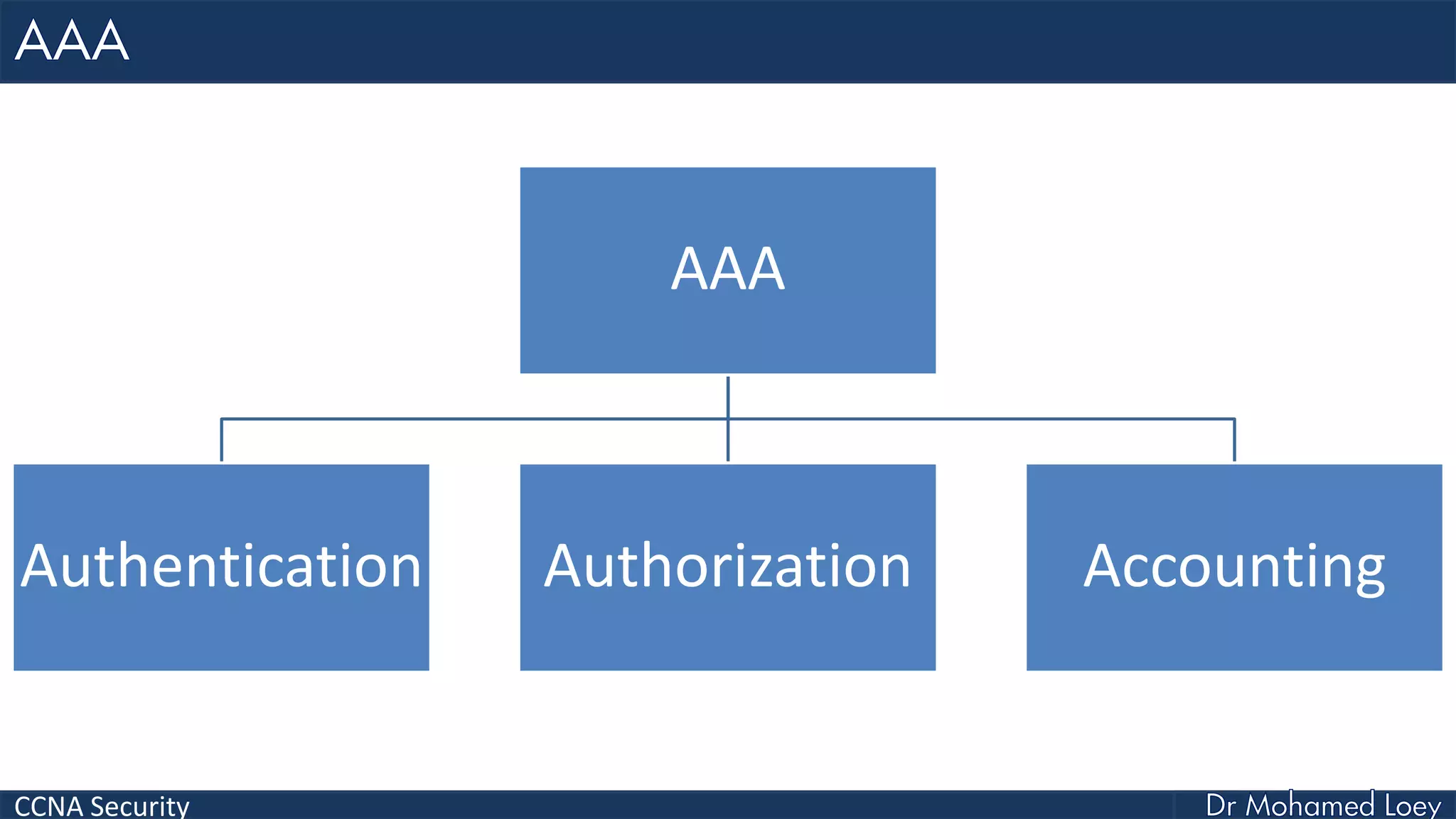
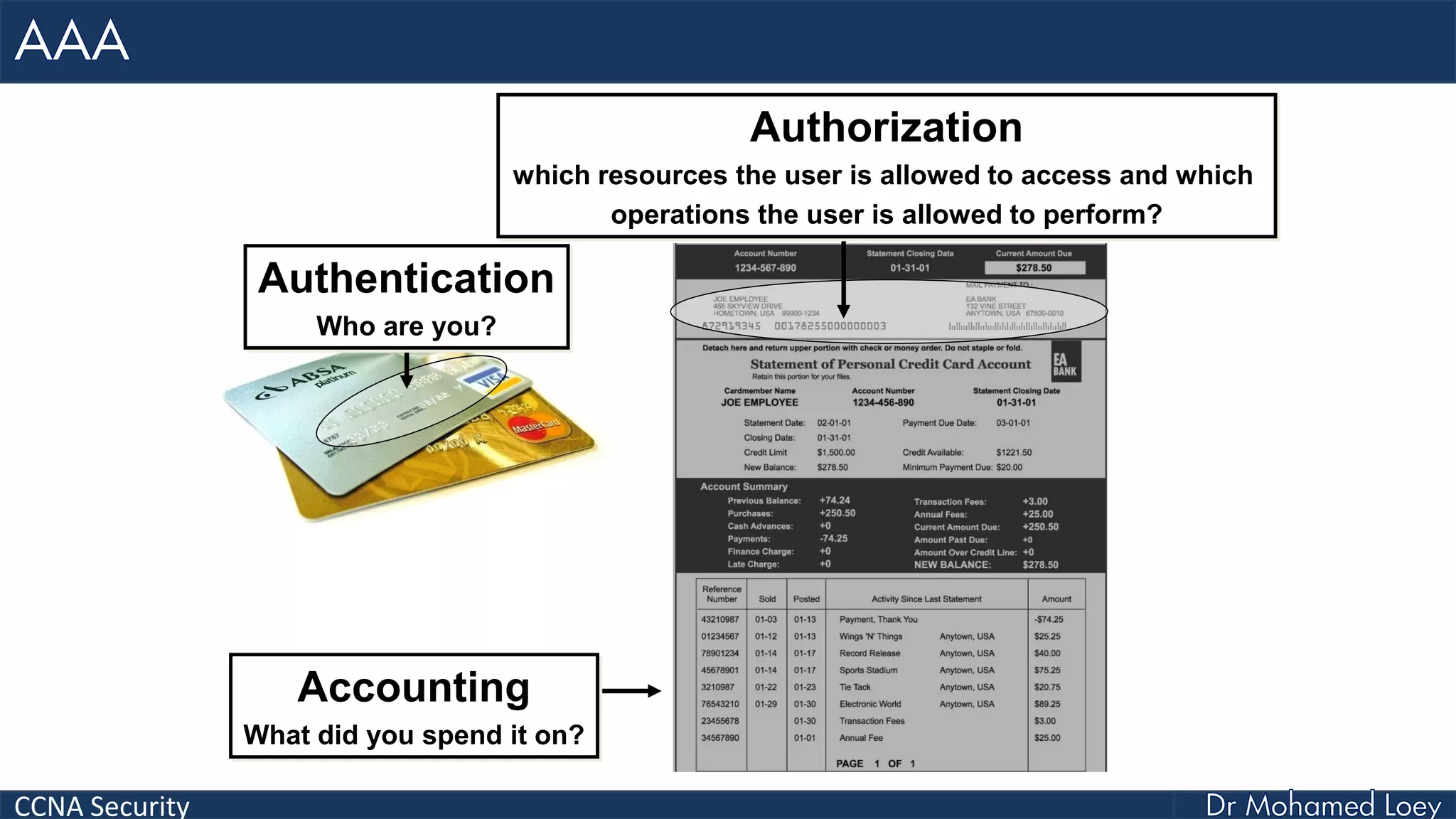
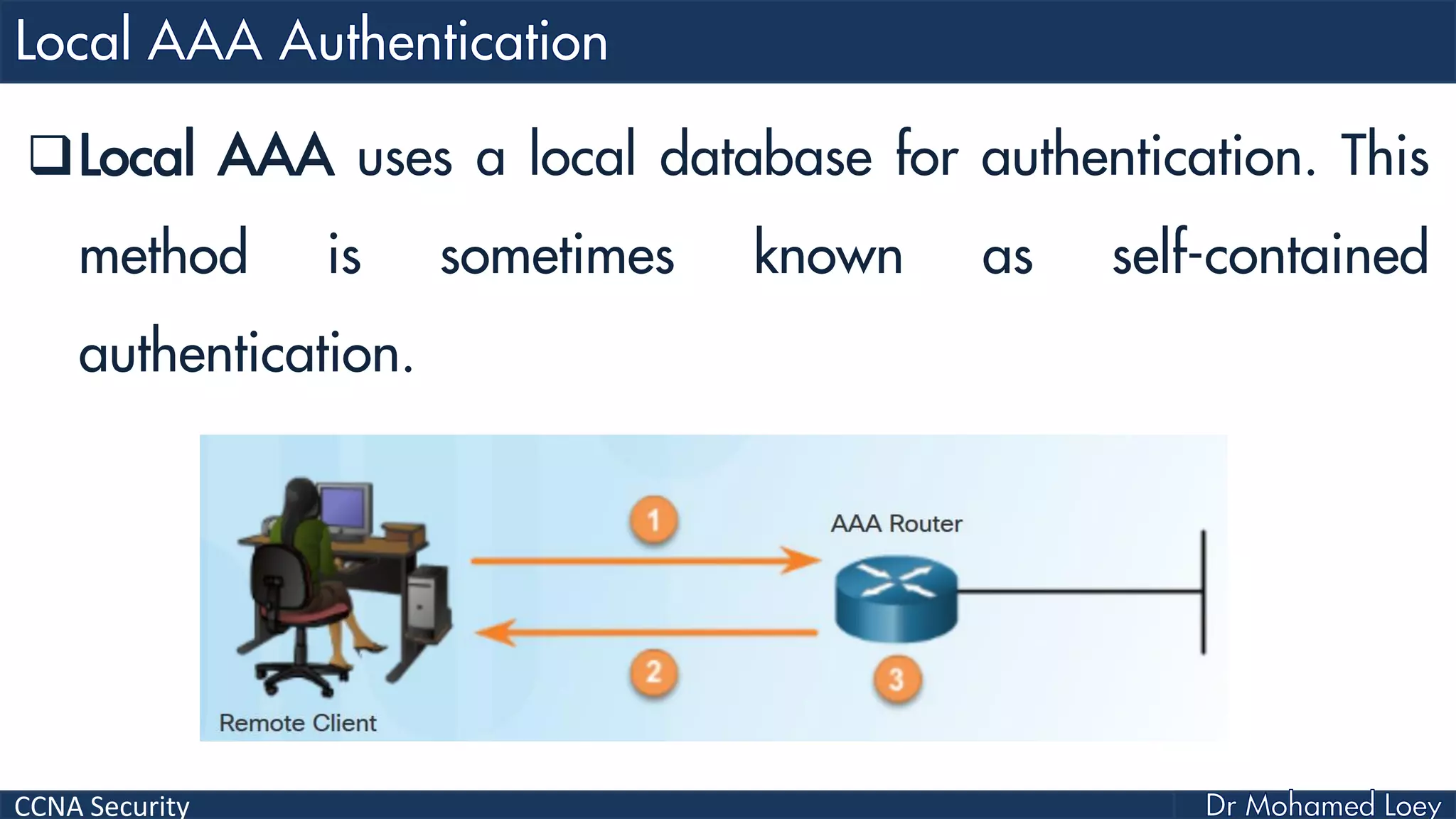
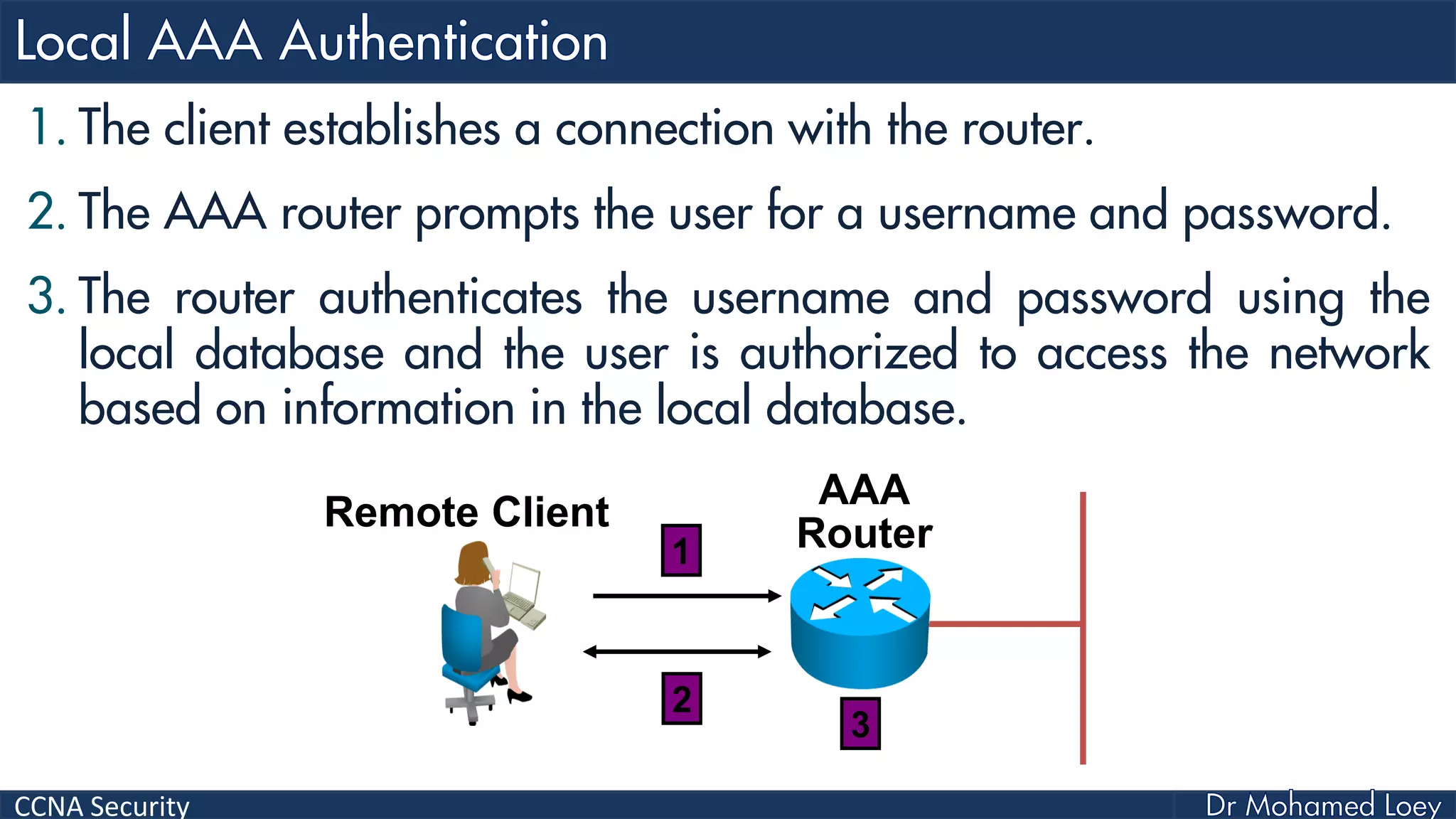
