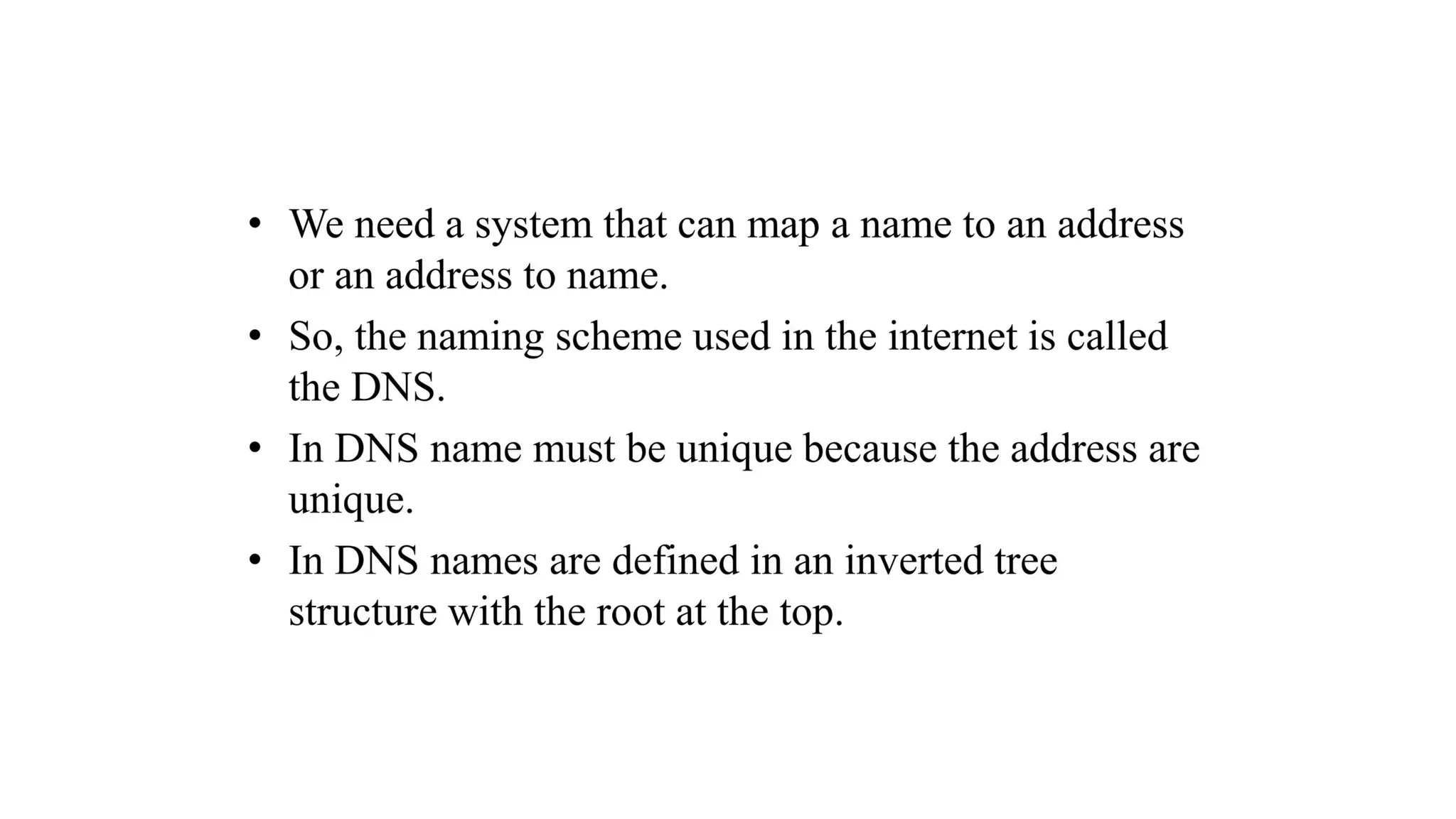
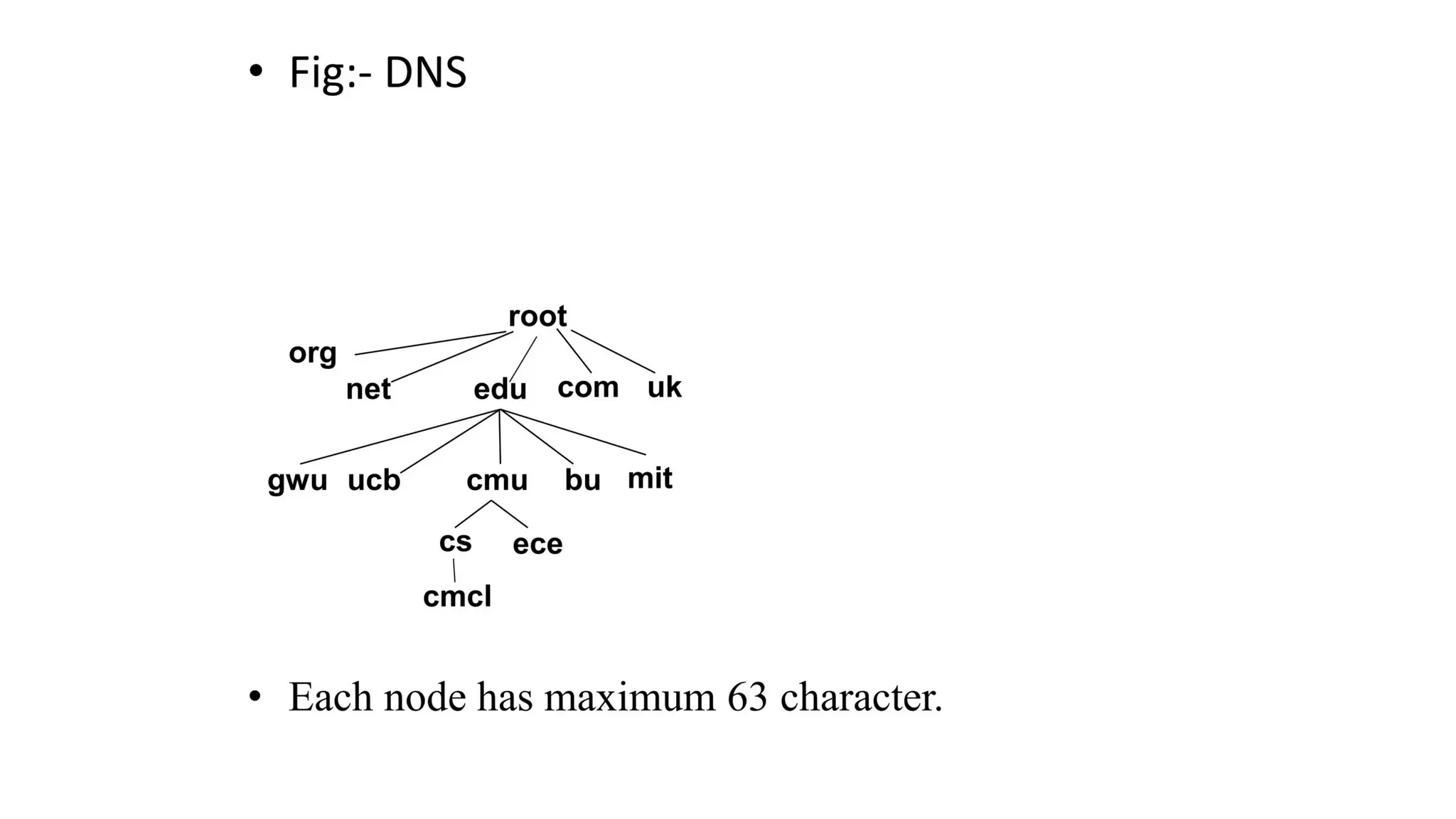
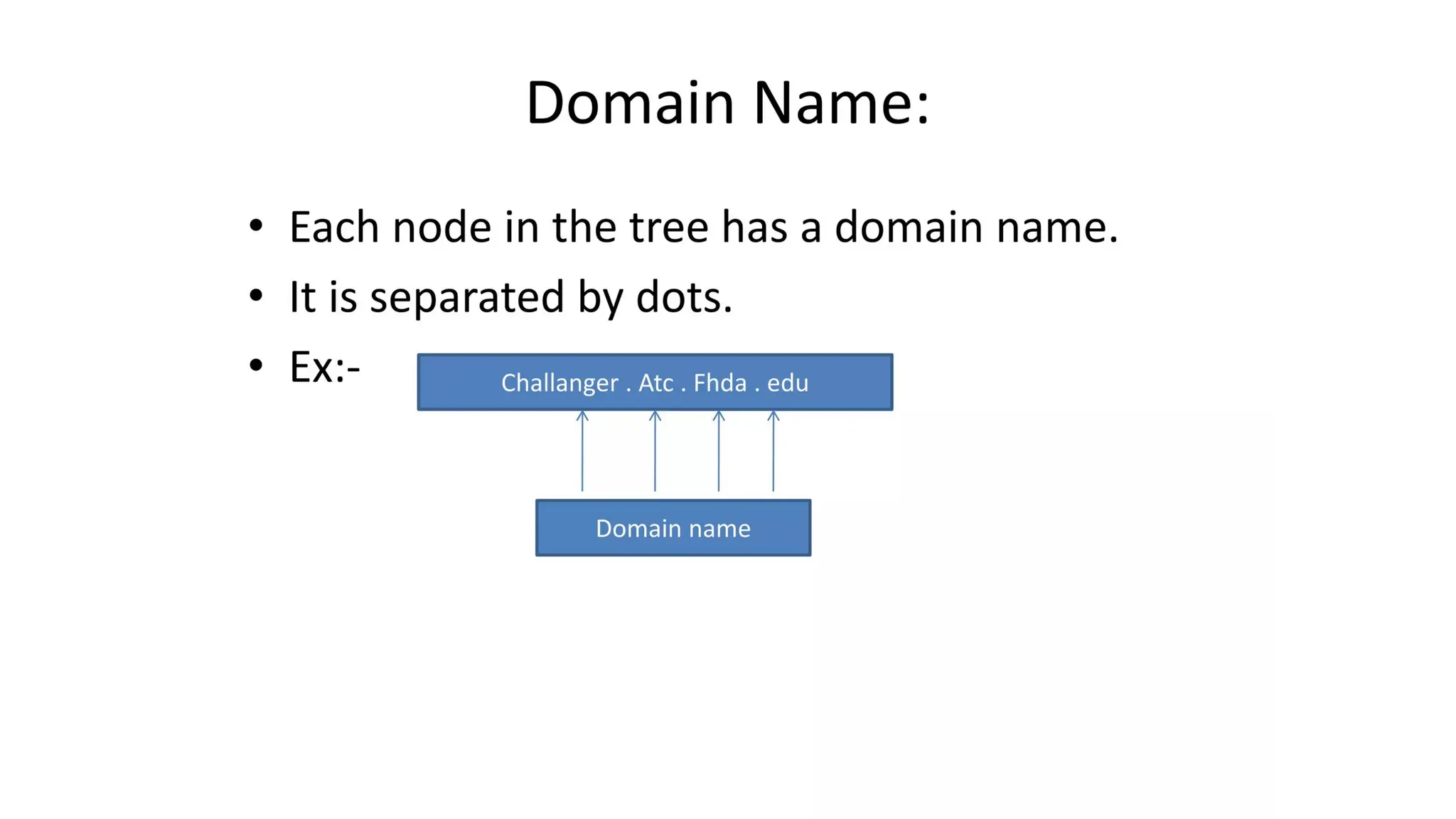
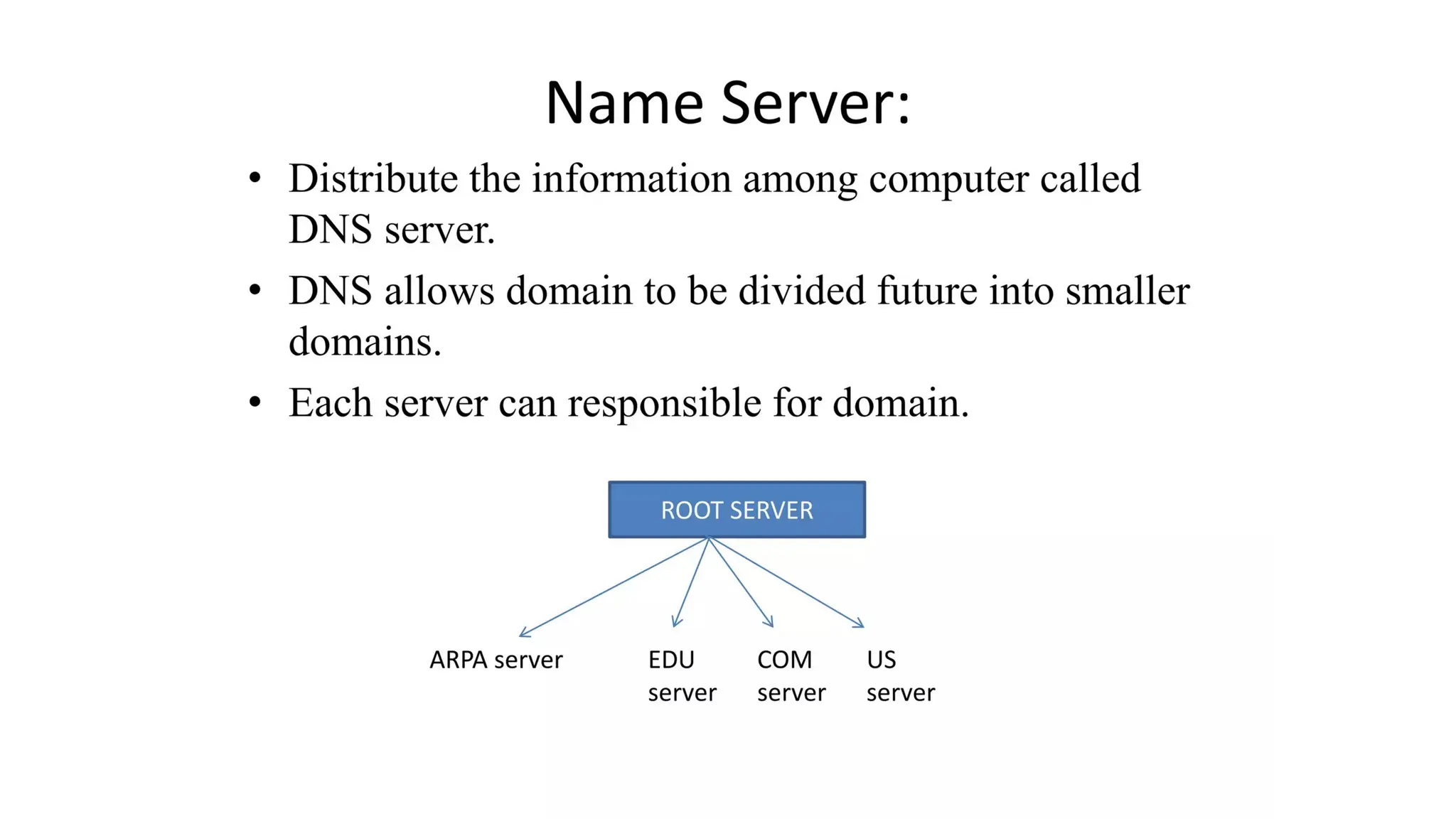
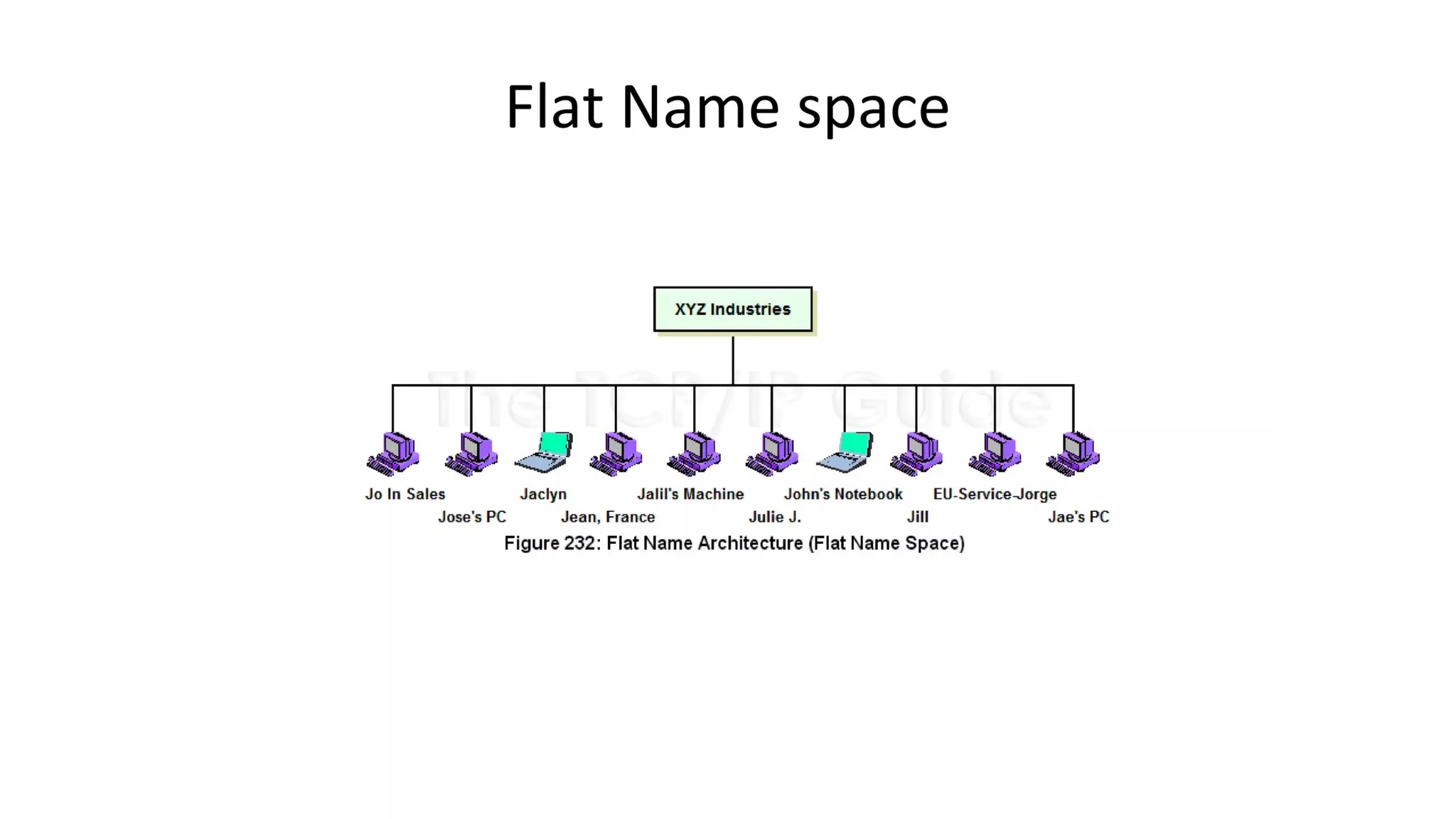
