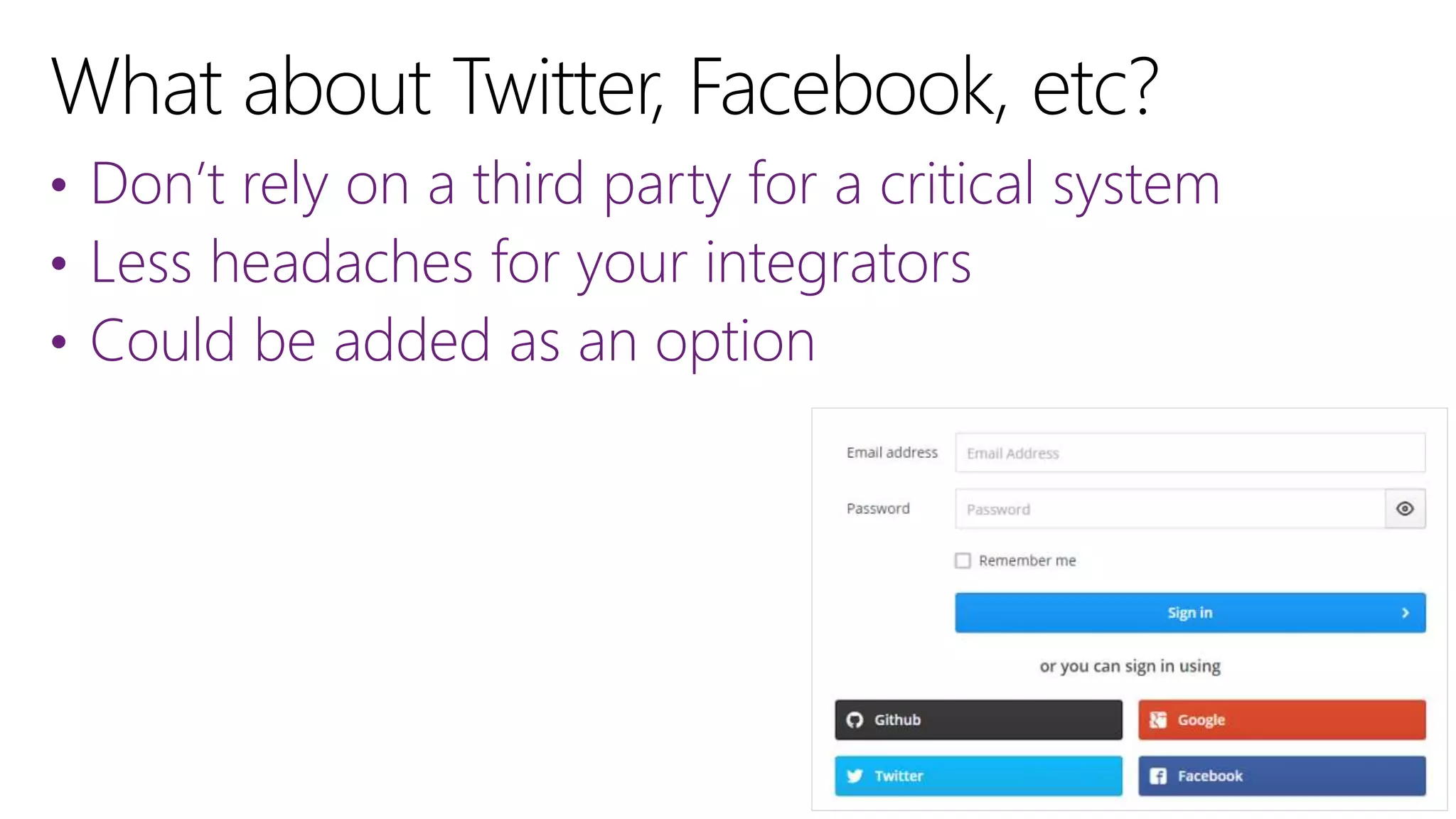
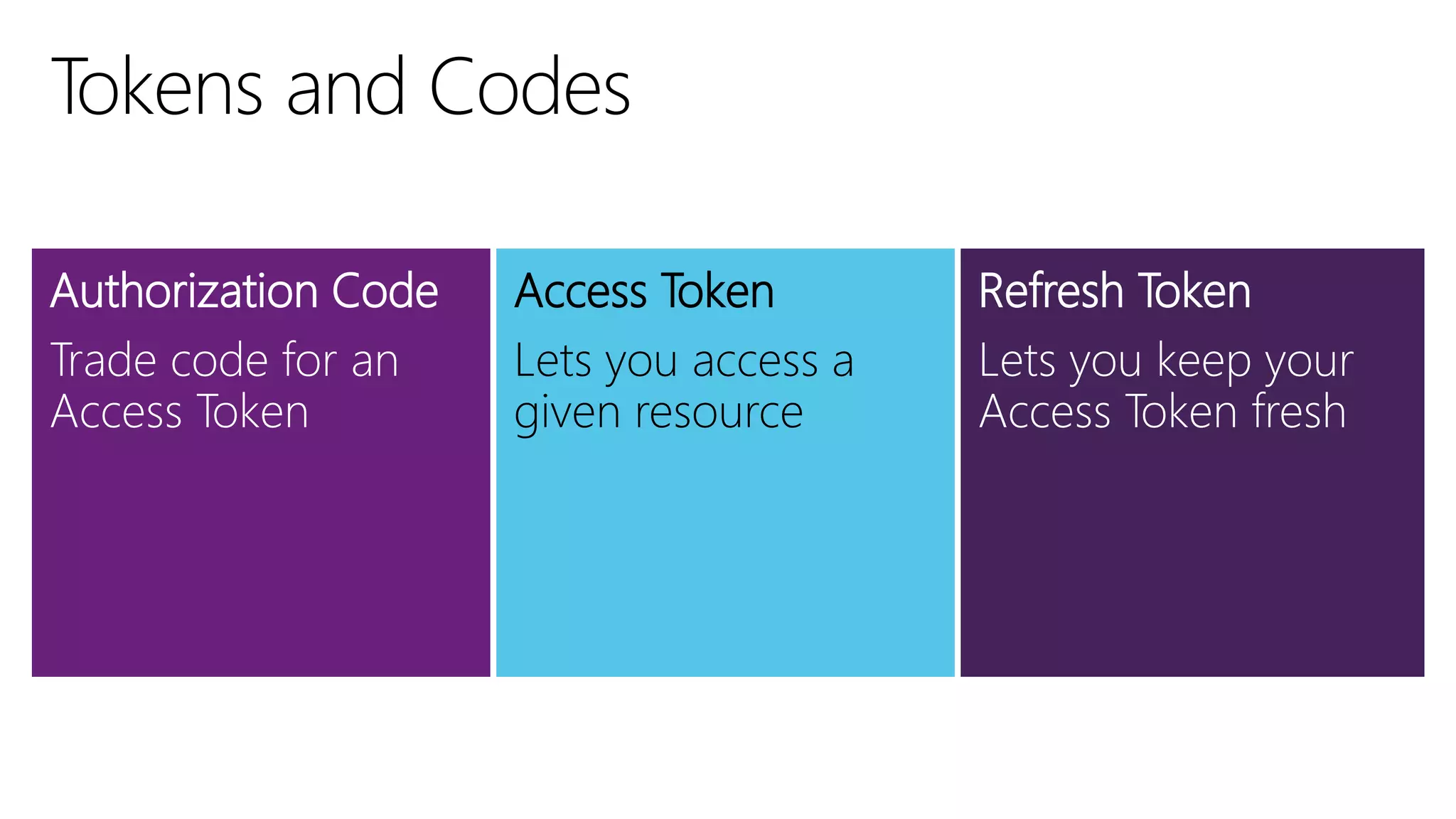
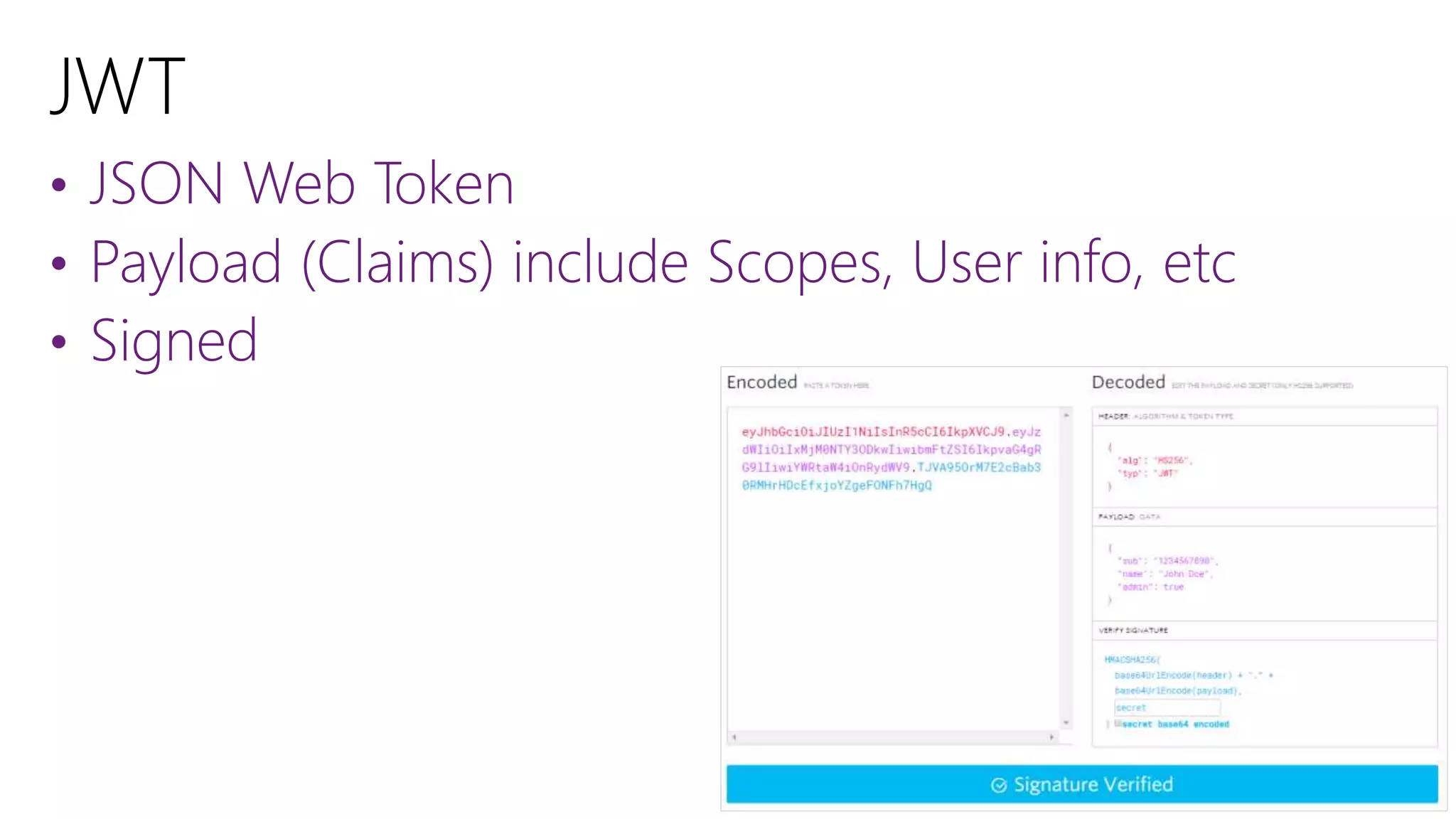
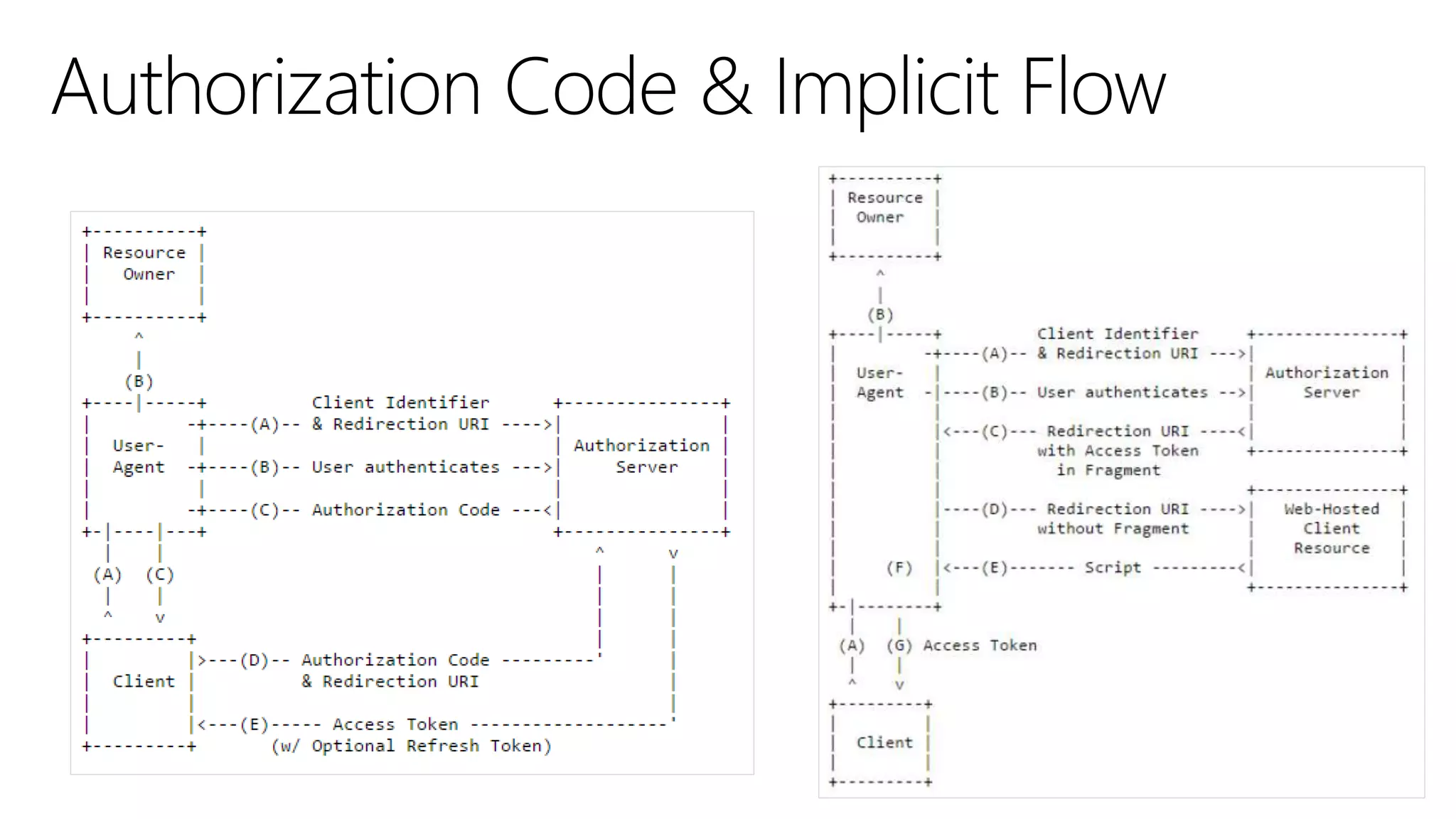
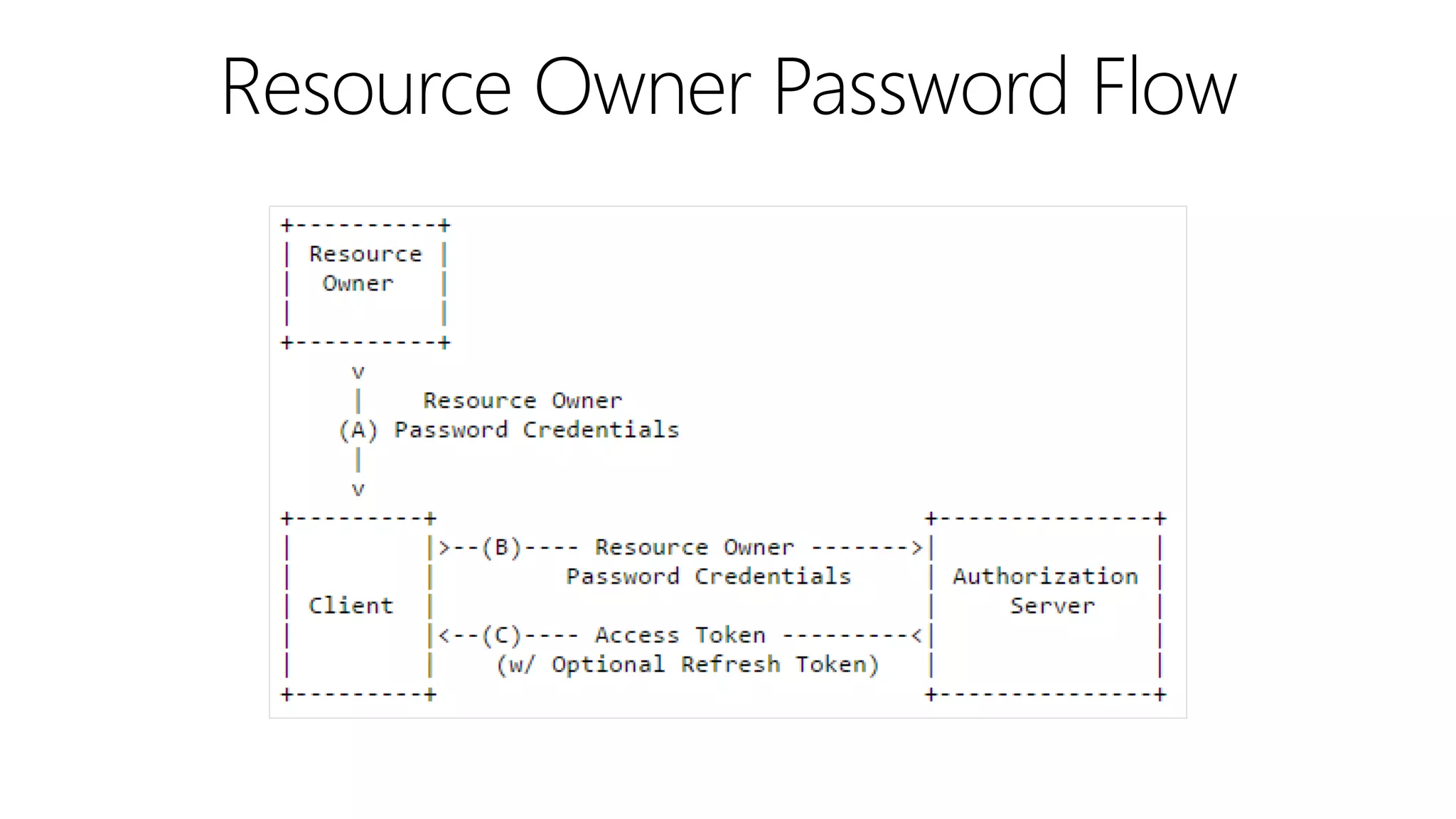
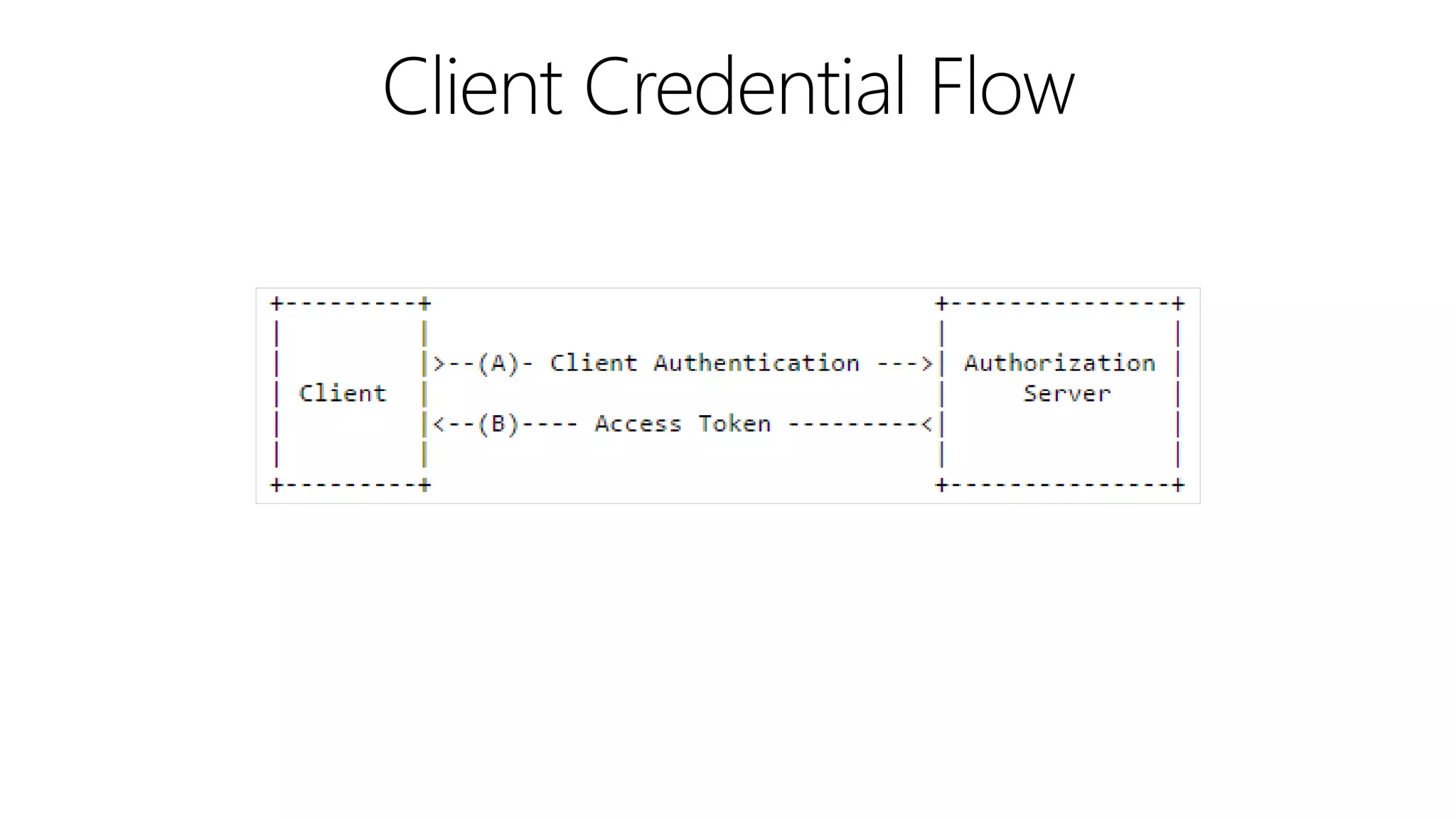
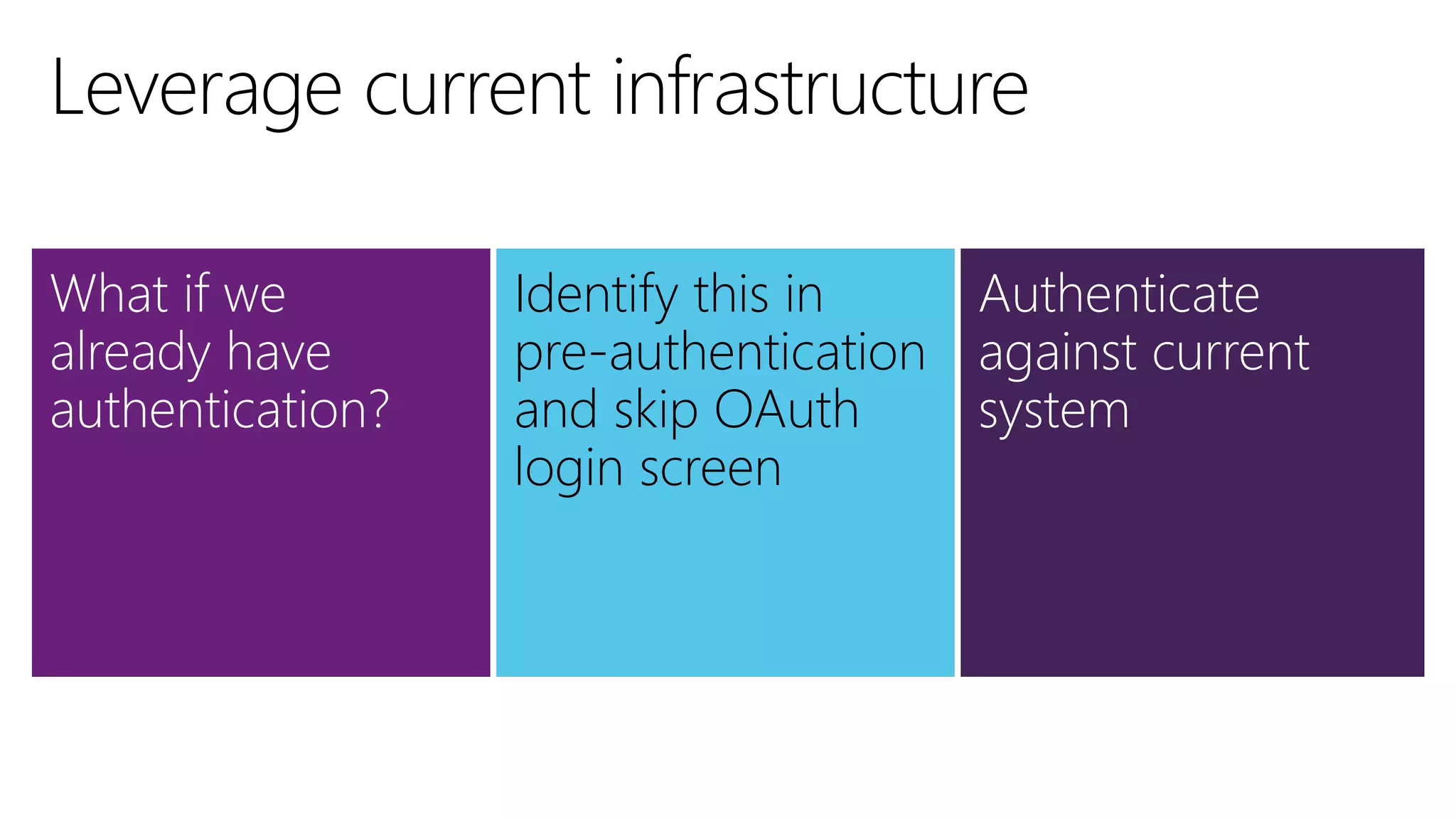
