In this article
SSPM Tools: Key Features and 8 Solutions to Know in 2025
What Are SaaS Security Posture Management (SSPM) Tools?
SaaS Security Posture Management (SSPM) tools help organizations manage and secure their SaaS applications. As organizations increasingly rely on SaaS platforms for critical operations, maintaining a strong security posture across these applications becomes crucial.
SSPM tools provide visibility, control, and protection by continuously monitoring SaaS environments for configuration issues, security risks, and compliance gaps. The primary goal of SSPM tools is to ensure SaaS applications are configured in line with security best practices, minimizing vulnerabilities and preventing potential breaches.
These tools automate the detection of misconfigurations, monitor user activity, enforce access controls, and identify risks across interconnected SaaS platforms. By offering a unified view of SaaS security, SSPM solutions help organizations protect sensitive data, maintain regulatory compliance, and improve overall security resilience.
Core Features of SSPM Tools
SSPM tools typically provide the following features to improve the security and management of SaaS applications.
Configuration Management
Configuration management ensures SaaS applications are configured securely and correctly according to predetermined policies. By continuously assessing configuration settings, SSPM tools can detect deviations and prevent potential security breaches or data loss events. This proactive approach prevents misconfigurations that could lead to unauthorized access.
Threat Detection and Activity Monitoring
Threat detection and activity monitoring capabilities allow organizations to identify abnormal activities and potential threats within their SaaS ecosystems. By analyzing user behaviors, access patterns, and data flows, SSPM tools can detect anomalies indicative of security breaches. This continuous monitoring ensures timely threat identification and response.
Identity and Access Management
Identity and access management (IAM) within SSPM ensures that users have appropriate access levels to SaaS applications. It involves managing credentials, permissions, and user provisioning to protect sensitive resources. By enforcing strict access controls, SSPM minimizes the risk of unauthorized access or data breaches, ensuring that users can only interact with resources required for their roles.
SaaS-to-SaaS Application Management
SaaS-to-SaaS application management focuses on overseeing interconnections between different SaaS applications. It ensures that data exchanges between these applications are secure and compliant with organizational policies. Enterprises increasingly integrate their software landscapes for smoother information flow, making cross-application oversight necessary to prevent unauthorized data sharing.
Compliance and Governance
Compliance and governance features ensure organization-wide adherence to legal and operational standards. SSPM tools provide governance frameworks, enabling organizations to structure their SaaS environments for compliance with industry regulations. This includes generating audit trails and automating compliance checks to reduce the risk of penalties and reputational damage.
Related content: Read our guide to SaaS security
Notable SSPM Tools
1. Cynet
The Cynet All-In-One cybersecurity platform automatically identifies, prioritizes and fixes security risks across leading SaaS applications. Using a simple dashboard, security administrators can immediately identify and prioritize SaaS security posture issues.
For each SaaS environment, you can quickly view the types of risk identified, the severity of each, and details about each misconfiguration, including the related compliance standards. Historical views allow administrators to identify and analyze persistent areas of concern to help avoid future compliance violations.
Key features include:
- Automated risk identification: Scans SaaS applications to detect misconfigurations, compliance gaps, and security risks. Automatically prioritizes these risks based on severity and provides actionable recommendations for remediation.
- Dynamic compliance management: Aligns security configurations with various compliance standards such as GDPR, HIPAA, and SOC 2, offering real-time updates on compliance status.
- Historical analysis: Tracks historical security issues and risk patterns, allowing organizations to analyze persistent vulnerabilities and make informed adjustments to policies and configurations.
- Unified dashboard: Provides a single interface for managing SaaS security posture, displaying risks, compliance scores, and actionable insights in an intuitive format.
- Integration and scalability: Supports seamless integration with popular SaaS platforms, ensuring scalability across diverse environments.
