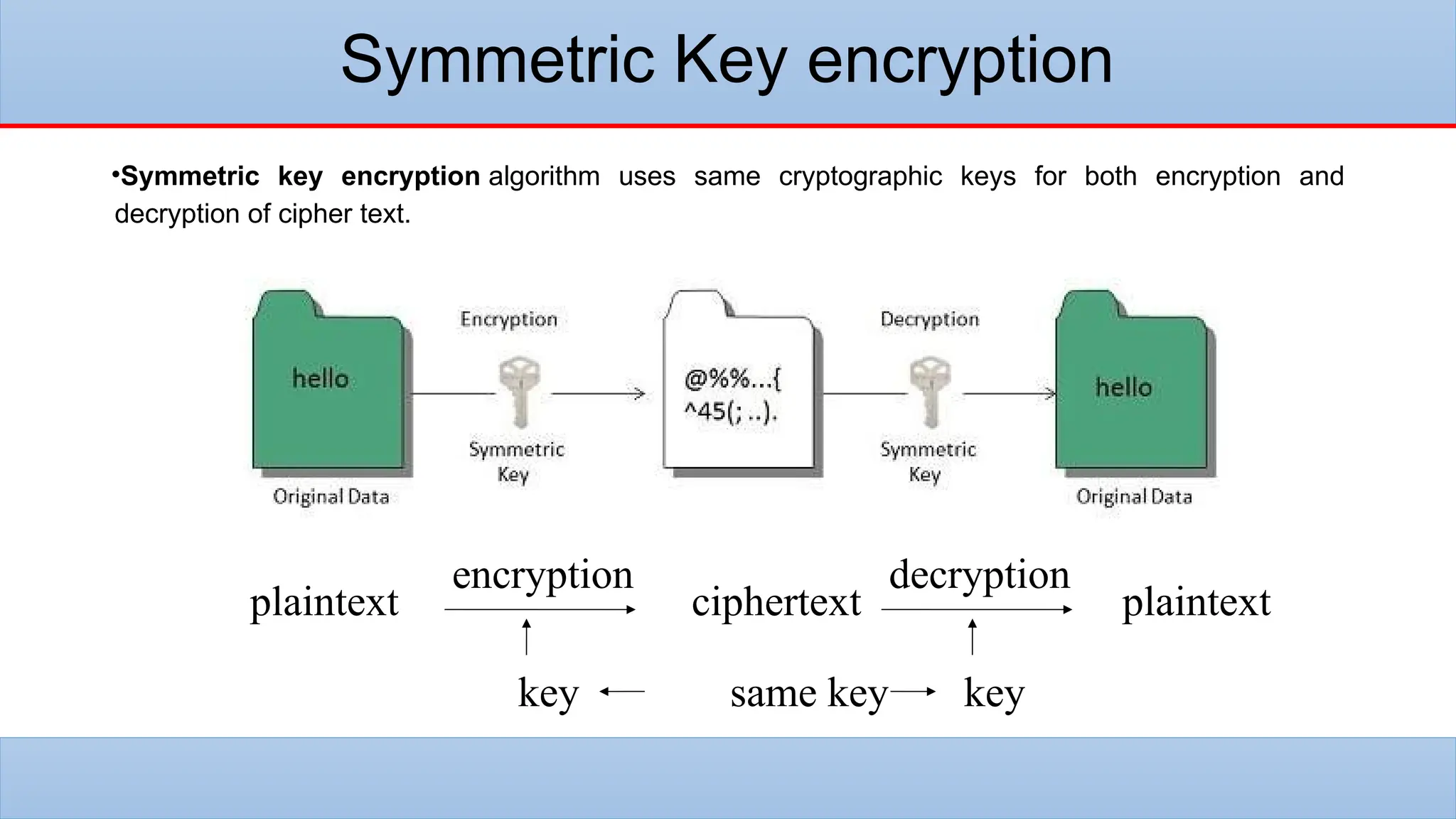
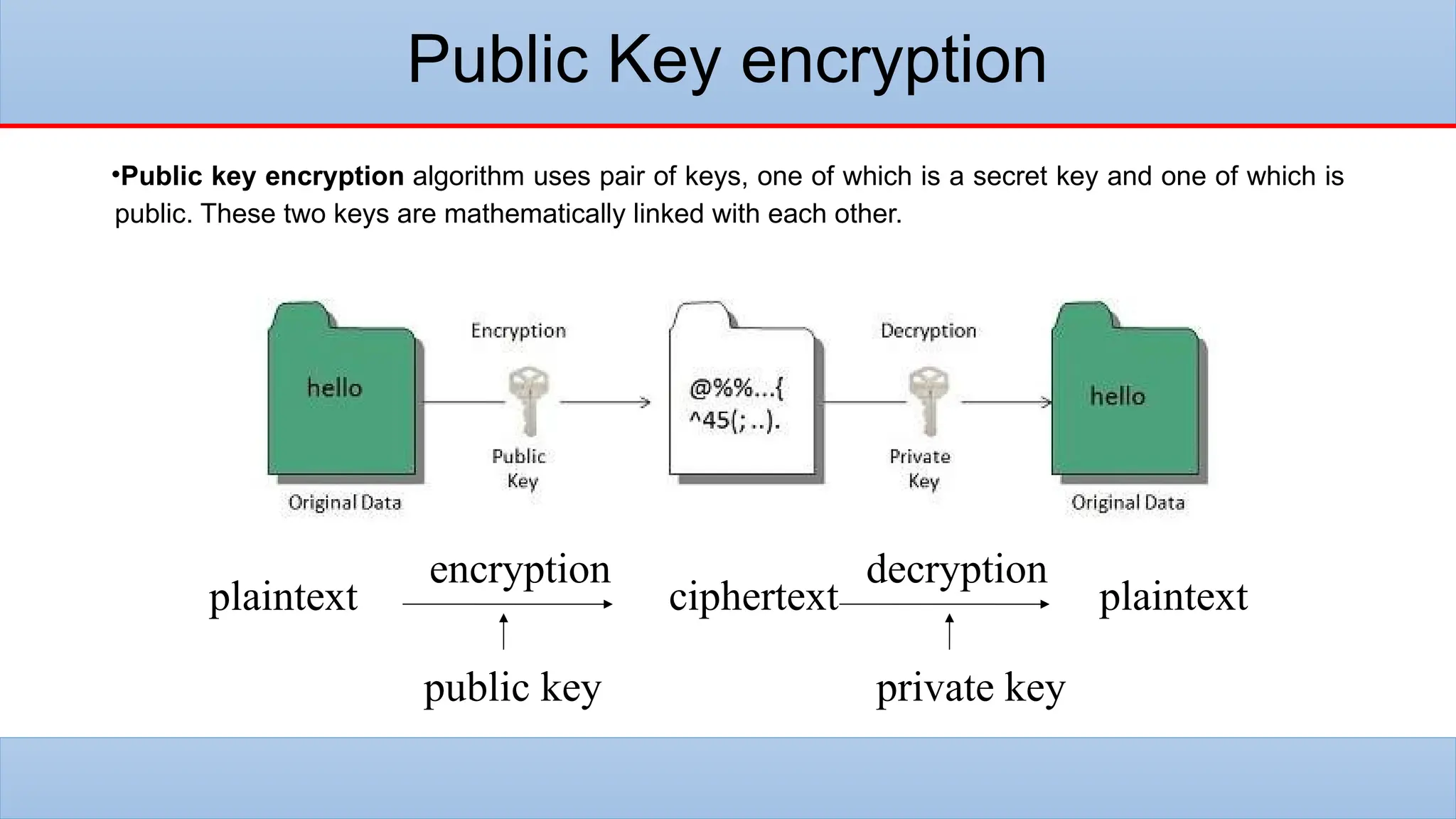
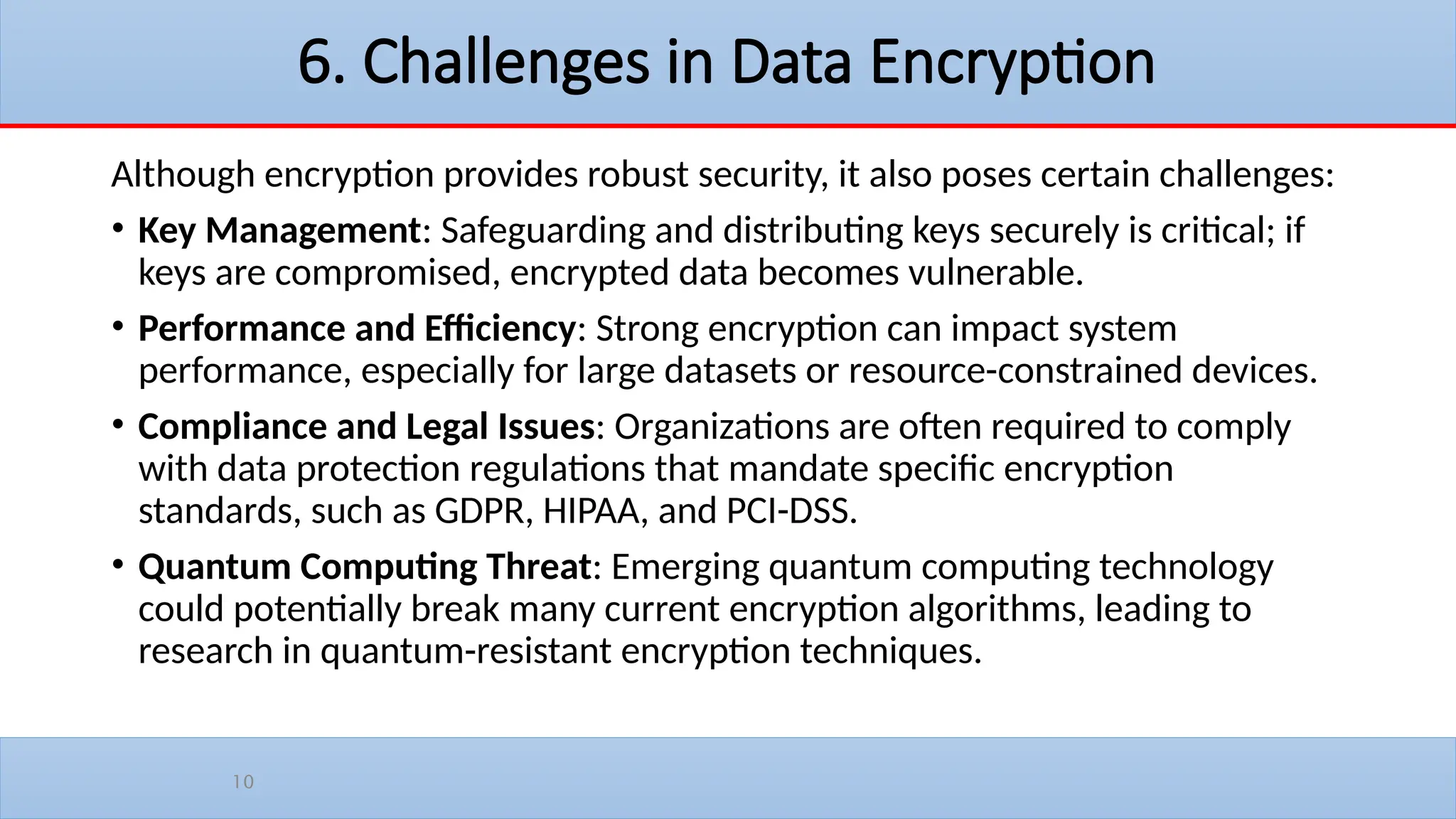
