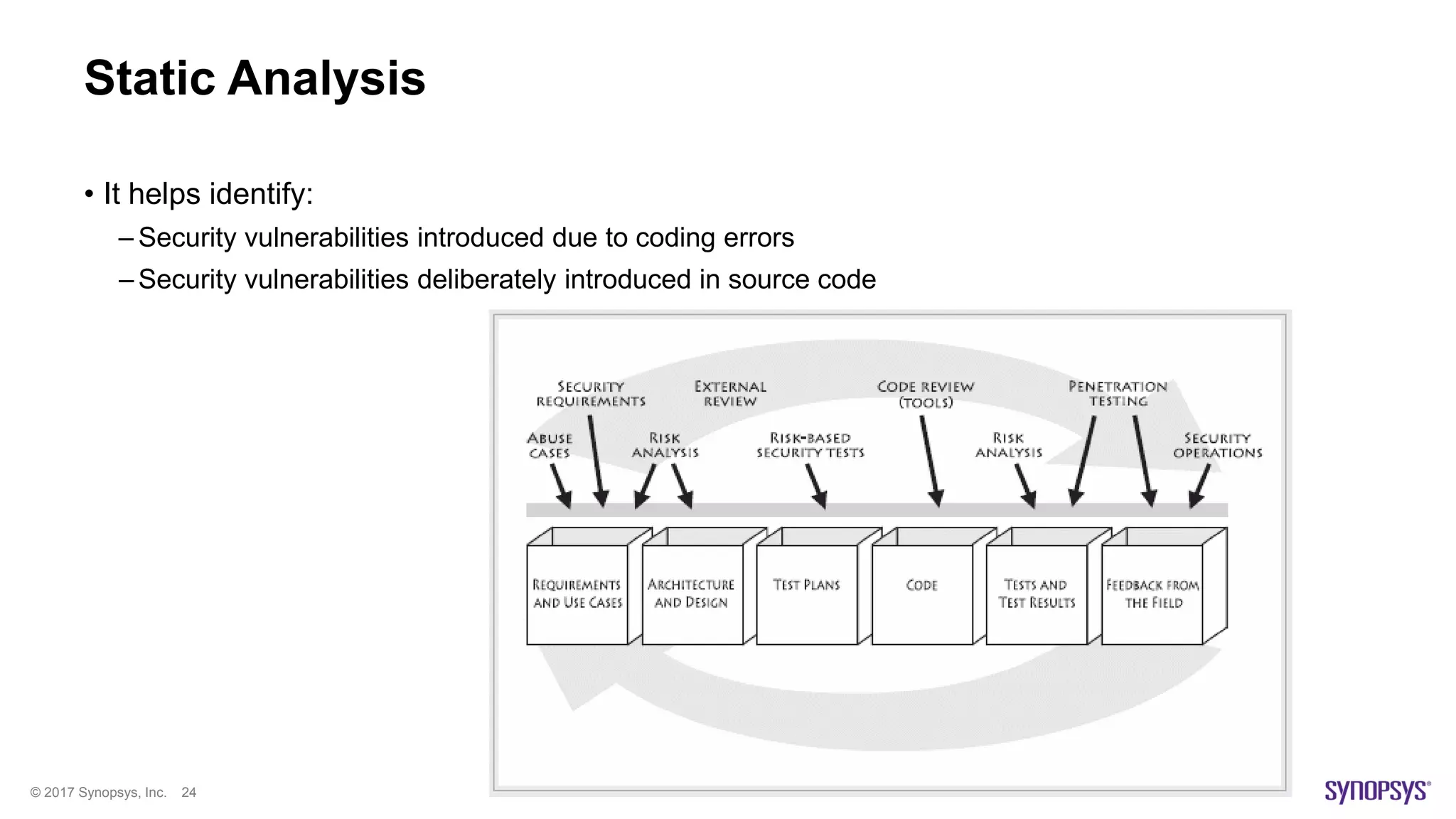
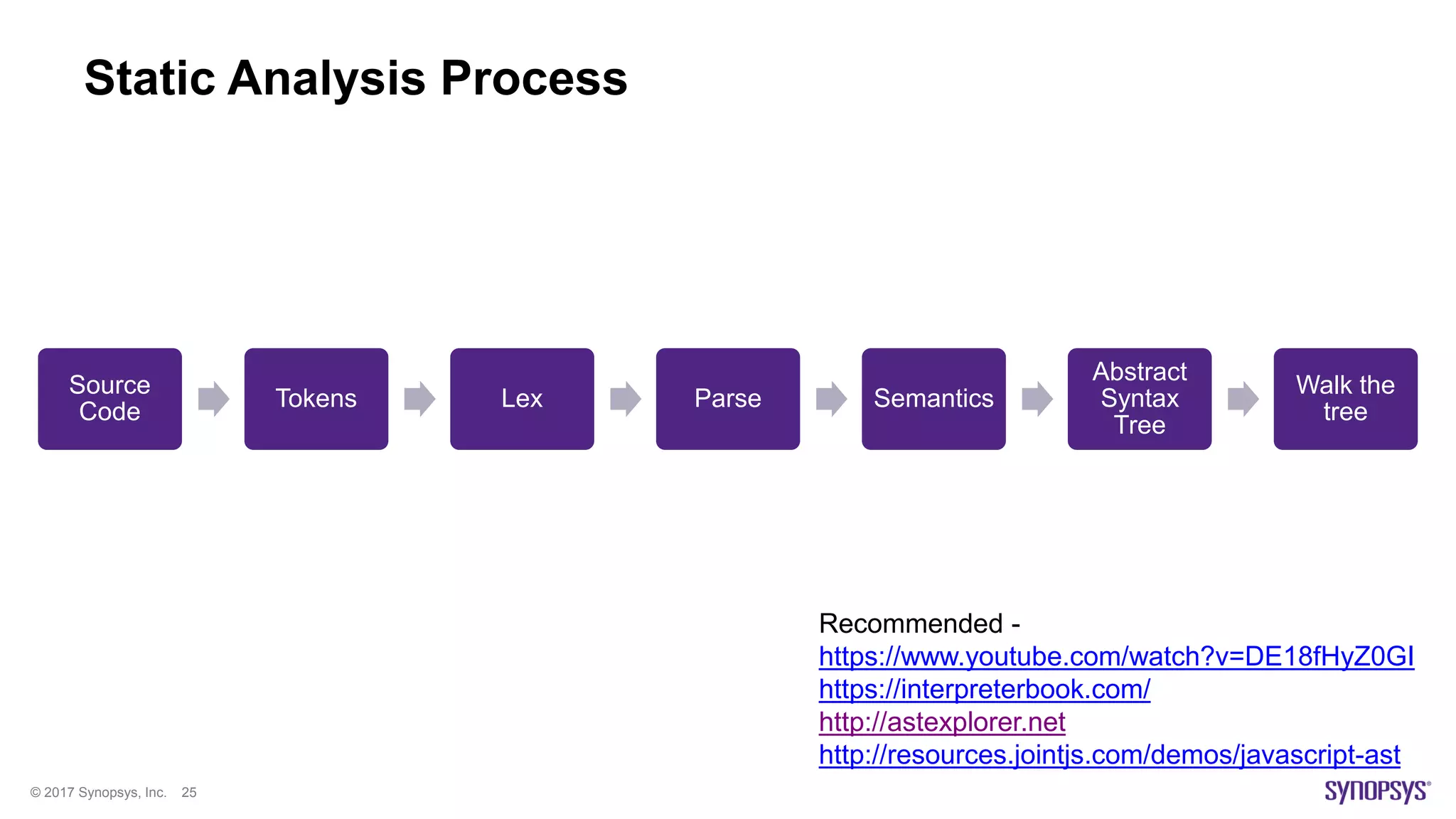
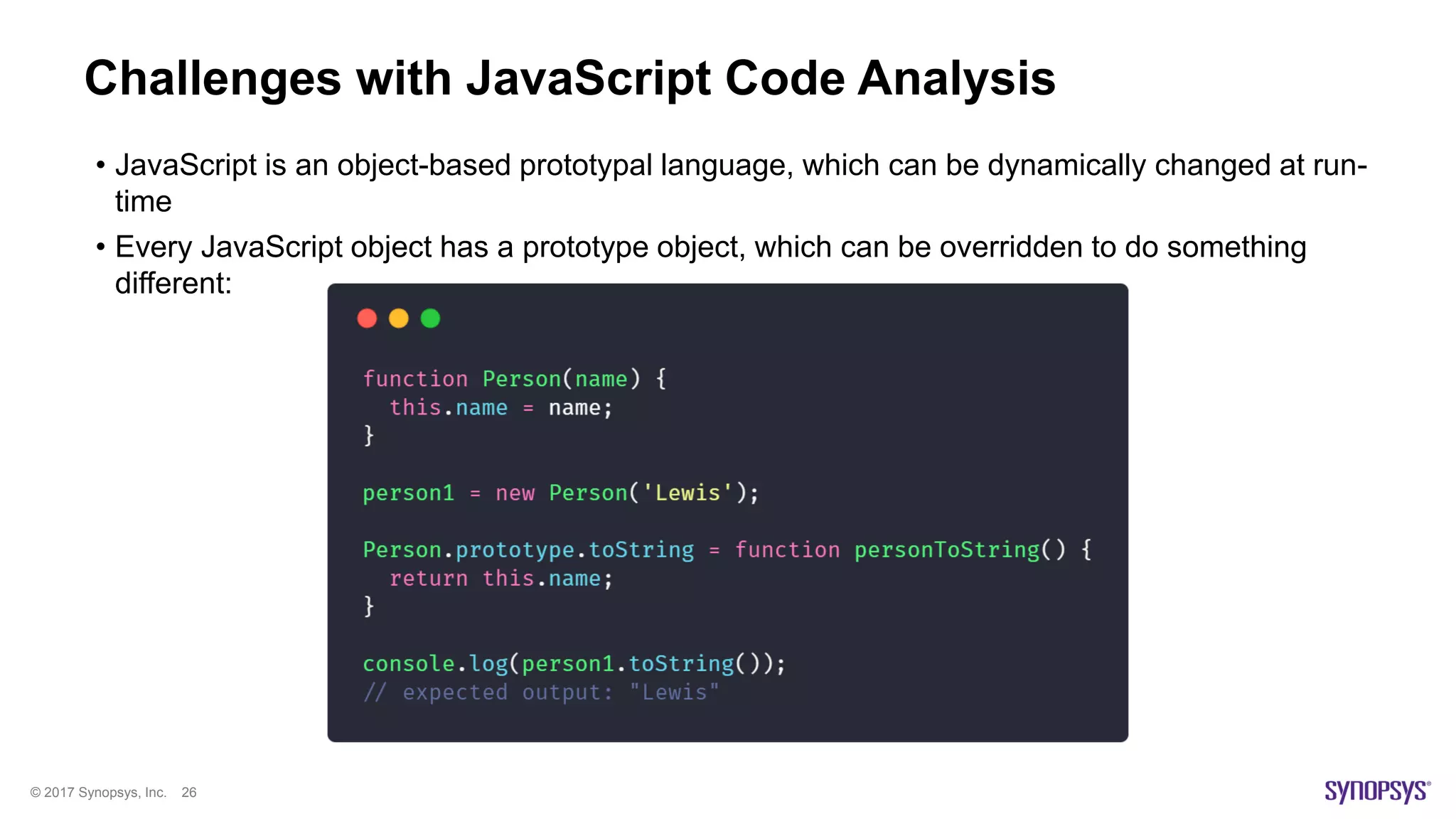