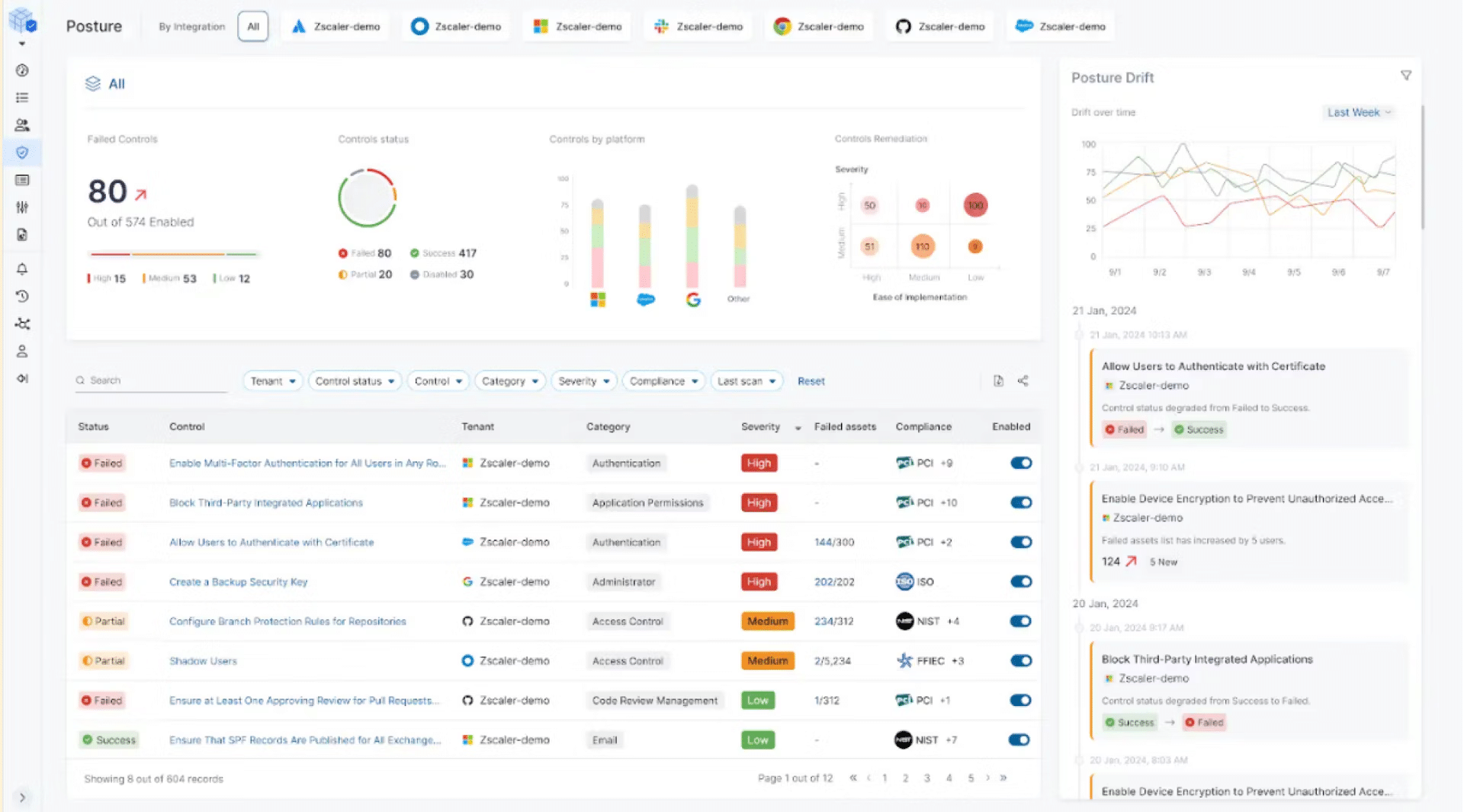
2. Zscaler
Zscaler Advanced SaaS Security Posture Management is a unified solution to provide protection for SaaS applications and data. By integrating SSPM with its cloud access security broker (CASB), Zscaler enables organizations to secure their SaaS platforms holistically.
