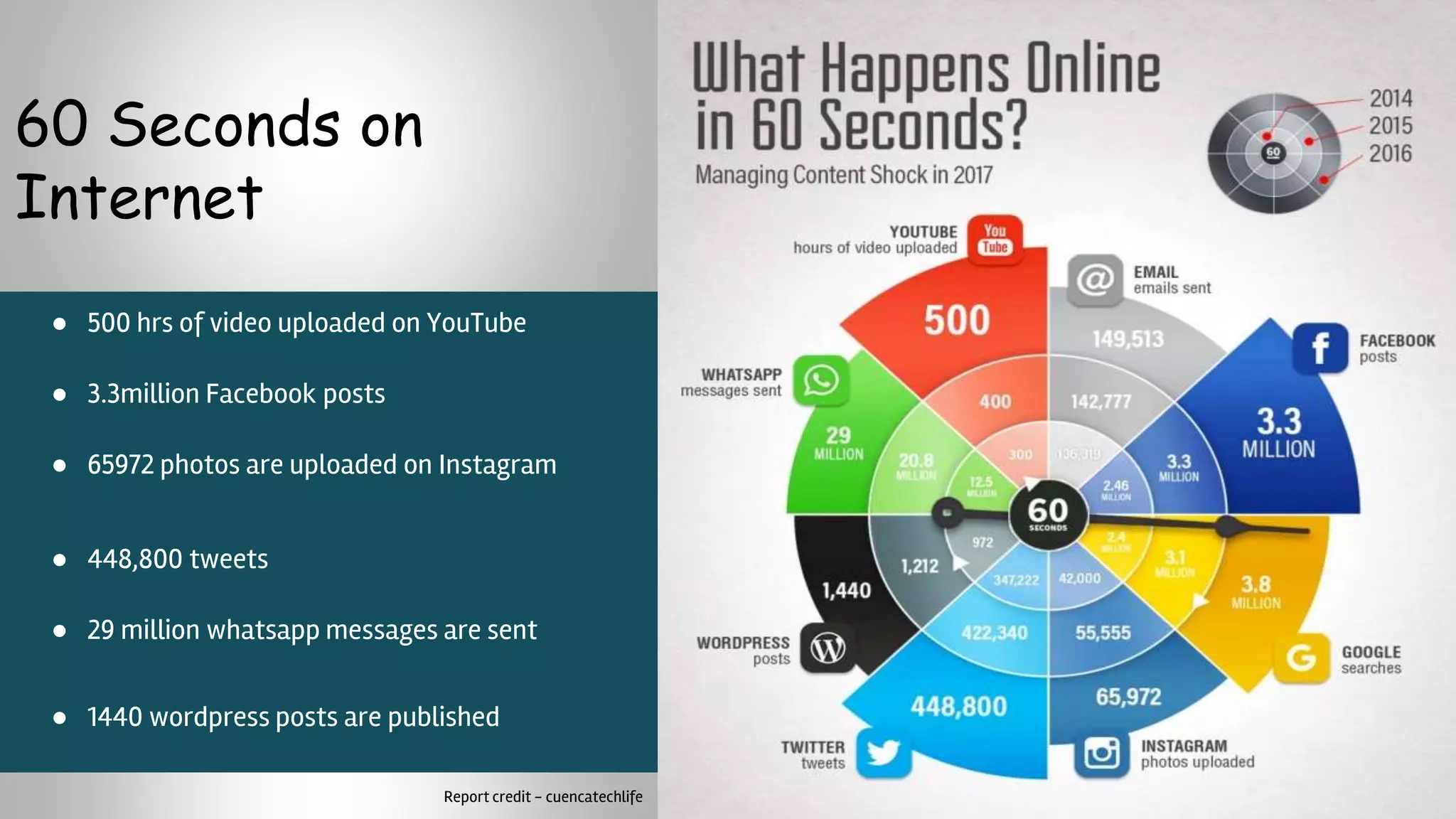
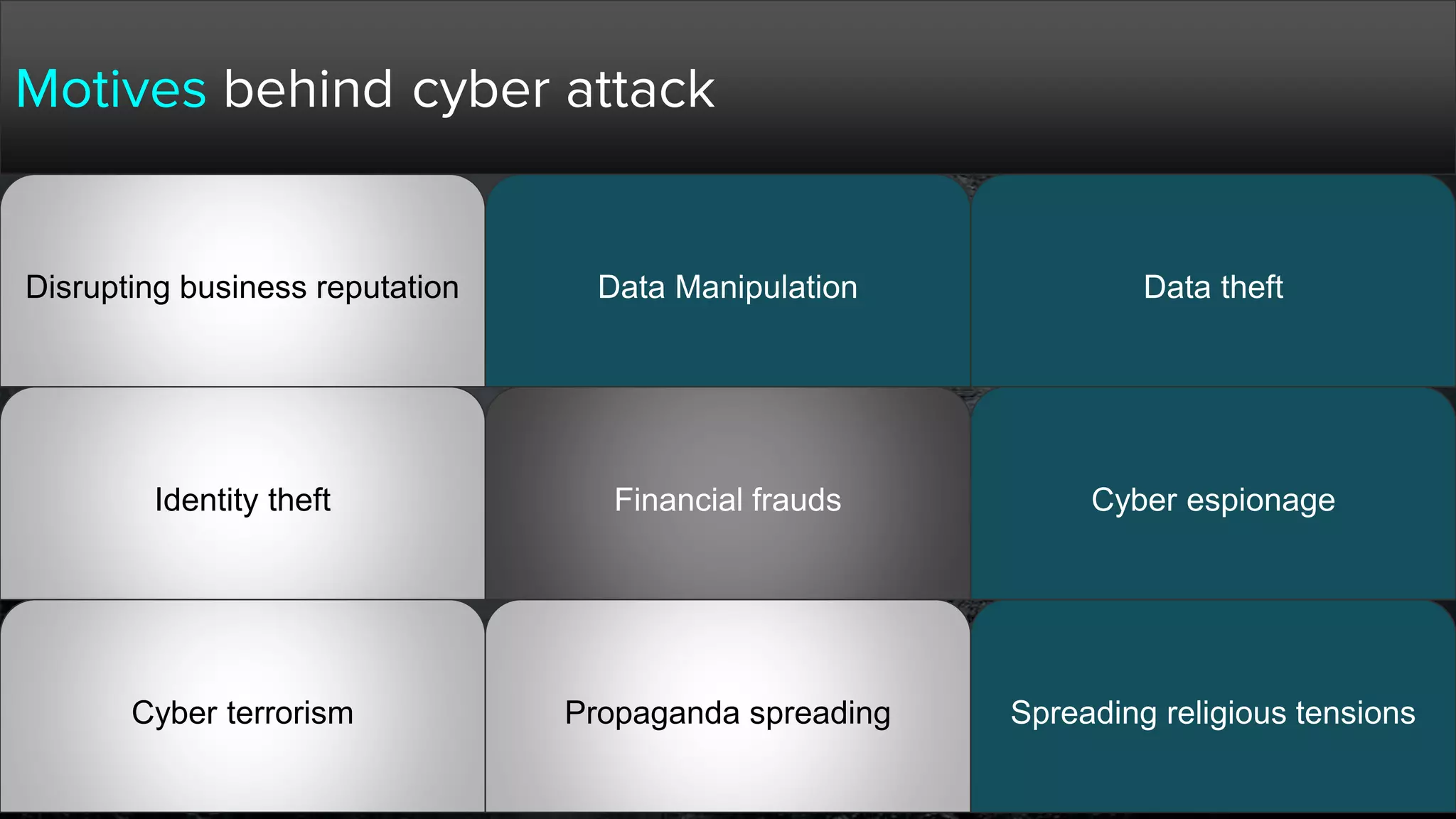
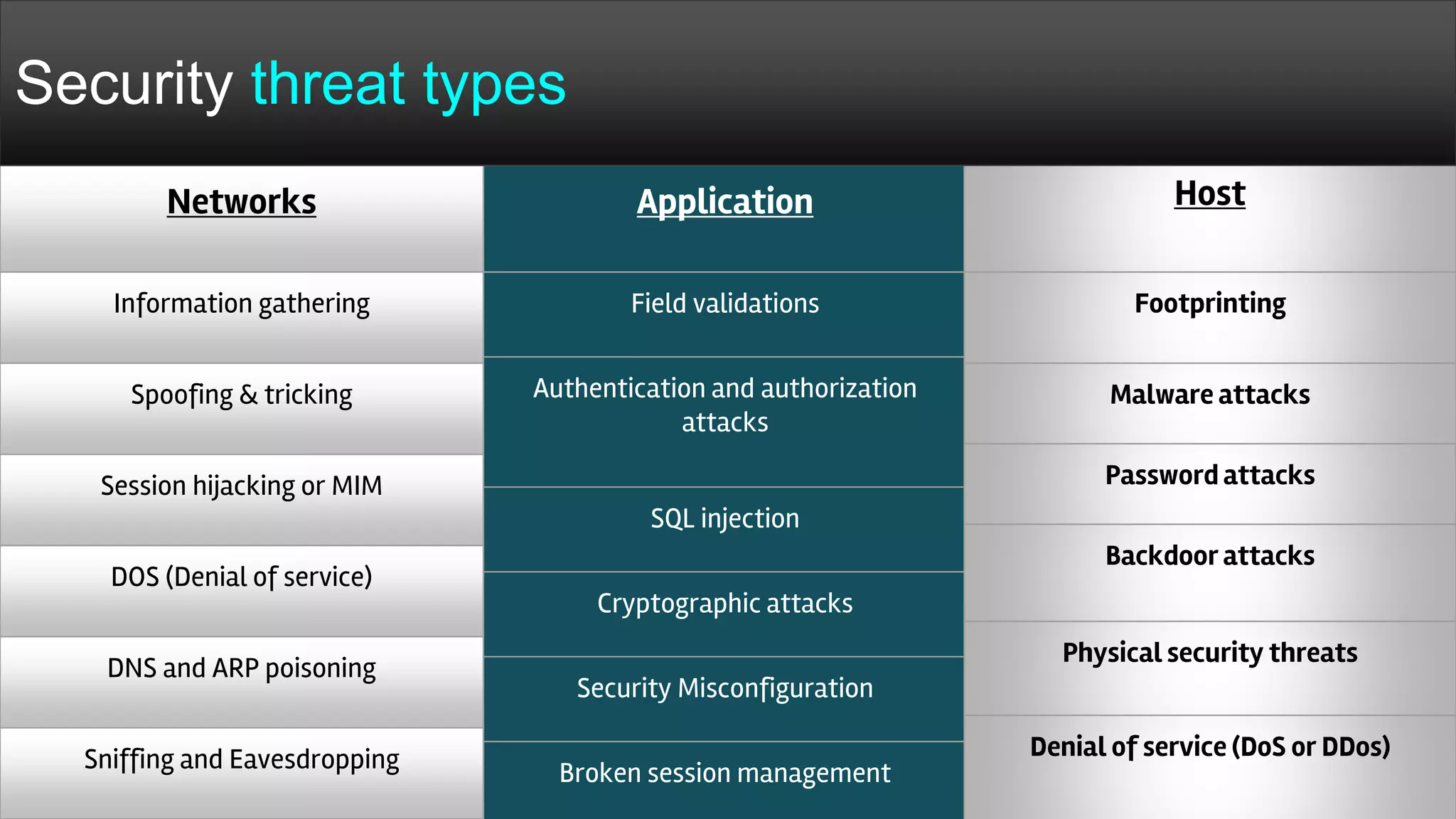
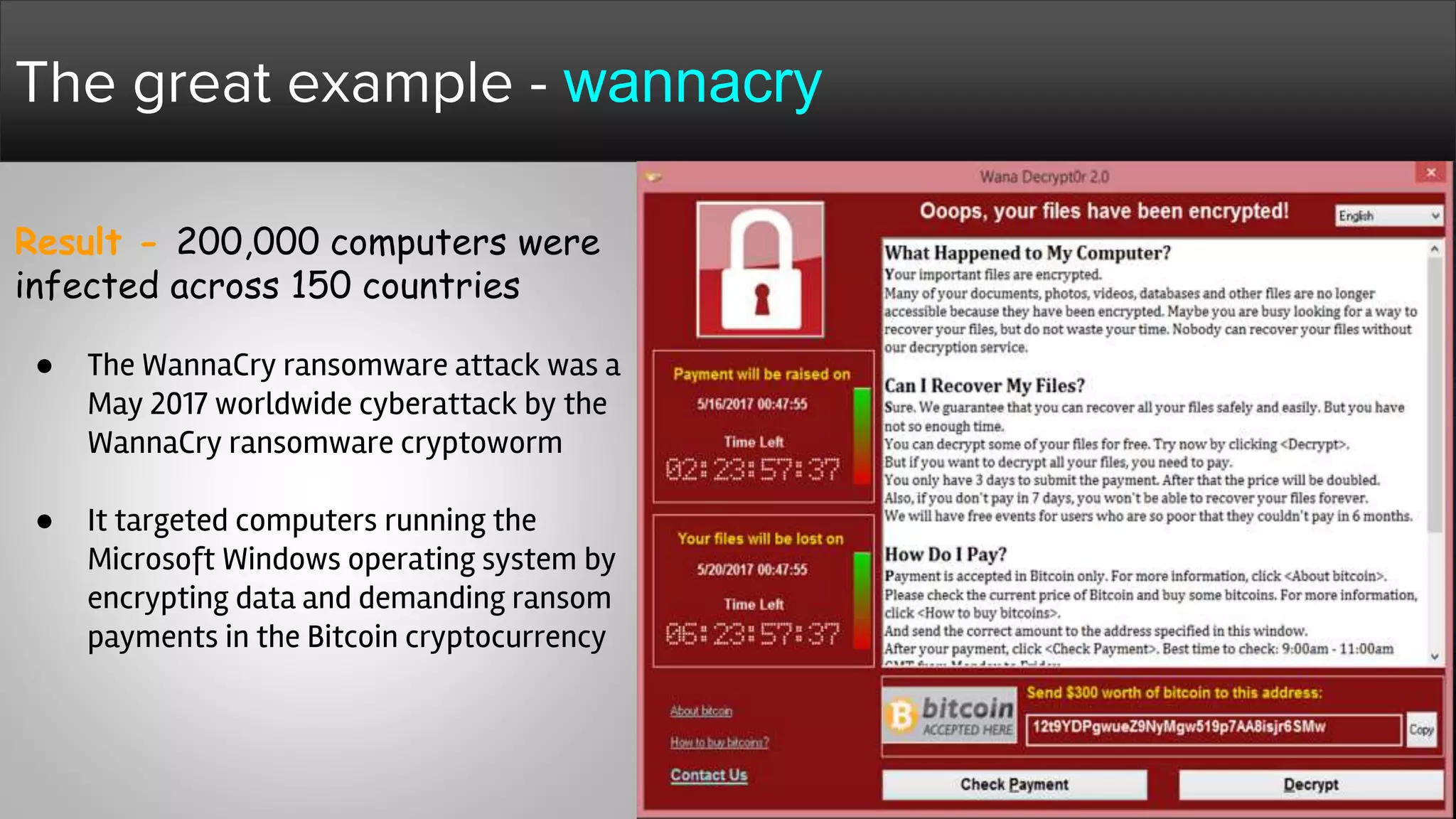