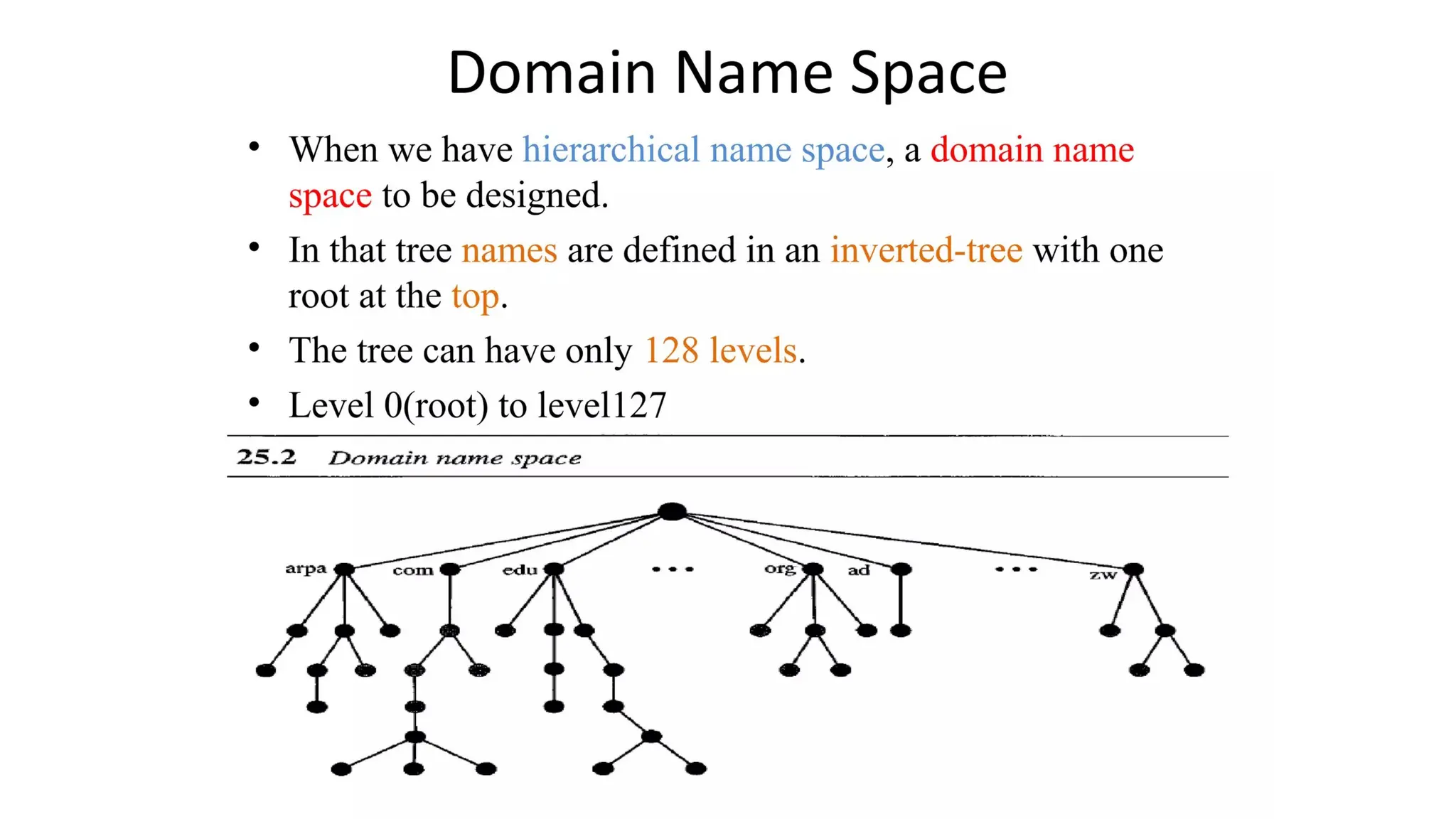
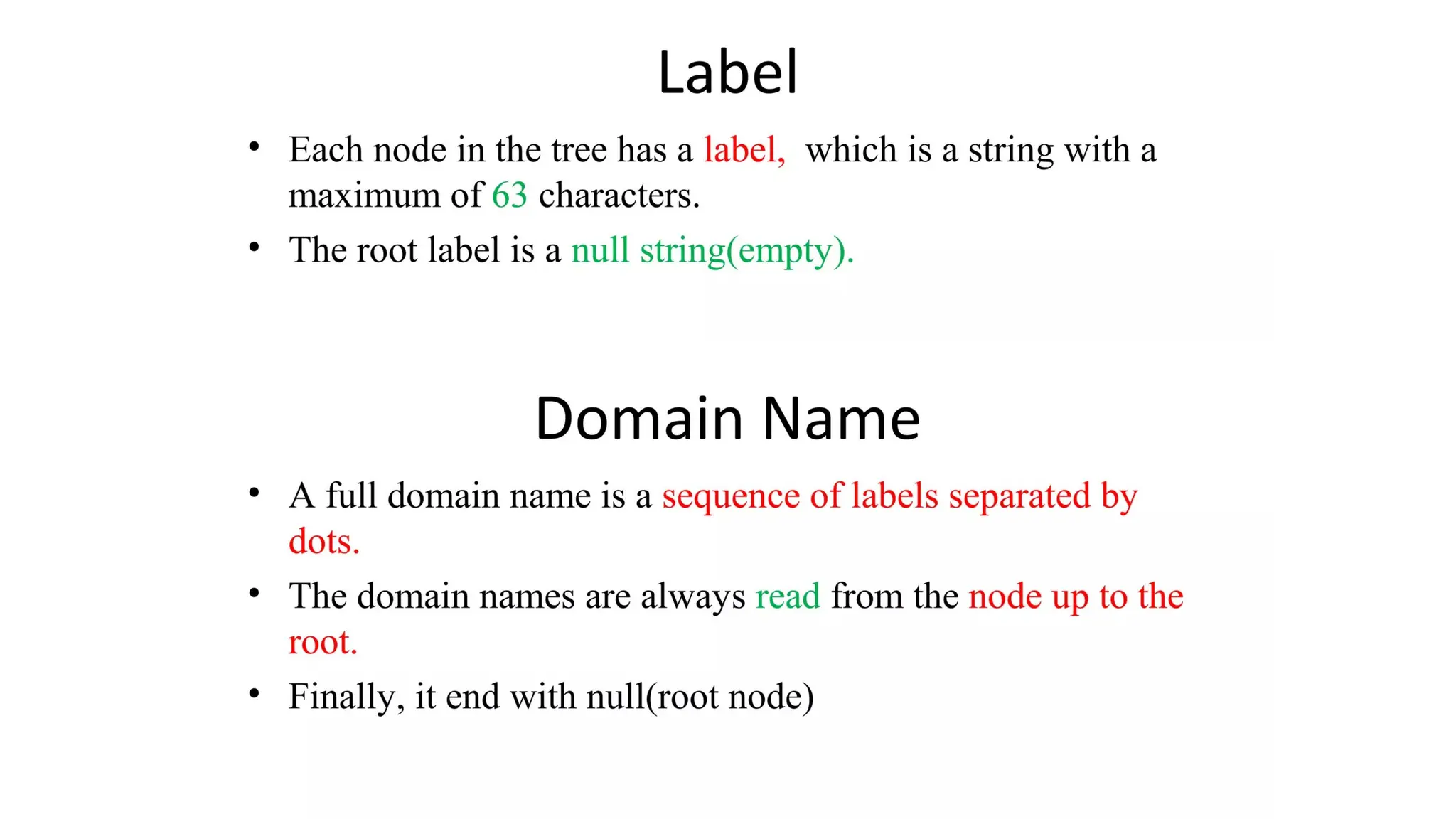
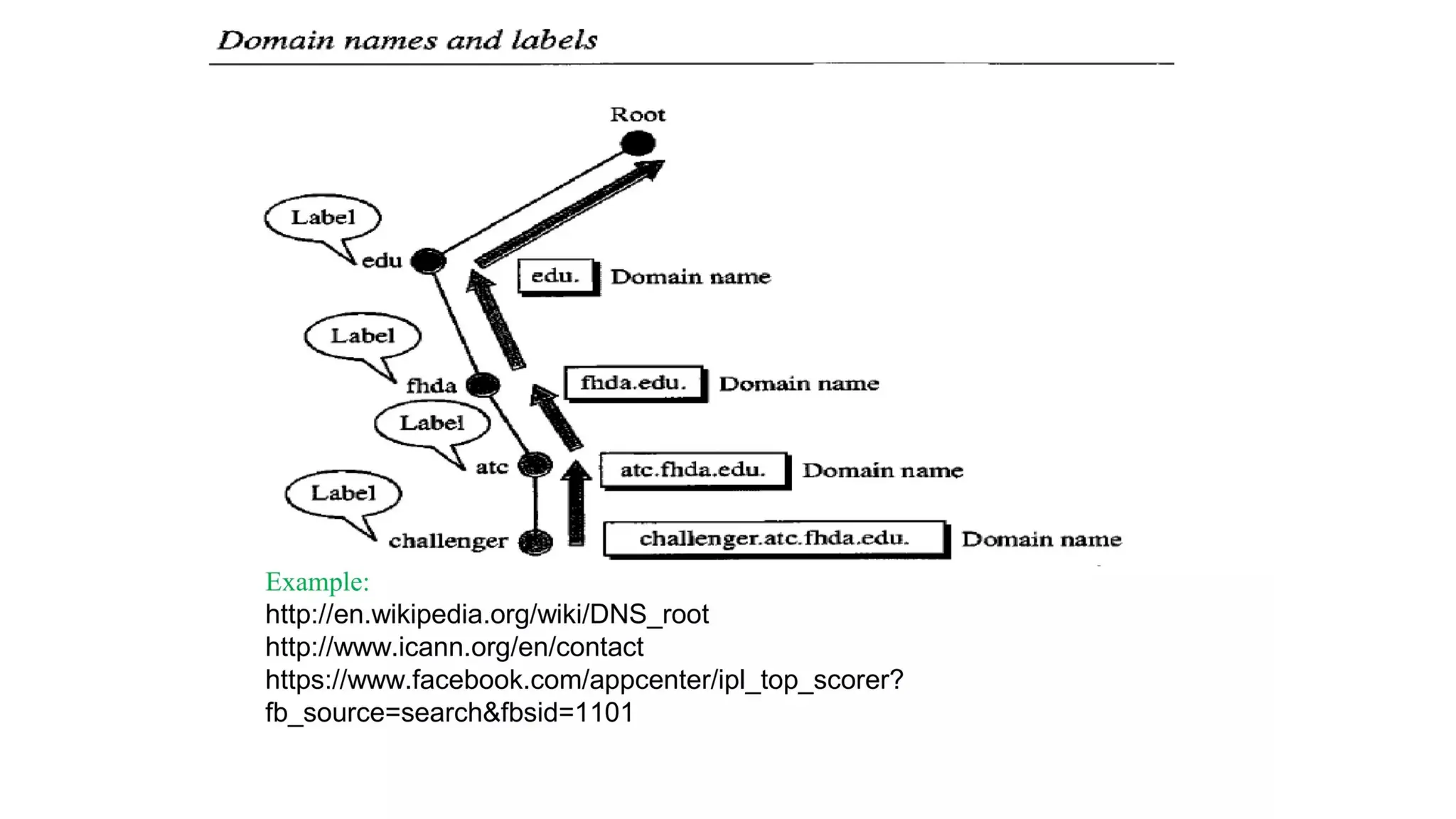
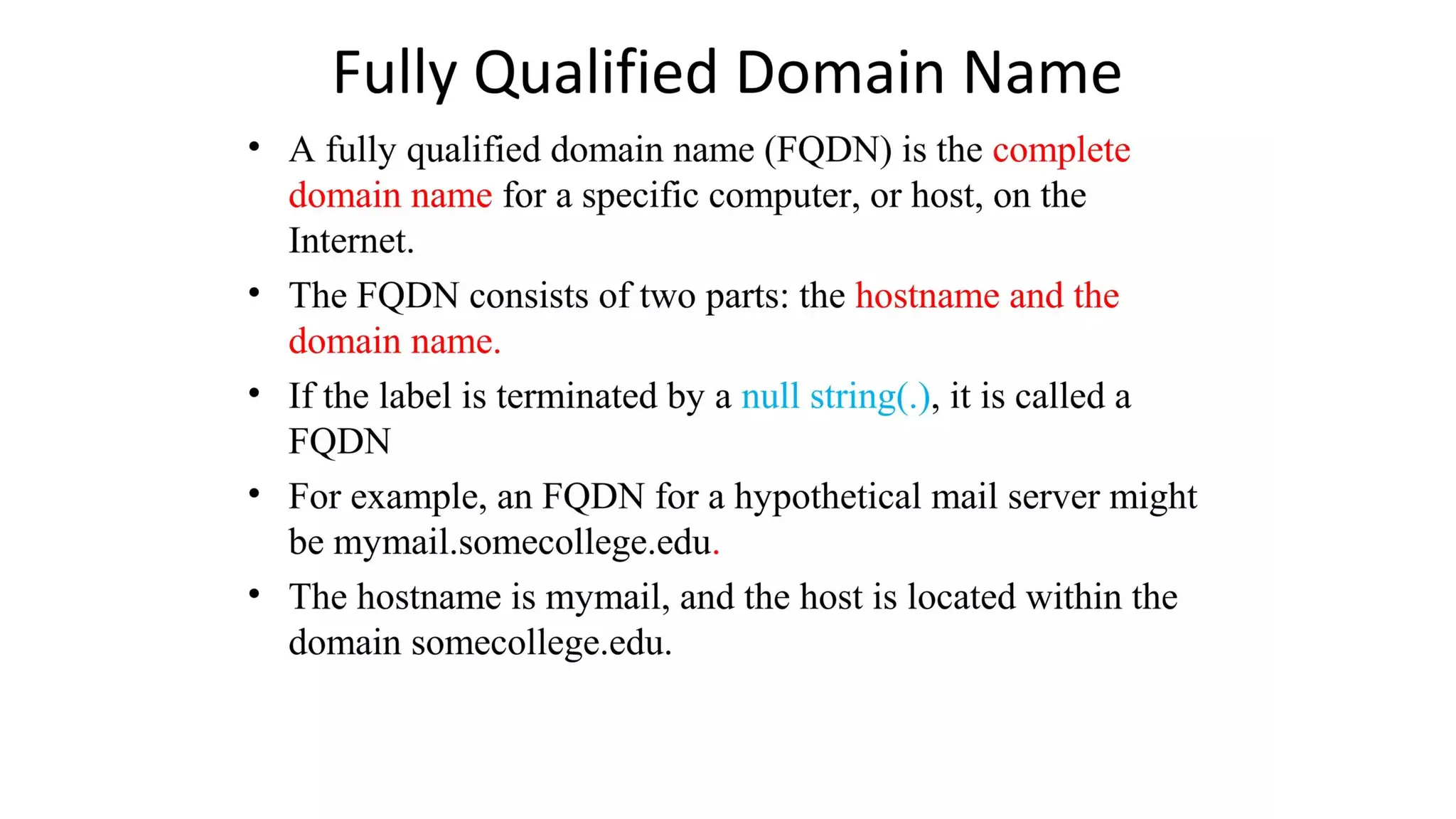
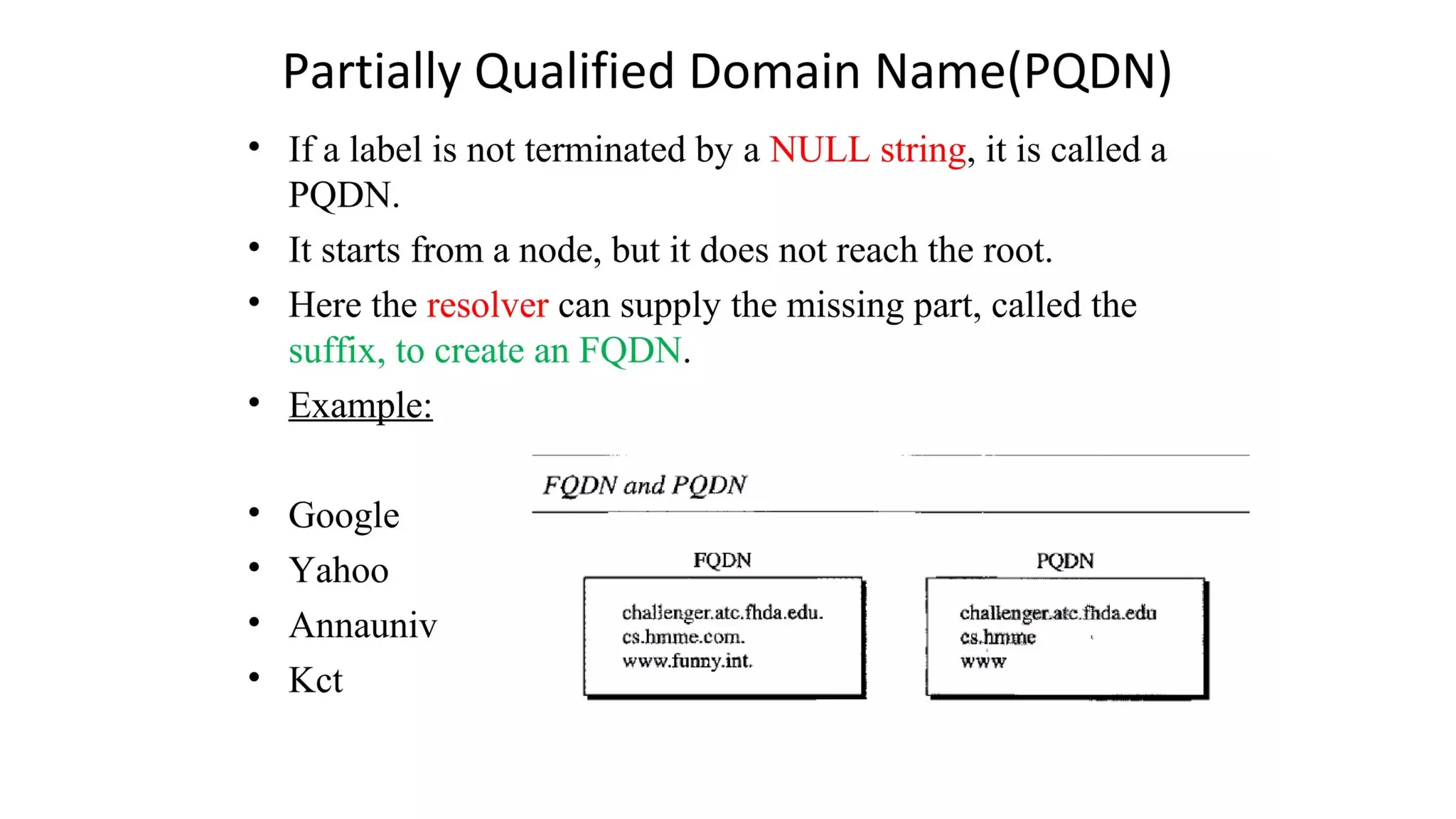