Key features include:
- Integrated CASB for SaaS data security: Offers visibility and control over data movement within SaaS apps. Enforces granular policies to prevent risky sharing and secure sensitive information.
- Continuous posture monitoring and hardening: Detects and resolves misconfigurations across SaaS platforms caused by human errors or policy drift. Provides prioritized risk assessments for effective remediation.
- SaaS shadow IT governance: Conducts deep discovery of third-party integrations and shadow IT. Identifies and audits unauthorized app add-ons to reduce integration risks and protect sensitive data.
- Zero trust identity management: Implements least-privileged access policies, ensuring that only authorized users can access SaaS apps and data.
- Auto-remediation and guidance: Strengthens security posture by automating remediation of configuration gaps. Offers guided recommendations to address identified risks.
Source: Zscaler
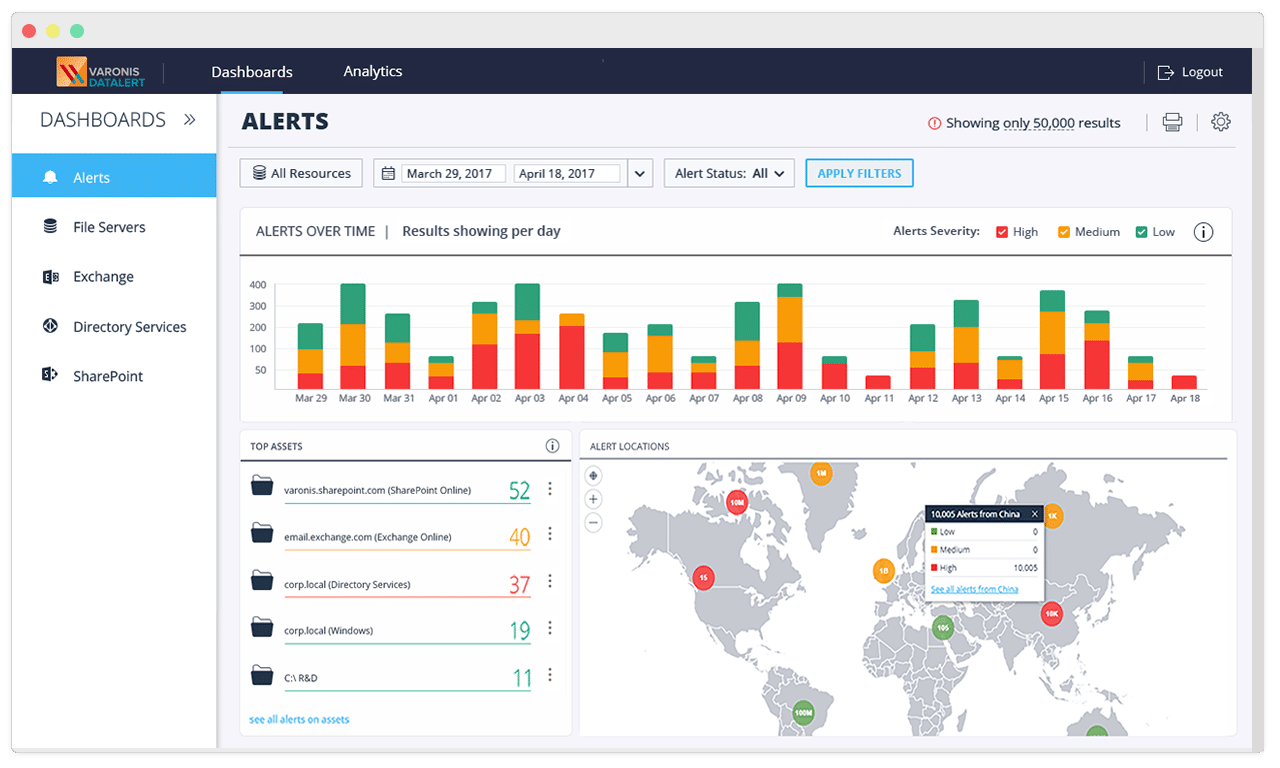
3. Varonis
Varonis takes a data-first approach, combining SSPM and Data Security Posture Management (DSPM) to secure SaaS applications and the sensitive data they contain. By offering continuous monitoring, automation, and insights into data exposure, it reduces risk across SaaS environments while simplifying remediation and compliance management.