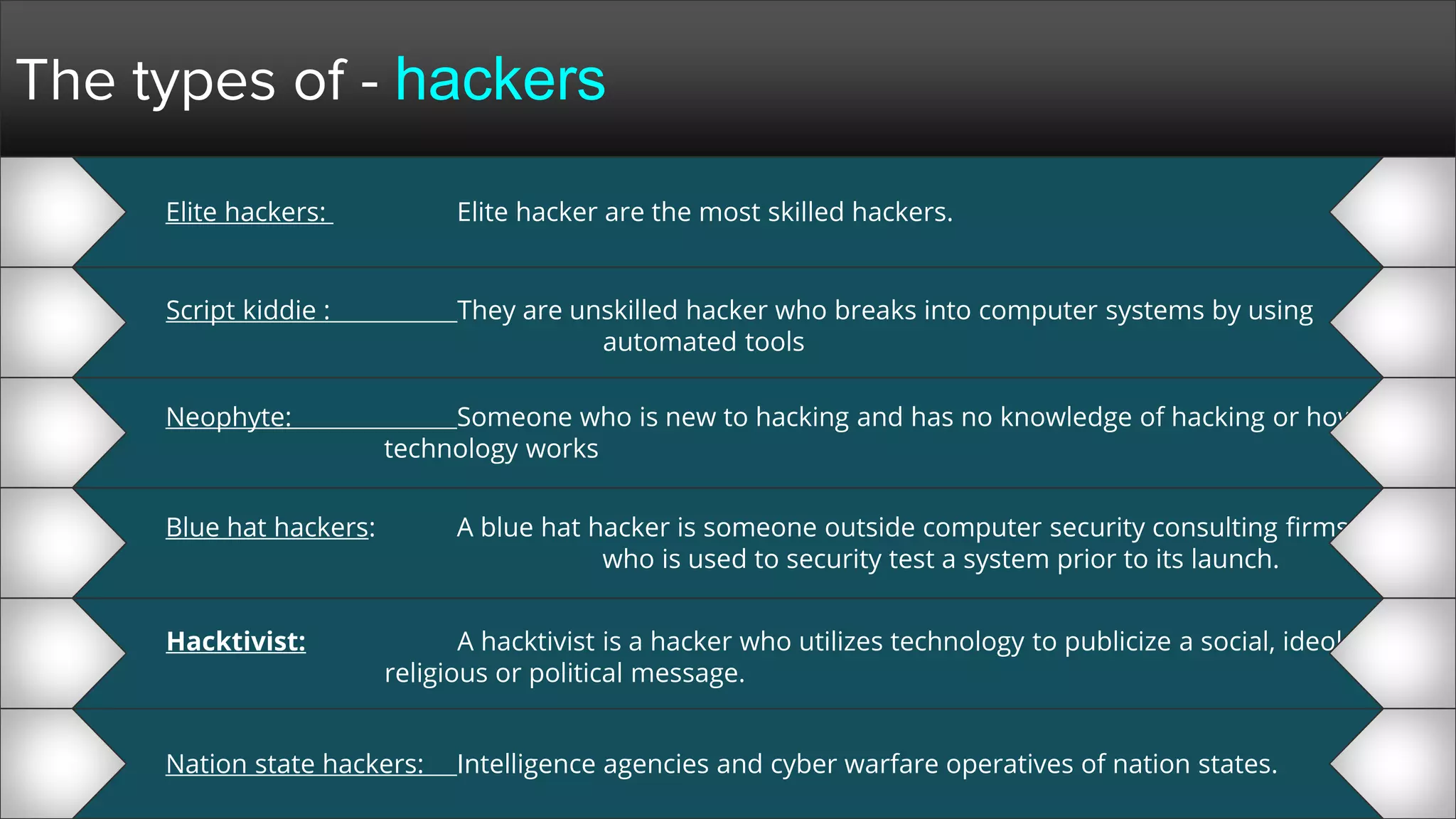
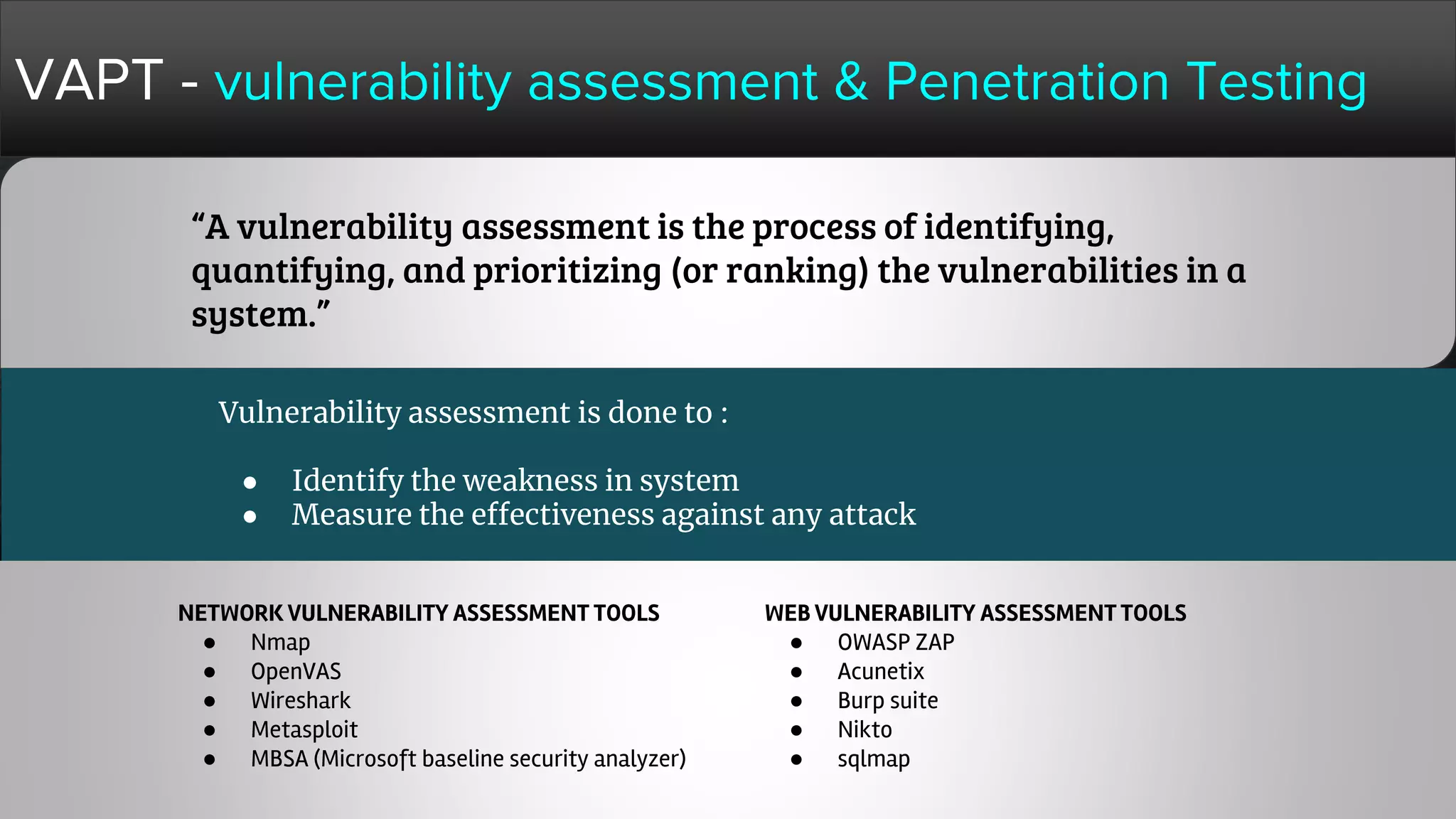
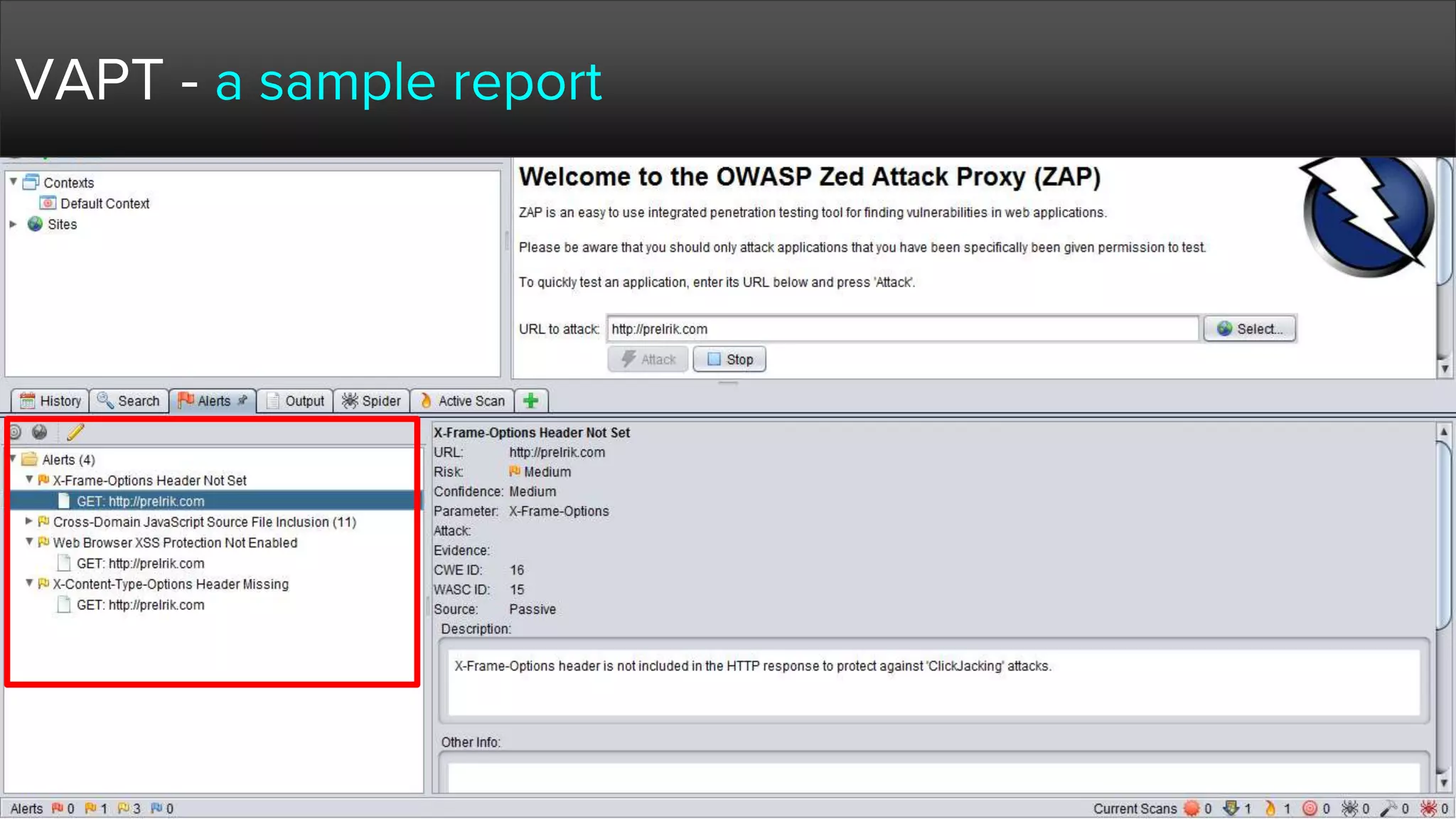
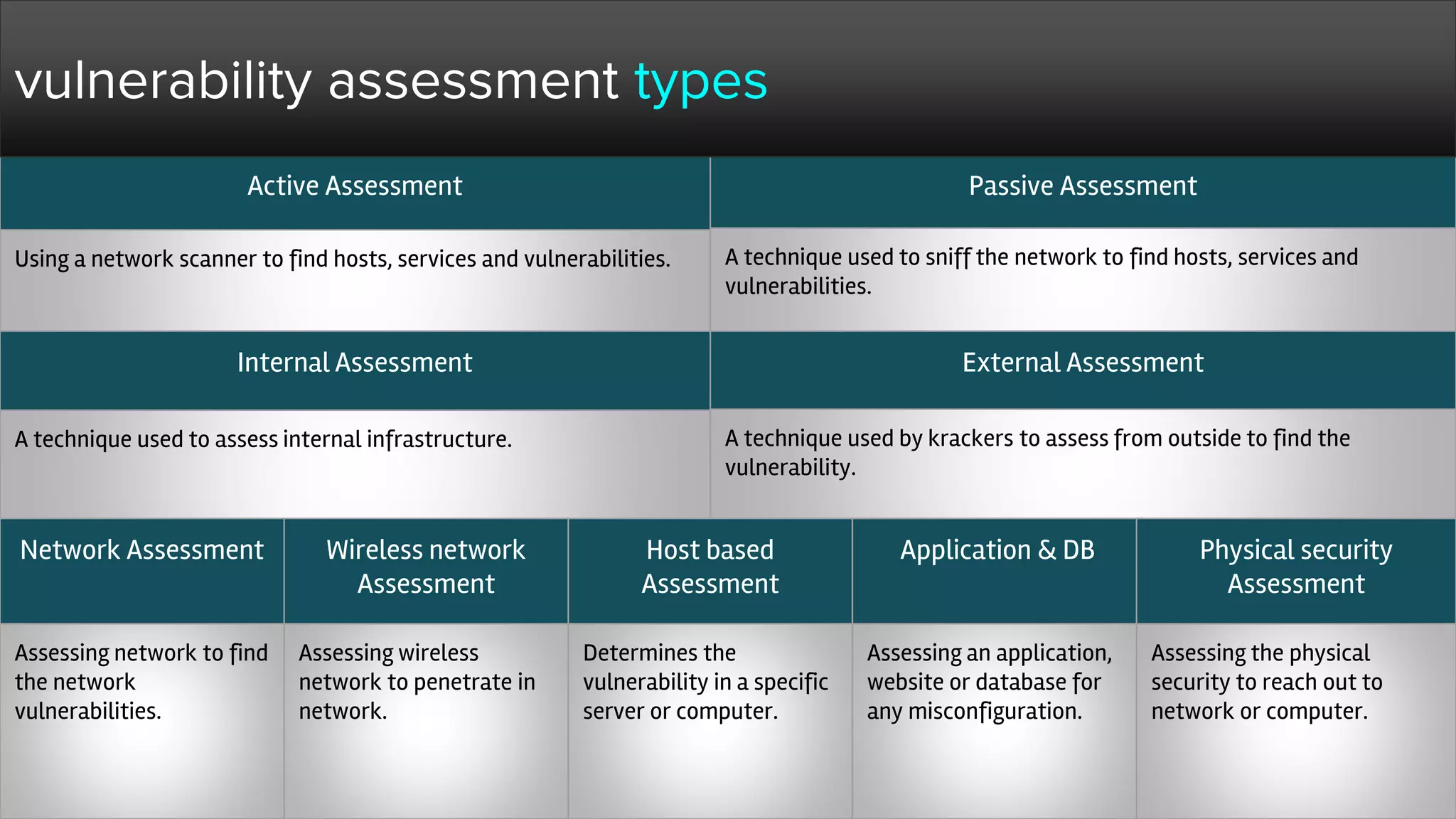
