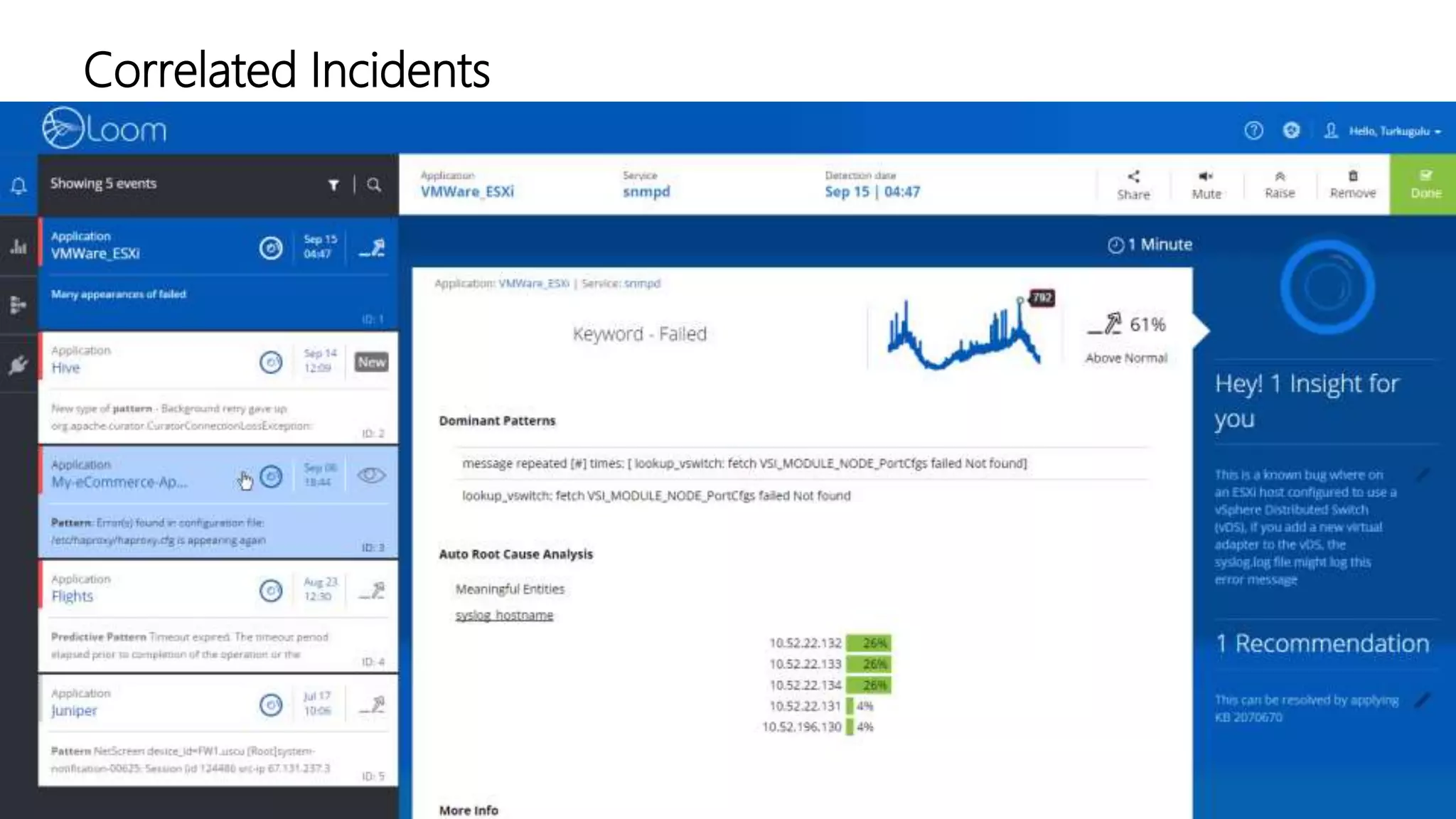
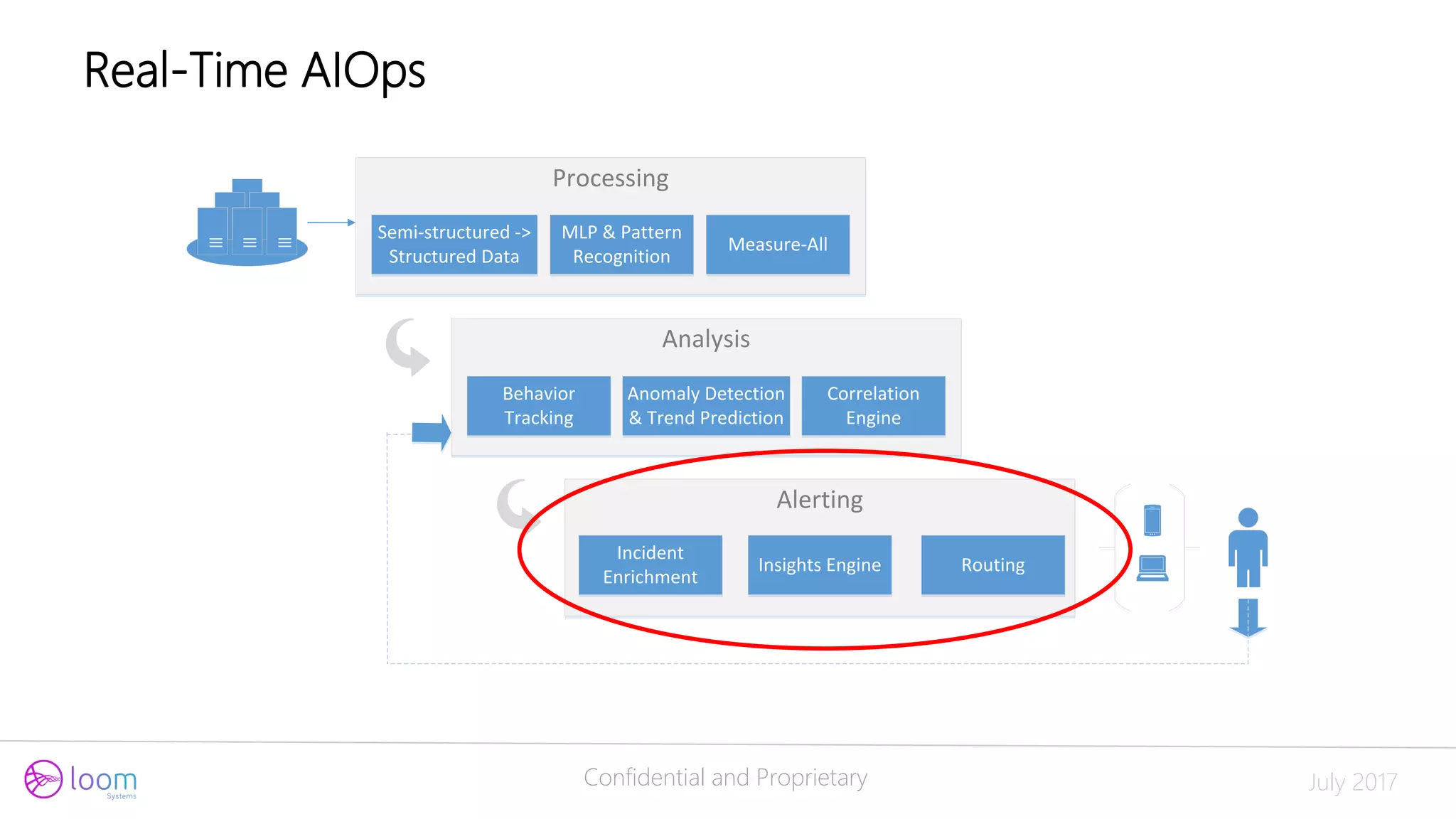
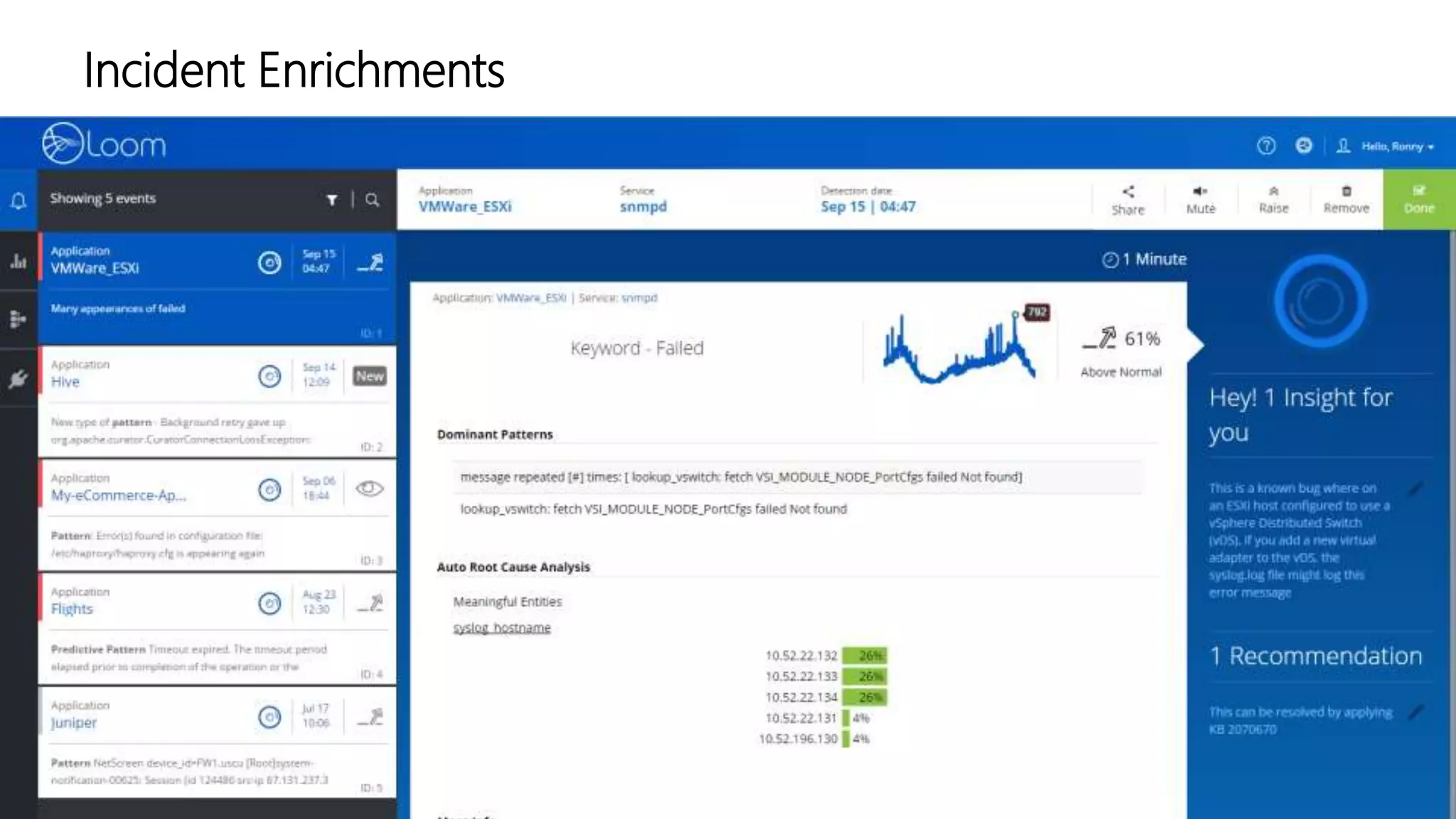
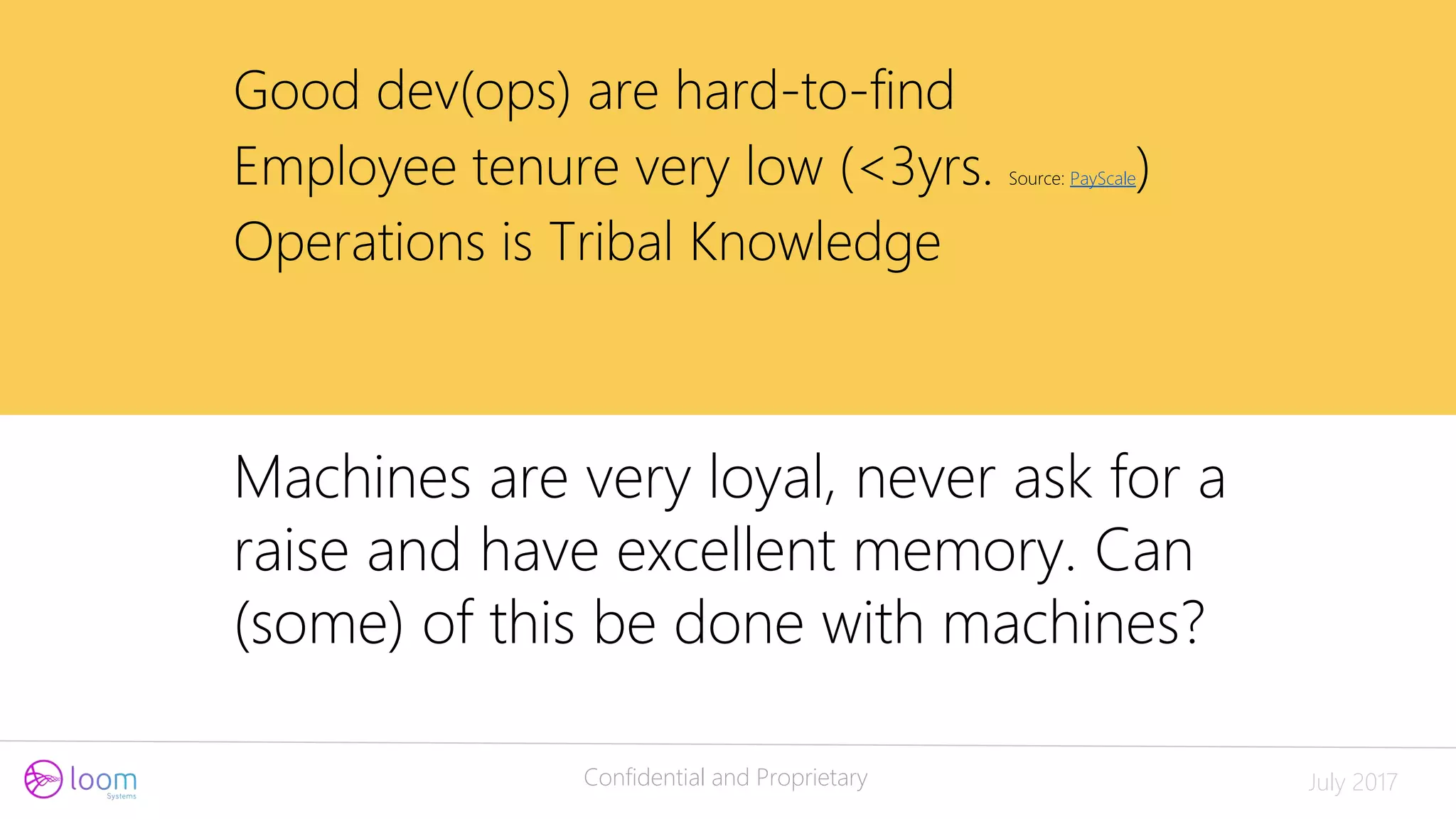