Key features include:
- Misconfiguration detection: Continuously scans SaaS platforms for misconfigurations, identifying risks like missing MFA or public access permissions. Alerts are prioritized by severity, with step-by-step instructions or automated remediation to resolve issues.
- Data access control: Audits and normalizes permissions across SaaS platforms, providing a clear view of who can access sensitive data and what actions they can perform.
- User activity auditing: Aggregates activity data such as privilege escalations, group changes, and authentication events.
- Sensitive data discovery and classification: Automatically identifies and classifies sensitive data like PII and financial information. Presents findings in a hierarchical file tree, allowing easy sorting and prioritization of risk reduction for critical assets.
- Automated remediation: Fixes flagged issues—such as misconfigurations or access vulnerabilities—with a single click or fully automated workflows.
Source: Varonis
4. Adaptive Shield
Adaptive Shield is a SaaS Security Posture Management solution that helps organizations continuously analyze and secure their SaaS environments. It integrates with a range of applications, providing capabilities to detect and address configuration risks, monitor user activities, and improve overall SaaS security posture.
Key features include:
- Breadth and depth analysis: Conducts continuous, in-depth assessments of the SaaS stack to identify security gaps and maintain compliance.
- Extensive integration: Supports over 150 SaaS applications, allowing organizations to contextualize risks and prioritize remediation efforts based on severity and impact.
- Security checks and alerts: Offers alerts for configuration drifts or potential risks, integrating with change control processes for monitoring.
- Remediation assistance: Provides insights into security risks, including exposure levels and affected stakeholders. Features a “Fix Now” option to directly resolve issues or enable ticket sharing for collaborative resolution.
- User inventory management: Delivers an overview of user accounts across SaaS platforms, highlighting privileged roles, deactivated accounts, and failed security checks.
Source: Adaptive Shield
5. Netskope SSPM
Netskope SSPM continuously monitors and enforces security settings, policies, and best practices for SaaS applications. By leveraging integrations and visualization techniques, it helps organizations uncover hidden risks, address policy drifts, and maintain compliance with industry standards.
Key features include:
- Graph-powered engine: Offers detections and visualizations to analyze context across SaaS apps, exposing misconfigurations and hidden risks.
- Unified SaaS posture dashboard: Provides a centralized view of SaaS security posture, enabling security teams to quickly drill down into issues for triage and investigation.
- SaaS app inventory: Displays a view of all SaaS app instances, resources, and their security configurations, providing context for risk management.
- Predefined detection rules: Includes hundreds of out-of-the-box rules for popular applications like Salesforce, Microsoft Exchange, and SharePoint, enabling identification and remediation of misconfigurations.
- Third-party app risk levels: Continuously monitors OAuth-connected third-party apps and assigns risk scores, helping organizations block or control high-risk integrations.