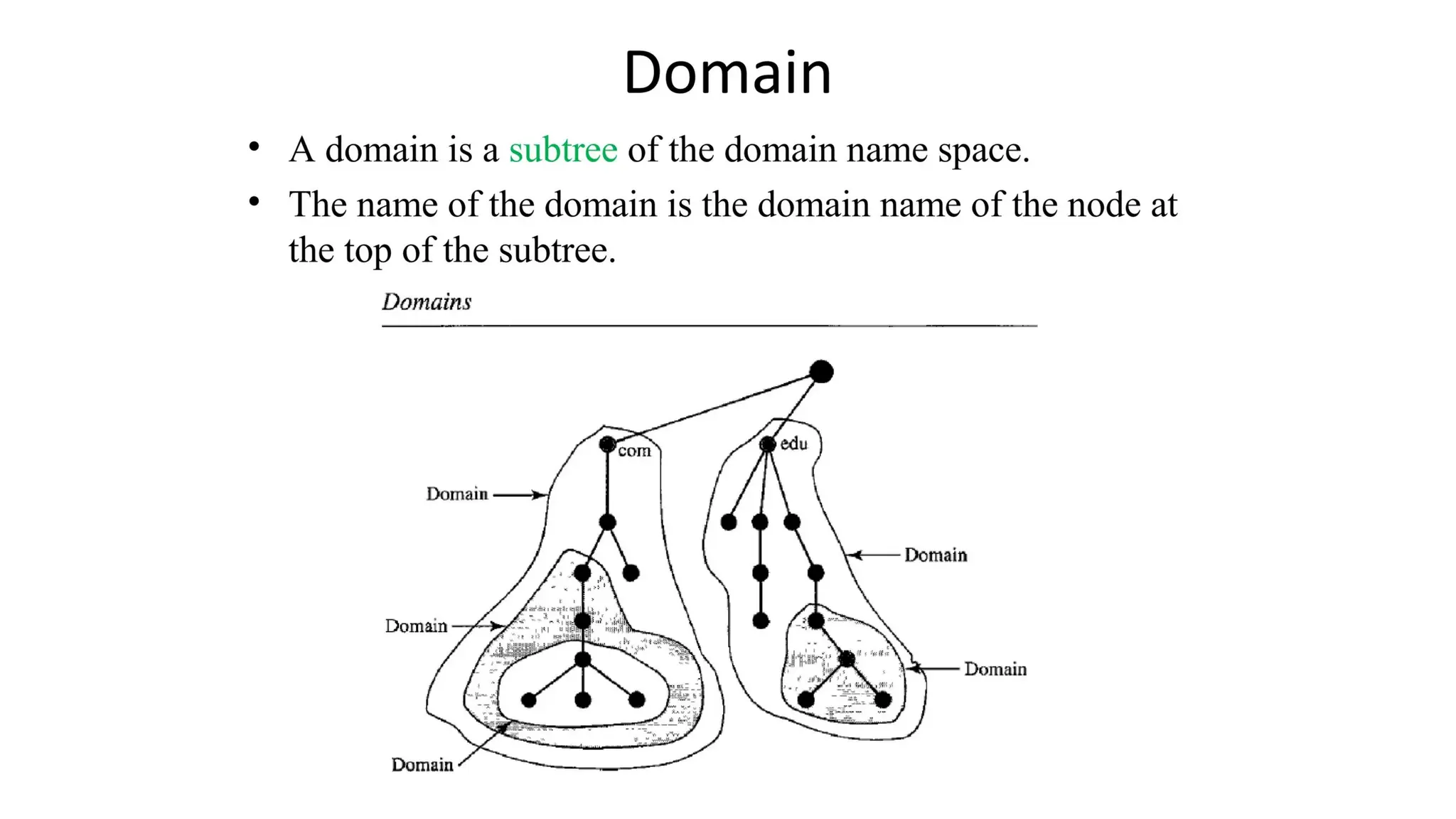
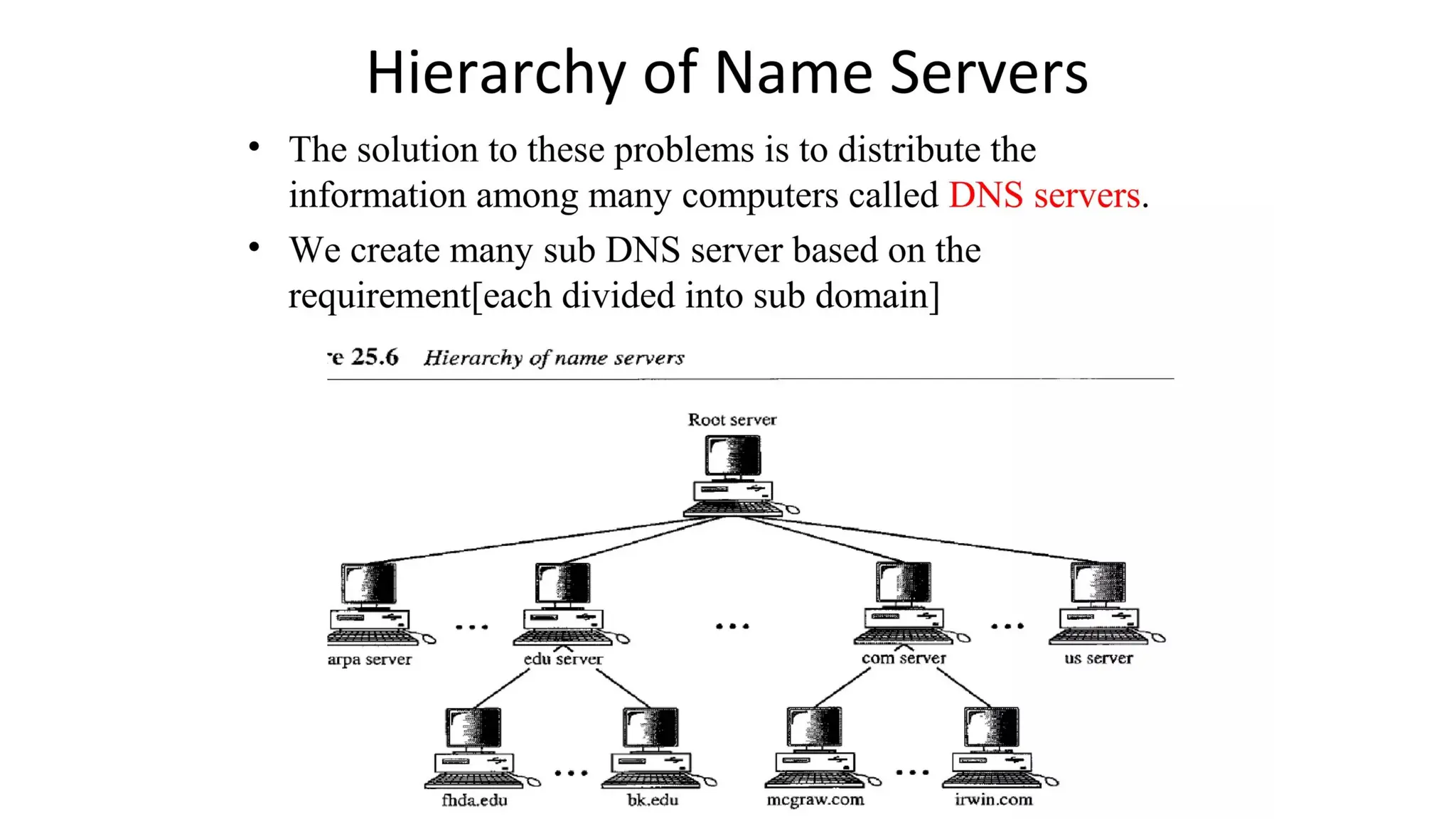
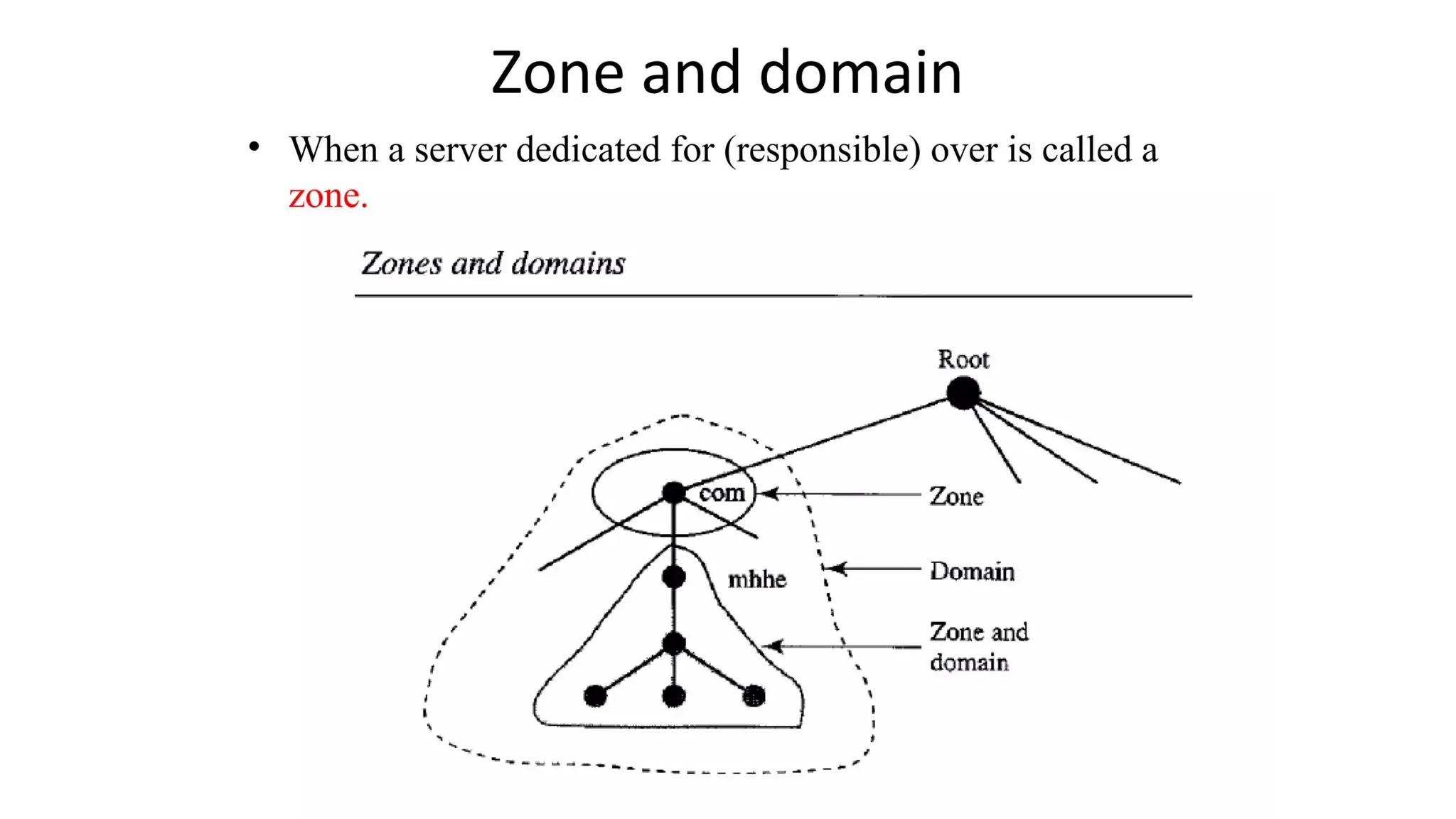
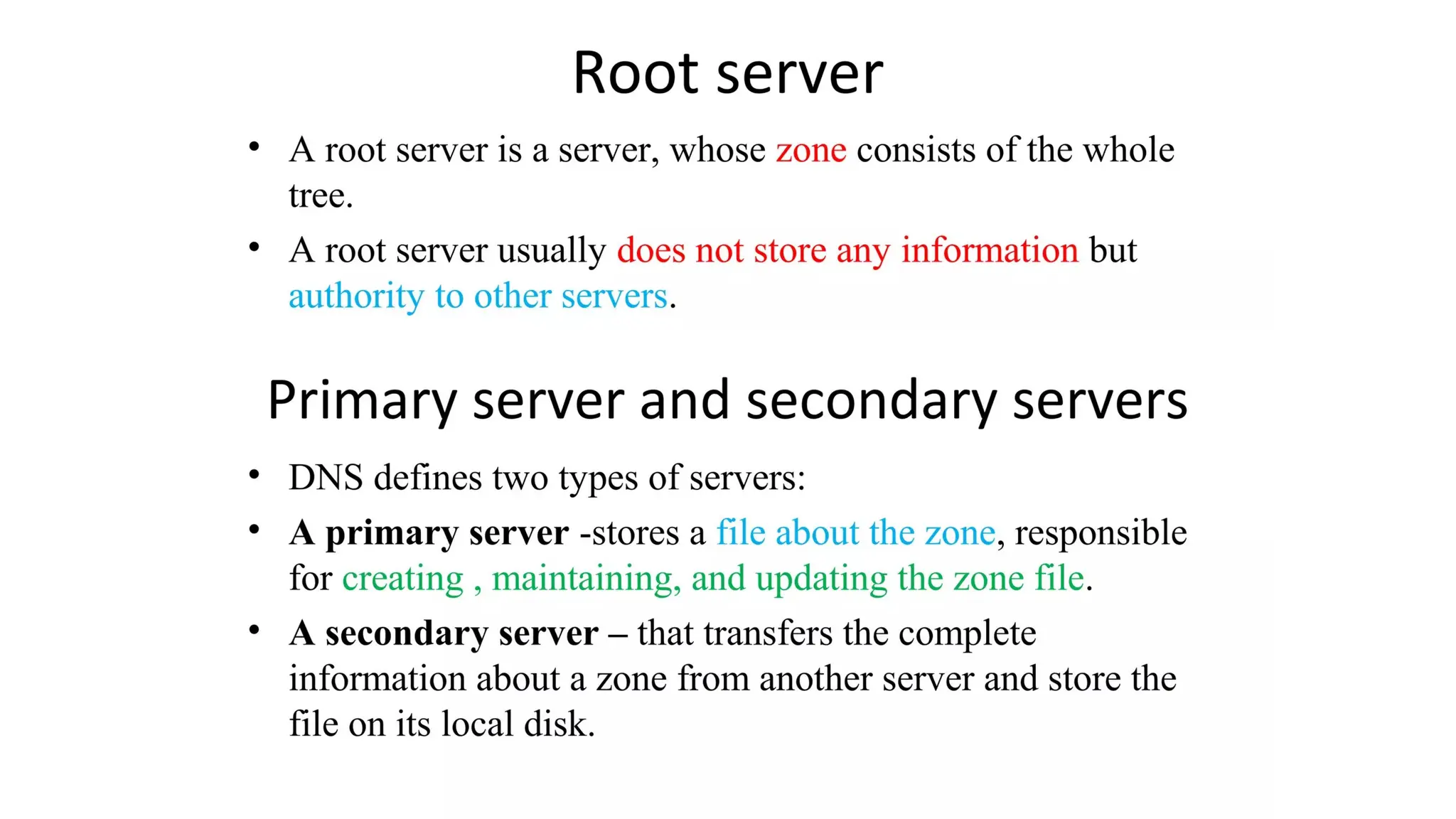