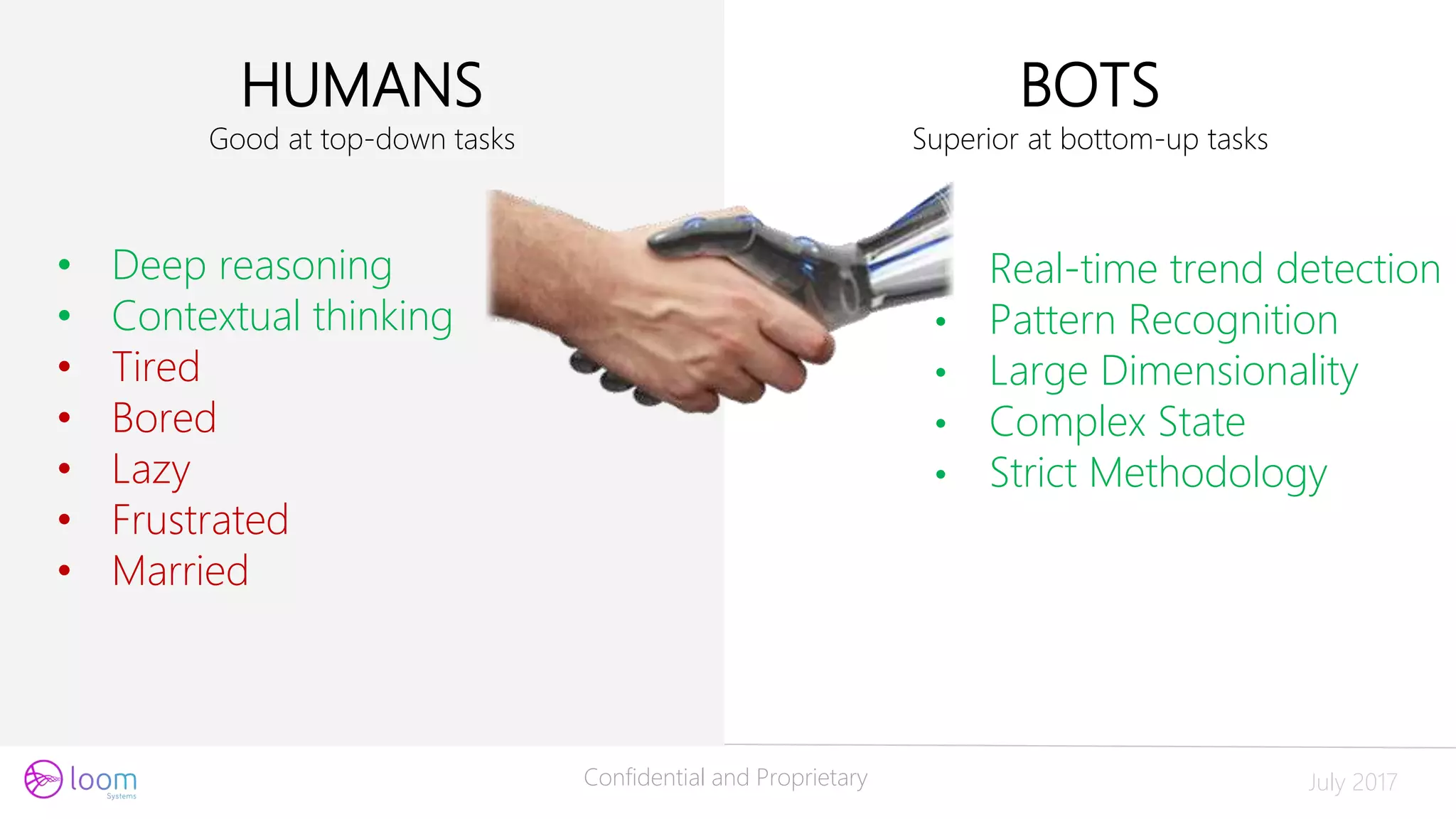
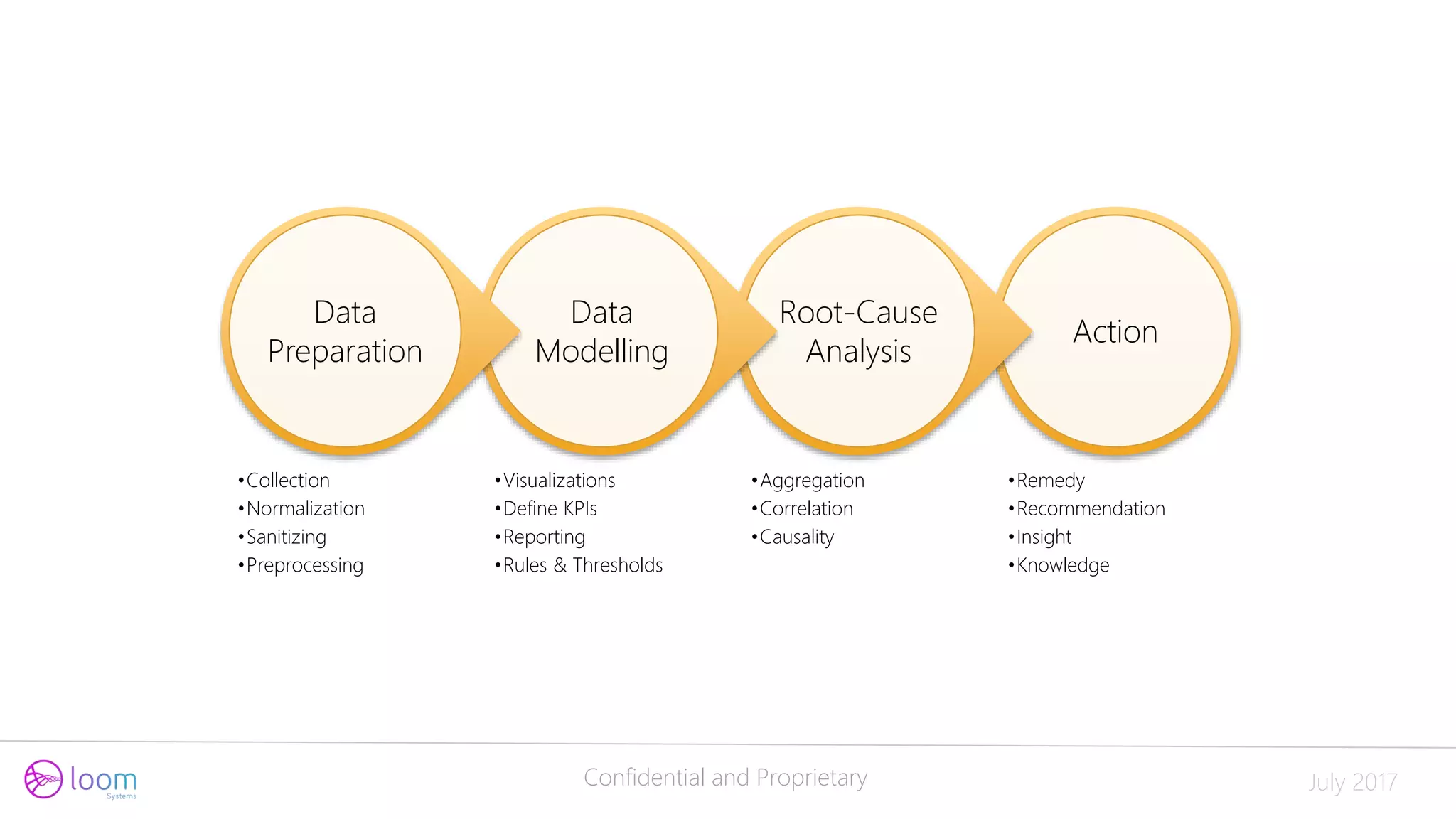
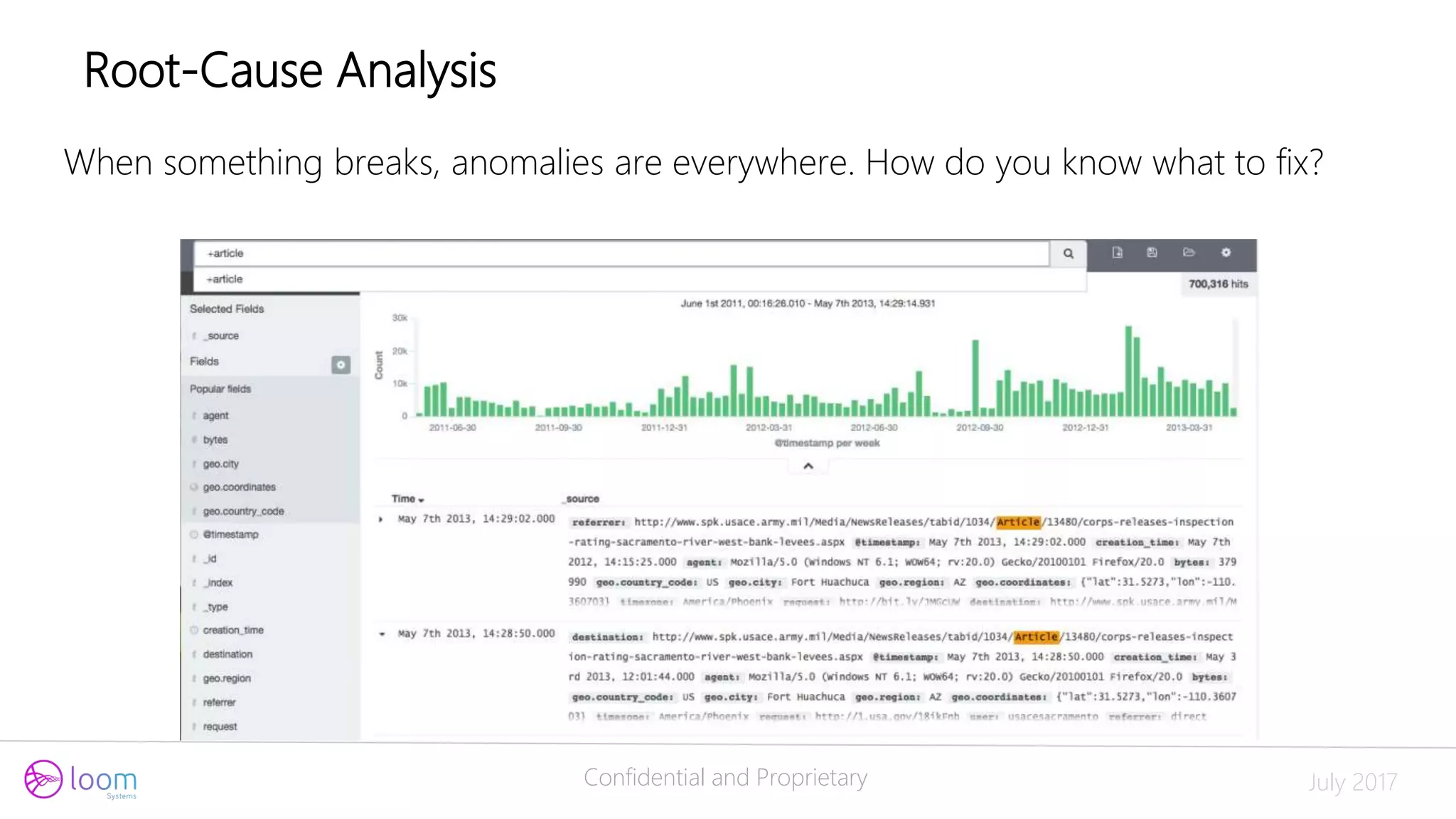
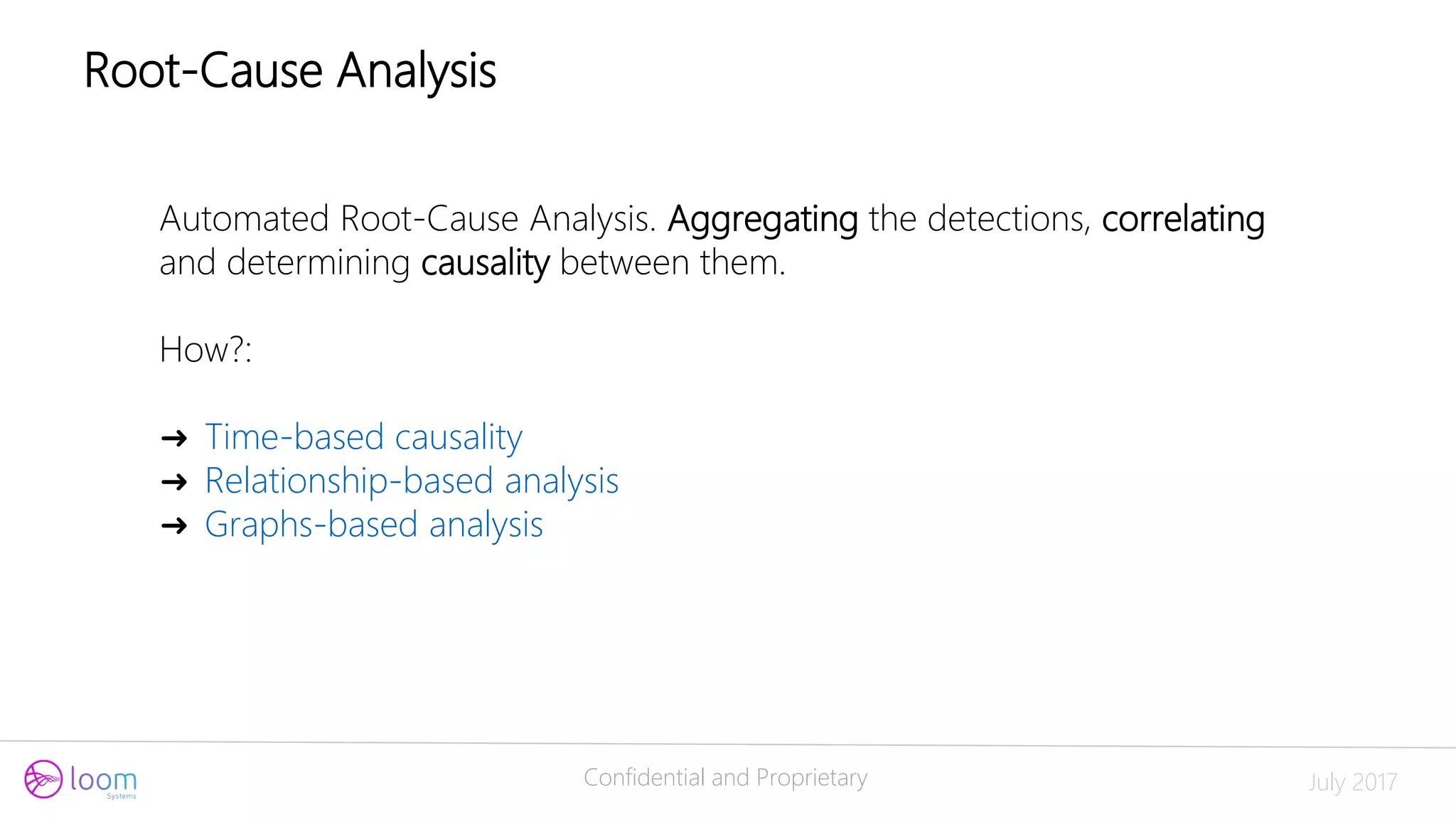
The document discusses the application of artificial intelligence in log analysis and IT operations management, focusing on Loom Systems' AI-driven approach to enhance real-time monitoring and root-cause analysis. It highlights the significance of automating data structuring, correlation, and contextual understanding to improve incident response and operational efficiency. The presentation emphasizes the potential of AI to alleviate current bottlenecks in IT operations and the need for skilled professionals in the field.