Source: Netskope
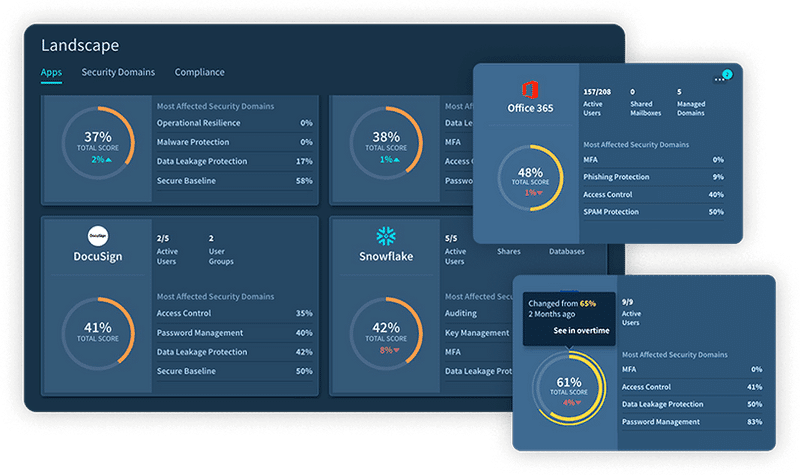
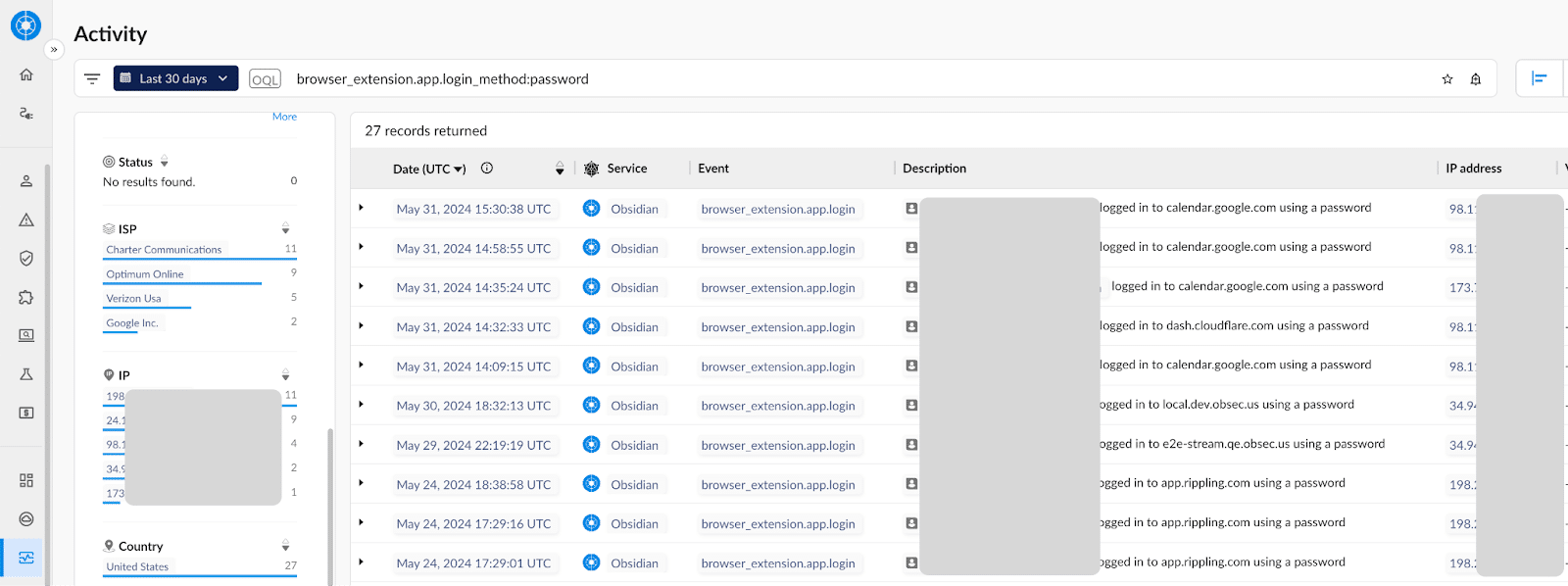
6. Obsidian SaaS Security
Obsidian SaaS Security helps eliminate risks across the SaaS attack surface. It provides visibility into SaaS inventory, strengthens app security posture, automates compliance management, and mitigates integration risks.