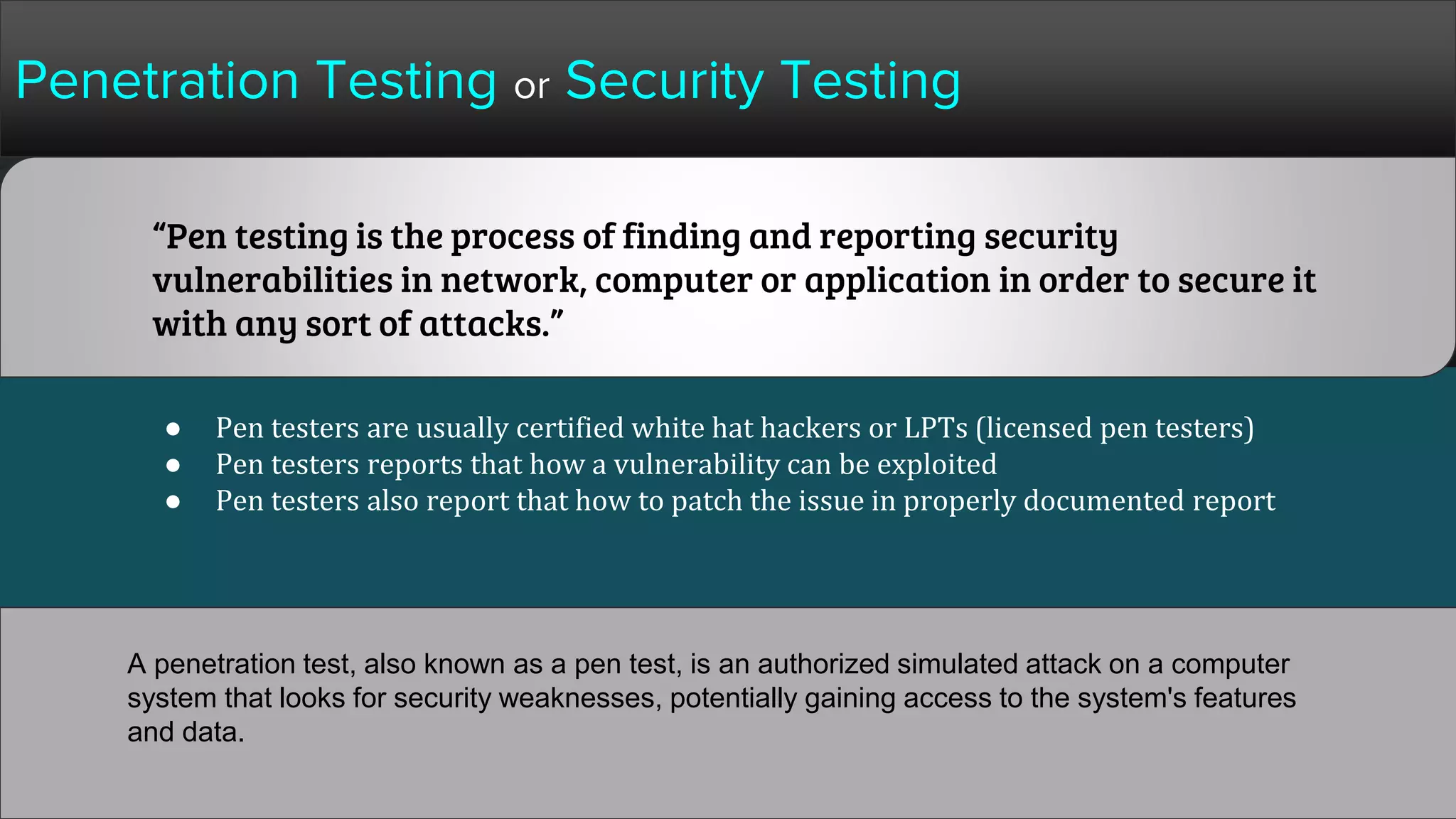
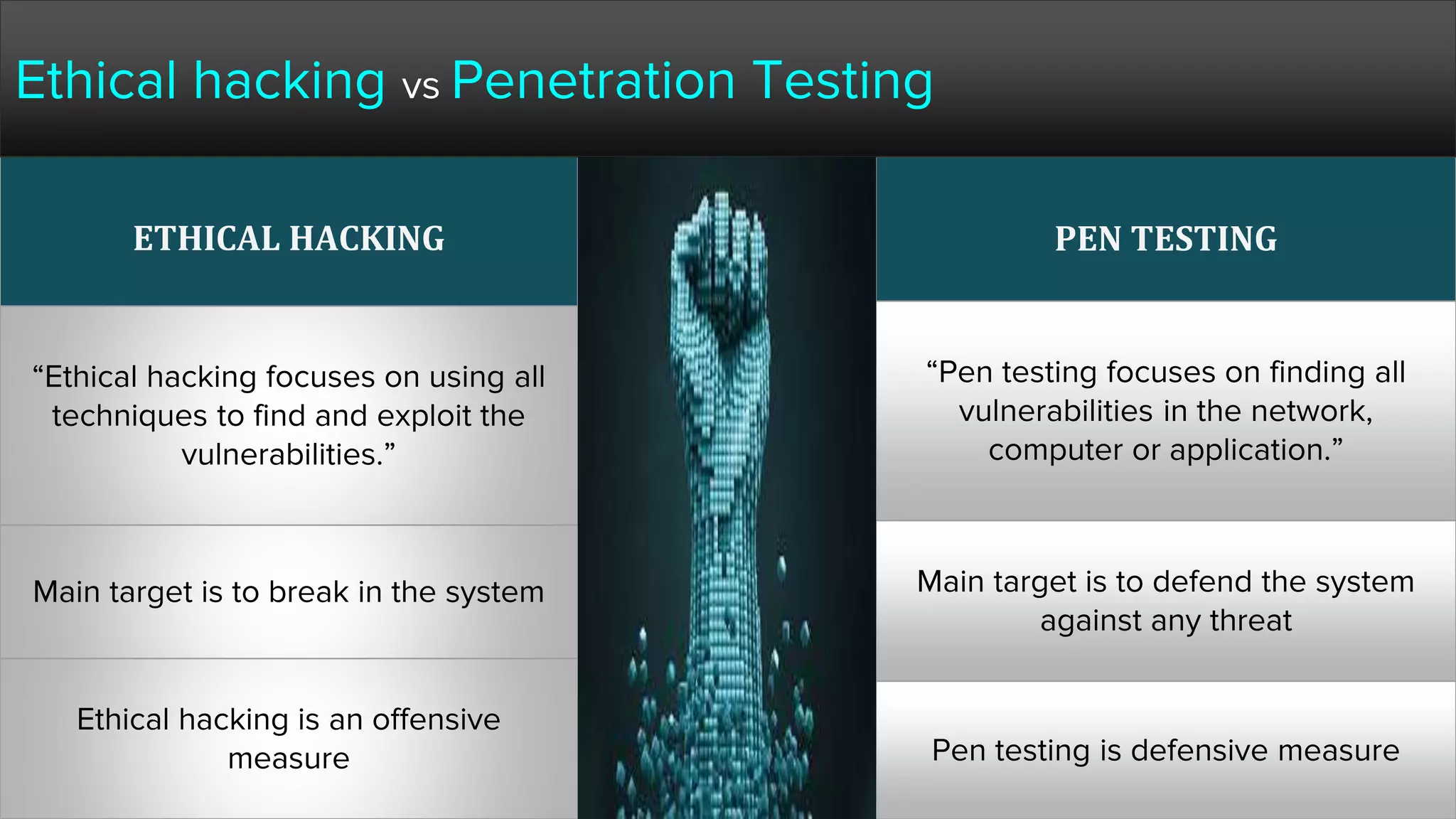
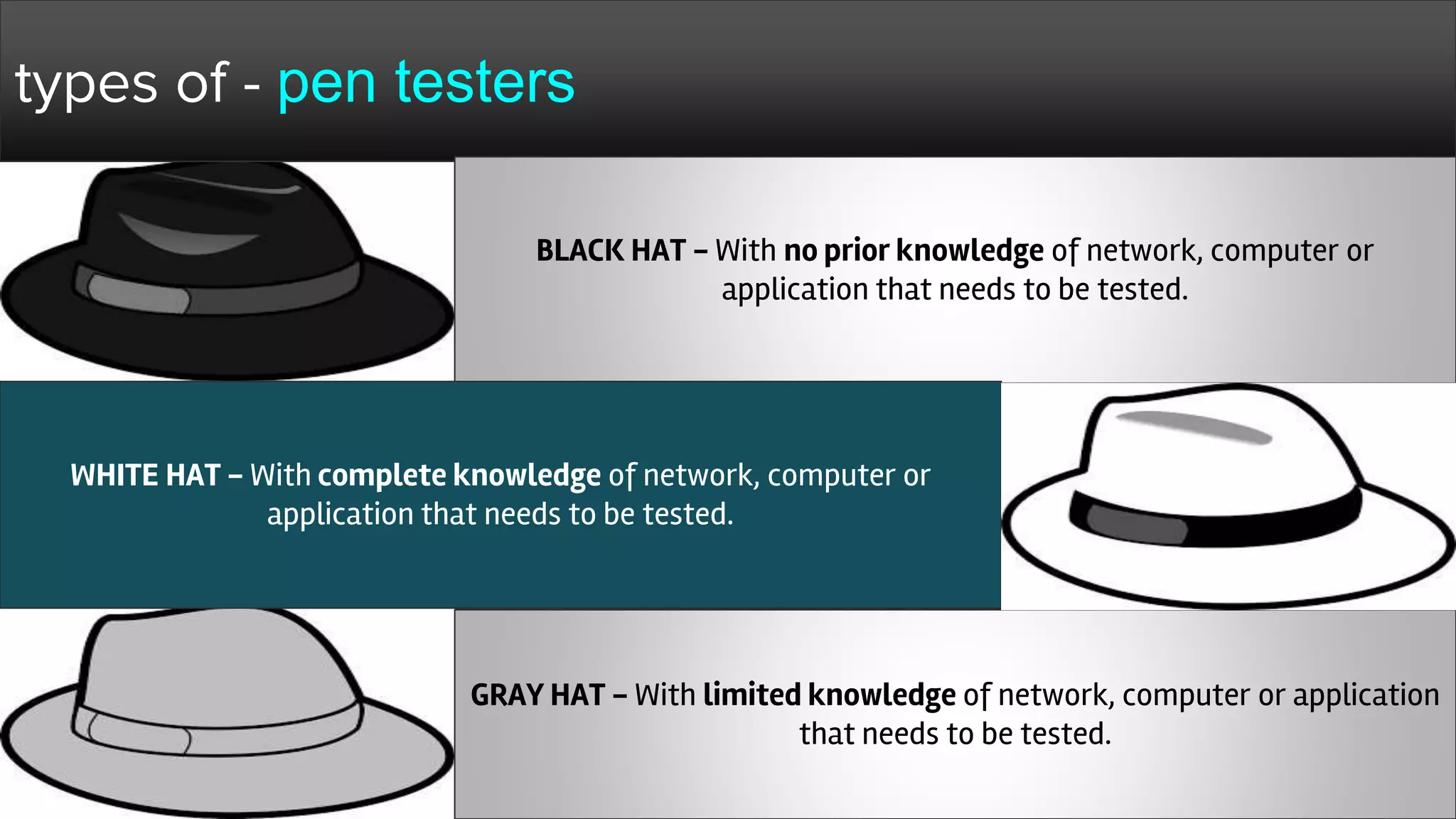
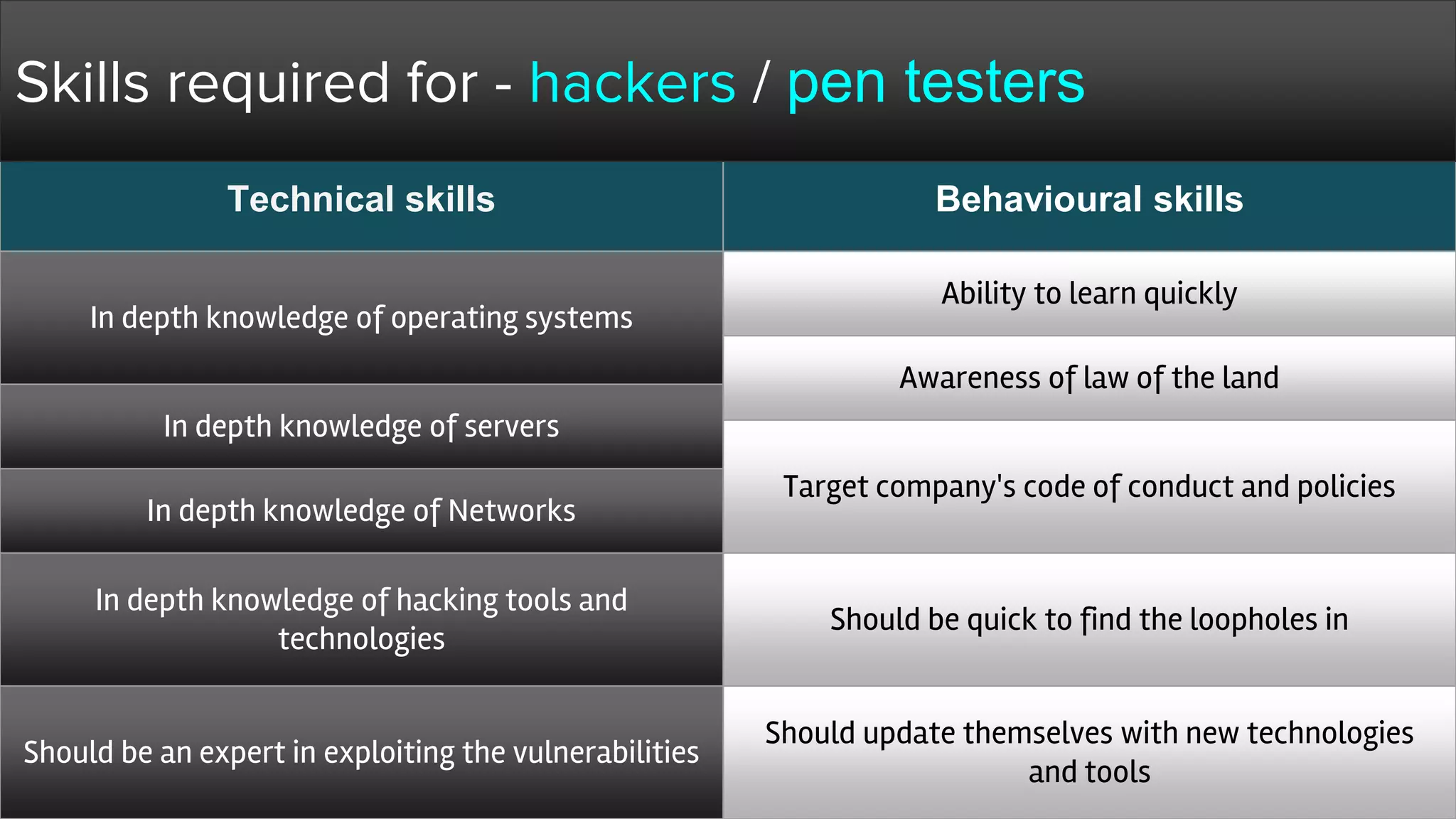