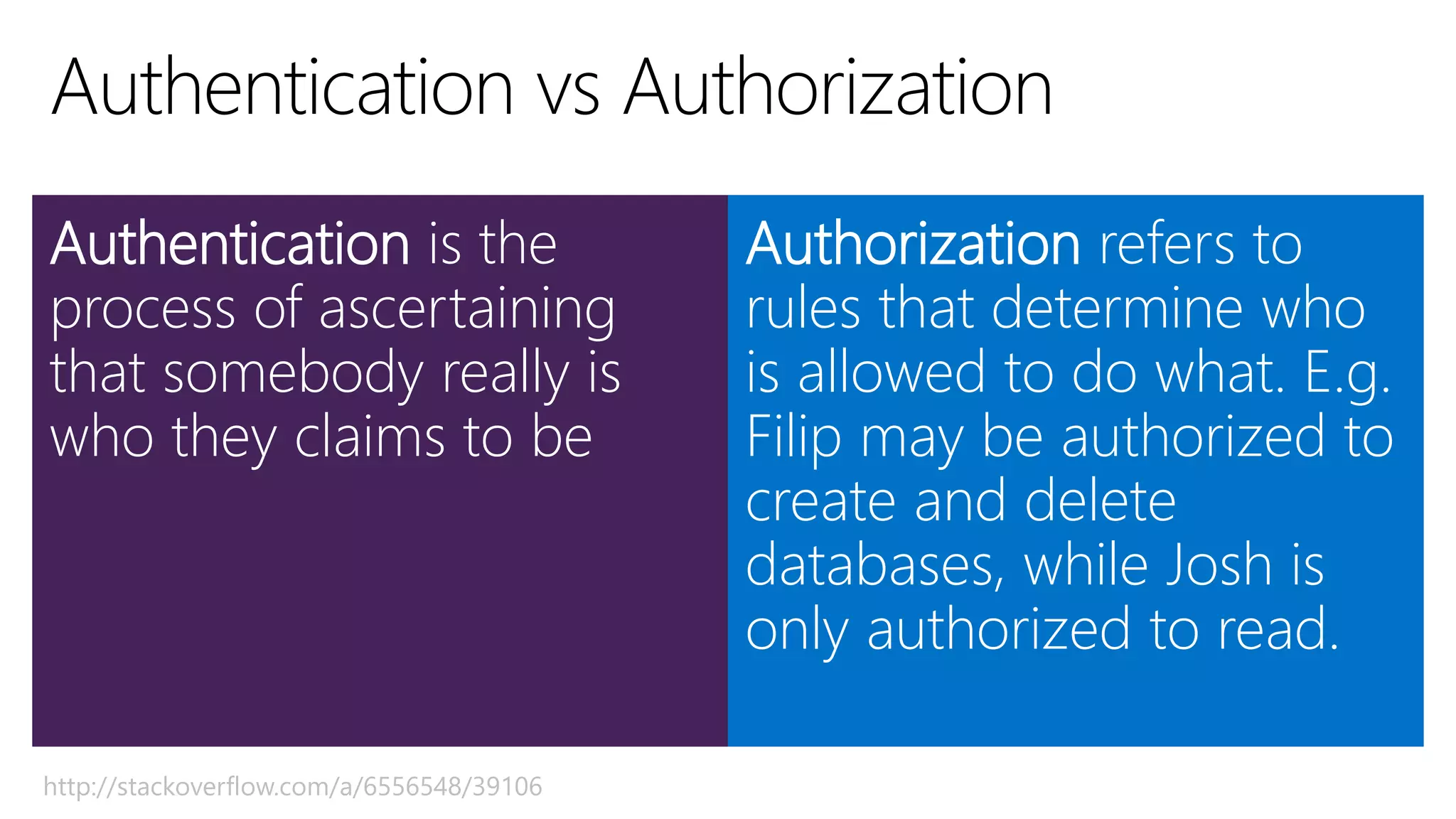
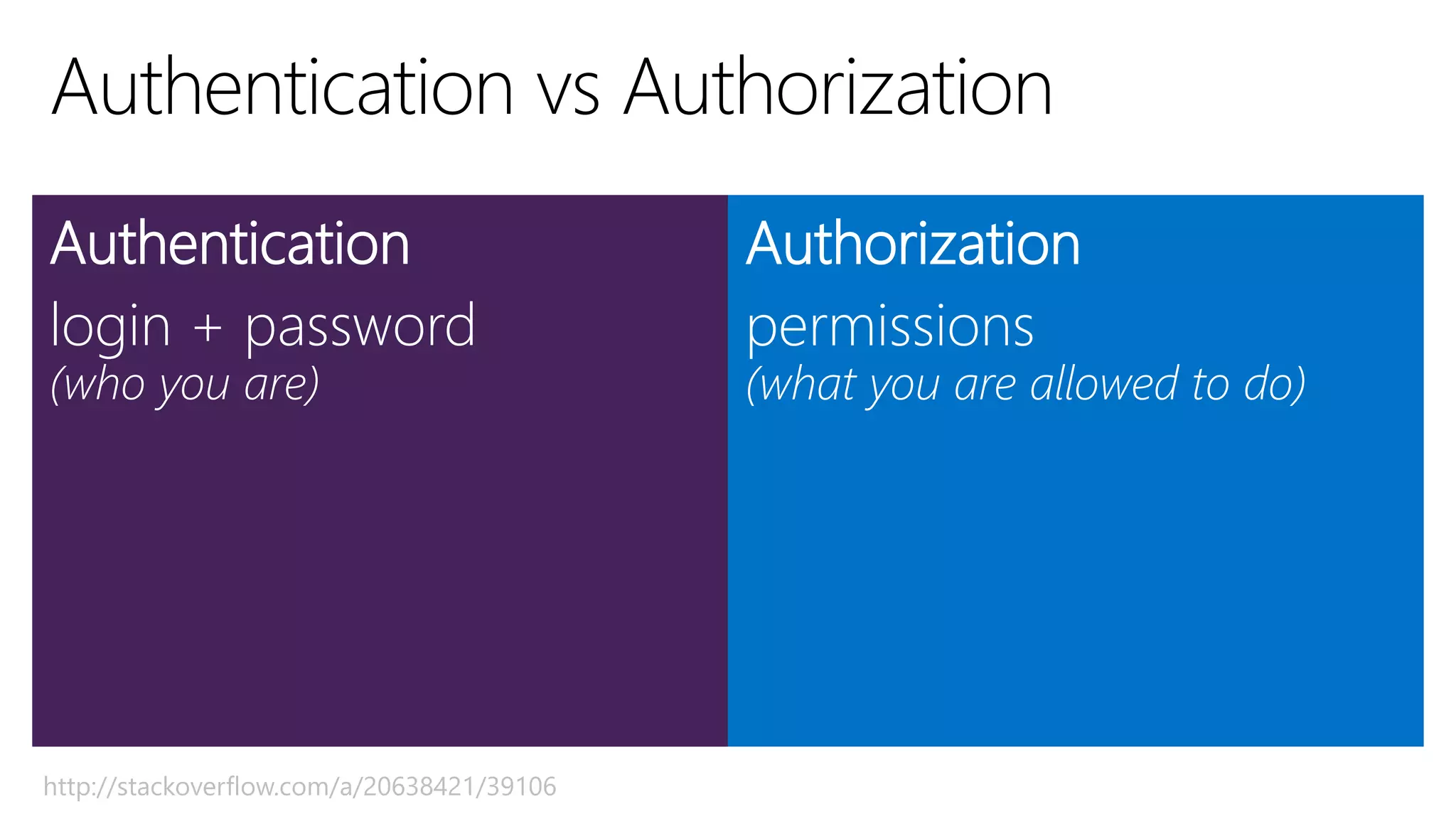
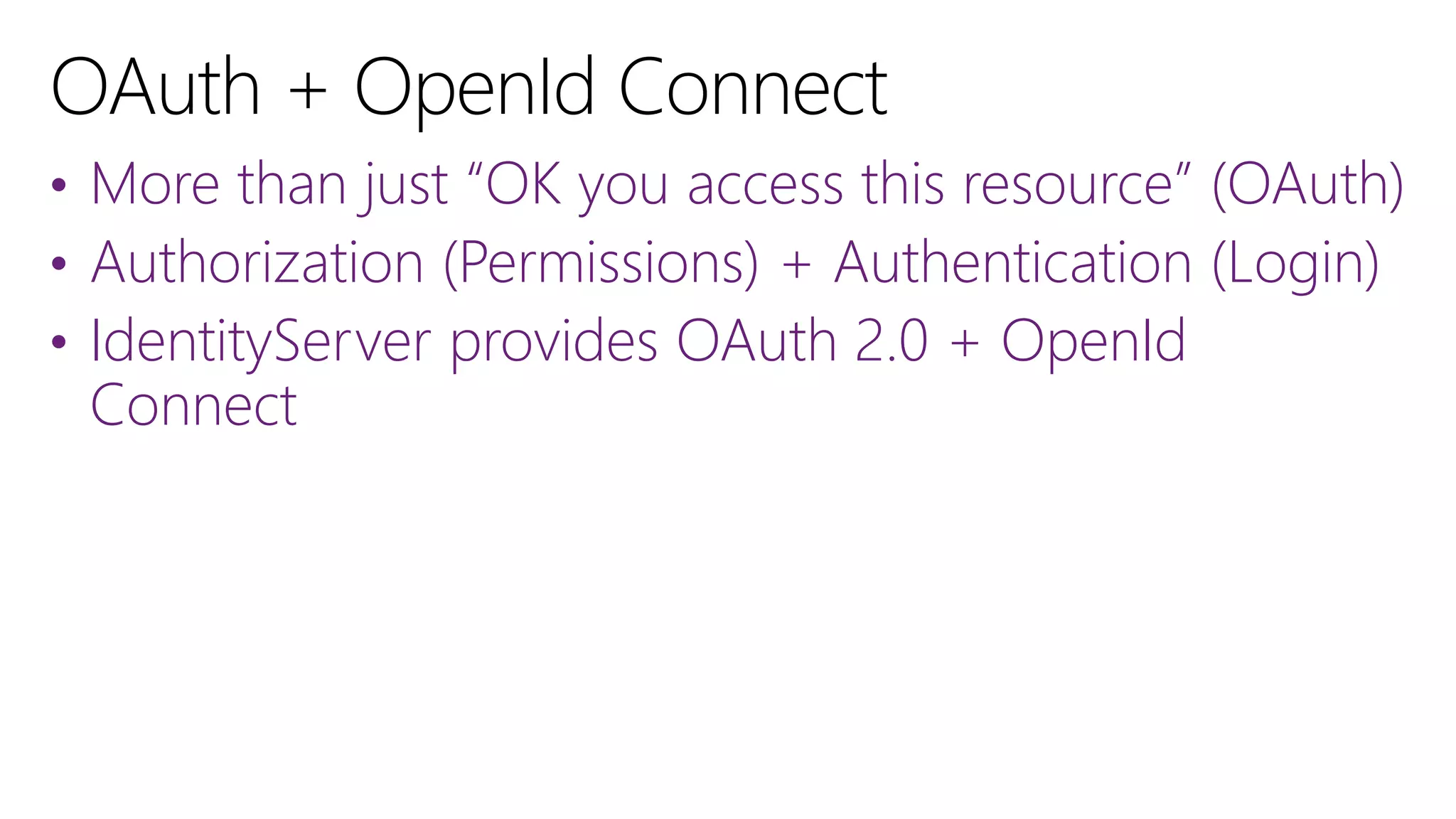
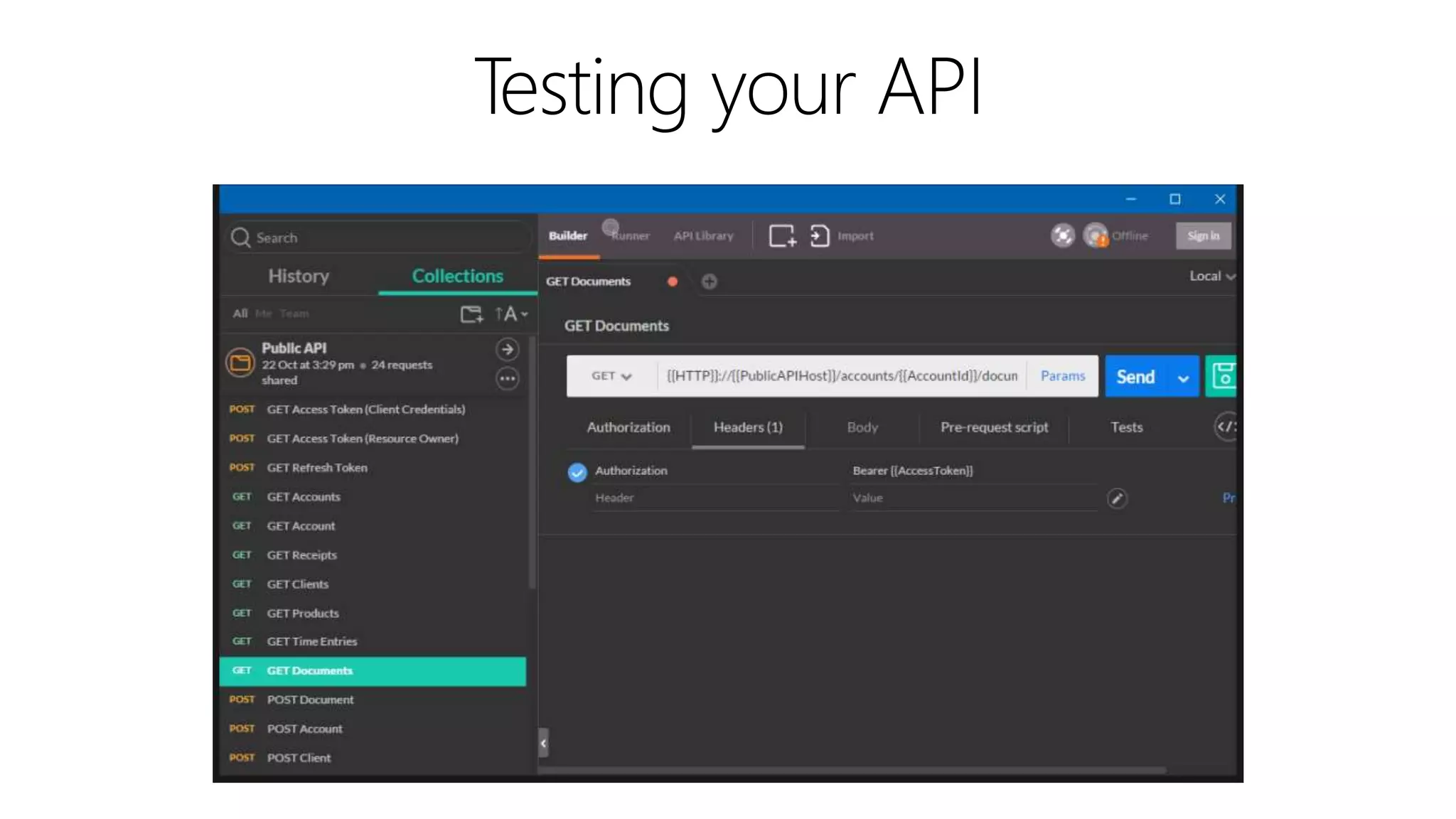
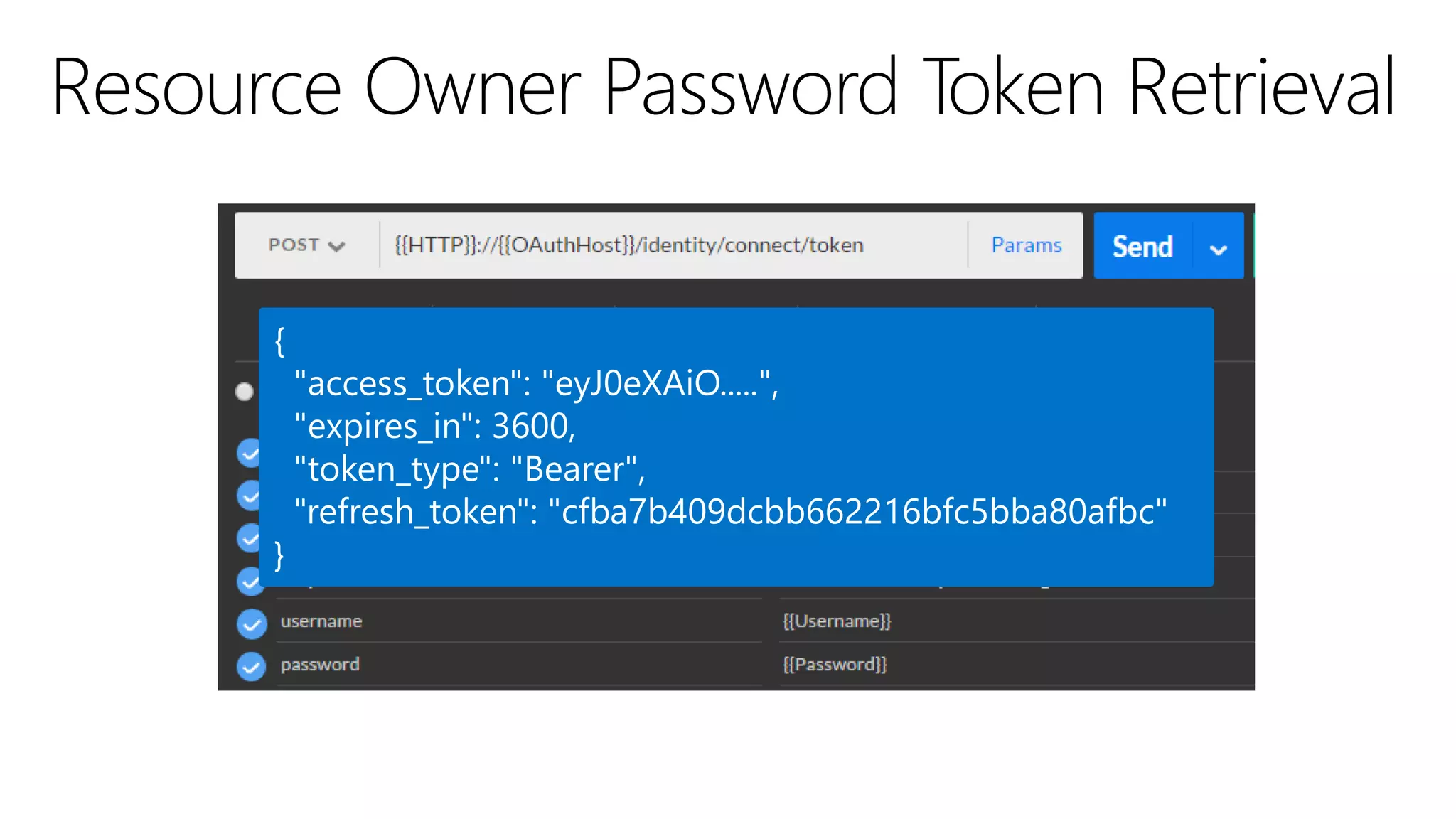
Filip Ekberg is a software engineer, author, blogger, and speaker. He