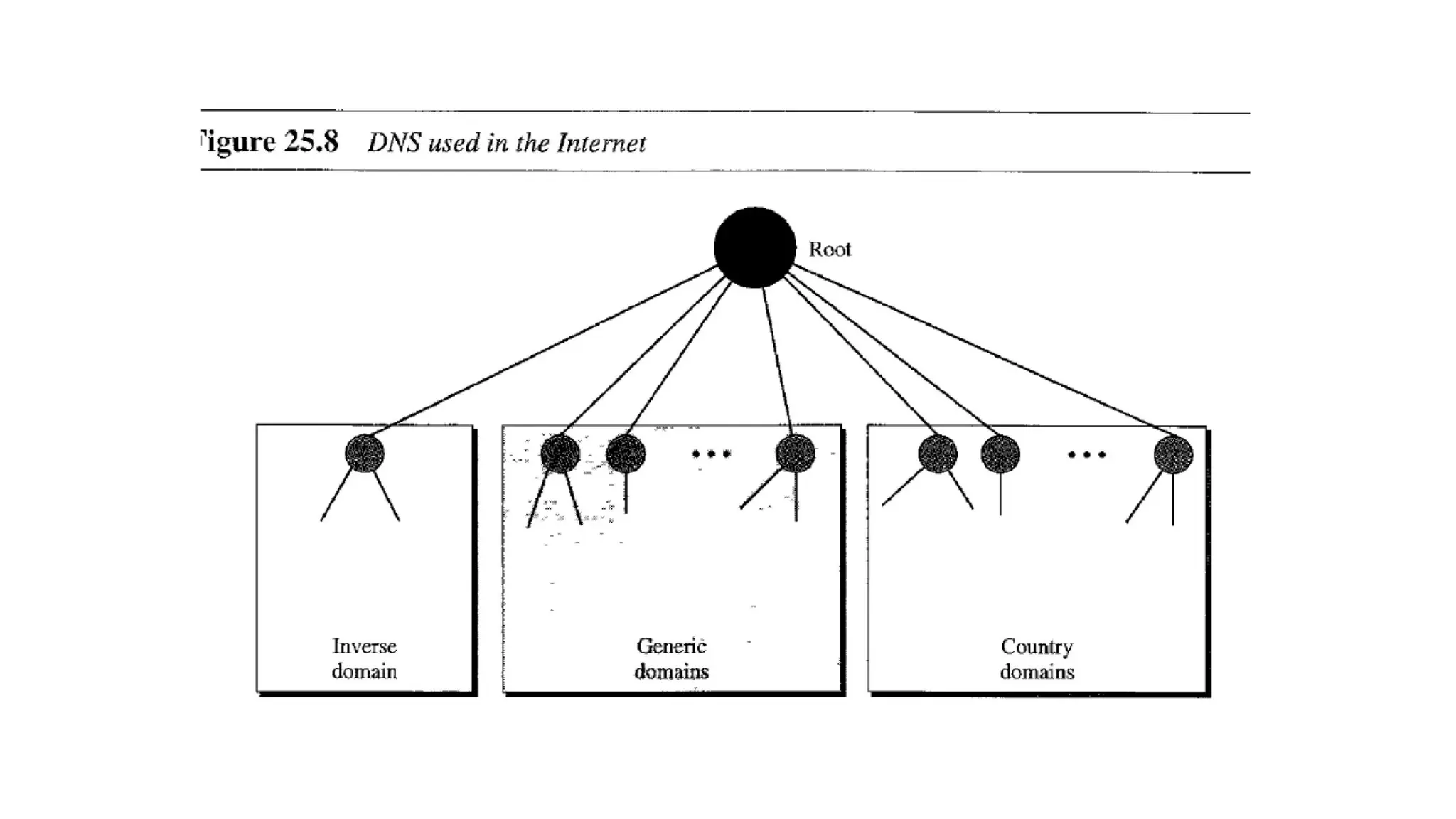
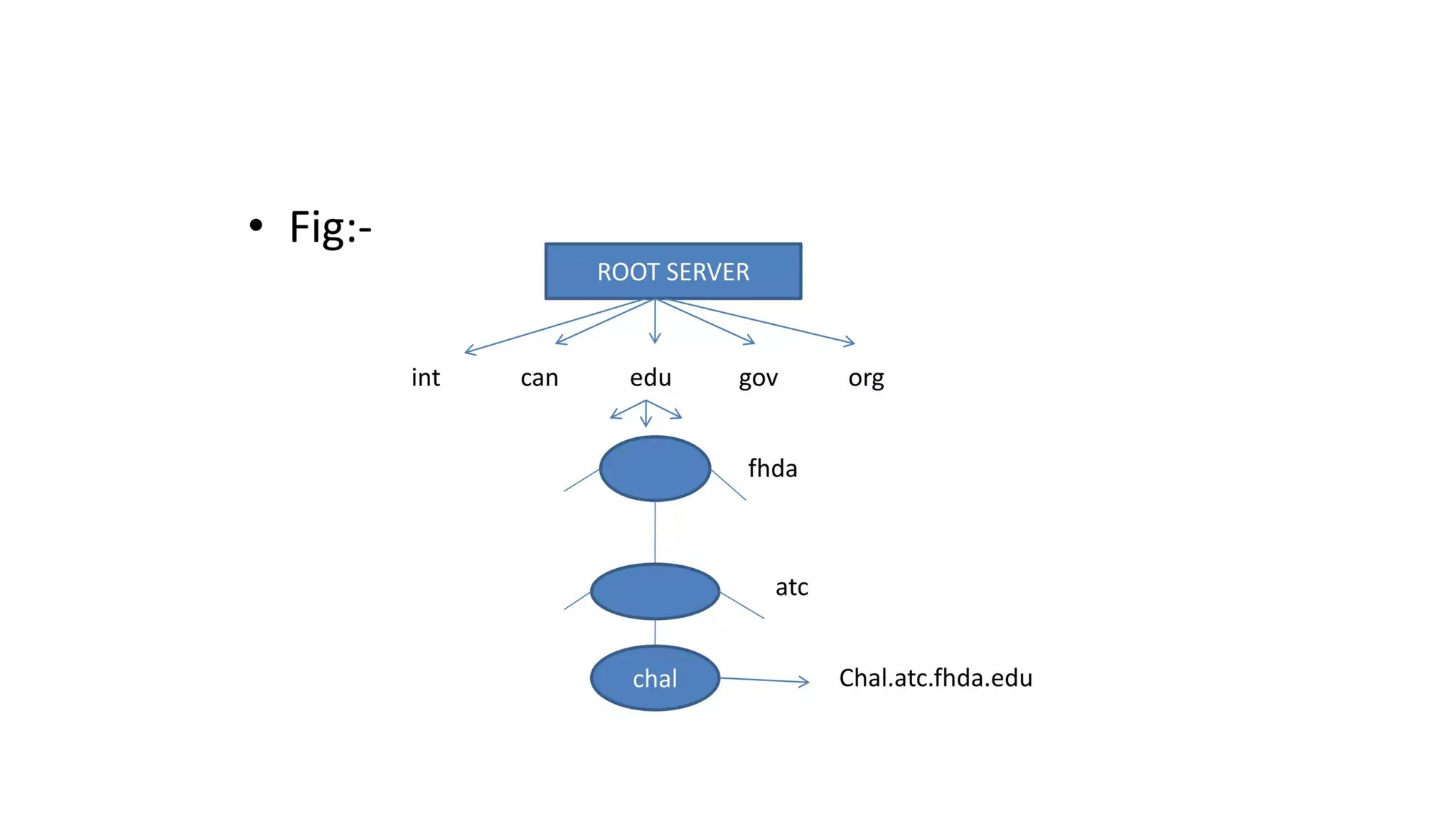
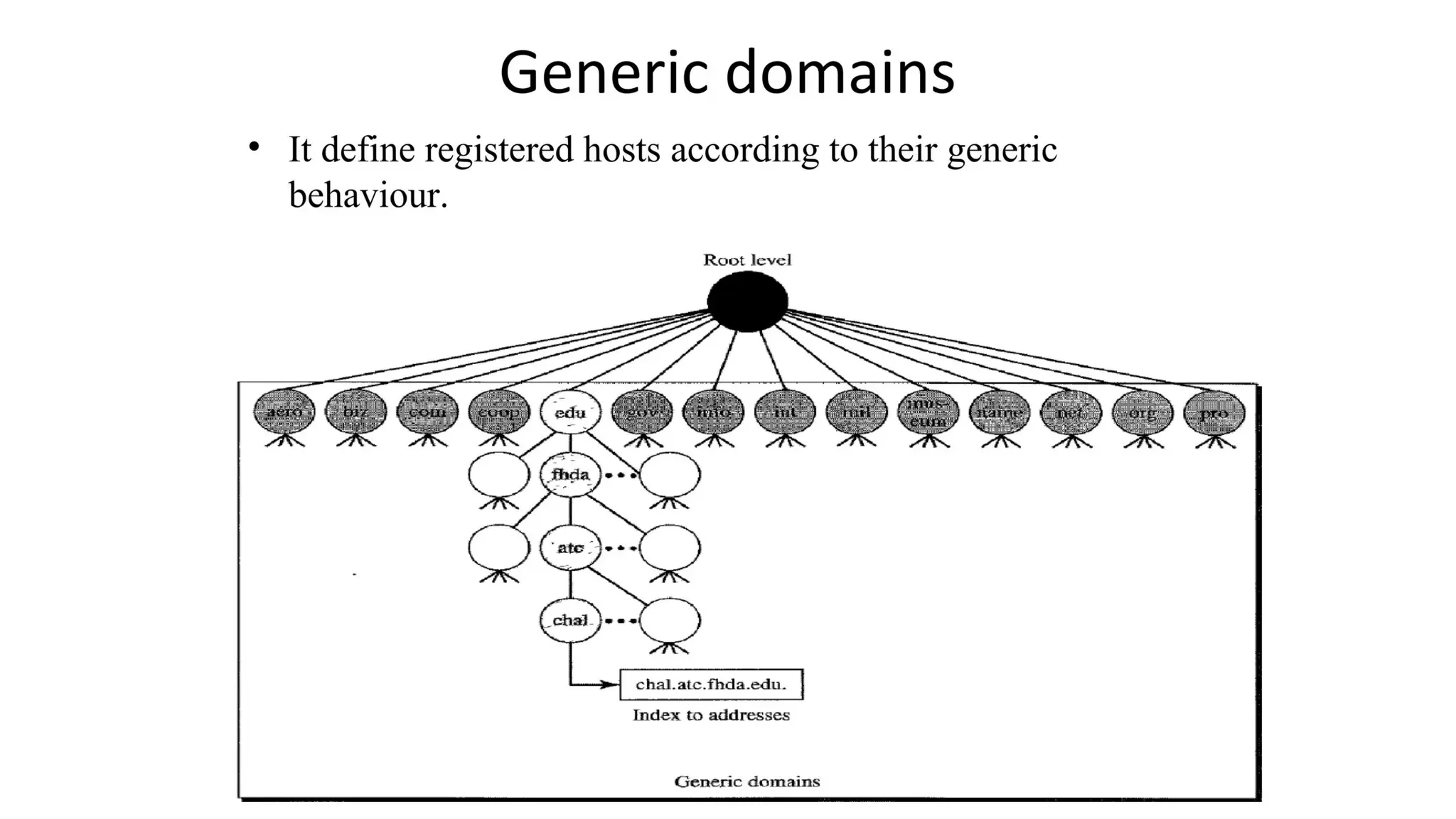
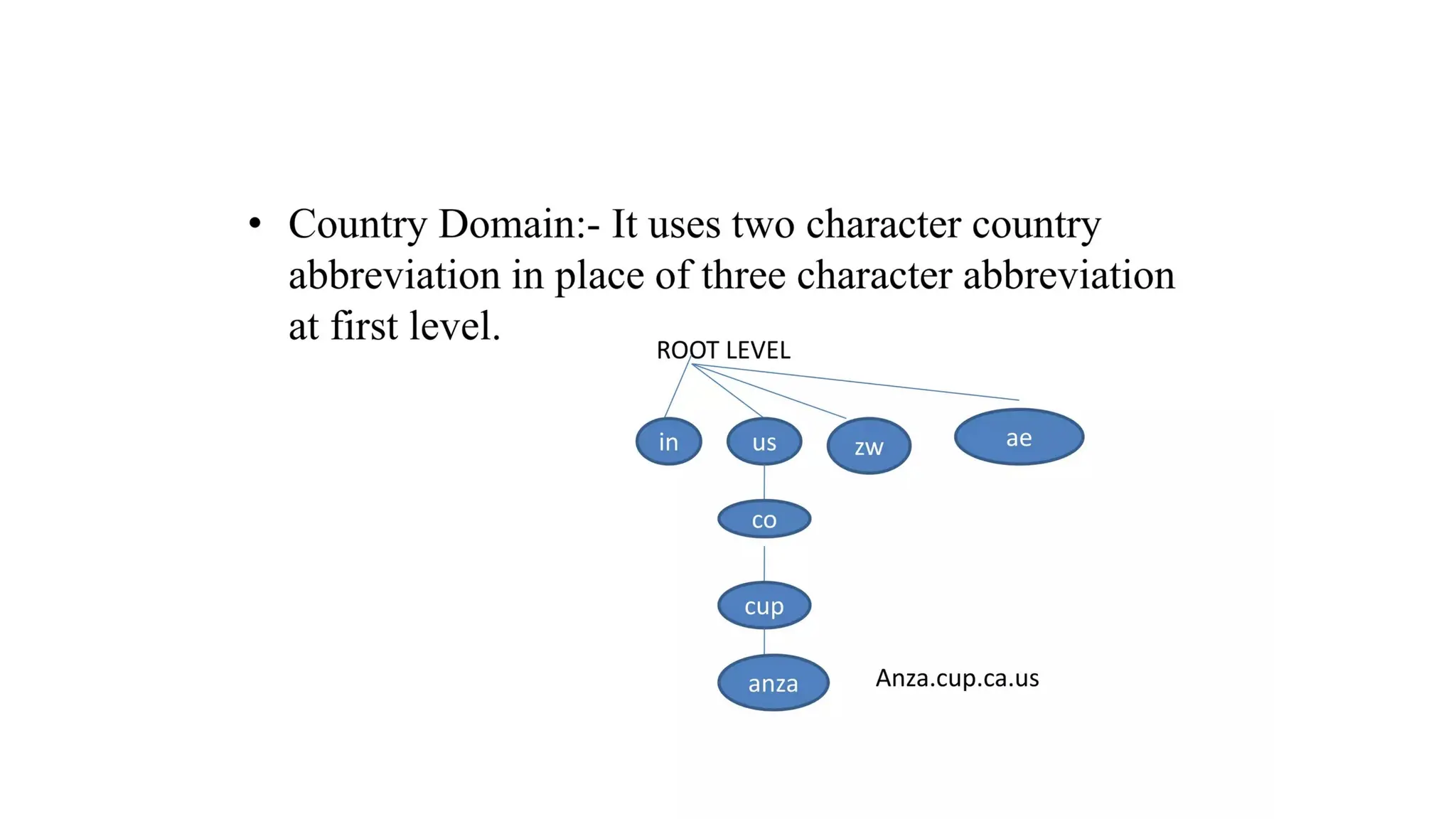
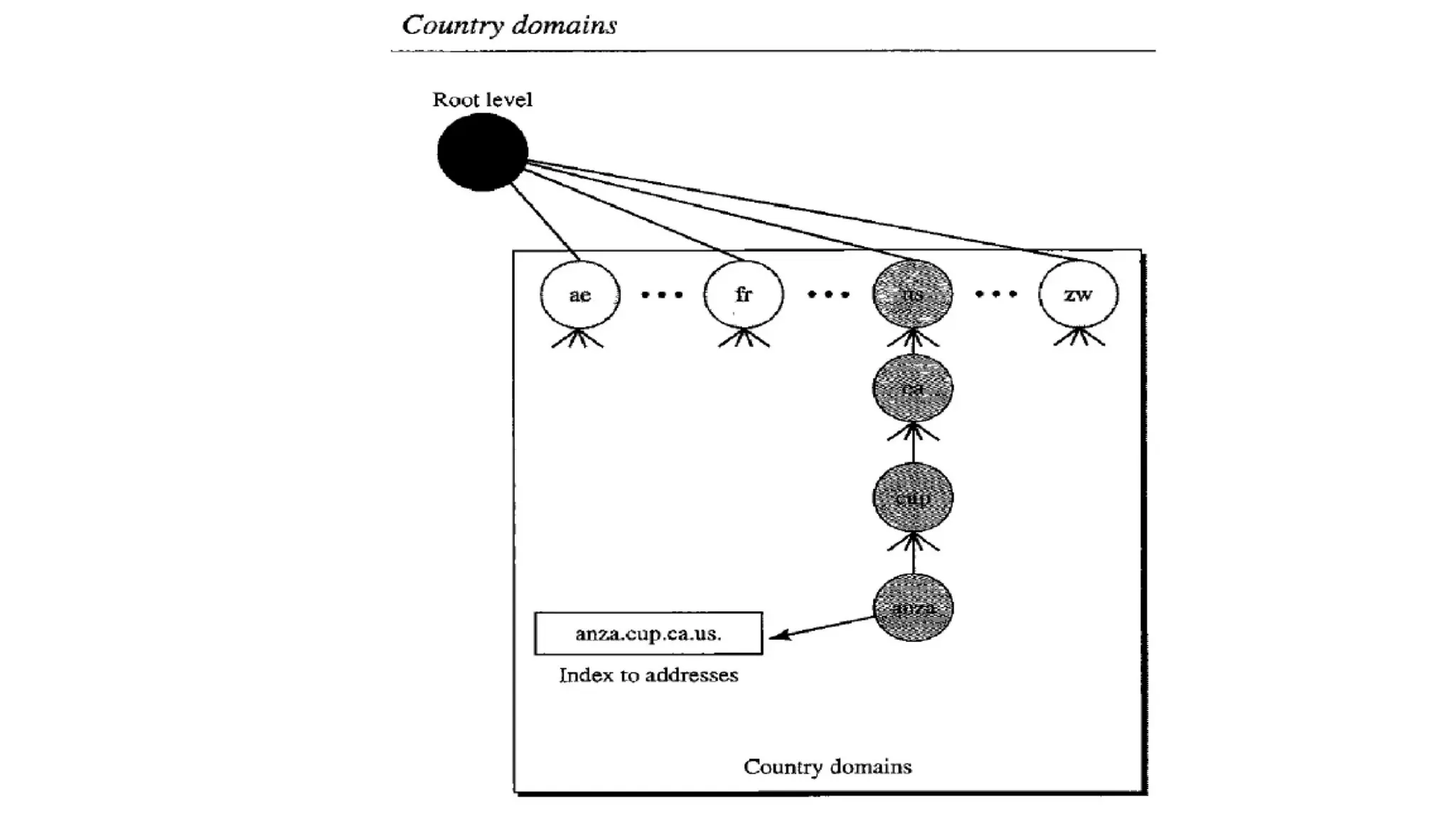