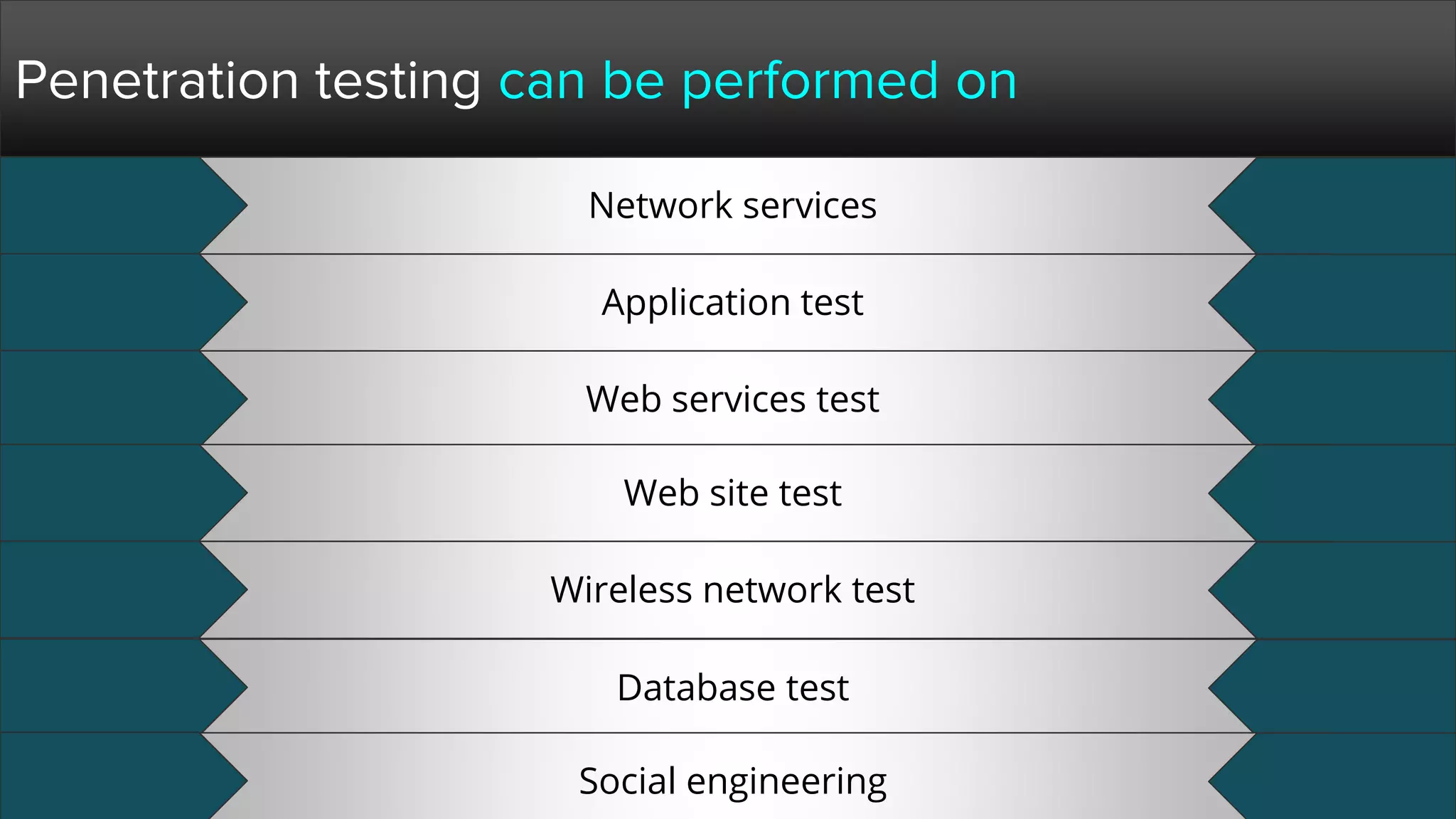
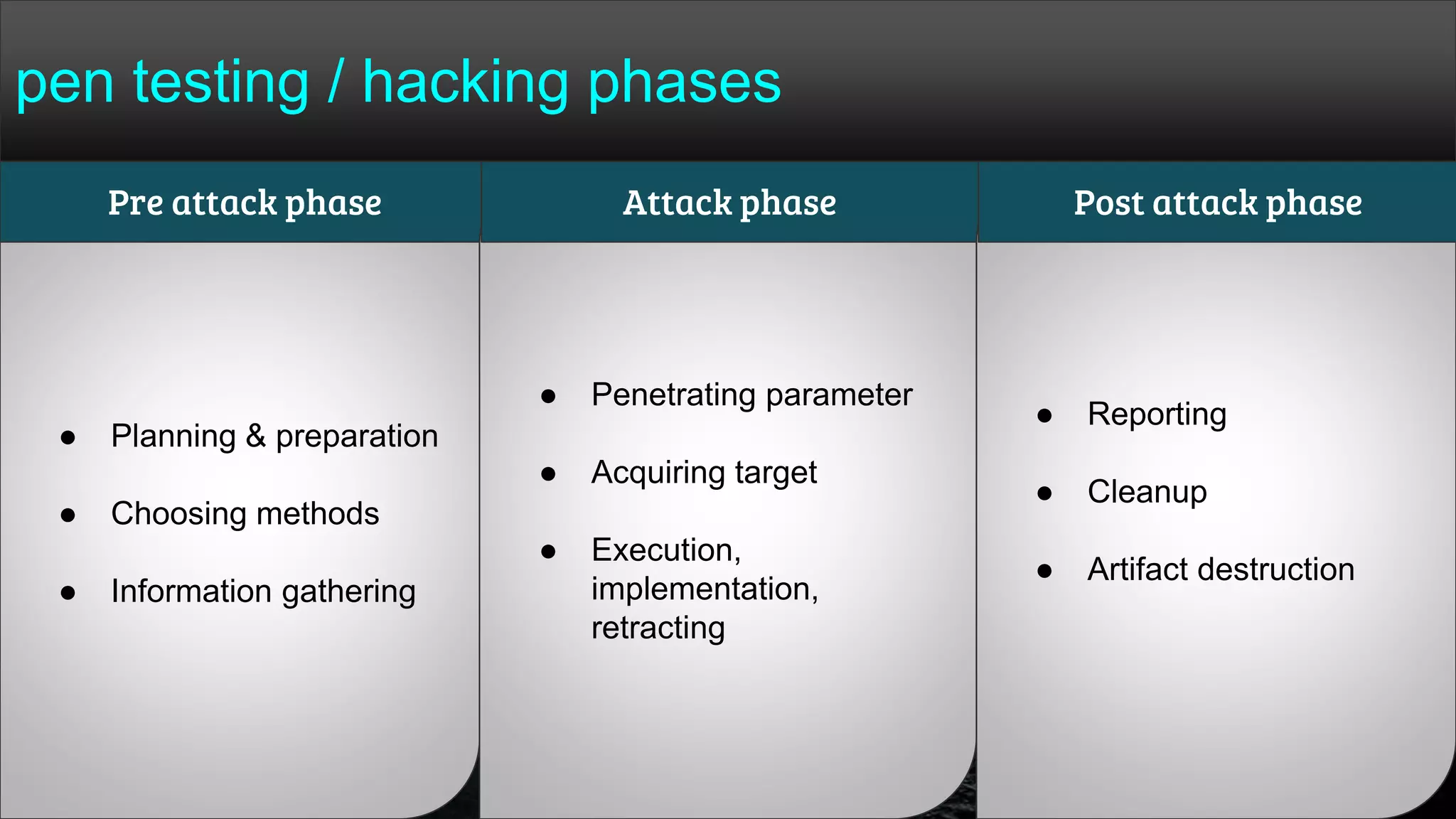
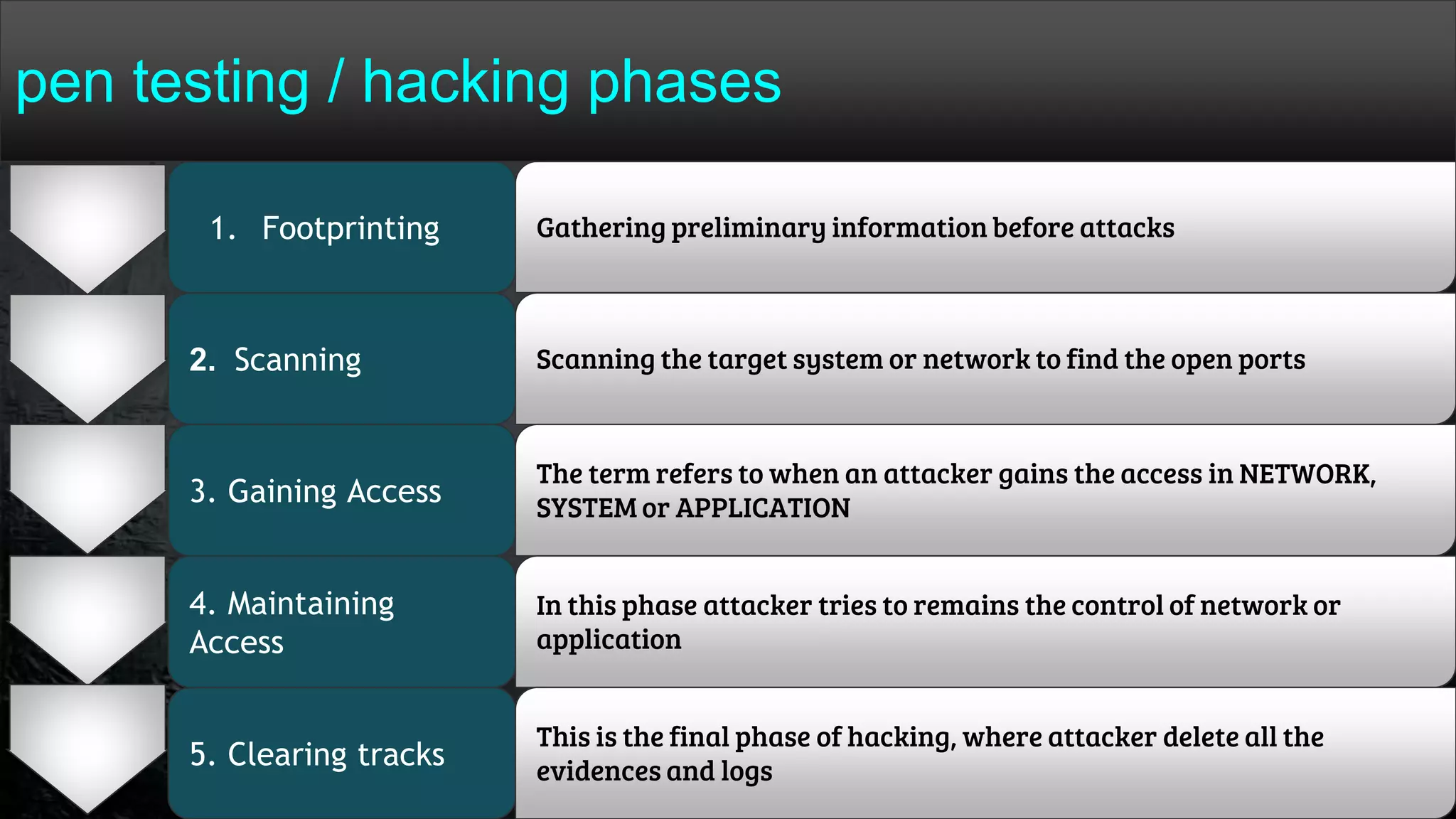
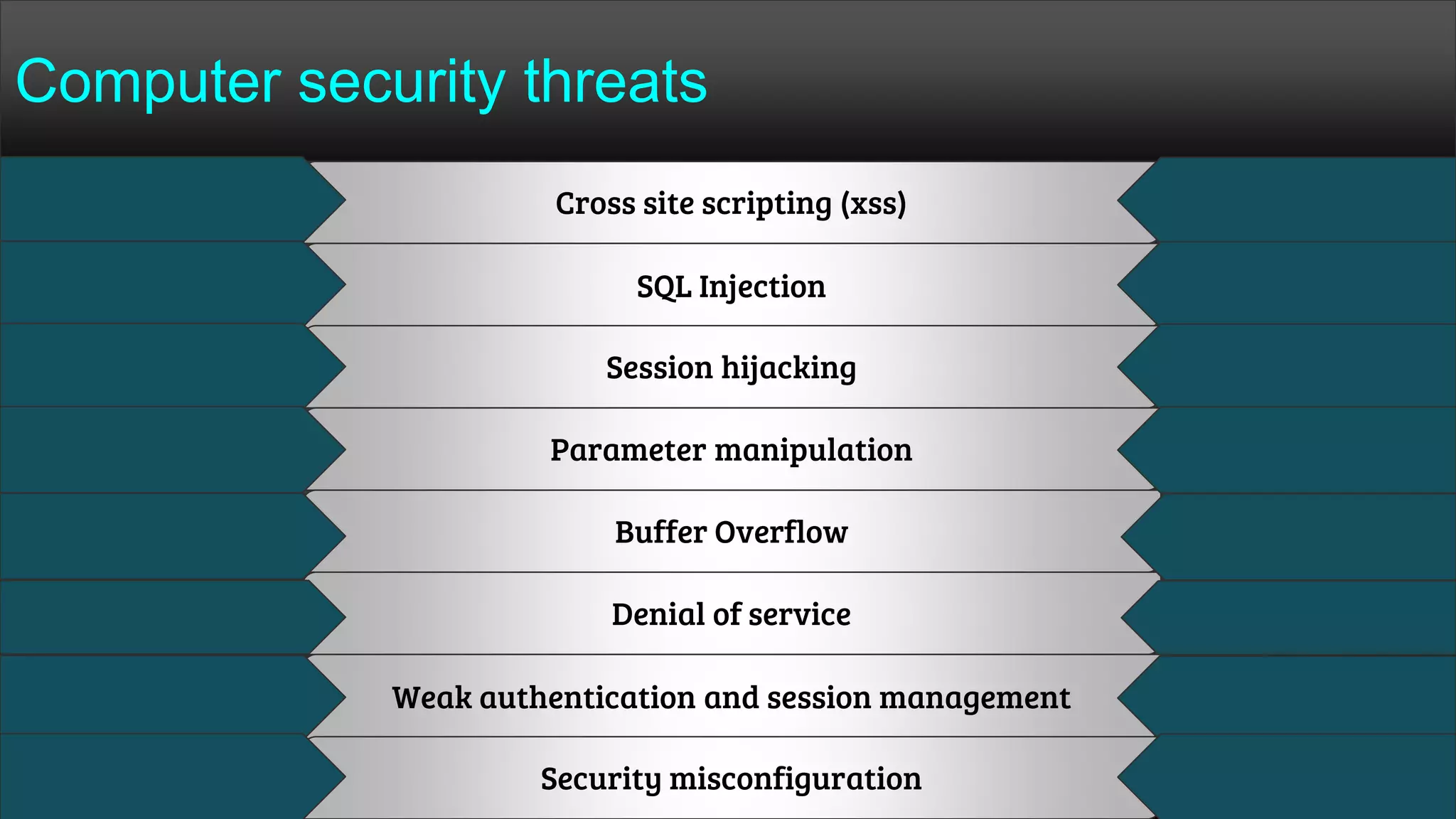
