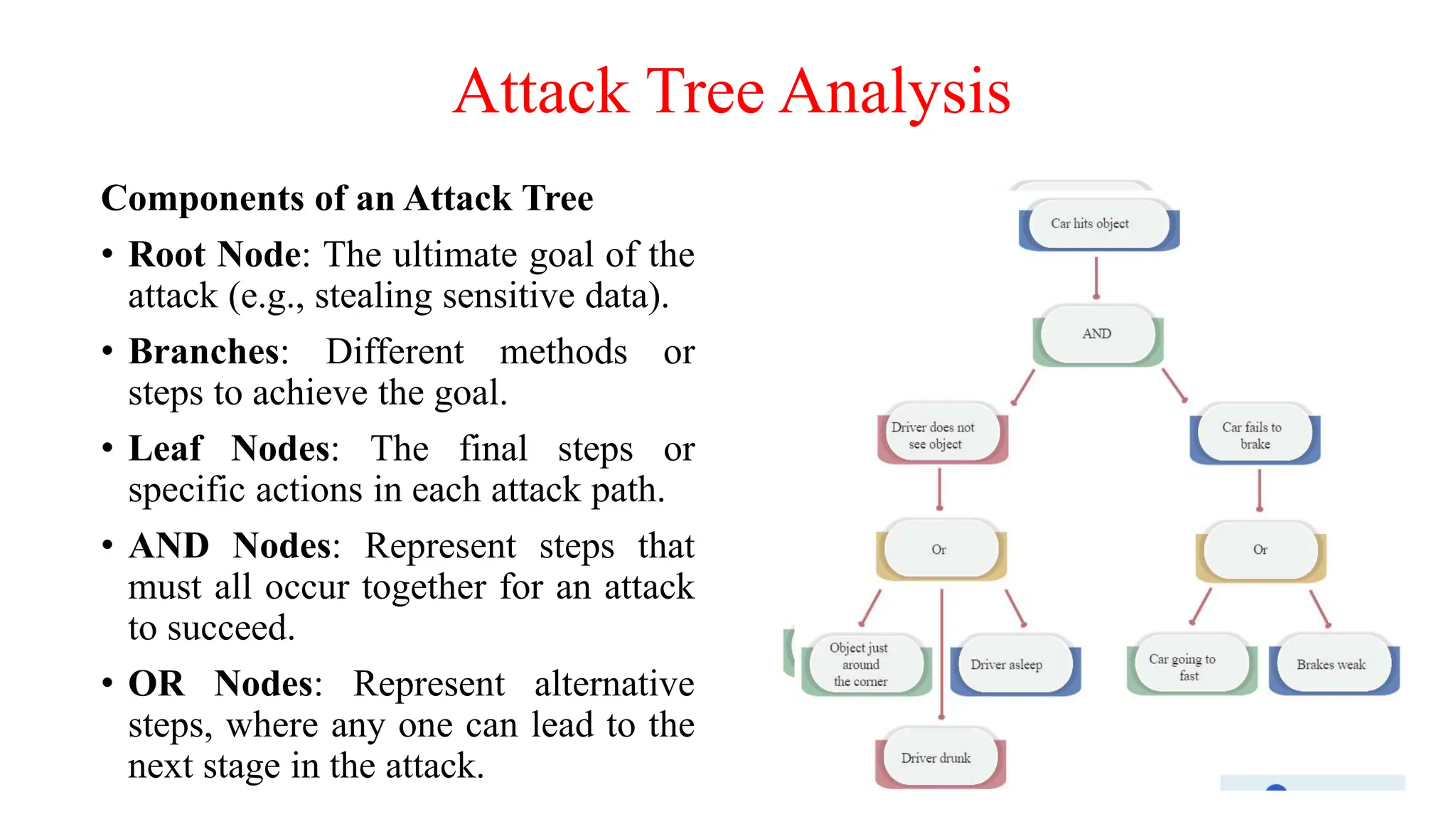
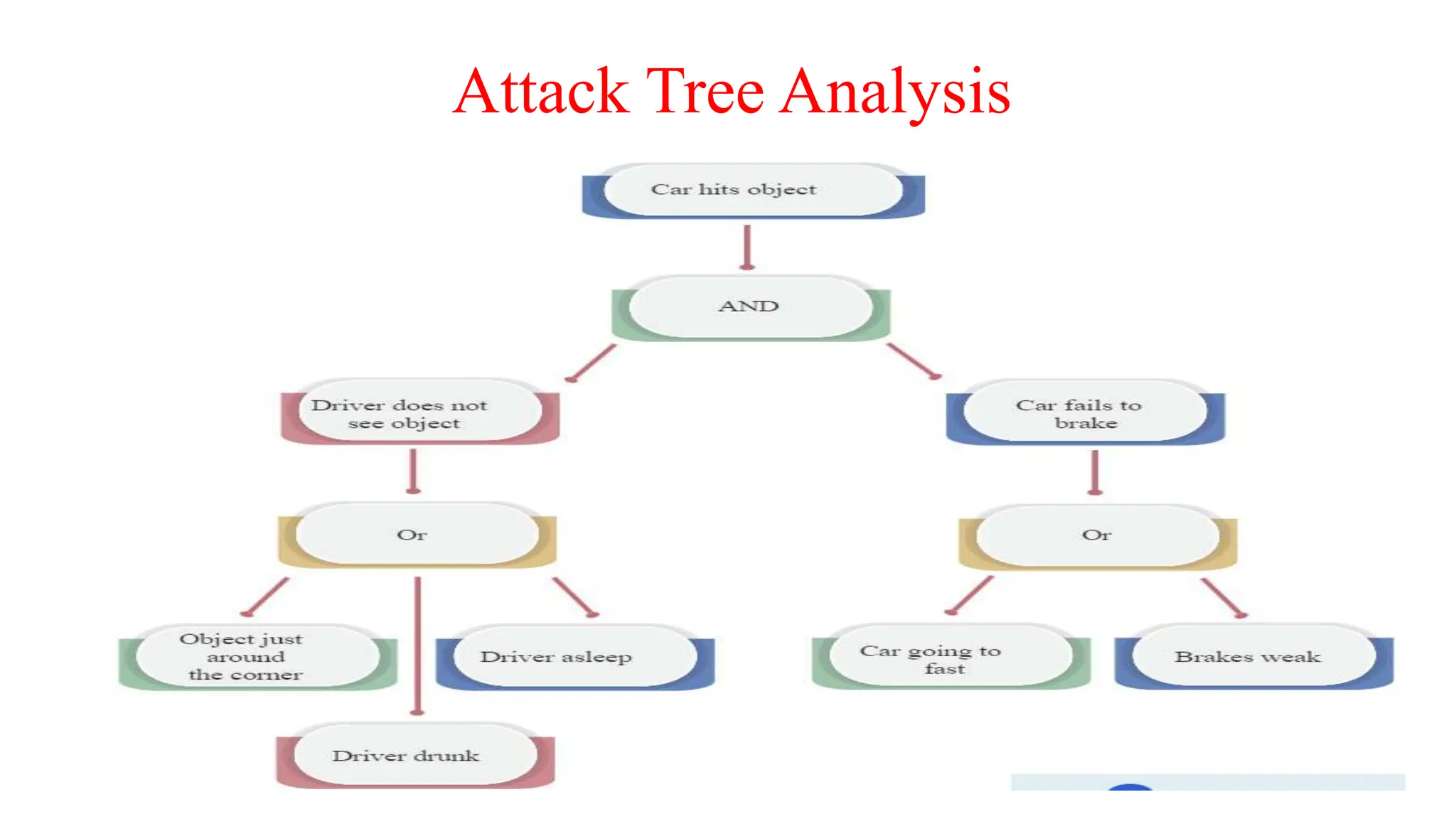
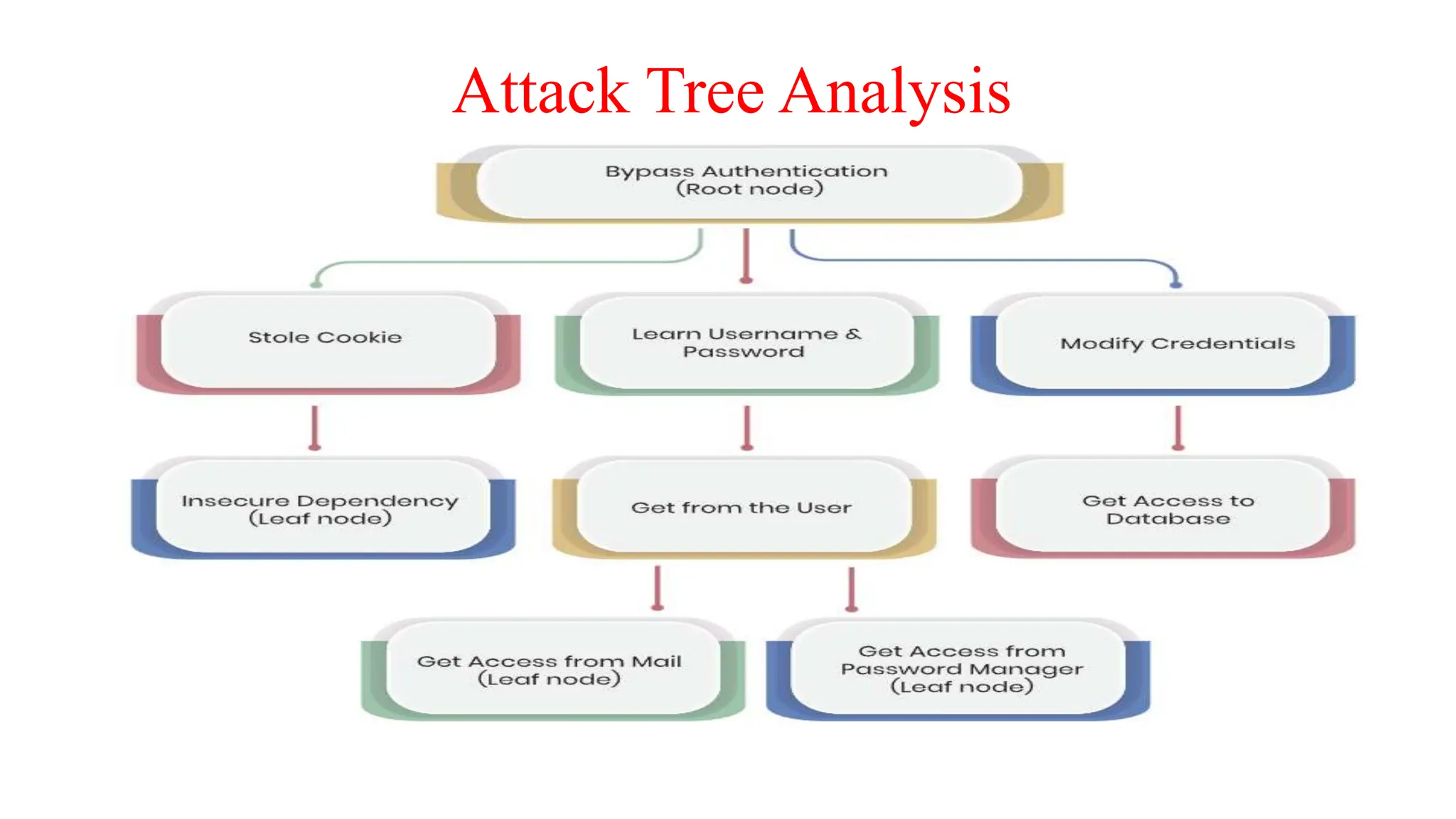