Key features include:
- SaaS inventory management: Identifies both sanctioned and unsanctioned SaaS applications, providing insights into users, login frequencies, user activities, authentication methods, and shared service accounts.
- App posture hardening: Enhances SaaS security by detecting privileged accounts without MFA, revoking dormant accounts, and controlling unnecessary access permissions.
- Integration risk management: Discovers all SaaS integrations and assigns risk scores by analyzing numerous risk factors. Monitors and manages unapproved, new, or inactive integrations to mitigate security vulnerabilities.
- Automated compliance management: Tracks compliance against external and custom frameworks, automating evidence collection to simplify audit preparation.
- Customizable controls and frameworks: Enables organizations to create, modify, and clone controls to build tailored compliance frameworks. Alerts provide actionable recommendations to address non-compliance issues promptly.
Source: Obsidian
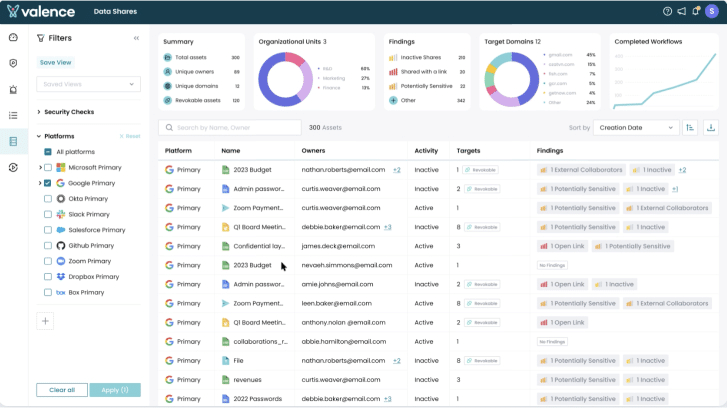
7. Valence
Valence offers an SSPM solution to address the complexities of SaaS environments. By providing centralized visibility, automated workflows, and actionable remediation, it enables organizations to secure their SaaS ecosystems, reduce risk exposure, and maintain compliance with industry standards.
Key features include:
- Central inventory and risk management: Provides a unified view of the SaaS environment, consolidating risks across applications and offering insights into misconfigurations, configuration drift, and data exposure.
- Automated configuration management: Continuously monitors SaaS configurations, detecting issues like missing MFA/SSO settings, inactive accounts, and risky SaaS-to-SaaS integrations. Alerts are paired with guided or automated remediation options.
- Compliance and auditing: Simplifies adherence to regulatory requirements and internal security policies with compliance reporting and automated checks.
- Data exposure analysis: Identifies and monitors data-sharing risks, helping organizations enforce security controls to prevent unauthorized access or exfiltration.
- SaaS integration oversight: Tracks SaaS-to-SaaS integrations to uncover and mitigate risks associated with unauthorized or insecure app connections.