![Confidential and Proprietary July 2017
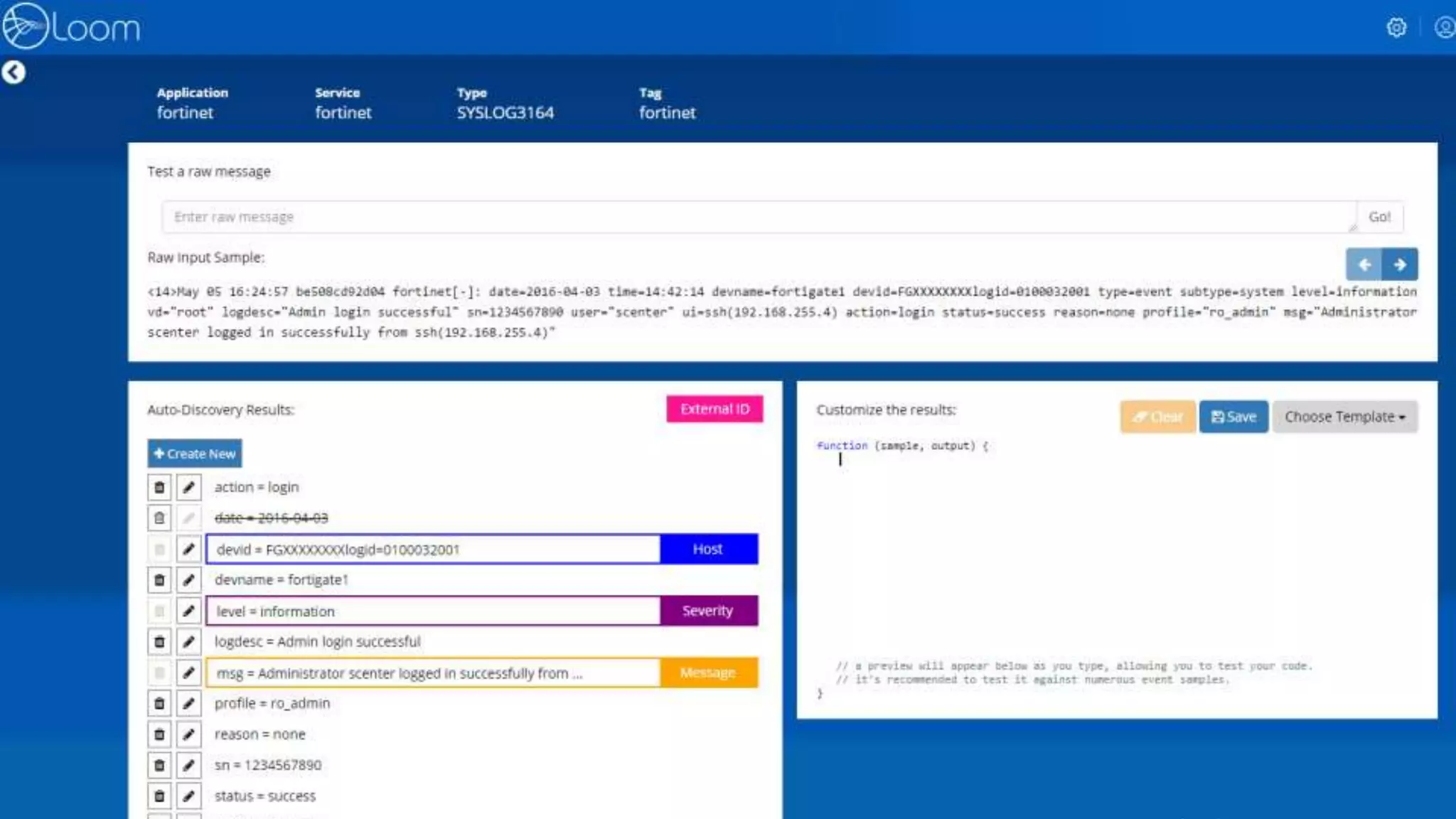
Sep 27 14:25:54 megatron sshd[7498]: WARN - Failed password for user ronny from 192.168.118.1 port 48278 ssh2
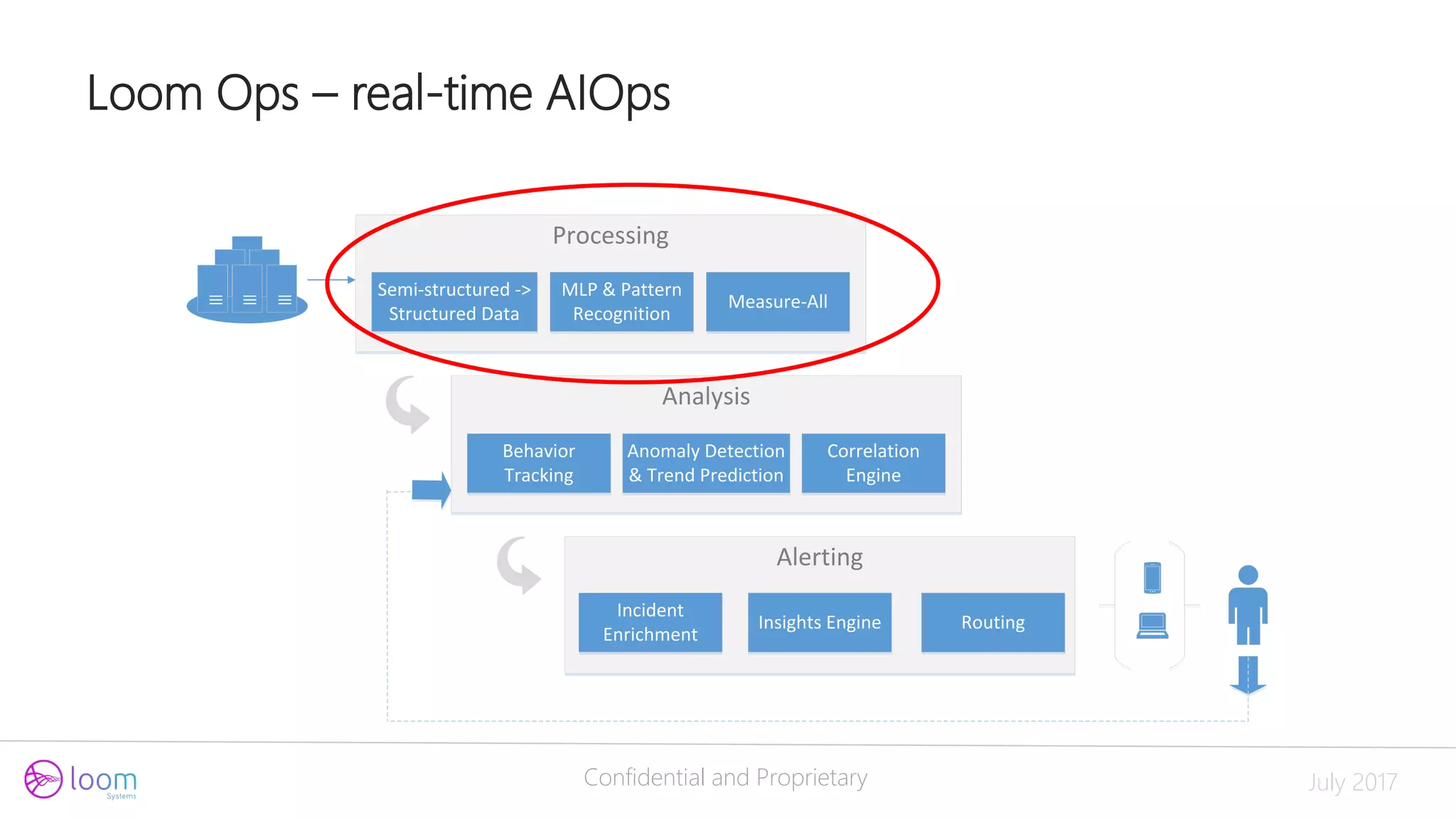
Processing
Generic context – rate of this pattern in the logs
Common Business Context –
➜ Contextual words (Warn, Failed)
➜ Common Entities (User, IP, ssh)
Proprietary Business Context –
➜ Server Name
Real-time Sturcturing, Clustering
Token & Entity Extraction and Classification
HistogrammegatronServer
MetersshdApplication
MeterronnyUser
Meter192.168.118.1source_IP
Random48278source_port
Failed password for user [user] from [source_IP] port [source_port] ssh2](https://image.slidesharecdn.com/doit-170717203538/75/Applying-ML-for-Log-Analysis-12-2048.jpg)

![Confidential and Proprietary July 2017
Sep 27 14:25:54 megatron sshd[7498]: WARN - Failed password for user ronny from 192.168.118.1 port…
Sep 27 14:25:54 megatron sshd[7498]: WARN - Failed password for user ronny from 192.168.118.1 port…
Sep 27 14:25:54 megatron sshd[7498]: WARN - Failed password for user ronny from 192.168.118.1 port…
Sep 27 14:25:55 megatron sshd[7498]: WARN - Failed password for user ronny from 192.168.118.1 port…