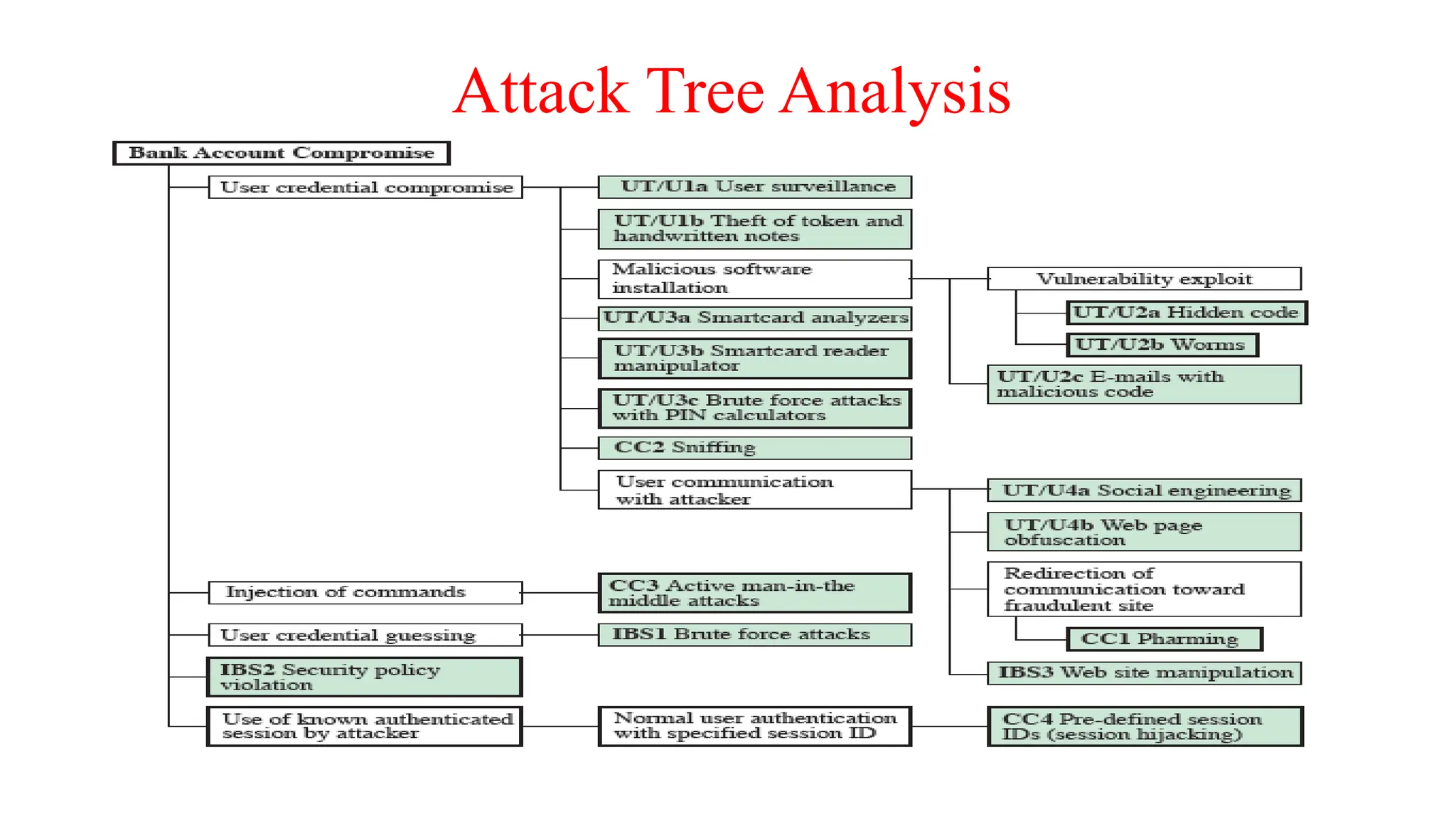
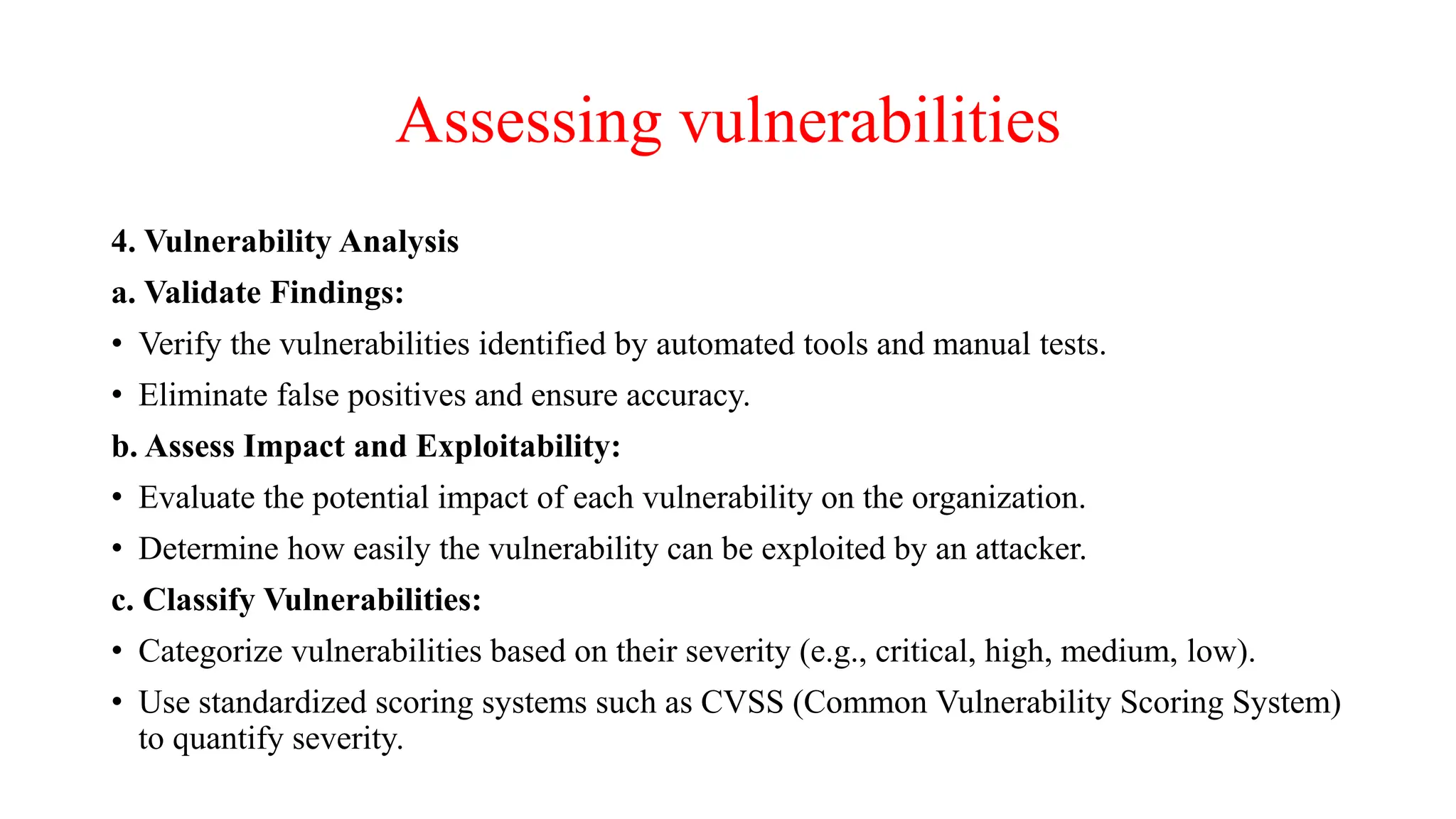
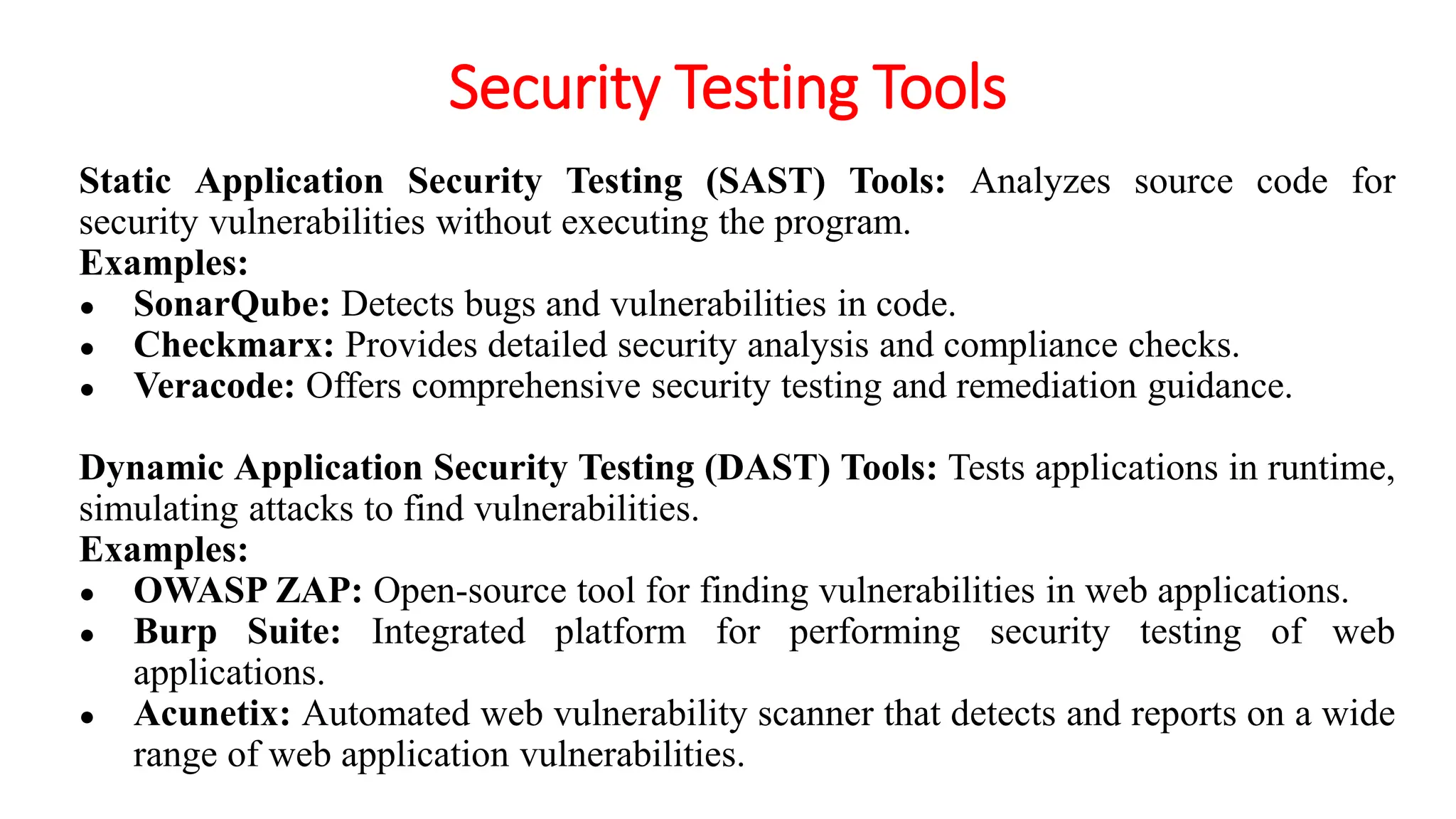
