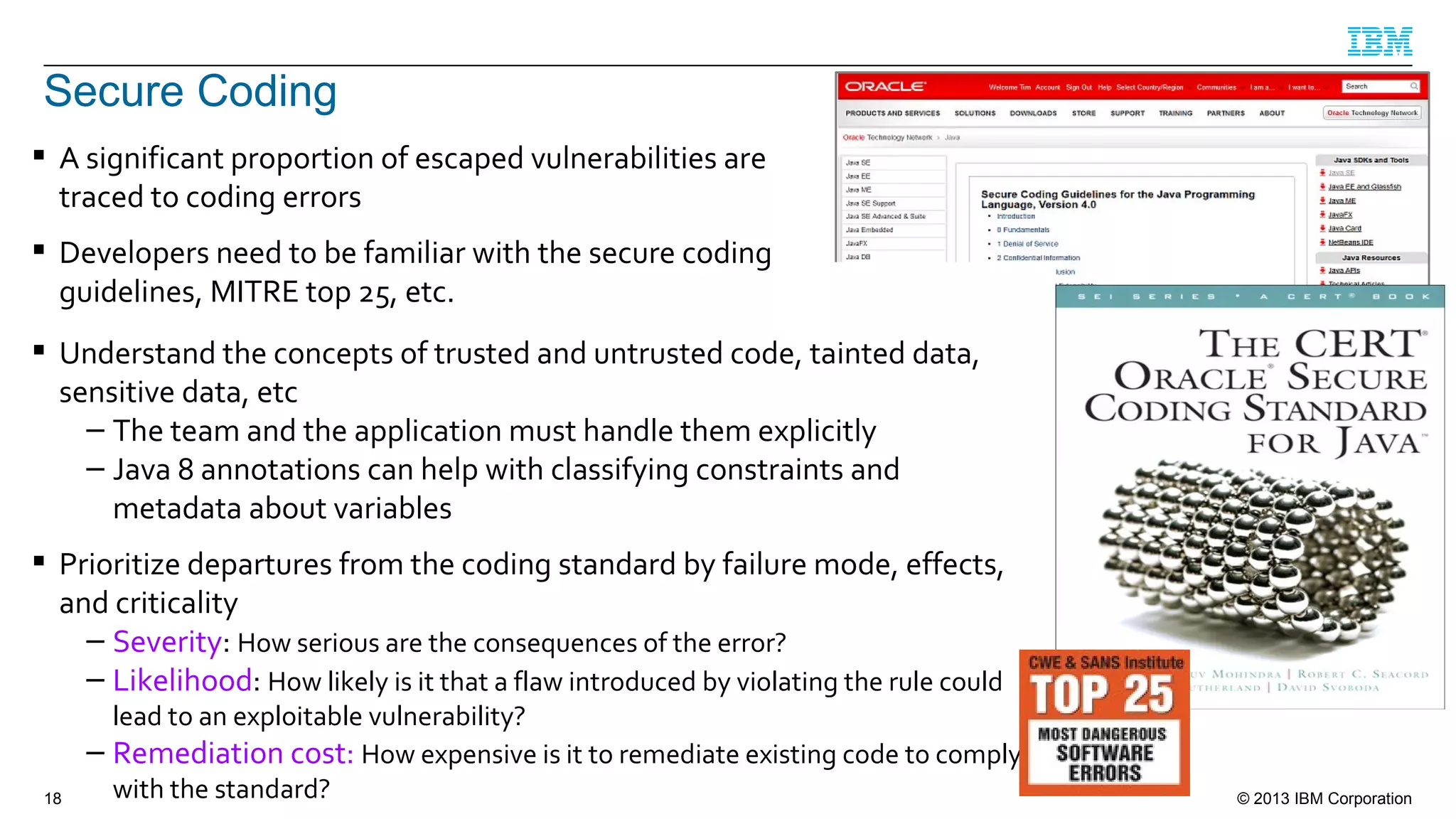
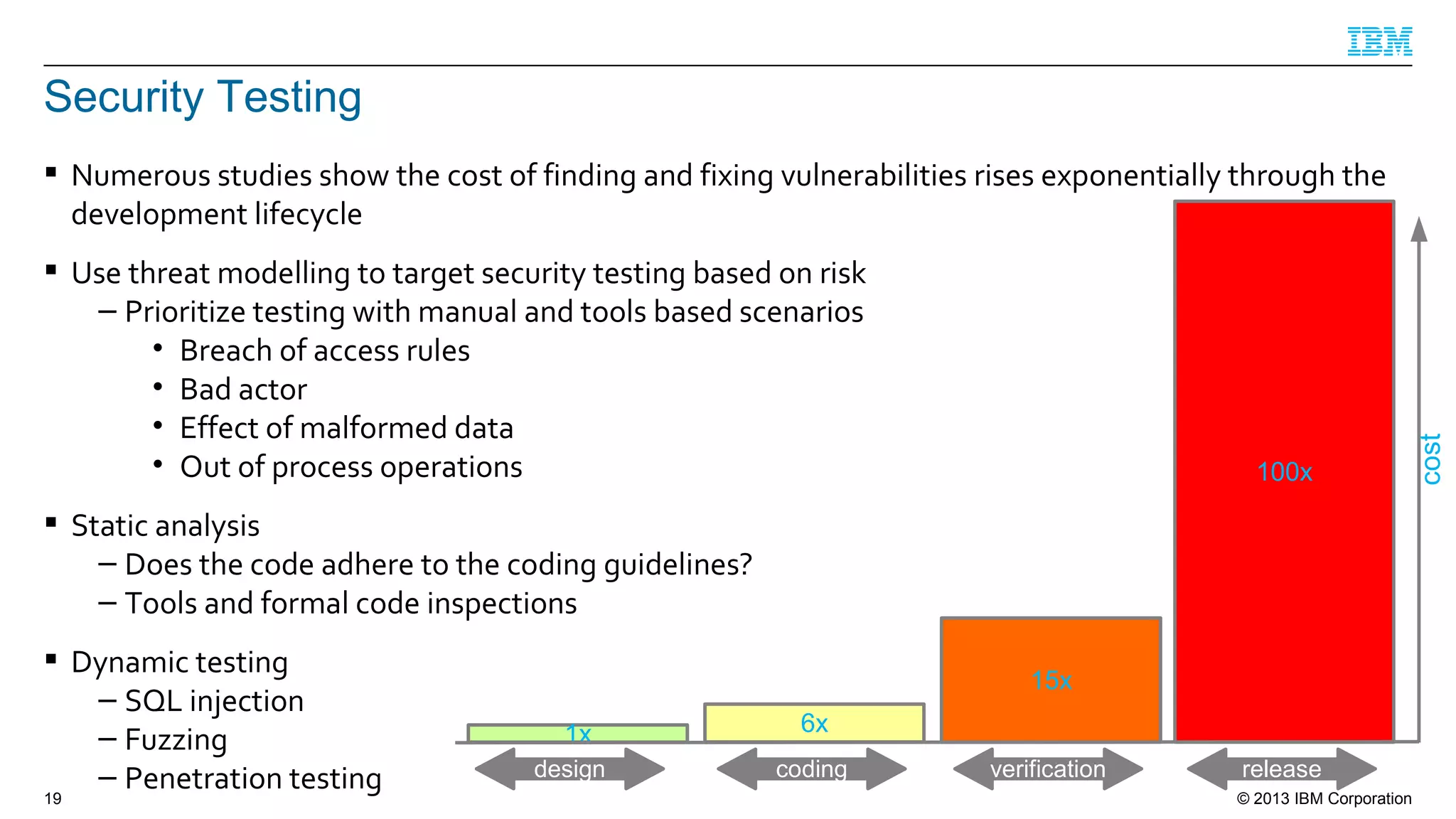
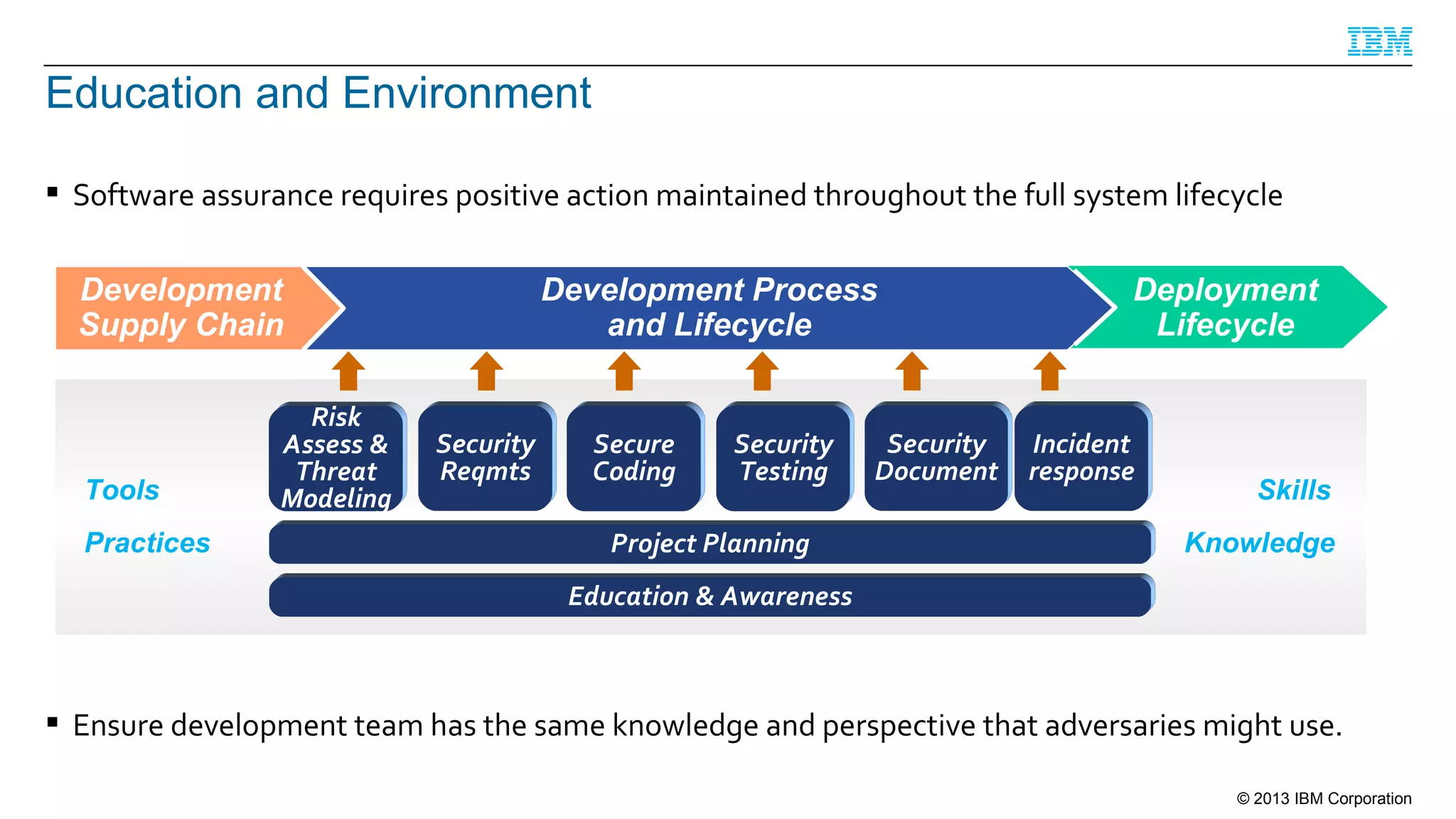
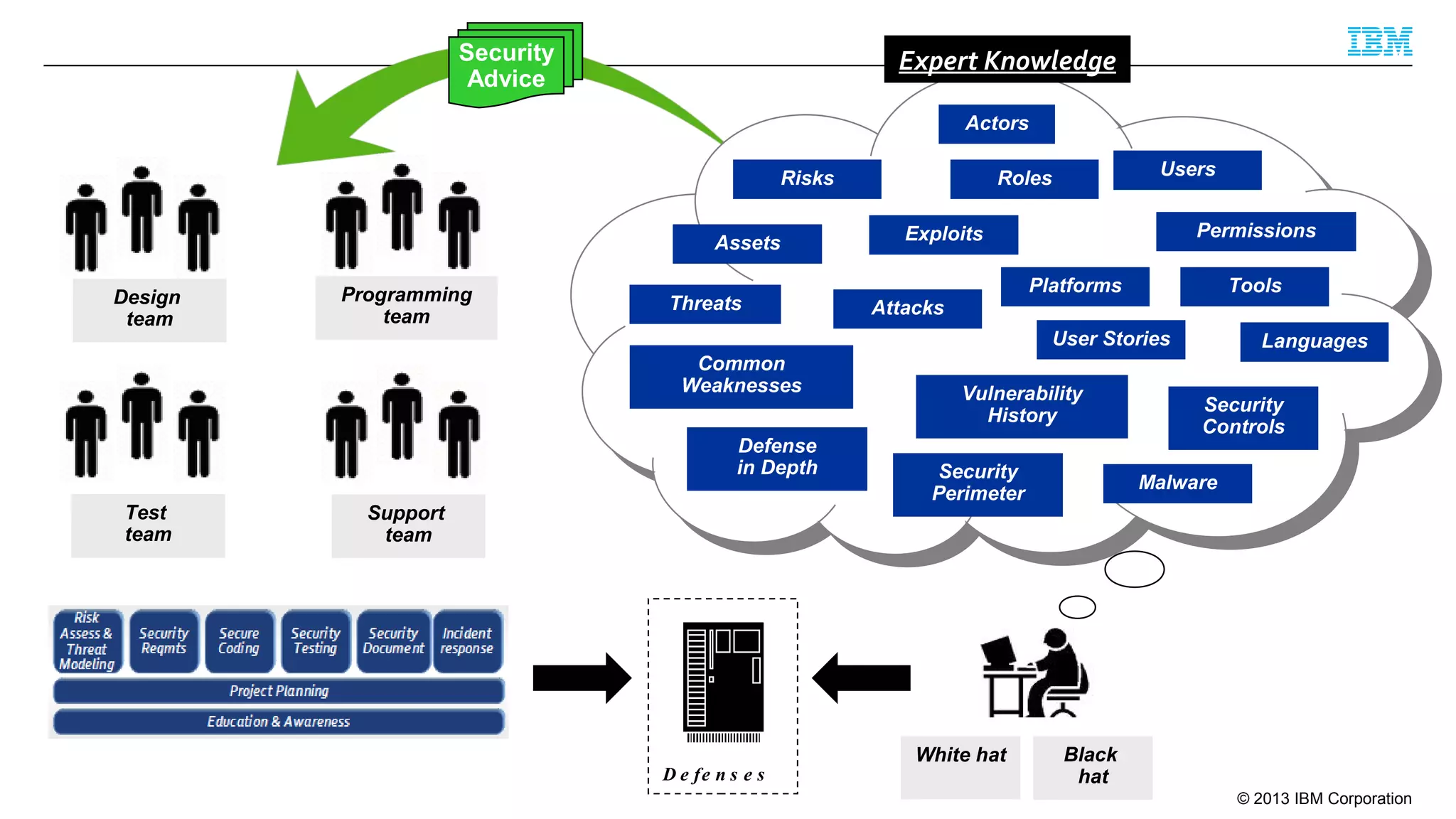