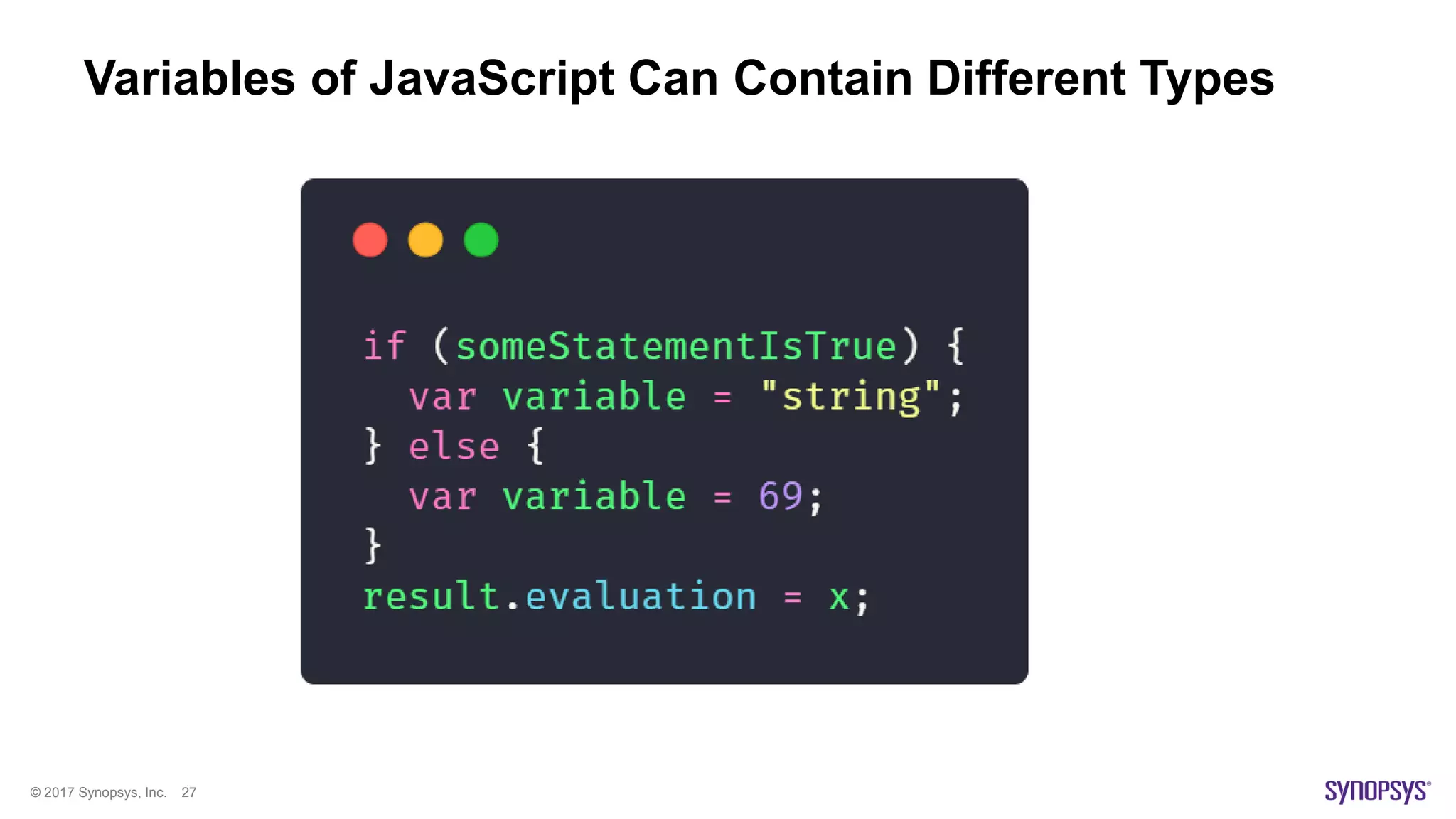
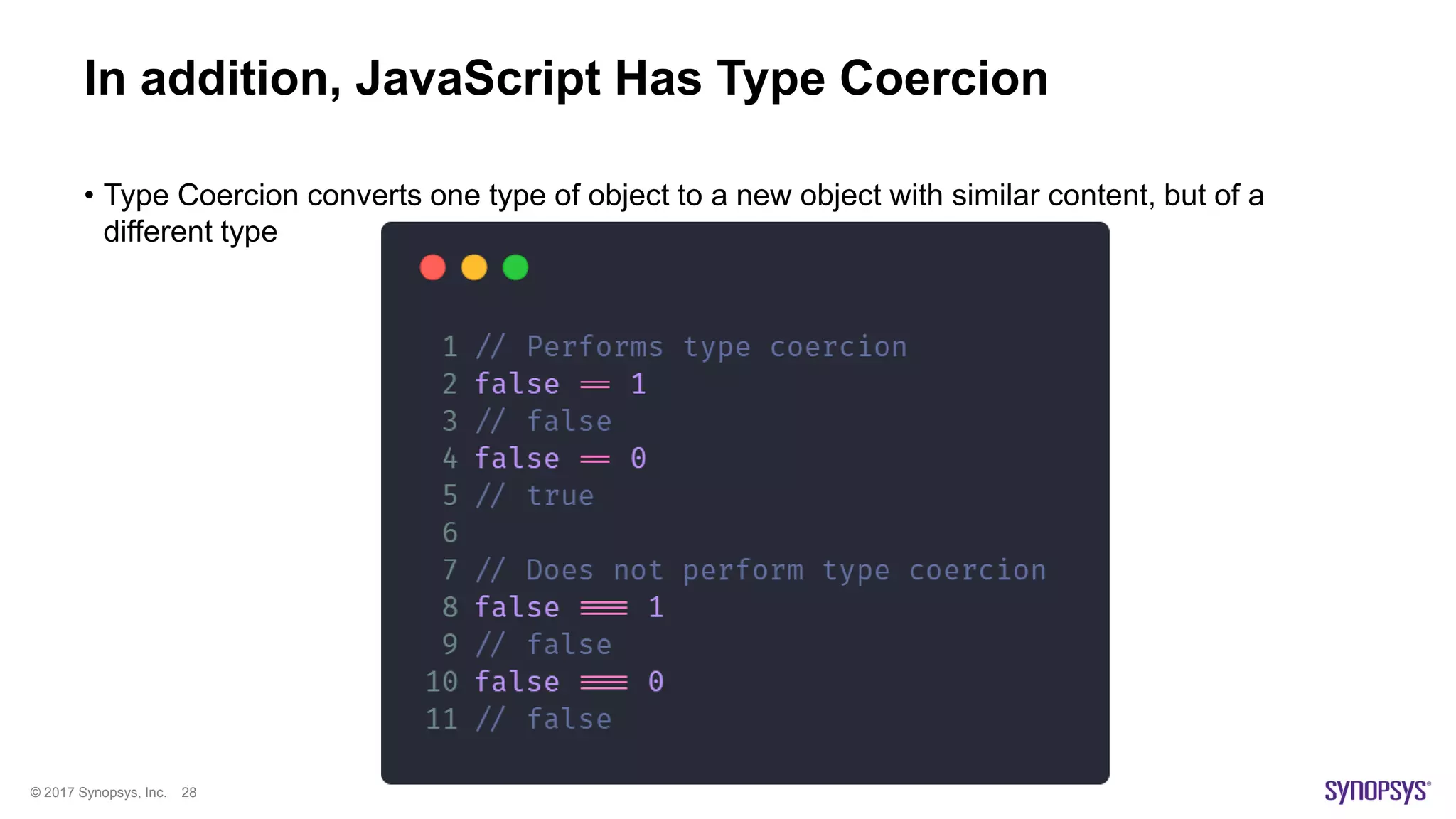
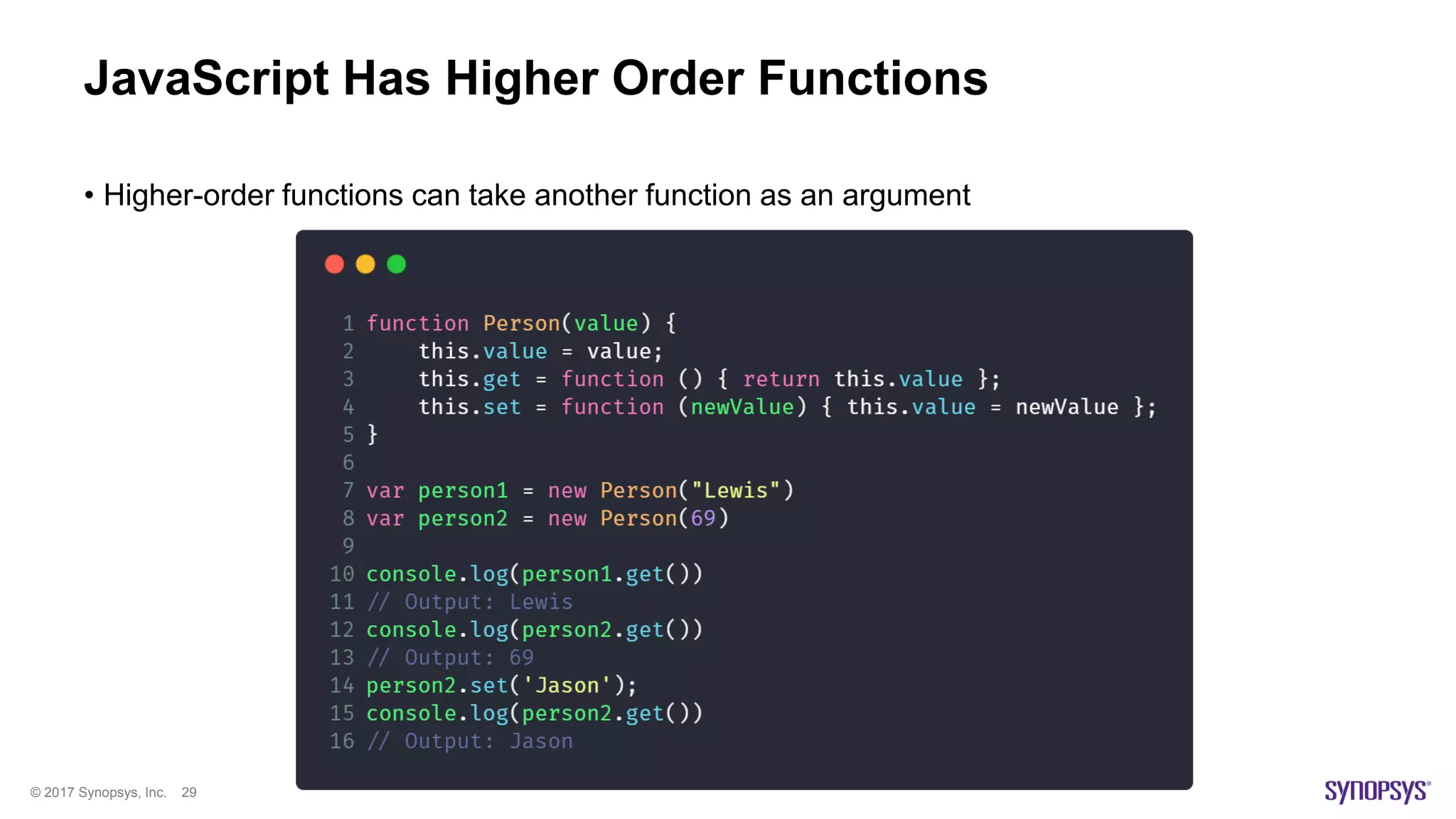