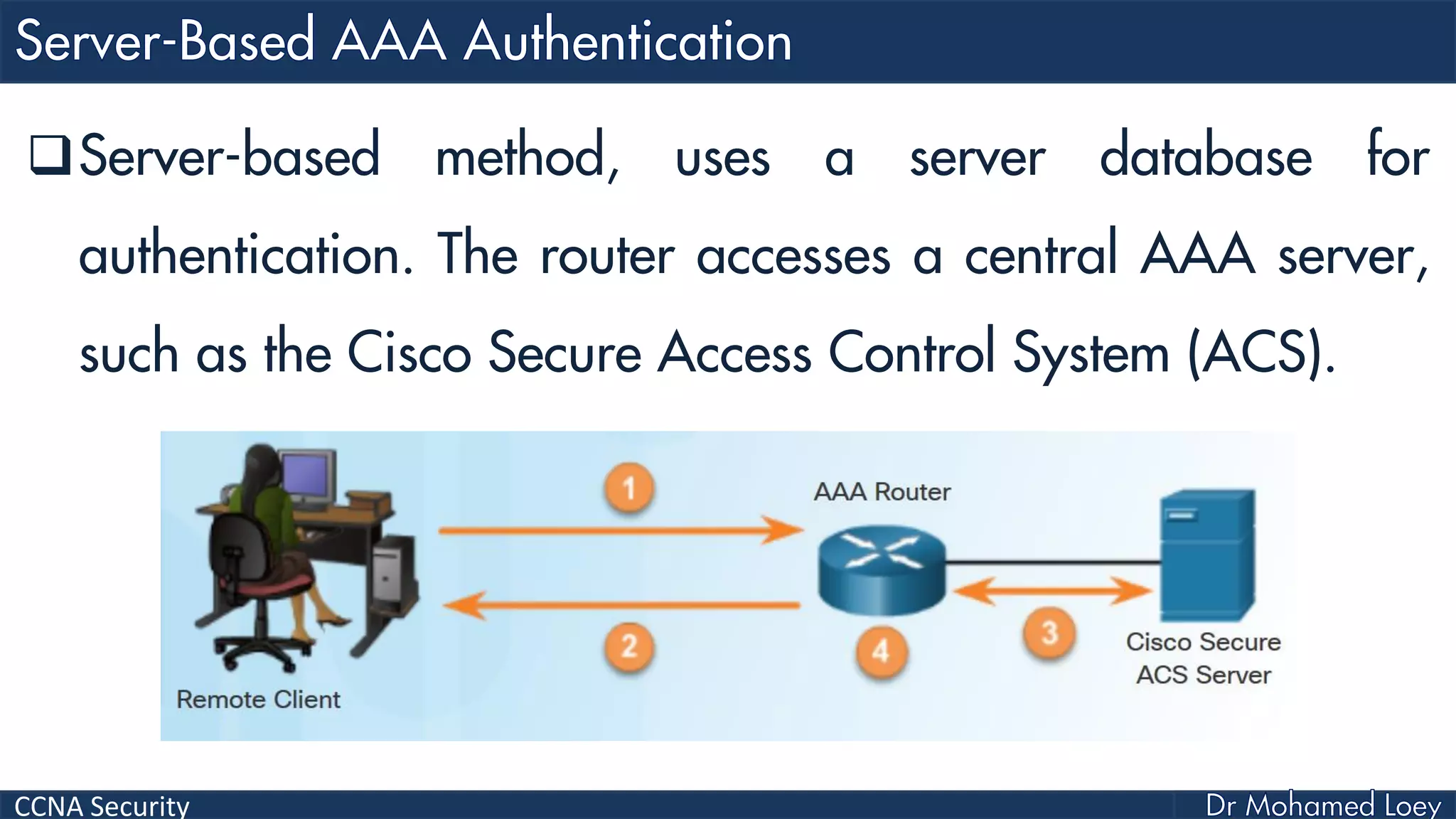
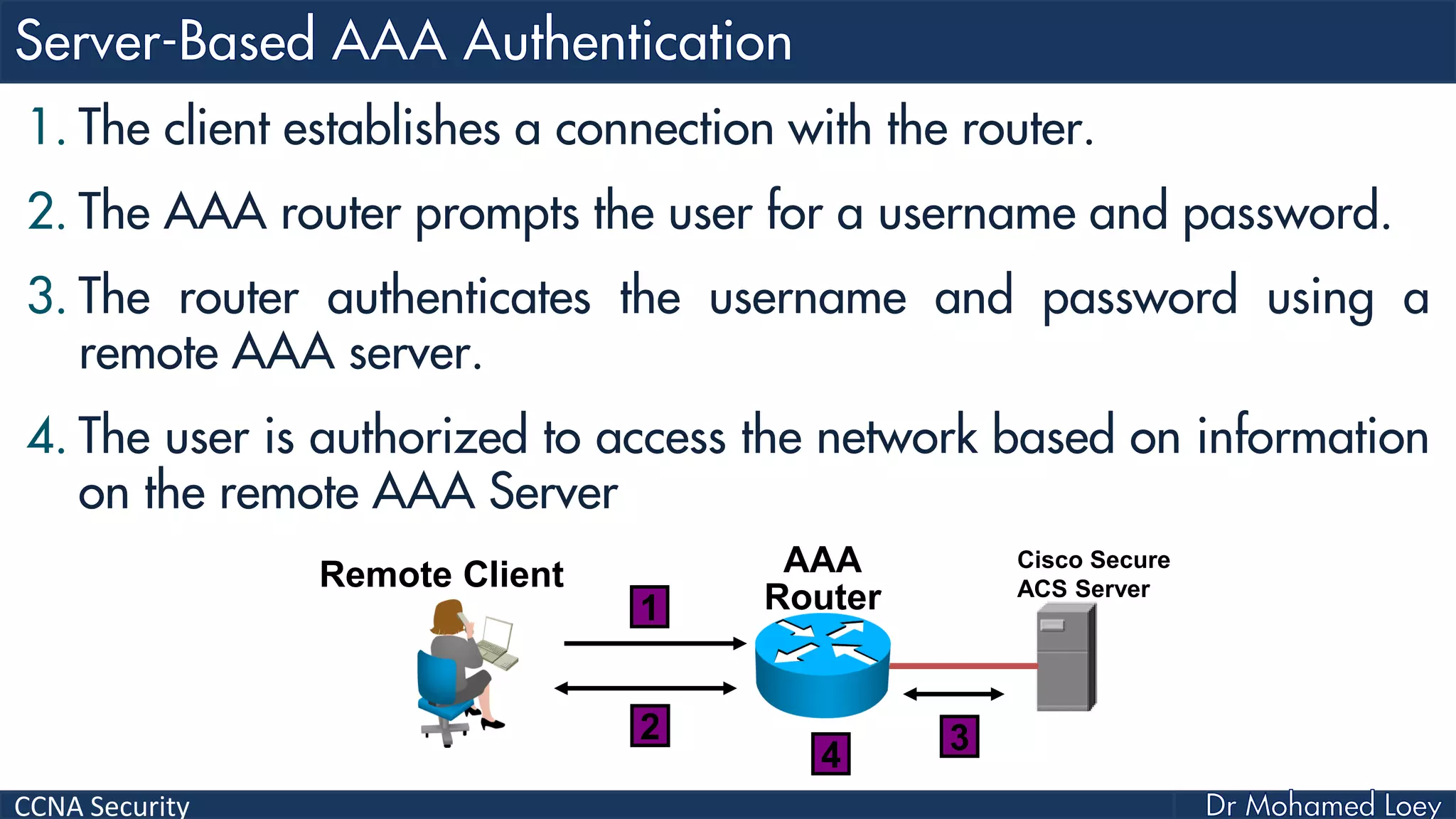
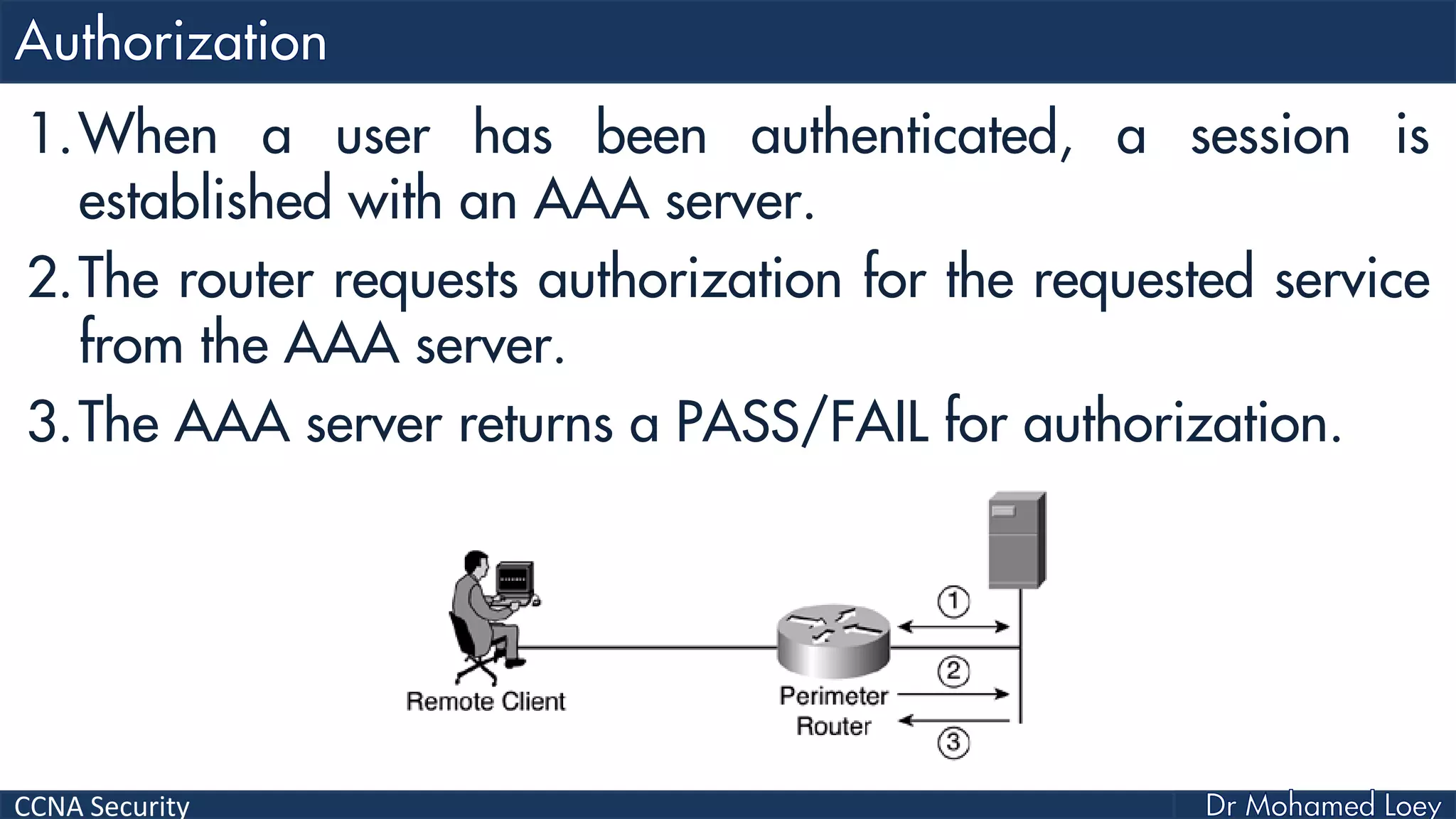
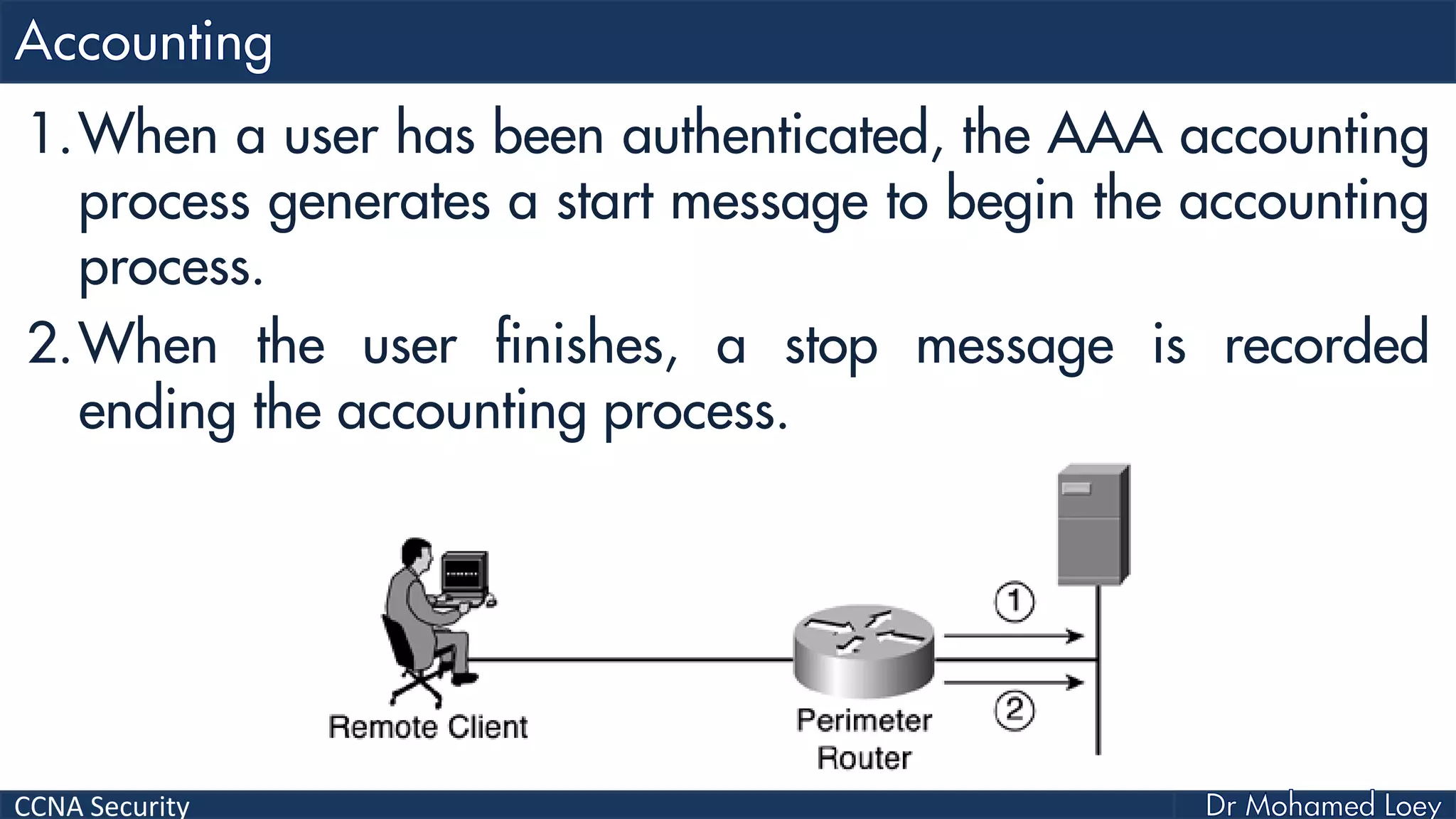