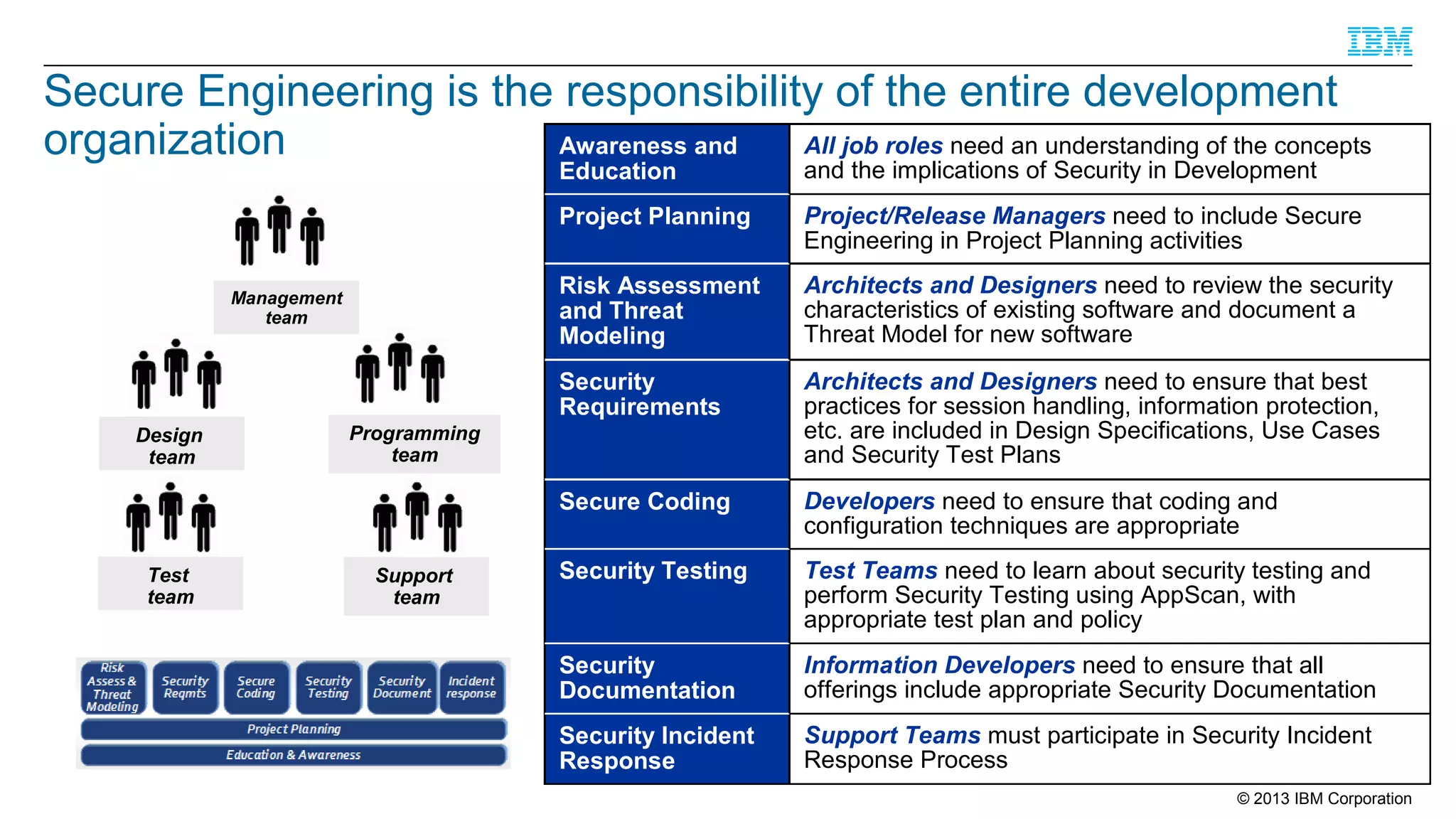
This document summarizes a presentation on secure engineering practices for Java given at JavaOne 2013. It discusses the importance of software assurance over just security controls. It emphasizes that achieving a high level of software assurance requires attention to security throughout the development lifecycle, including risk assessment, secure coding practices, security testing, documentation, and incident response. The presentation recommends that development teams understand security risks and threats in order to build secure software.