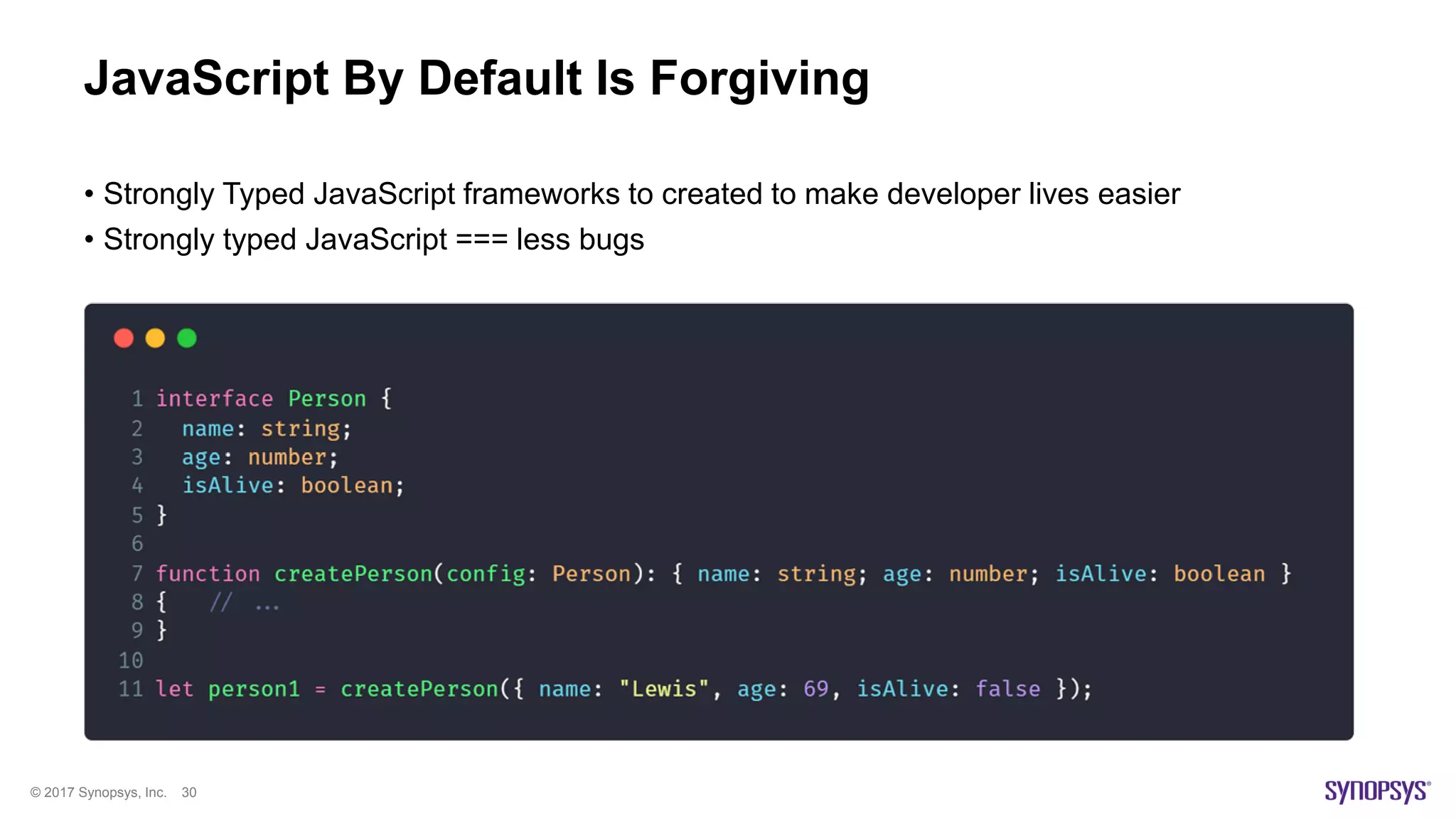
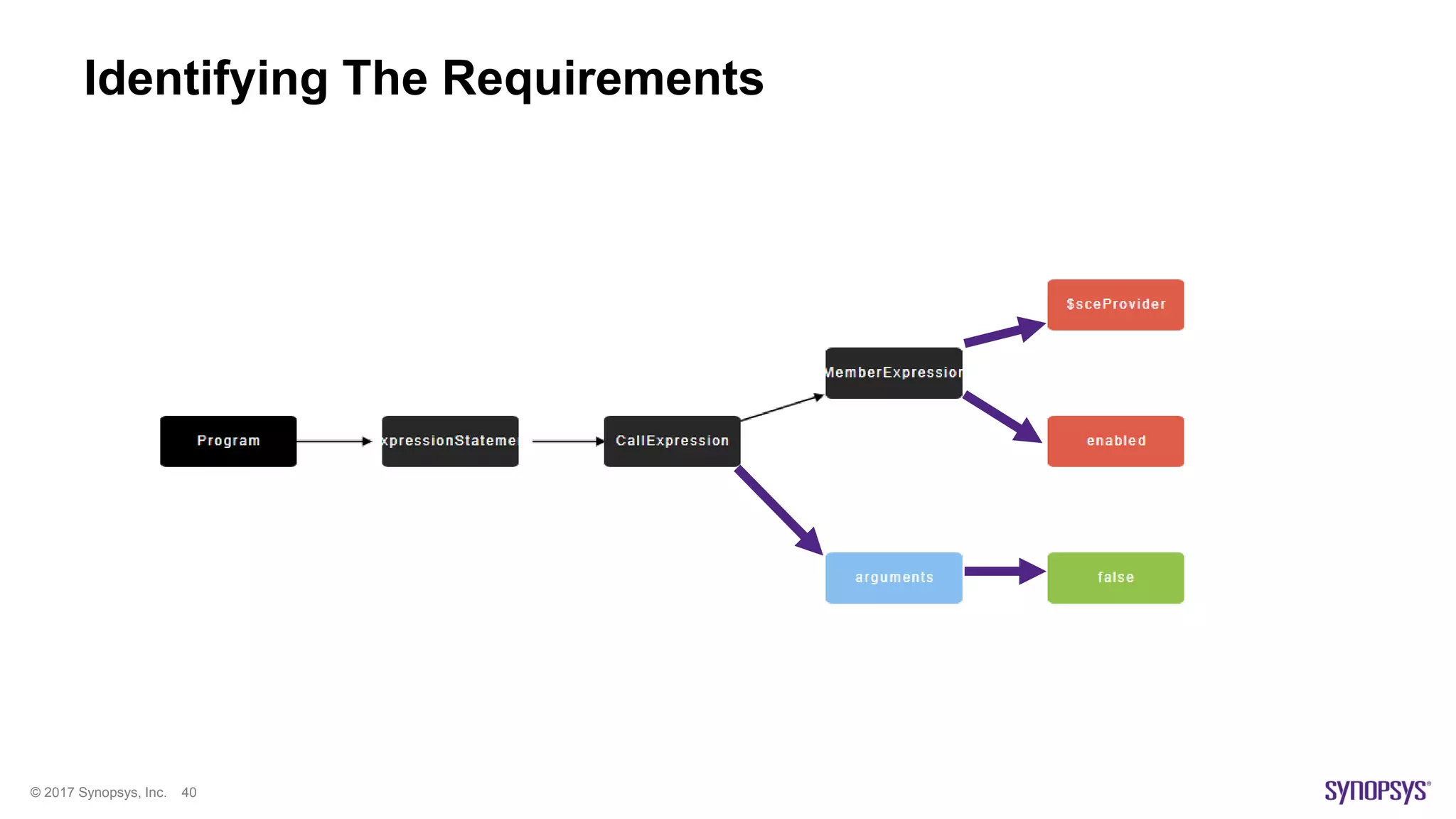
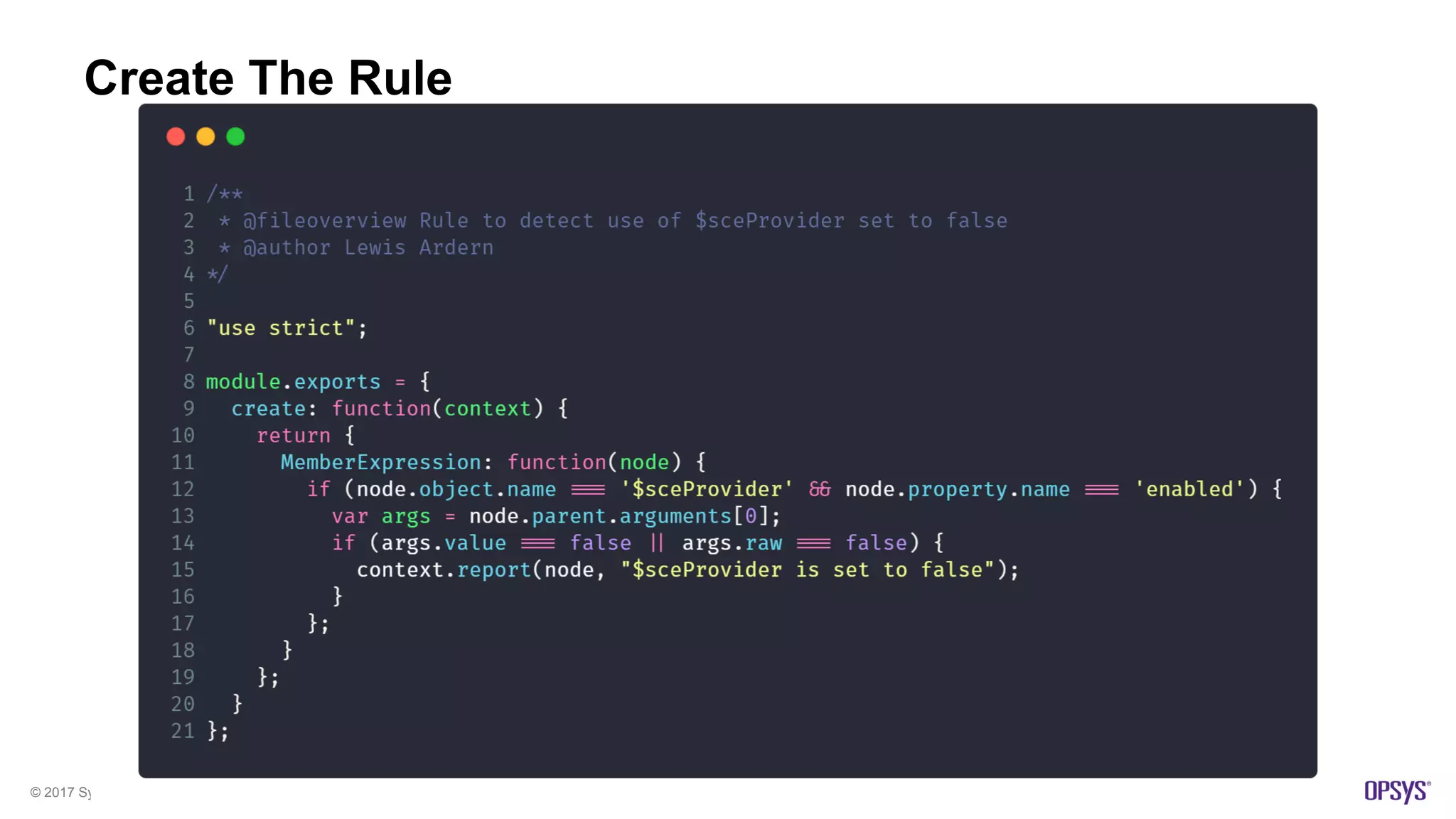
The document presents a high-level overview of JavaScript static analysis, discussing its evolution, security issues, and challenges associated with code reviews. It emphasizes the importance of understanding the nuances of JavaScript while suggesting various tools, like ESLint, for effective static code analysis and security assessments. The author also provides practical tips for developers and emphasizes customizing tools to enhance effectiveness in identifying vulnerabilities.