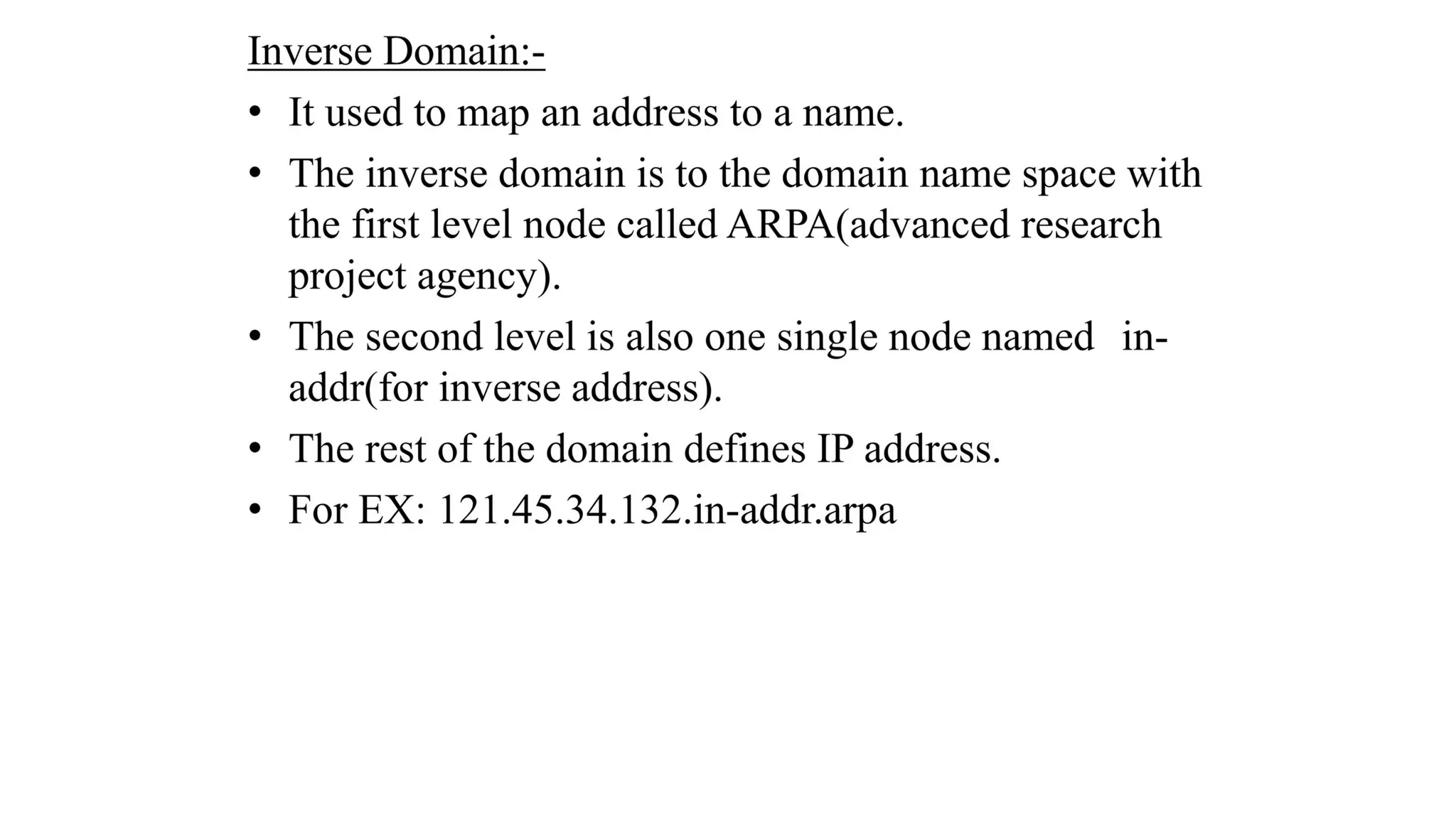
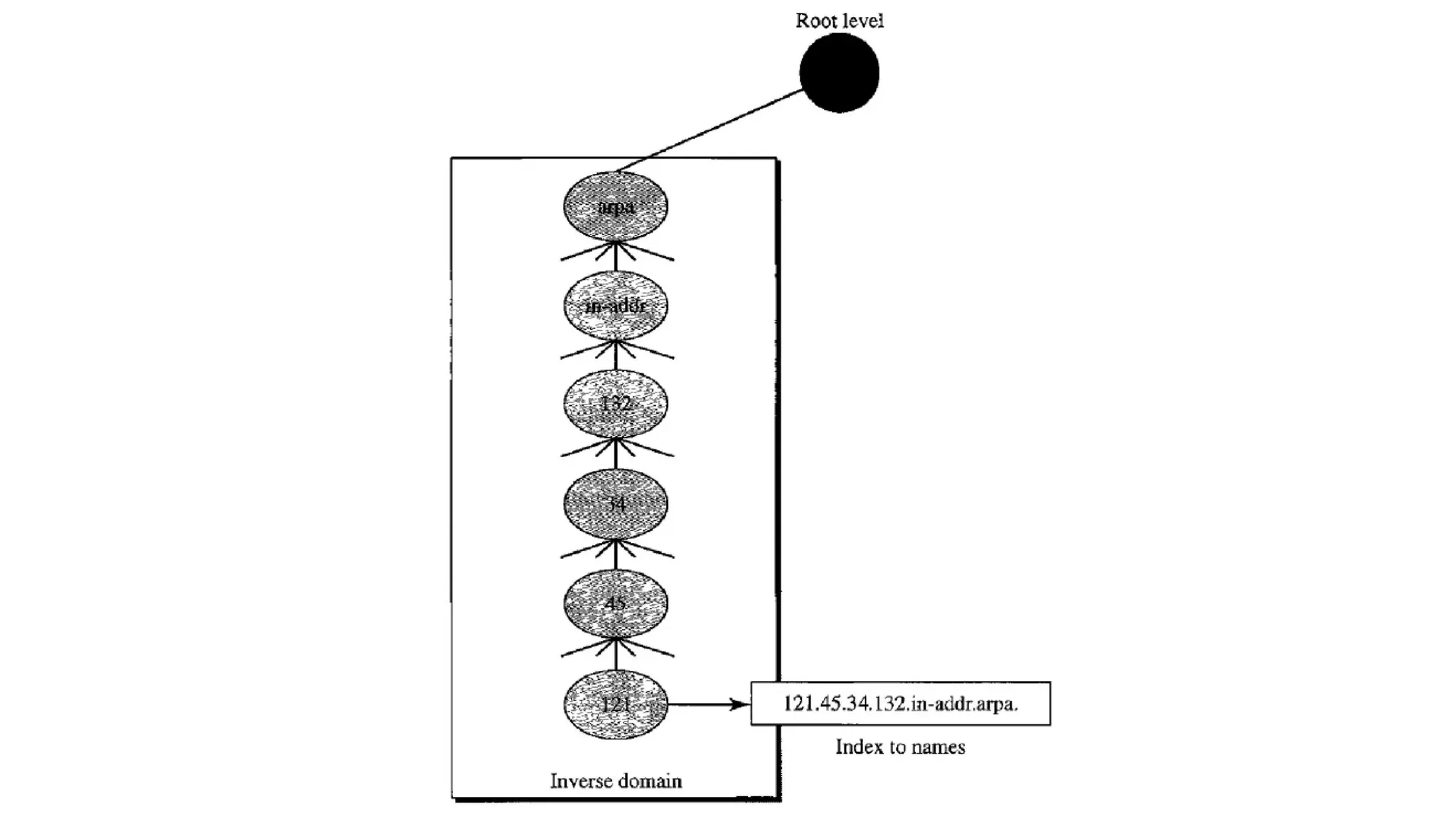
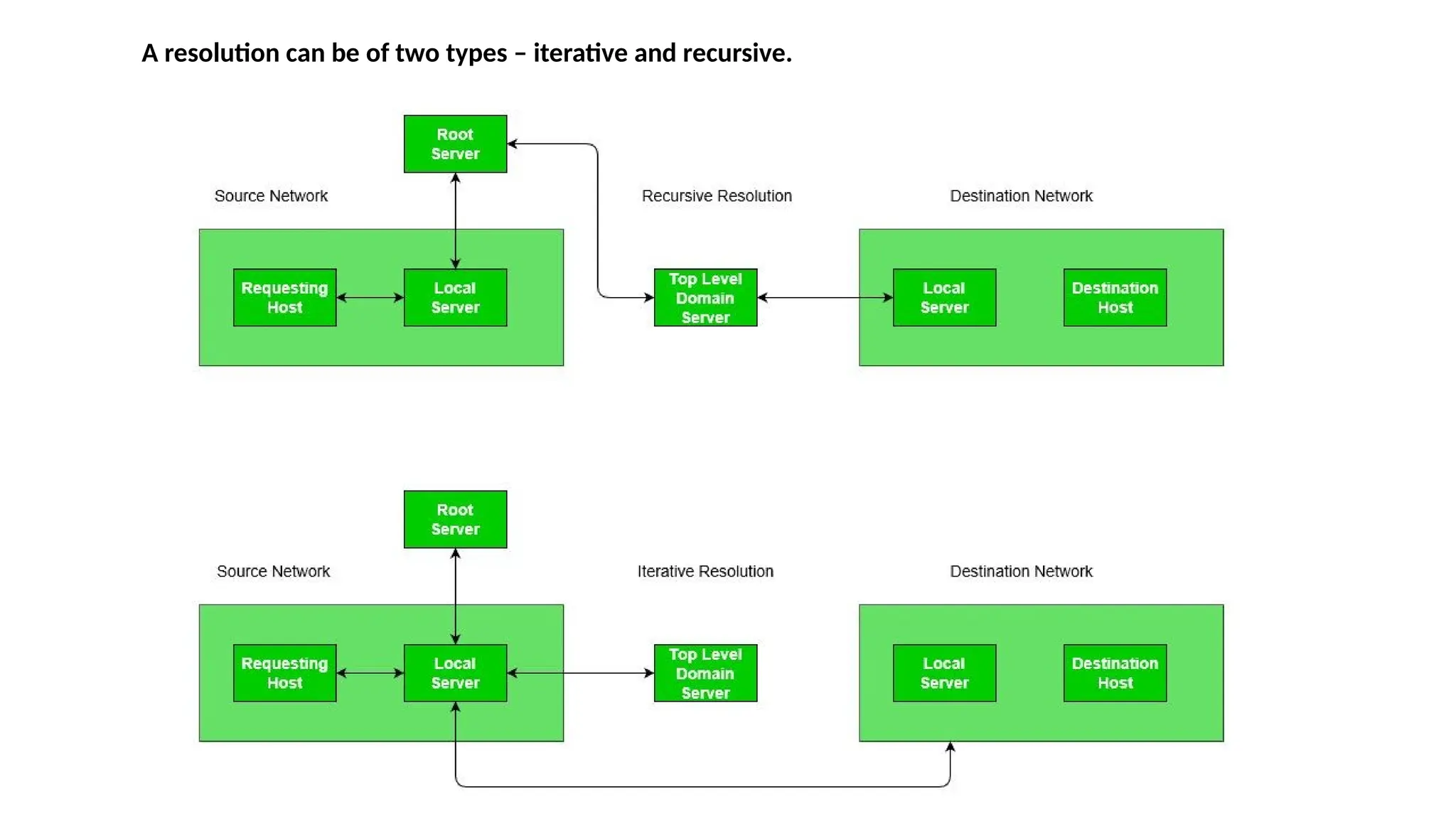
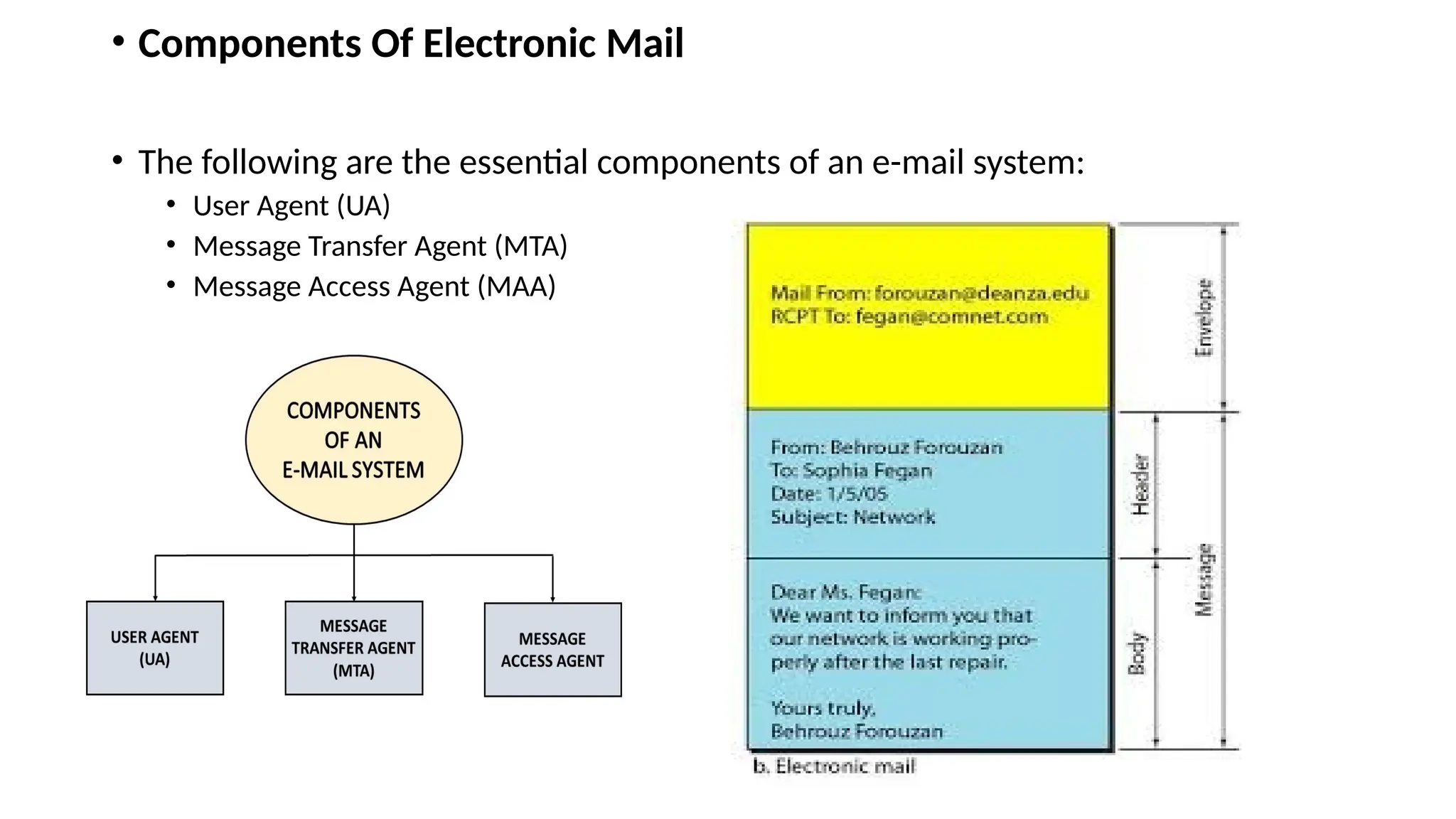
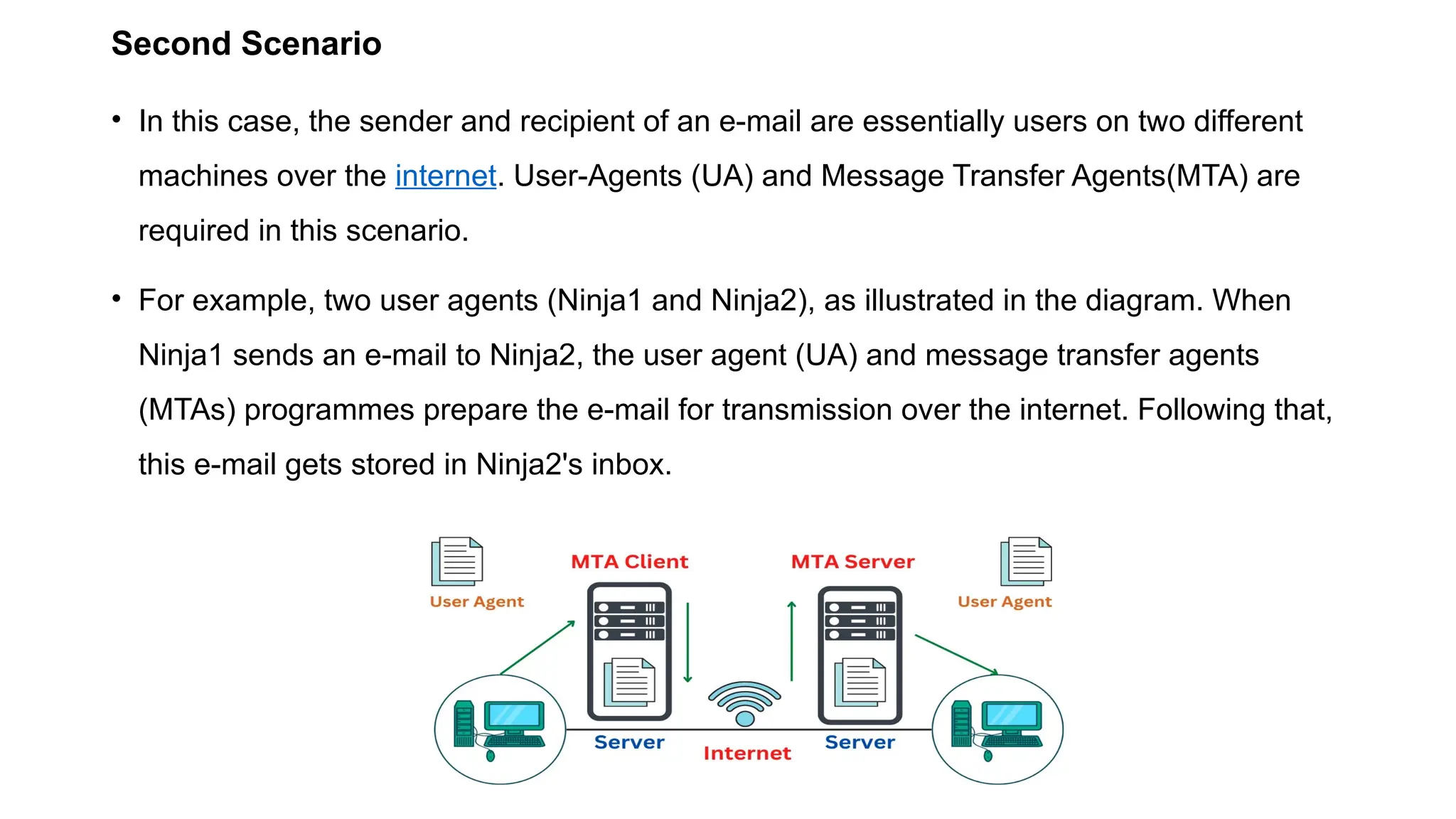