Sep 27 14:25:55 megatron sshd[7498]: WARN - Failed password for user ronny from 192.168.118.1 port…
Sep 27 14:25:55 megatron sshd[7498]: WARN - Failed password for user ronny from 192.168.118.1 port…
Sep 27 14:25:55 megatron sshd[7498]: WARN - Failed password for user ronny from 192.168.118.1 port…
Sep 27 14:25:56 megatron sshd[7498]: WARN - Failed password for user ronny from 192.168.118.1 port…
Sep 27 14:25:56 megatron sshd[7498]: WARN - Failed password for user ronny from 192.168.118.1 port…
Sep 27 14:25:56 megatron sshd[7498]: WARN - Failed password for user ronny from 192.168.118.1 port…
Sep 27 14:25:56 megatron sshd[7498]: WARN - Failed password for user ronny from 192.168.118.1 port…
Sep 27 14:25:56 megatron sshd[7498]: WARN - Failed password for user ronny from 192.168.118.1 port…
Sep 27 14:25:57 megatron sshd[7498]: WARN - Failed password for user ronny from 192.168.118.1 port…
Sep 27 14:25:54 megatron sshd[7498]: WARN - Failed password for user ronny from 192.168.118.16 port…
Sep 27 14:25:54 megatron sshd[7498]: WARN - Failed password for user dror from 192.168.118.4 port…
Sep 27 14:25:54 megatron sshd[7498]: WARN - Failed password for user john from 192.168.118.14 port…
Sep 27 14:25:55 megatron sshd[7498]: WARN - Failed password for user dan from 192.168.118.121 port…