![© 2017 Synopsys, Inc. 12
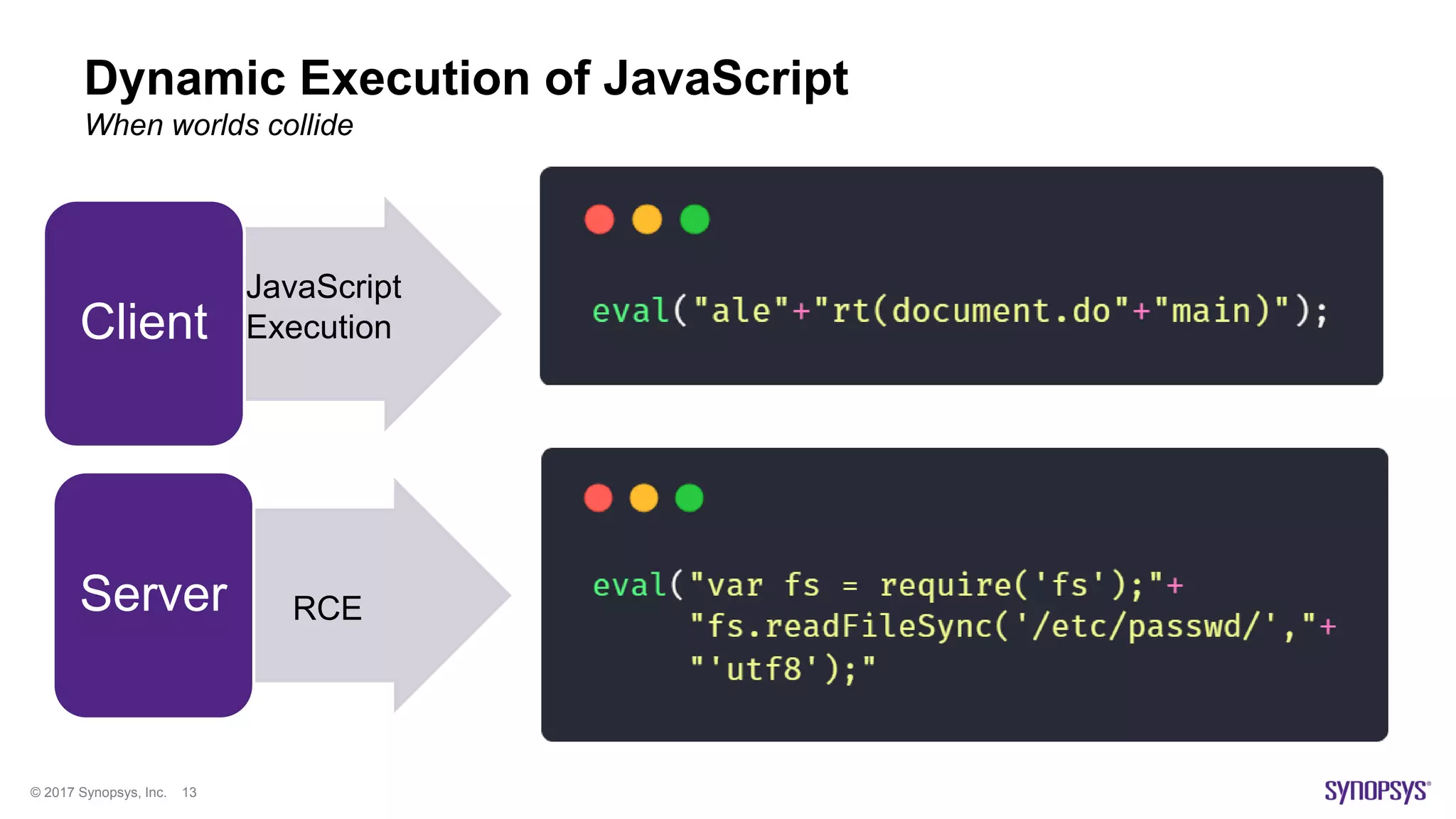
Dynamic Execution of JavaScript
Method Example
eval(expression) eval("ale"+"rt(document.co"+"okie)");
execScript(expression [, language]) window.execScript("alert(document.cookie)");
setTimeout(expression, milliseconds) setTimeout("alert('XSS')",3000);
setInterval(expression, milliseconds [,
language])
setInterval("alert('XSS')",3000);
JavaScript provides various ways to execute JavaScript dynamically
• DOM-XSS happens quite often through Dynamic Execution of JavaScript
• Avoid the use of user-input in execution queries such as eval](https://image.slidesharecdn.com/bsidesleeds-javascriptstaticcodeanalysis-180126164622/75/BSides-Leeds-Performing-JavaScript-Static-Analysis-12-2048.jpg)