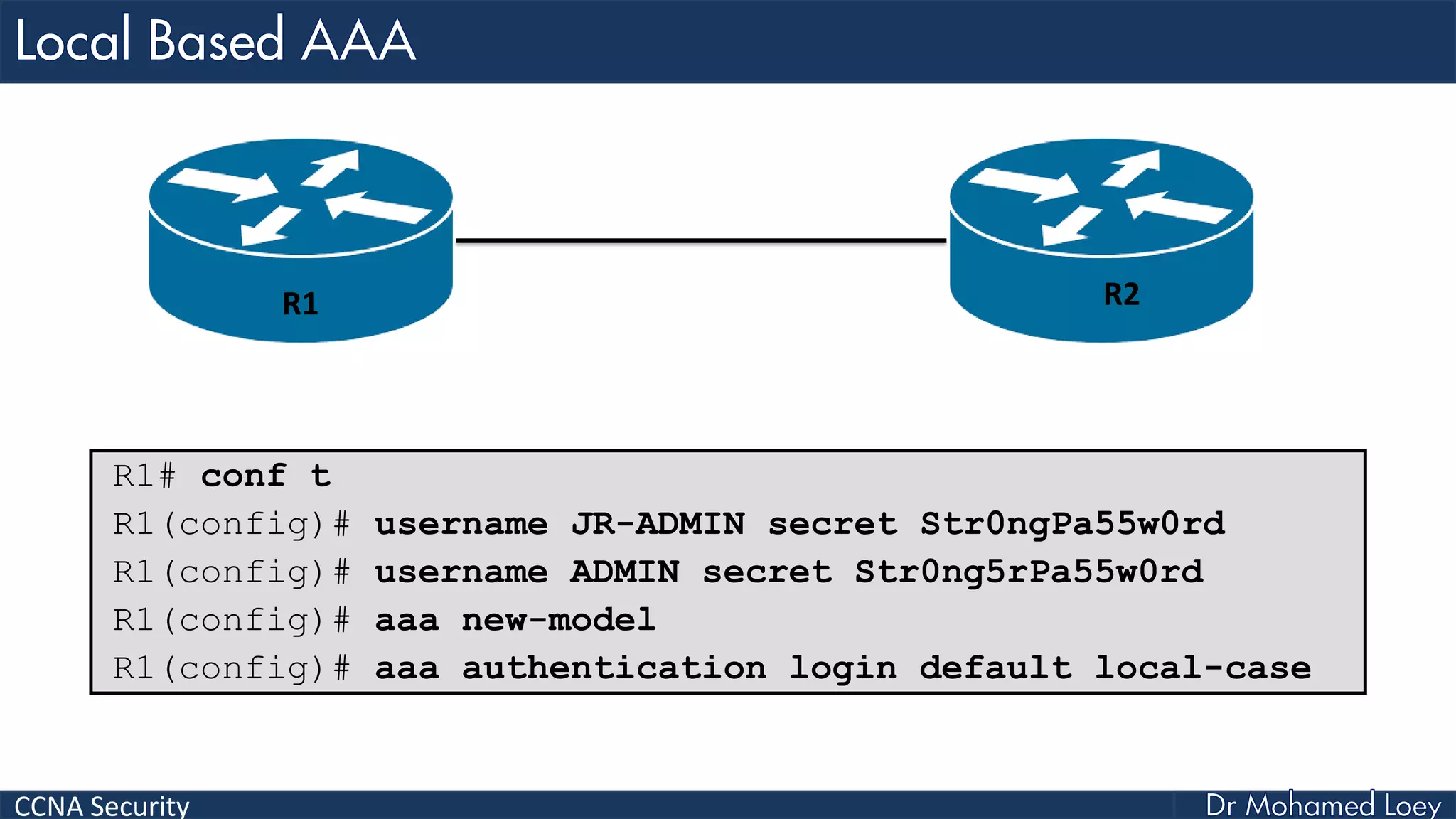
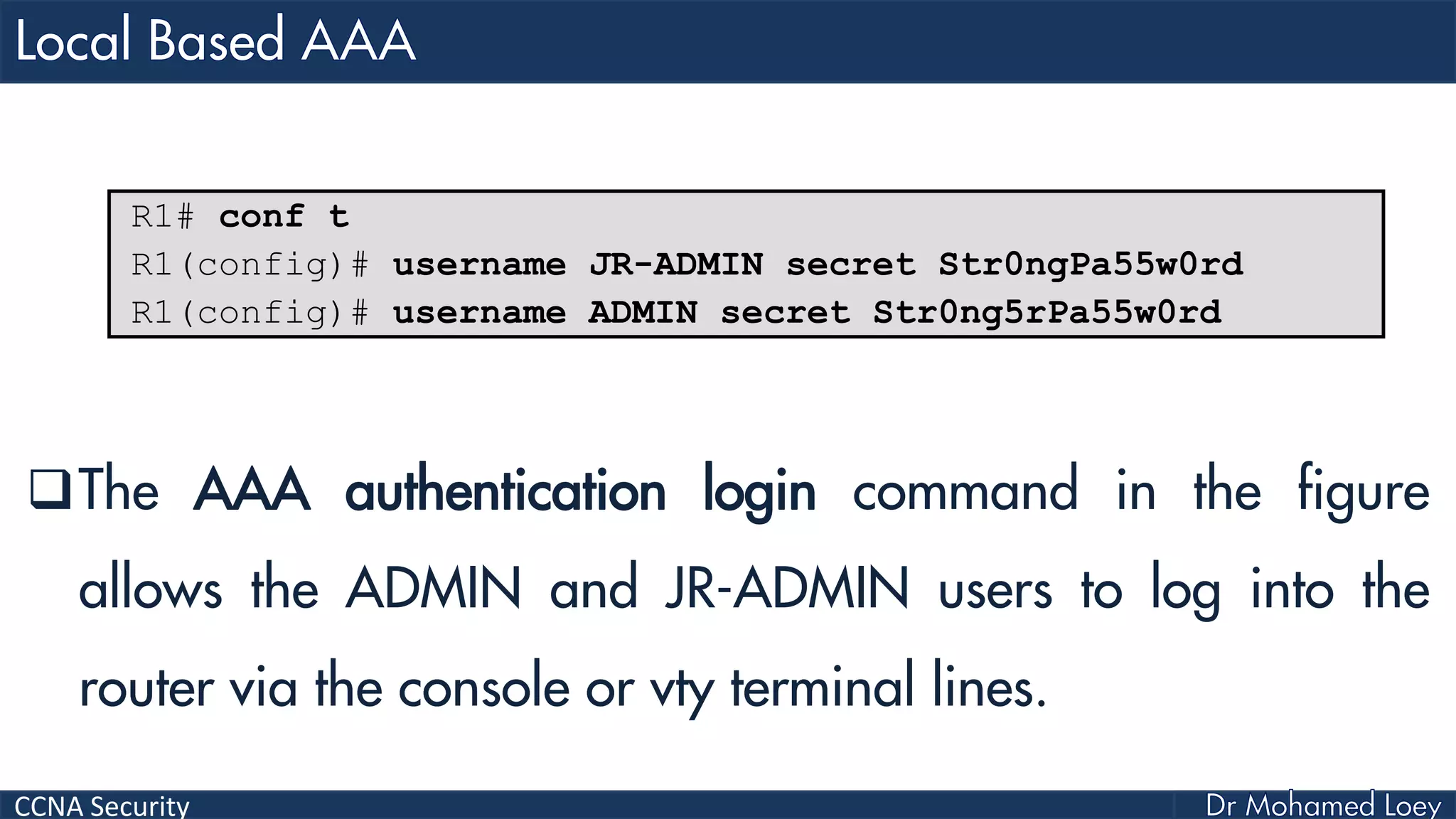
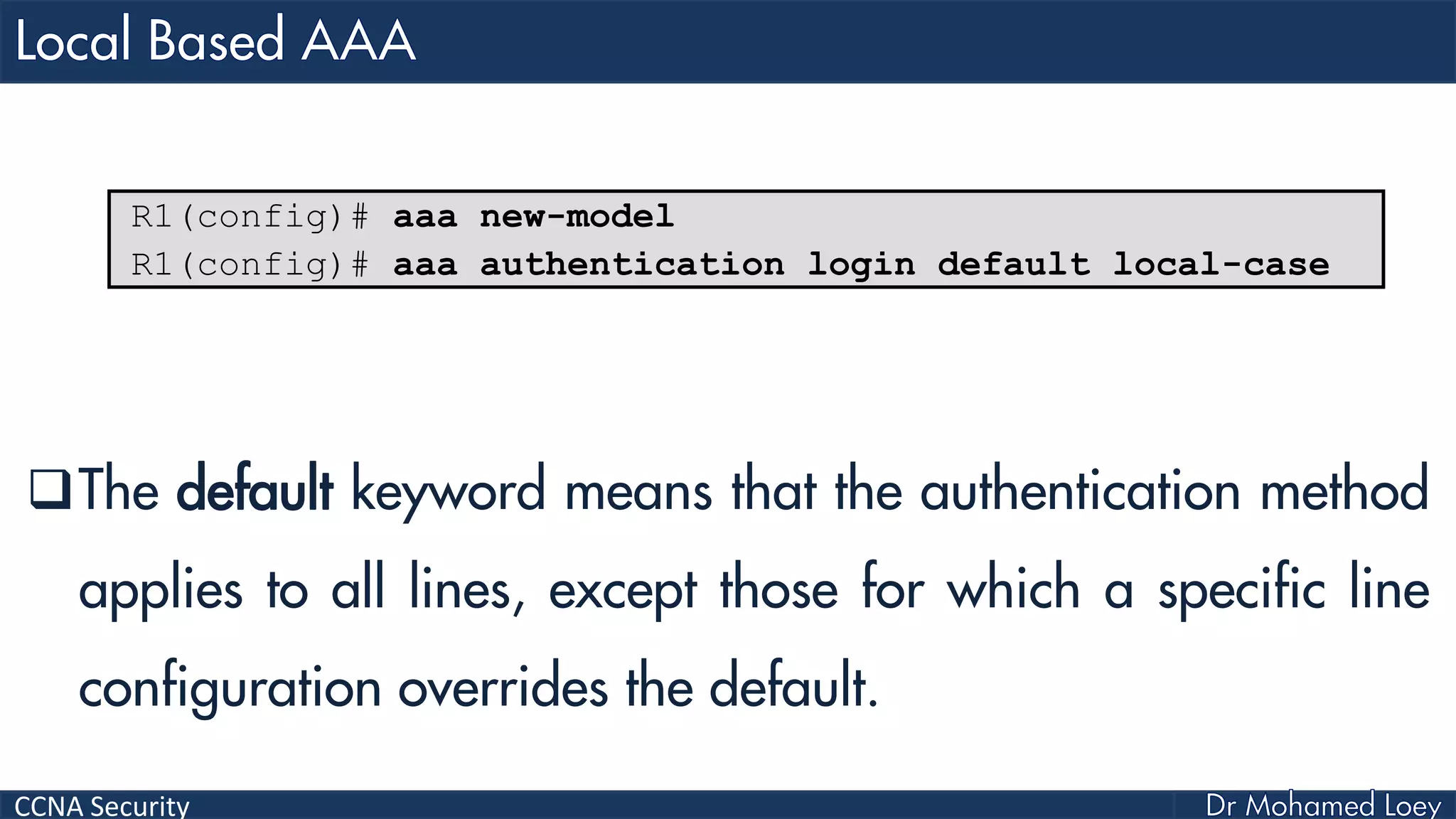
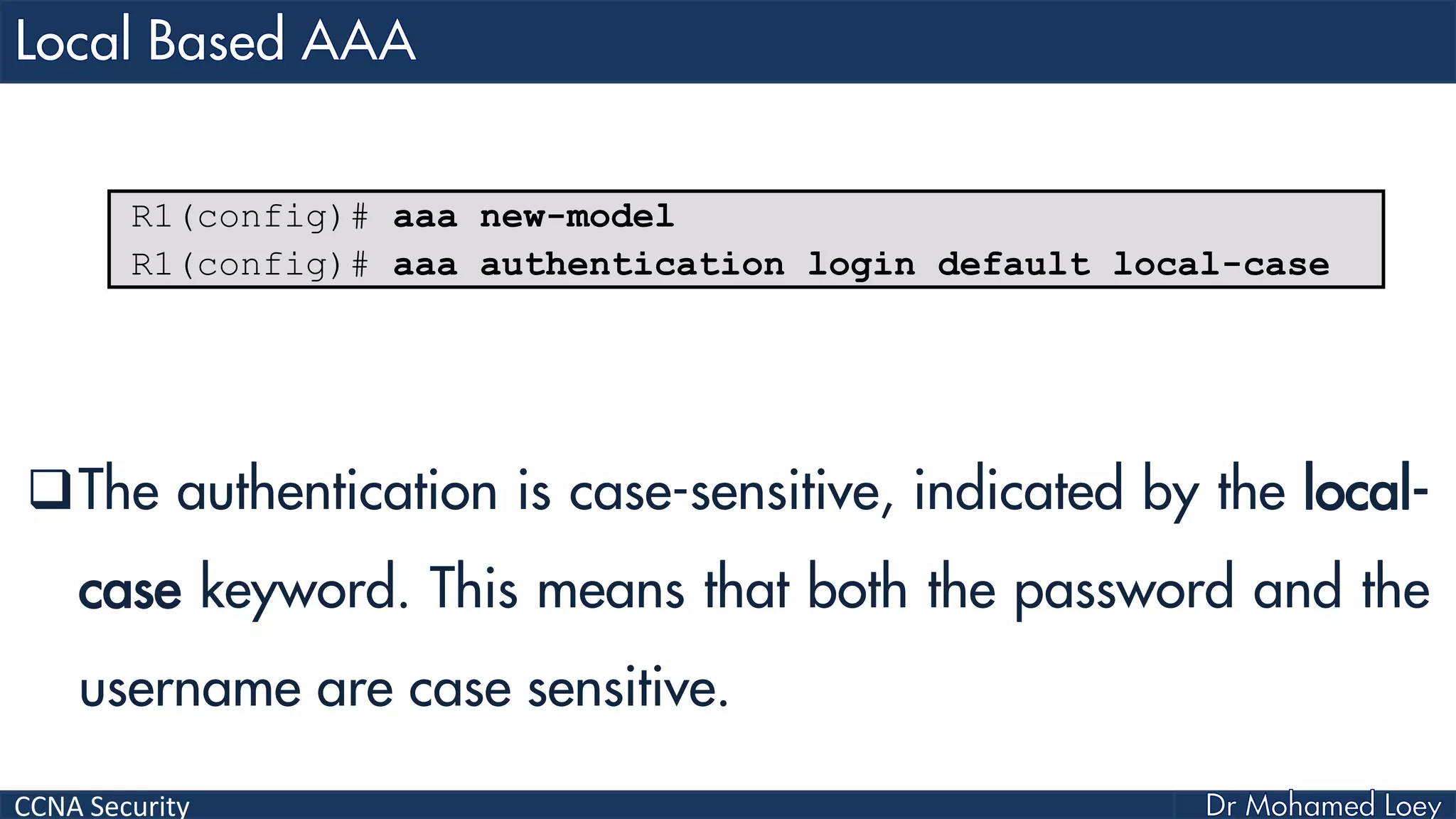