discusses ASP.NET 5 and OAuth, highlighting that it is cross-platform, open source, and has a modular design. He provides tips for using OAuth with ASP.NET 5, including consuming APIs, securing APIs, and choosing an OAuth flow. He emphasizes best practices like validating tokens, securing tokens like passwords, and leveraging claims-based authentication.



![• Powershell, powershell and more powershell…
$out = (Get-Item -Path "." -Verbose).FullName
$(dnu restore --no-cache --lock --unlock --parallel)
get-childitem -recurse -filter 'project.json' -exclude '*artifacts*', '*Build*', '*Publish*' | Where-Object {
!$_.Directory.FullName.Contains("artifacts")
} | ForEach-Object {
$res = $(cd $_.Directory;$?) -and $(dnu build | Out-Host;$?)
-and $(dnu pack --configuration release --out $outBuildPackages)
if (!$res) {
Write-Error "Build failed!"
Exit 1
}
}
$out = (Get-Item -Path "." -Verbose).FullName
get-childitem -recurse -filter 'project.json' -exclude '*artifacts*', '*Build*', '*Publish*' | Where-Object {
$_.Directory.FullName.Contains("Tests")
} | ForEach-Object {
$(cd $_.Directory;$?)
$testOutput = $(dnx . test | Write-Host)
if ($testOutput -contains "*[FAIL]*") {
Write-Error "Tests failed!"
Exit 1
}
}](https://image.slidesharecdn.com/filipekberg-dddbrisbane2015-151206222556-lva1-app6891/75/Building-APIs-with-MVC-6-and-OAuth-7-2048.jpg)



















![[HttpDelete]
[Authorize("write")]
[Route("/accounts/{accountId}/documents/{documentId}")]
public async Task<JsonResult> DeleteAsync(string accountId,
long documentId)](https://image.slidesharecdn.com/filipekberg-dddbrisbane2015-151206222556-lva1-app6891/75/Building-APIs-with-MVC-6-and-OAuth-40-2048.jpg)