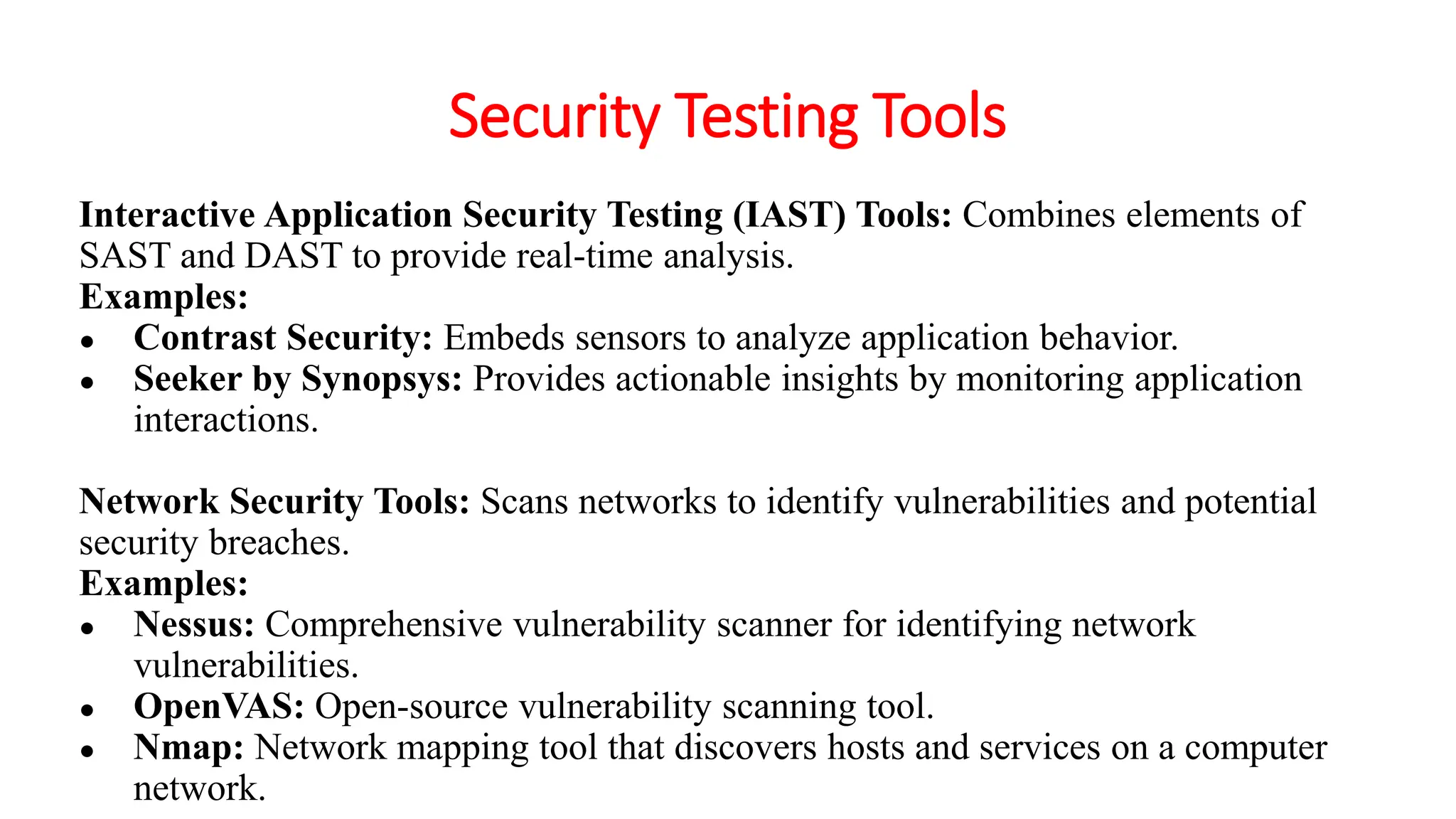
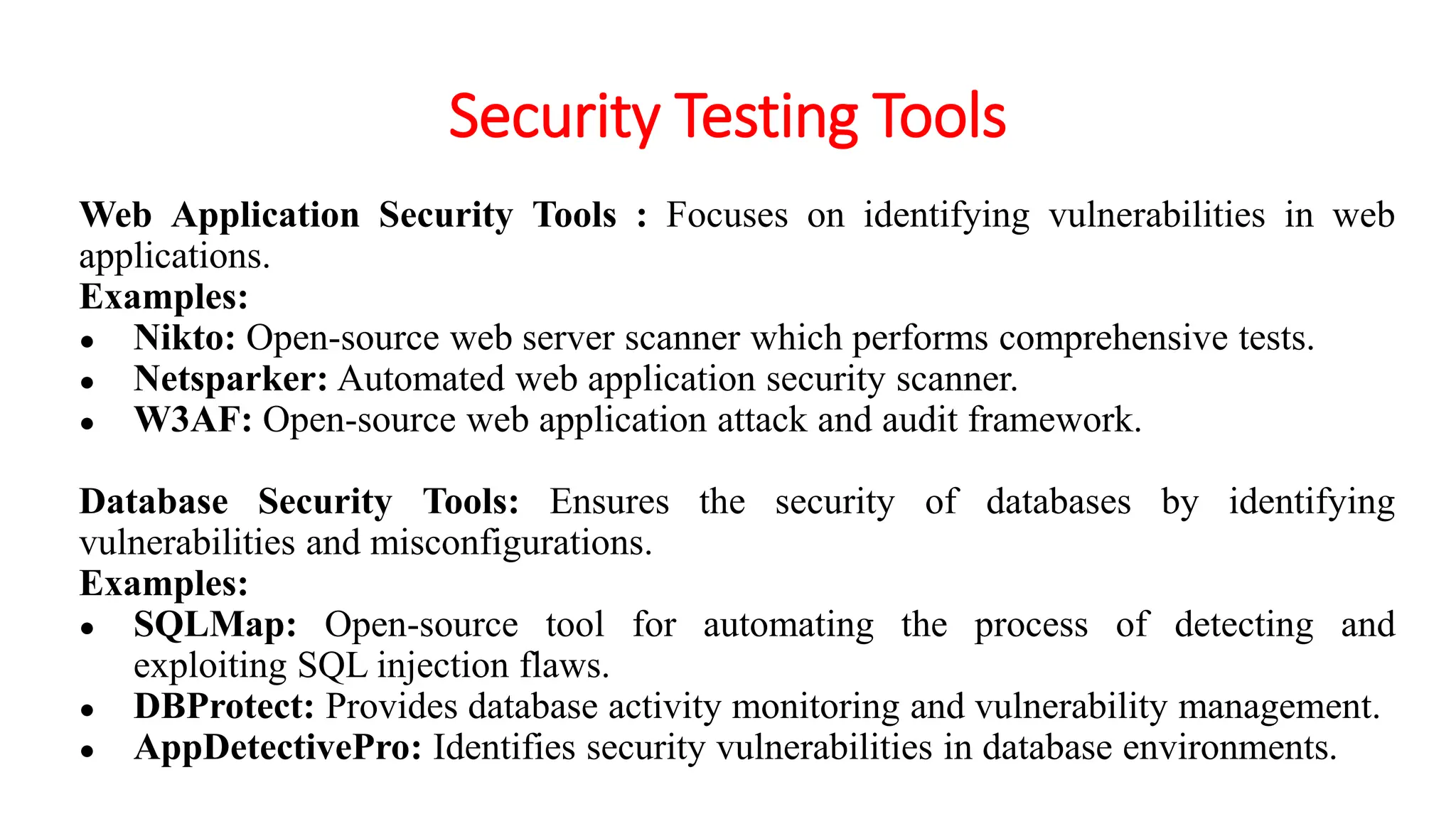
The document provides an in-depth overview of cybersecurity, focusing on scanning processes used to identify and mitigate vulnerabilities in various systems, networks, and applications. It discusses different types of scanning methods, including network, vulnerability, web application, database, host-based, and wireless network scanning, along with the tools and techniques used in each. Additionally, it covers attack tree analysis, penetration testing, and security testing tools, emphasizing their importance for identifying security threats and ensuring compliance with regulations.