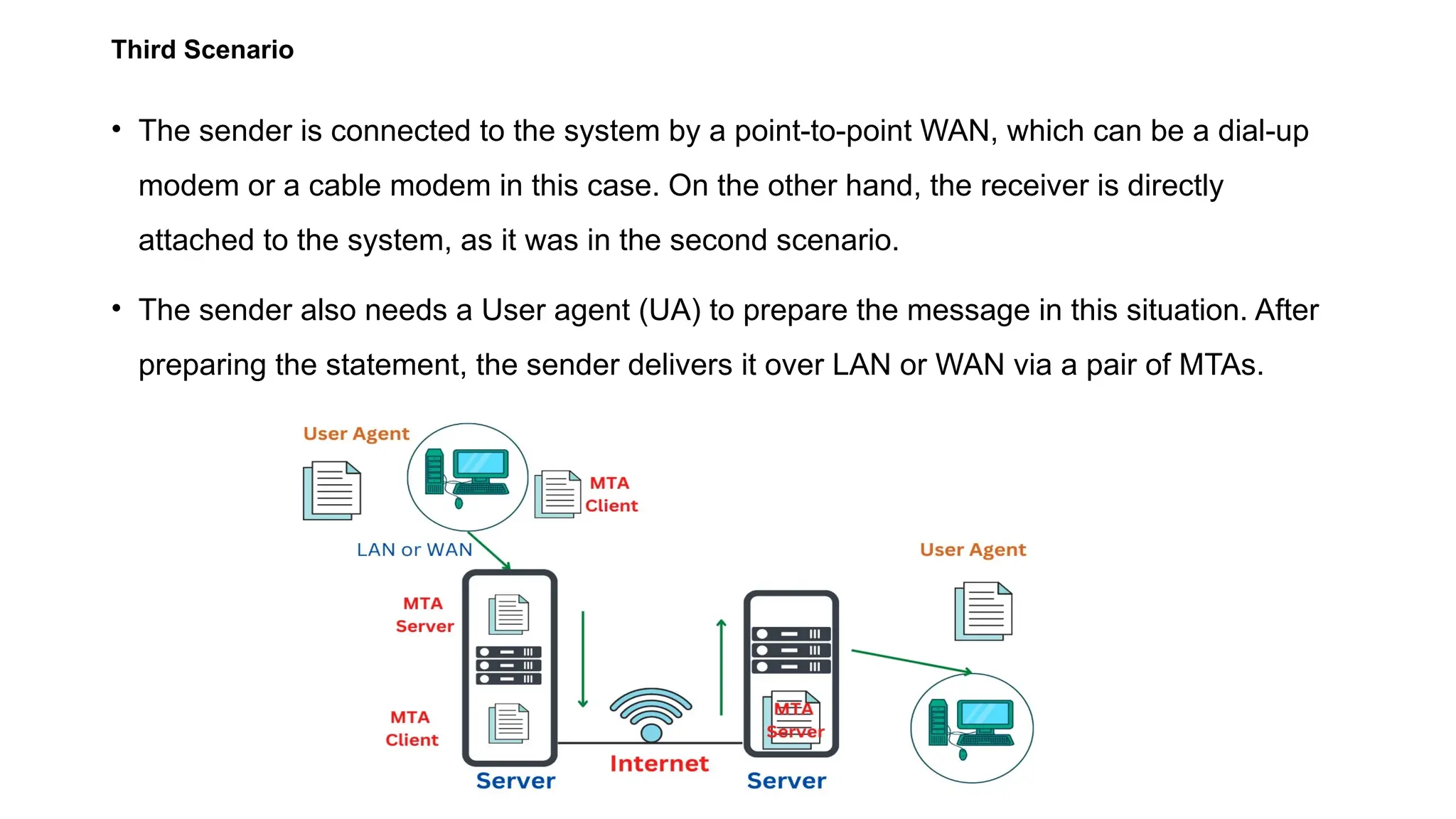
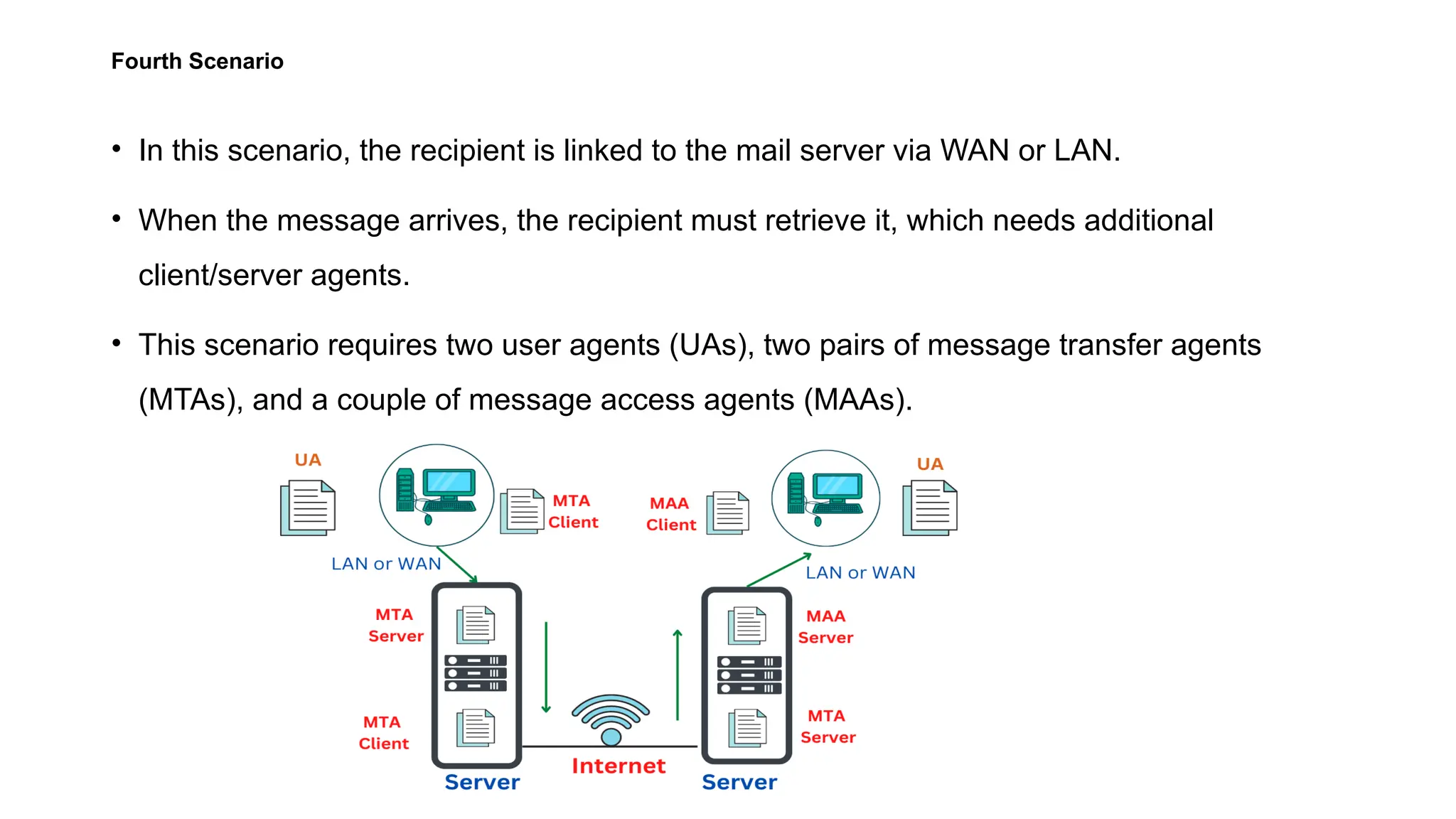
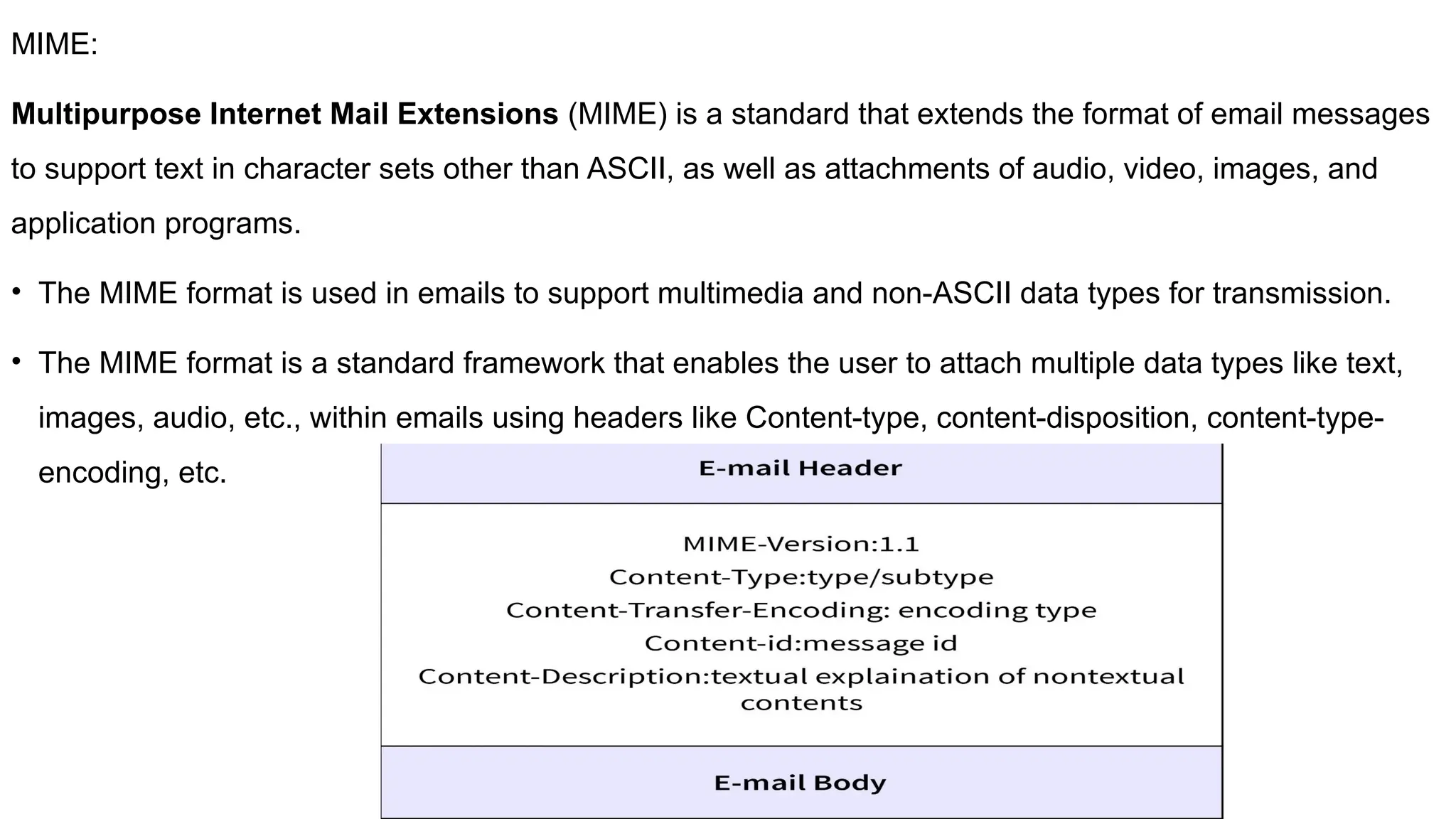
The document provides an overview of name-address resolution in DNS, detailing how resolvers map addresses to names and vice versa, including iterative and recursive resolution. It also outlines the components and processes of electronic mail, including user agents, message transfer agents, and protocols used for email transmission. Additionally, it discusses the MIME standard for multimedia email support, allowing various data types to be transmitted within emails.