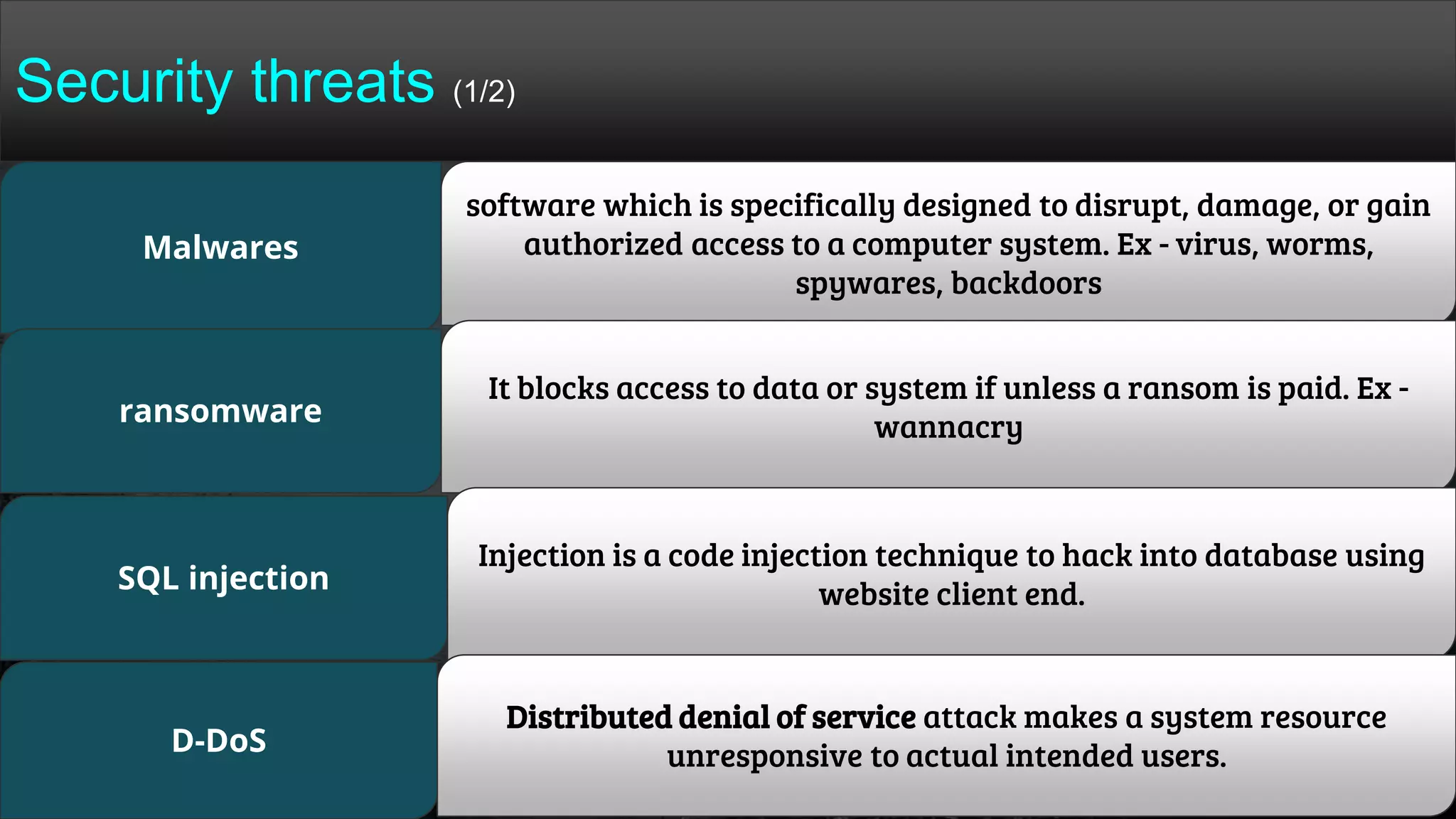
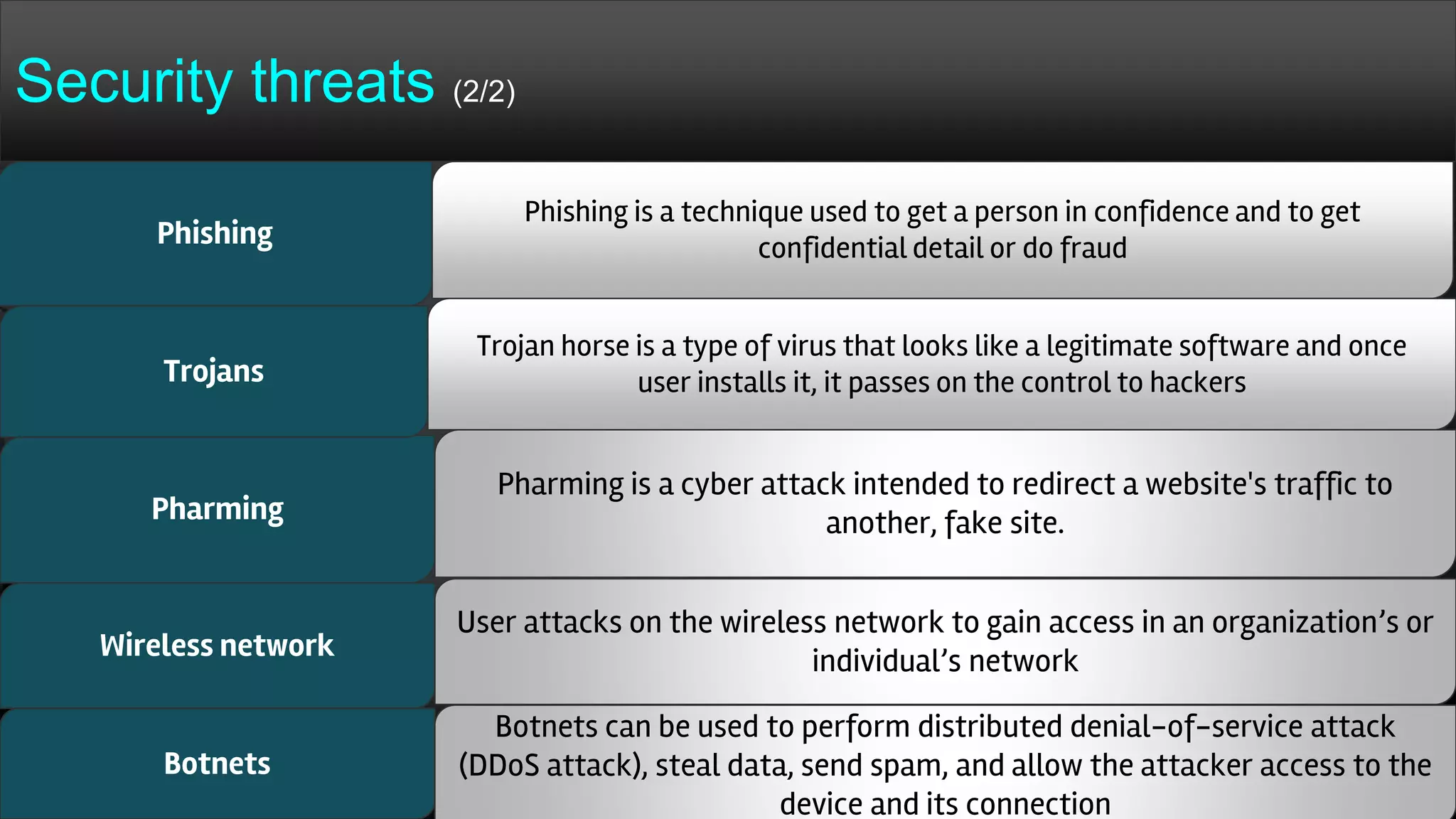
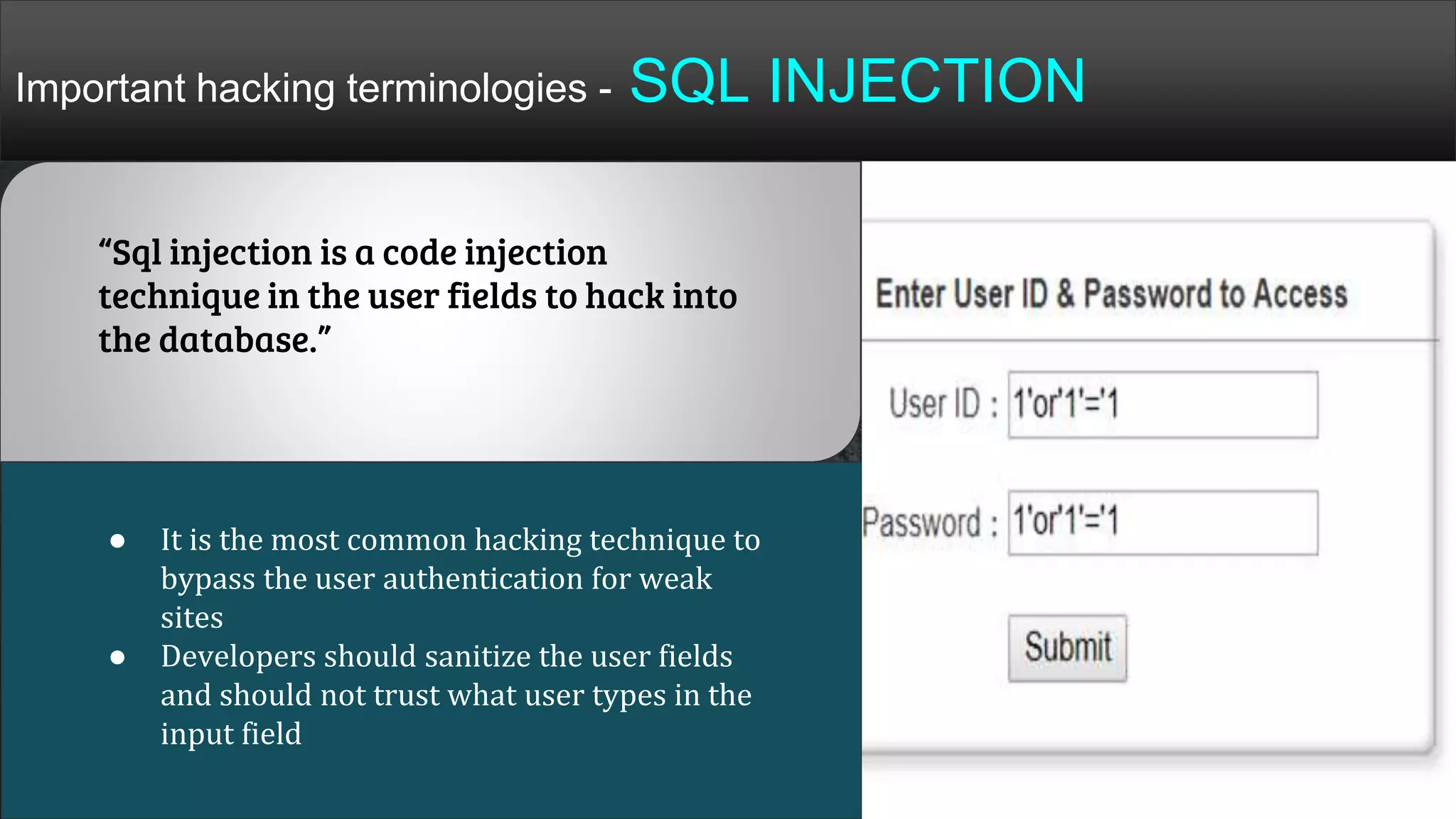
The document provides a comprehensive overview of hacking, cyber security, and penetration testing, highlighting the significance of vulnerability assessment in protecting systems from cyber crimes. It distinguishes between different types of hackers, such as black hat and white hat, and introduces concepts like ethical hacking and digital forensics. Additionally, it discusses various cyber threats, techniques used for attacks, and the importance of continuous learning in the field of cybersecurity.