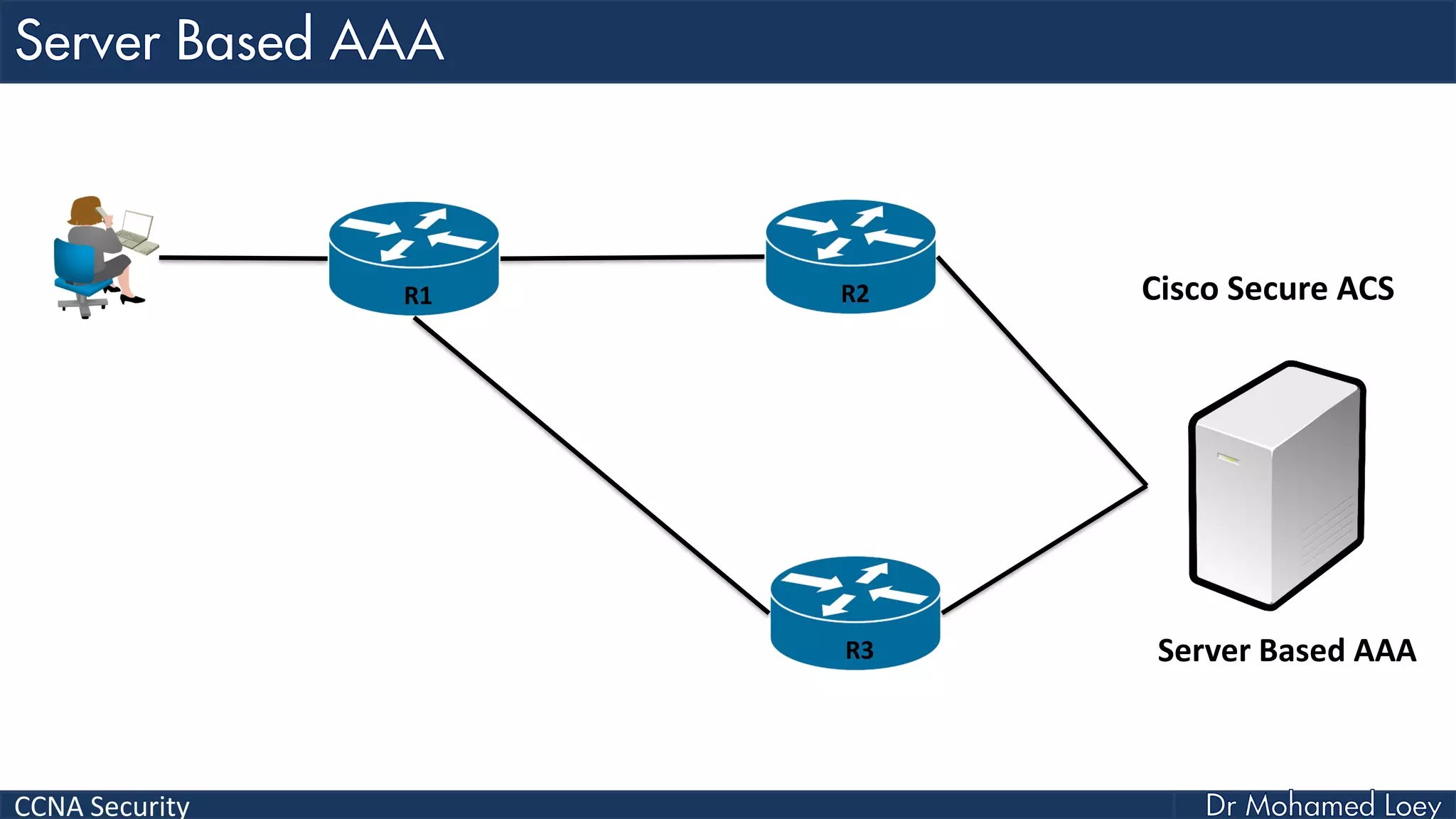
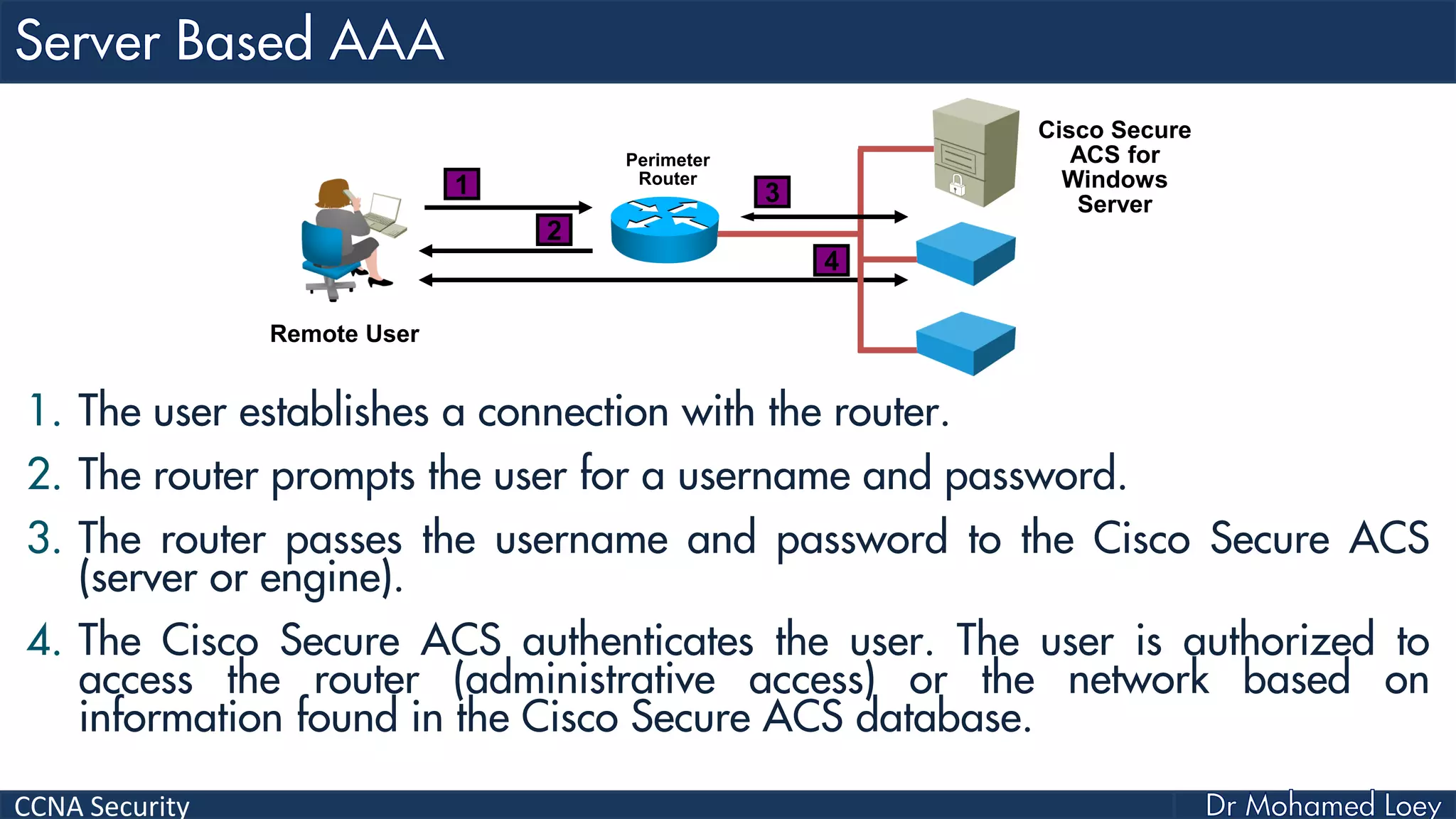
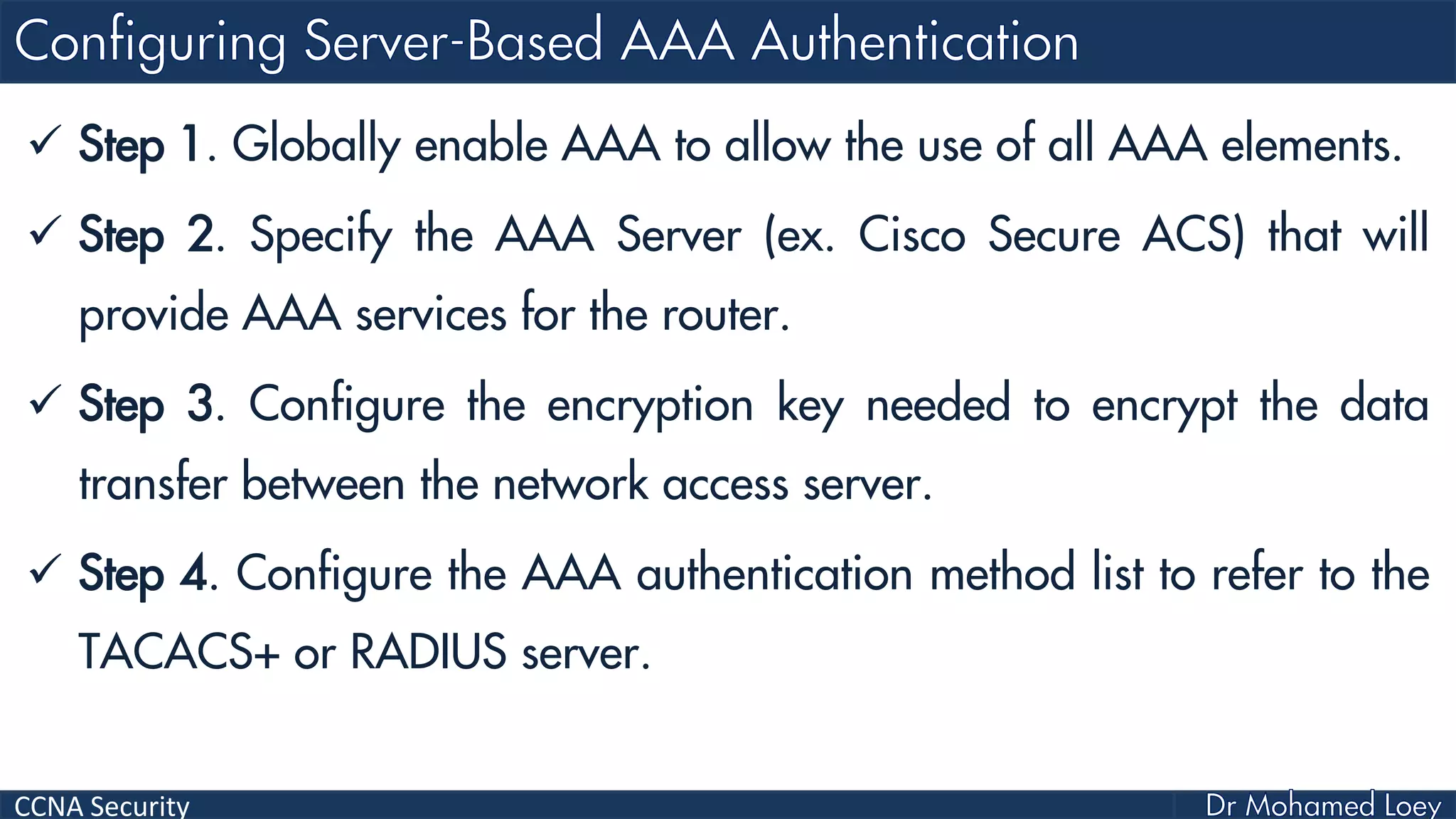
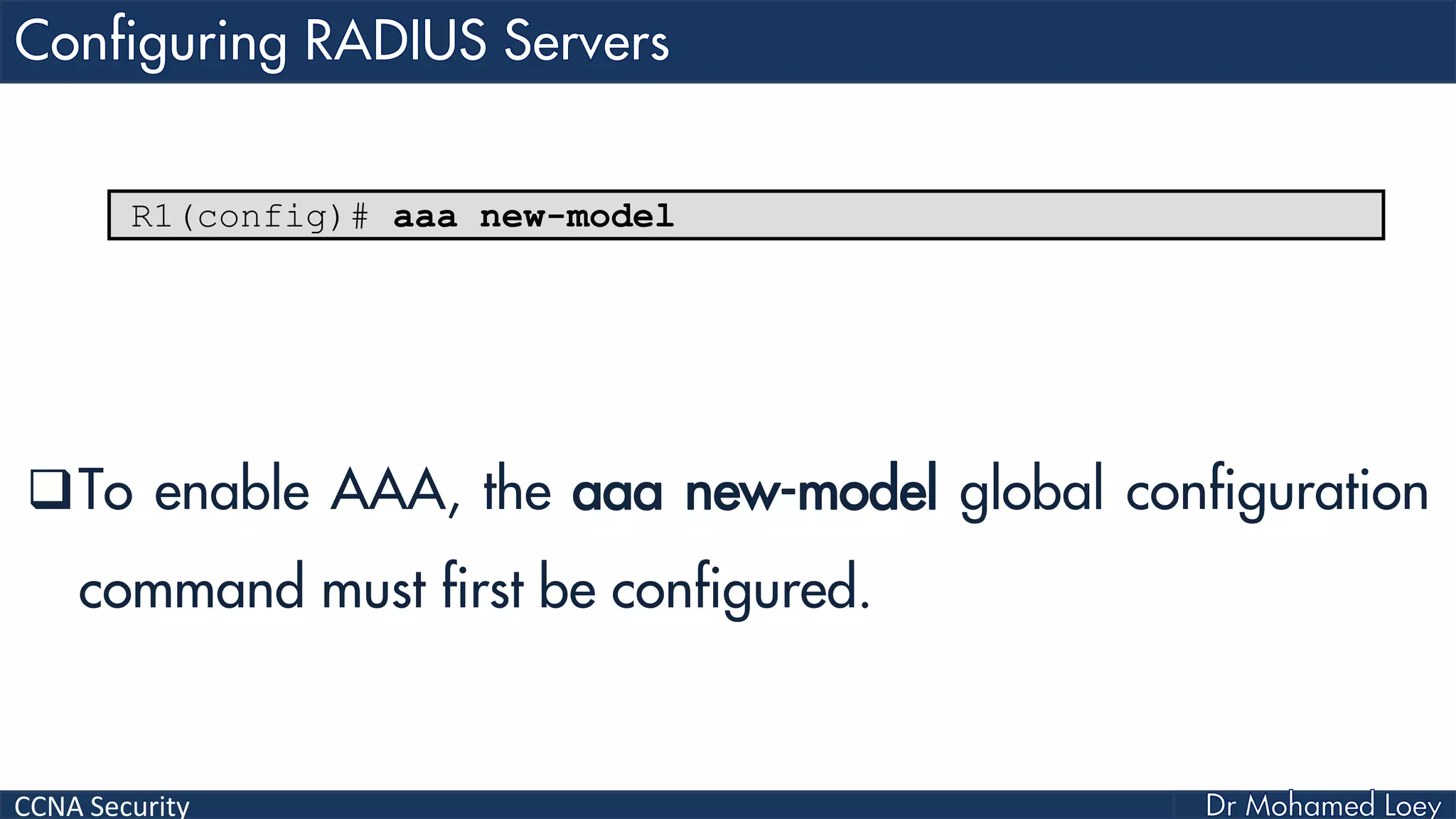