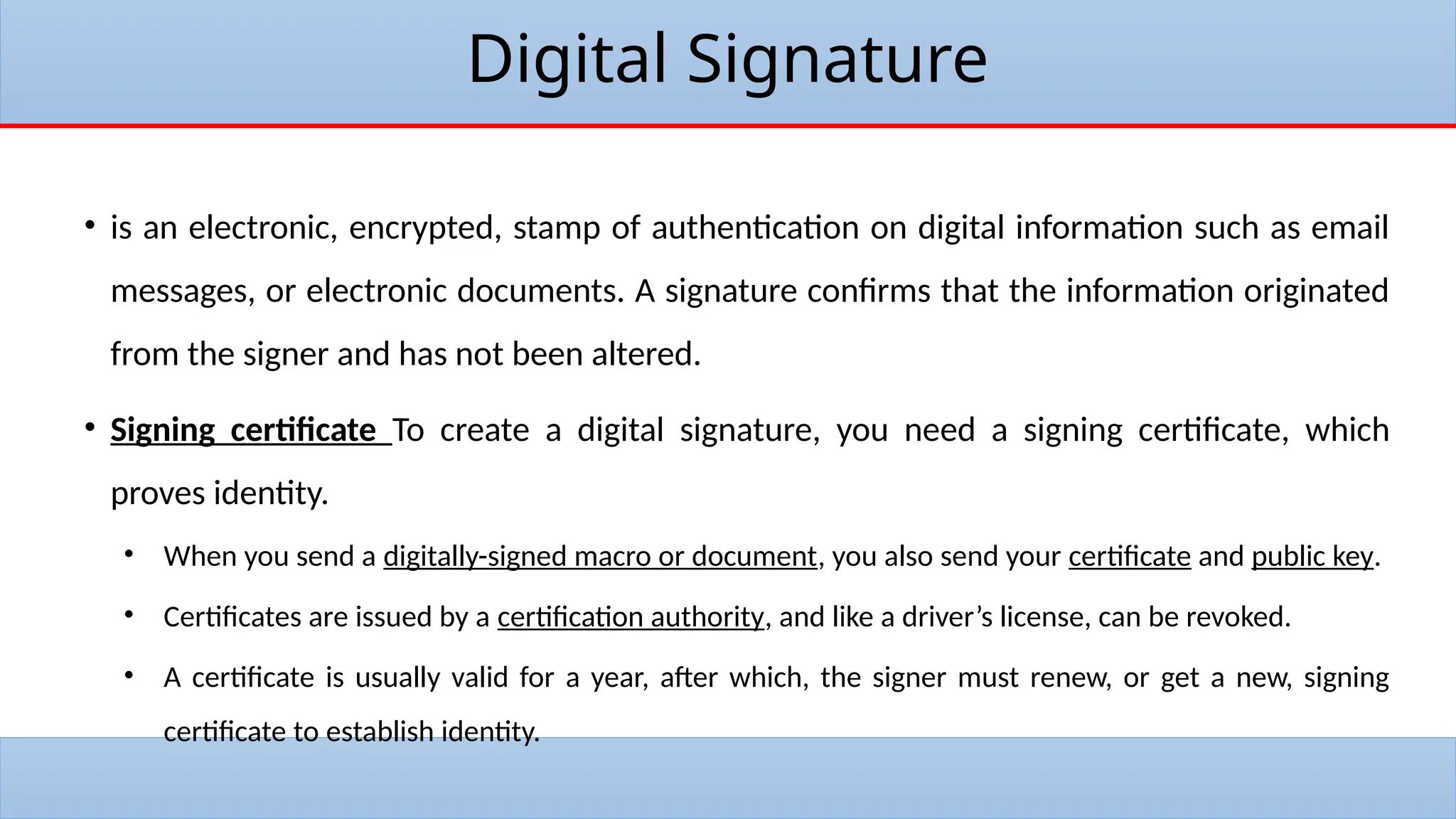
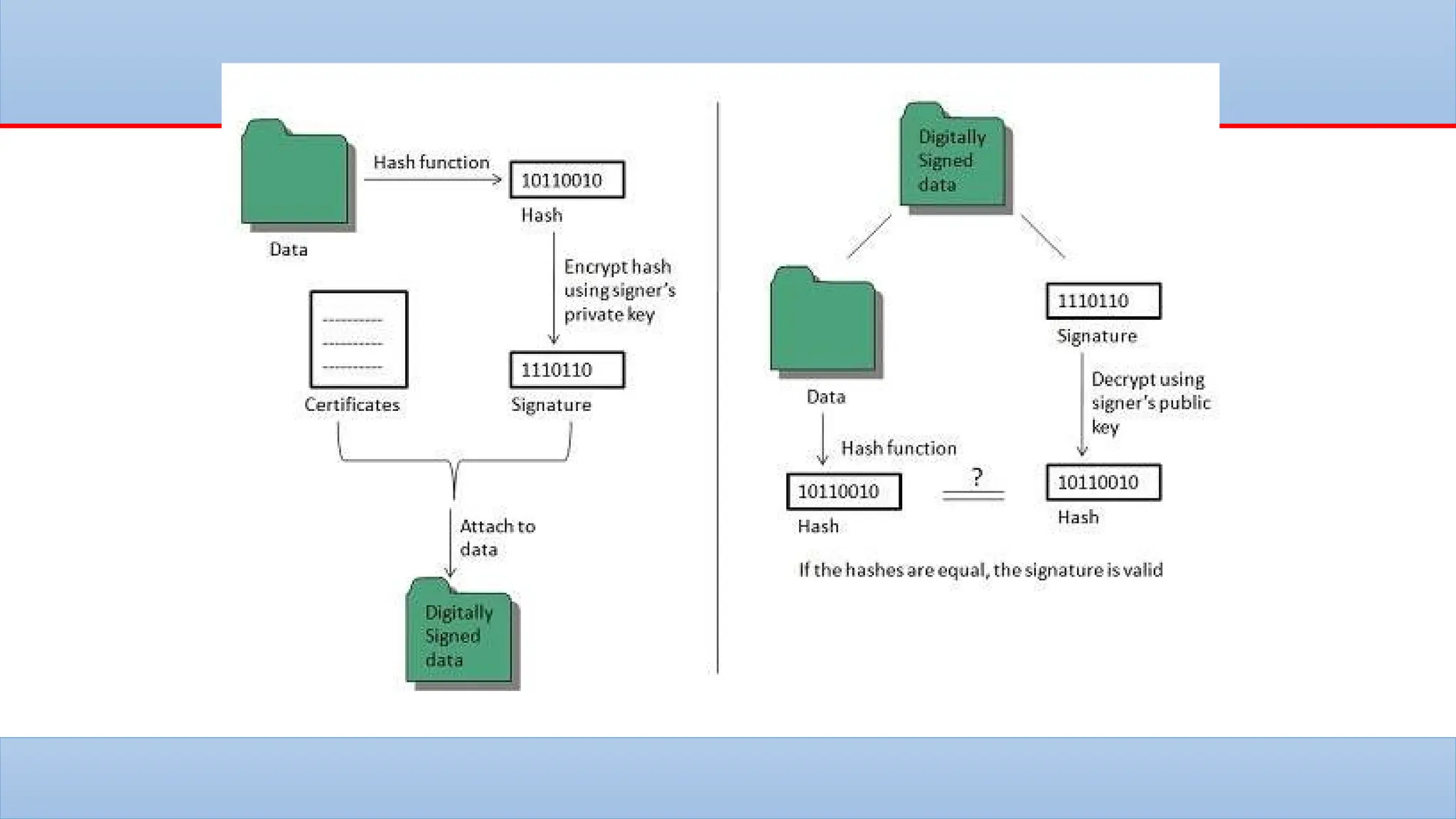
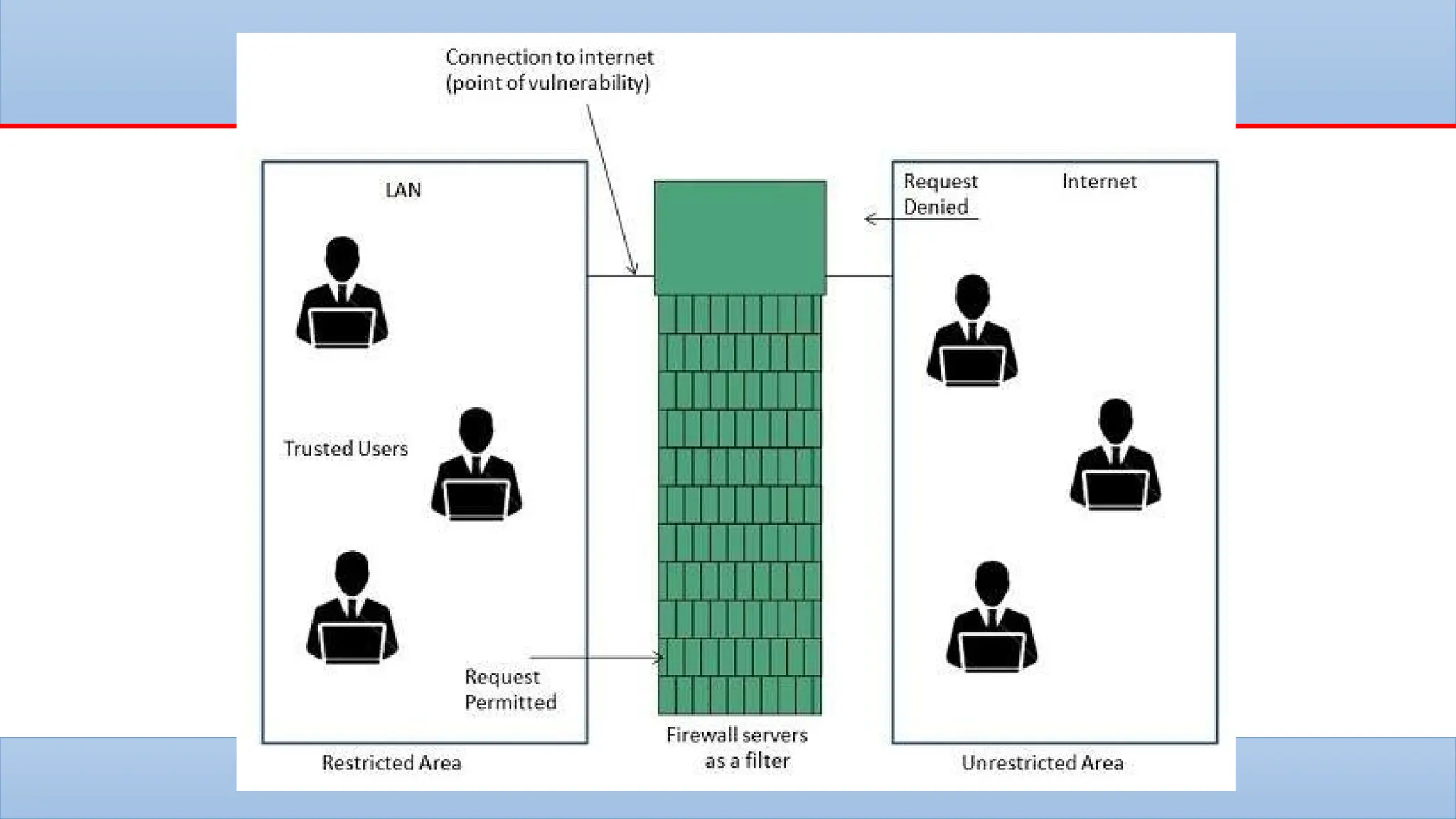
The lecture covers the historical context and purpose of data encryption, emphasizing its importance for data privacy and protection against cyber threats. It explains two main types of encryption: symmetric and asymmetric, as well as challenges such as key management and the potential threats posed by quantum computing. Additionally, hashing and digital signatures are discussed, highlighting their role in ensuring data integrity and authenticity.