Sep 27 14:25:55 megatron sshd[7498]: WARN - Failed password for user gab from 192.168.118.51 port…
Sep 27 14:25:55 megatron sshd[7498]: WARN - Failed password for user anna from 192.168.118.66 port…
Sep 27 14:25:55 megatron sshd[7498]: WARN - Failed password for user dan from 192.168.118.123 port…
Sep 27 14:25:56 megatron sshd[7498]: WARN - Failed password for user jim from 192.168.118.133 port…
Sep 27 14:25:56 megatron sshd[7498]: WARN - Failed password for user nate from 192.168.118.201 port…
Sep 27 14:25:56 megatron sshd[7498]: WARN - Failed password for user stan from 192.168.118.194 port…
Sep 27 14:25:56 megatron sshd[7498]: WARN - Failed password for user paul from 192.168.118.144 port…
Sep 27 14:25:56 megatron sshd[7498]: WARN - Failed password for user avi from 192.168.118.81 port…
Sep 27 14:25:57 megatron sshd[7498]: WARN - Failed password for user stas from 192.168.118.54 port…
ronny is mentioned more than normal in the context of ssh failures
The context of ssh failures is mentioned more than normal
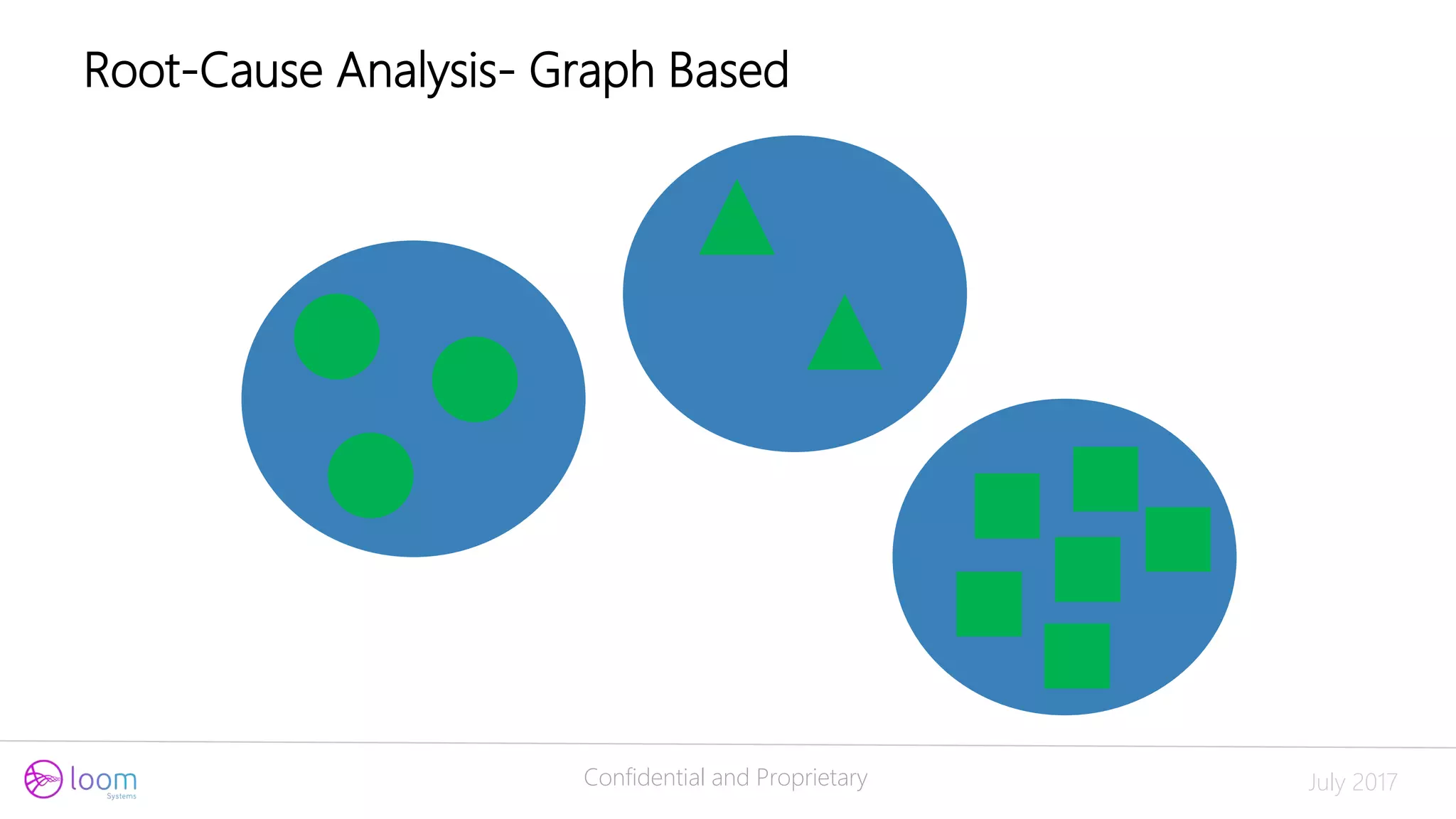
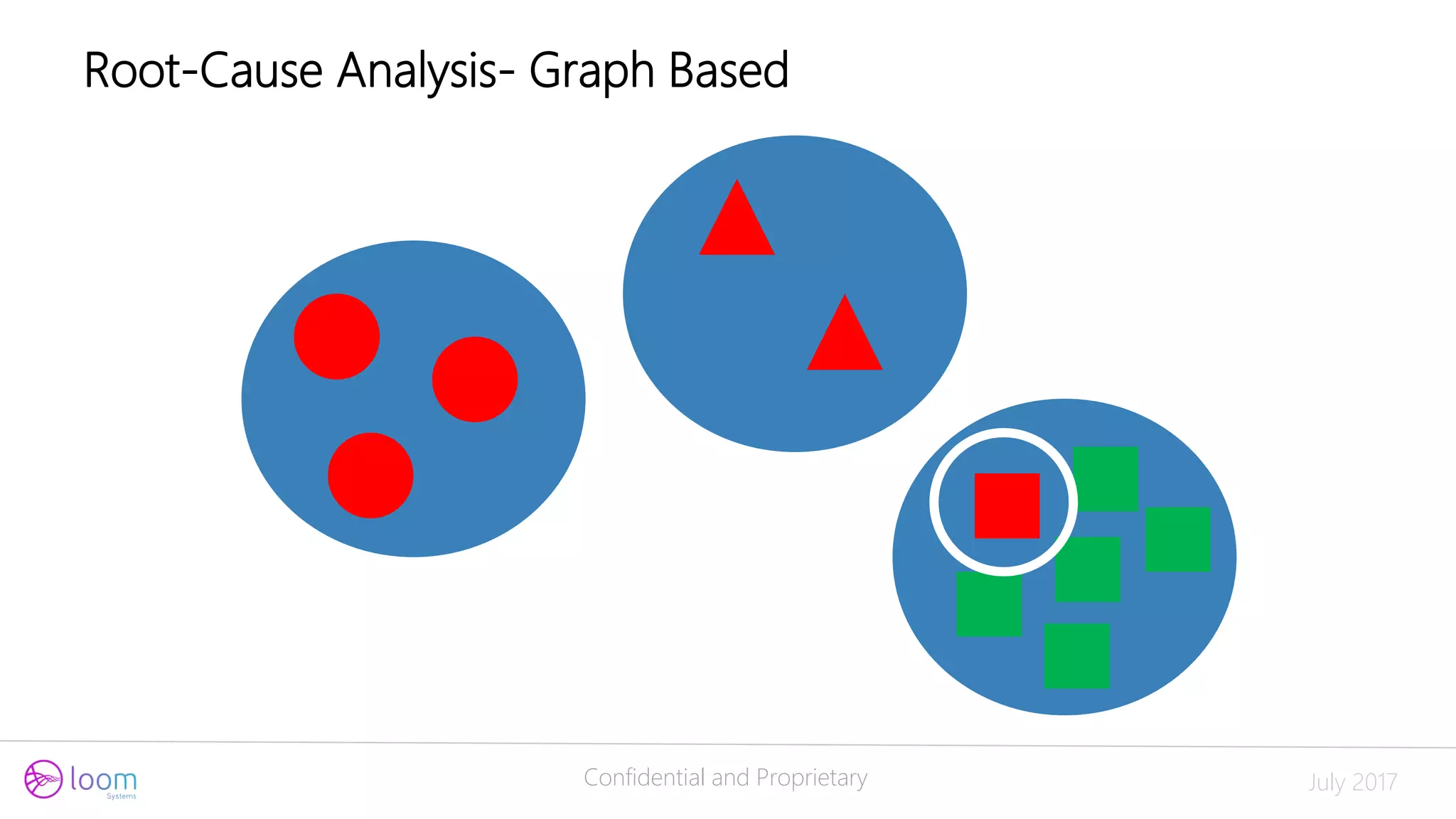
Root-Cause Analysis – Relationship Based](https://image.slidesharecdn.com/doit-170717203538/75/Applying-ML-for-Log-Analysis-20-2048.jpg)