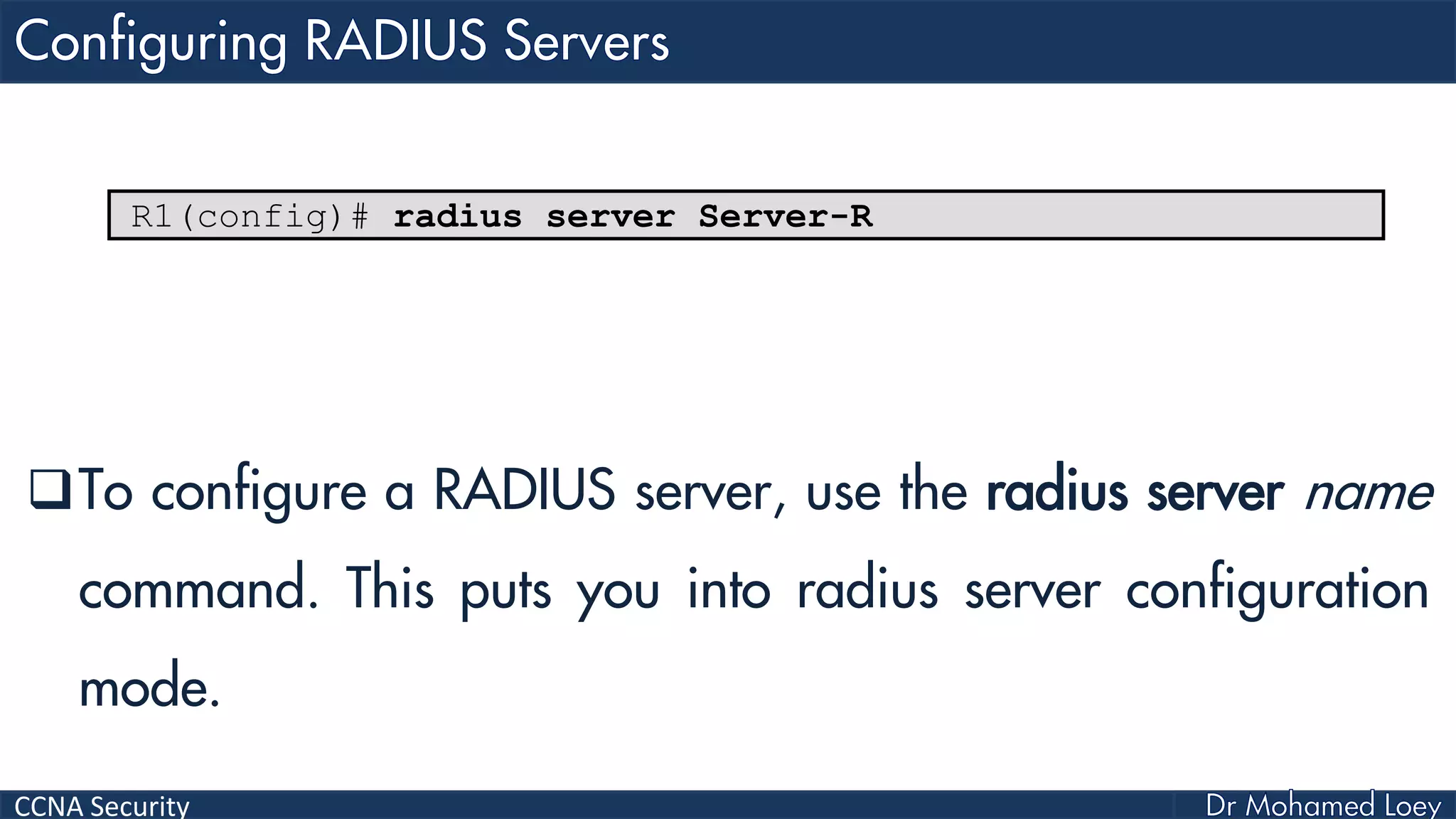
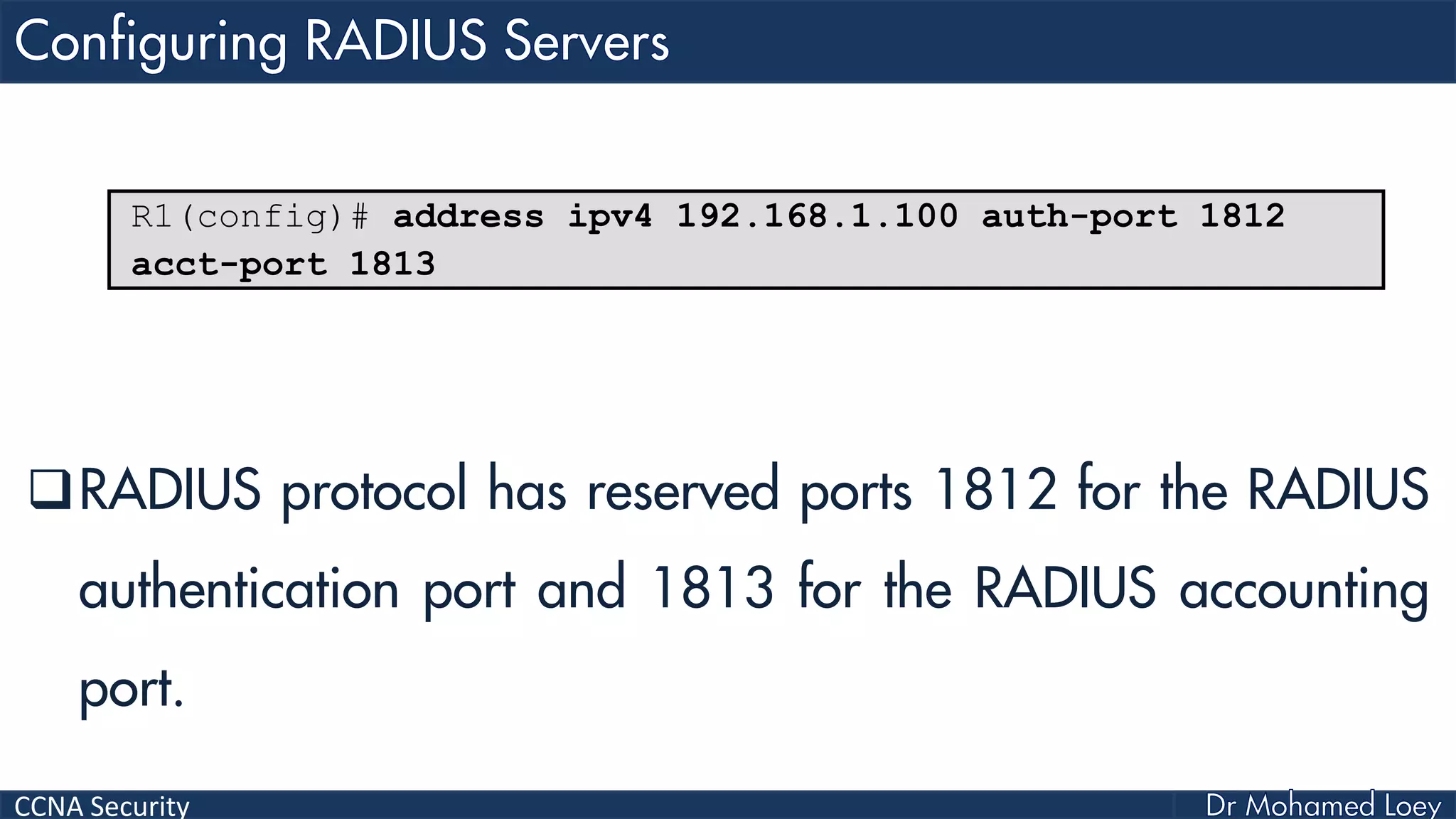
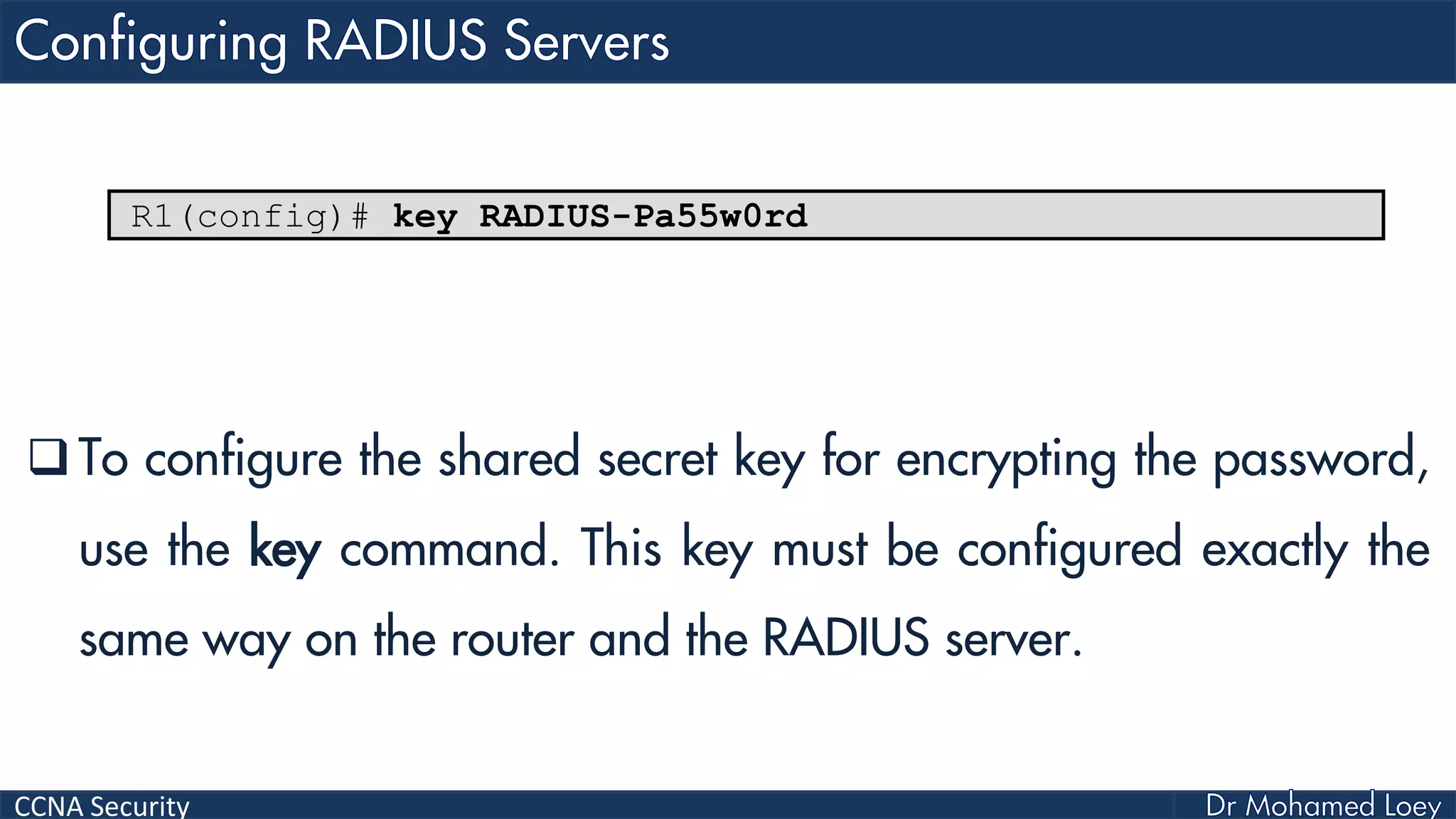
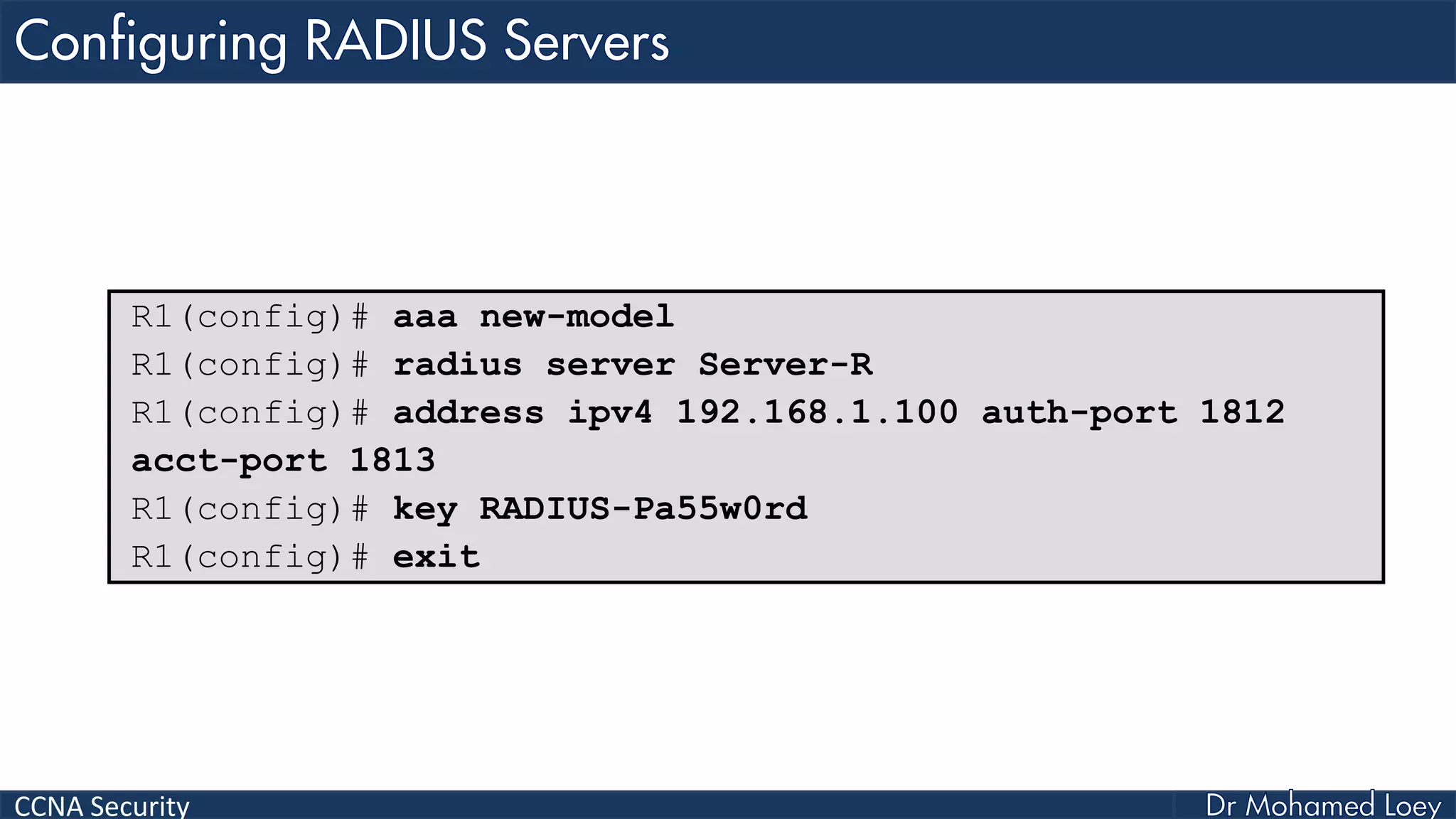
The document covers various aspects of network security, specifically focusing on authentication, authorization, and accounting (AAA) processes essential for effective network management. It discusses methods for implementing AAA, including local and server-based authentication, and explains protocols like TACACS+ and RADIUS used in these processes. Additionally, it highlights best practices for configuring AAA in different network environments, emphasizing the importance of securing access to network resources.