Source: Valence
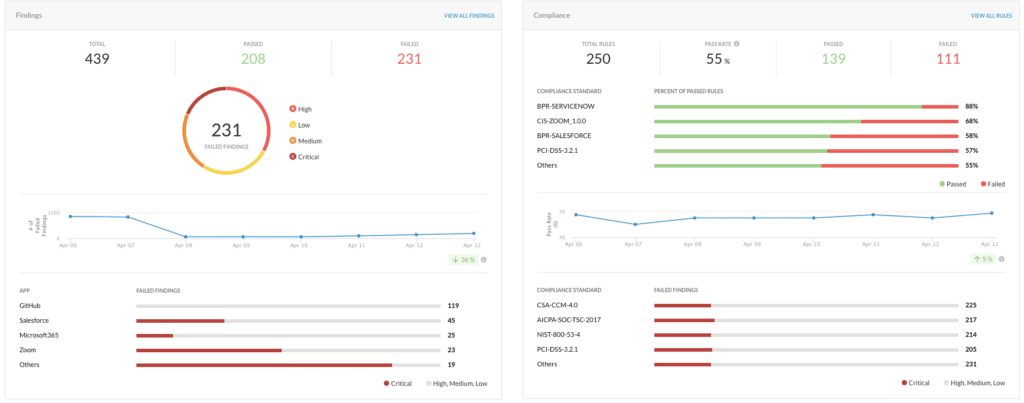
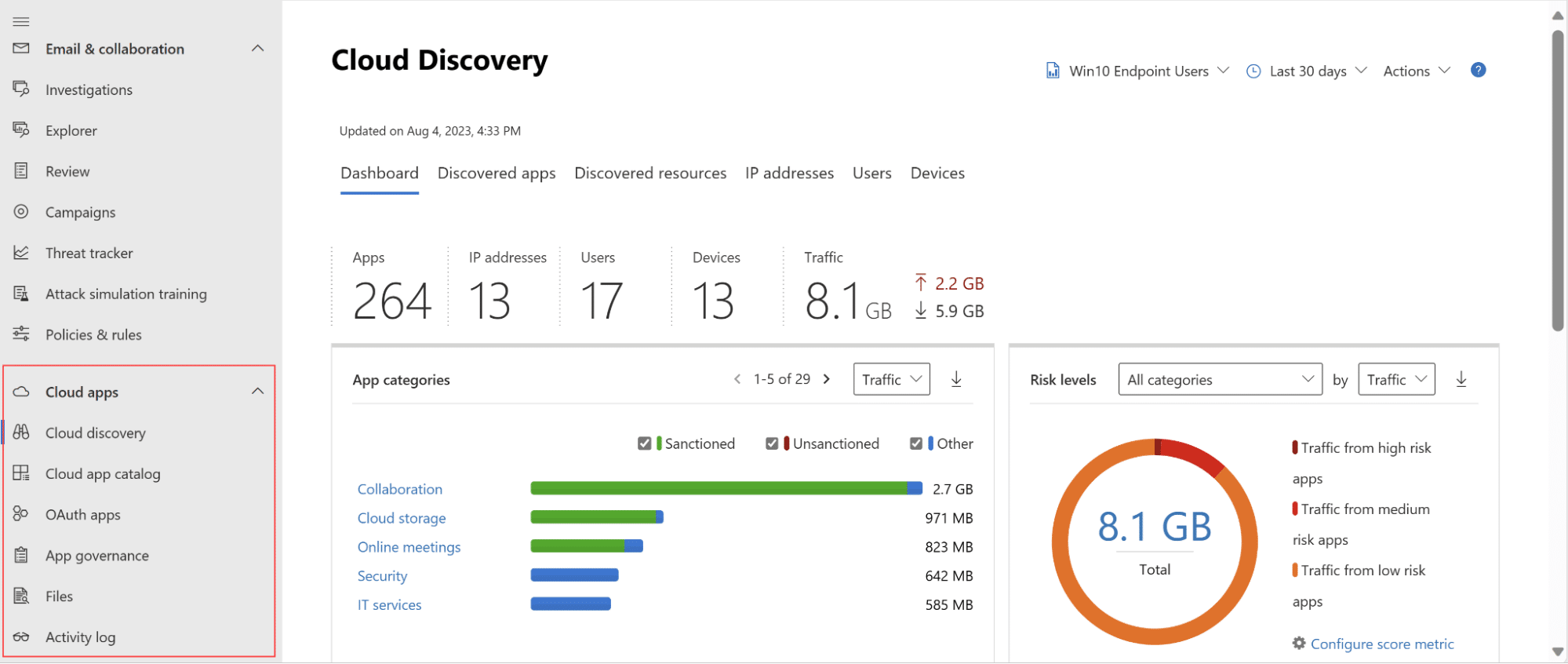
8. Microsoft Defender for Cloud Apps
Microsoft Defender for Cloud Apps integrates SaaS Security Posture Management capabilities into its broader security ecosystem to help organizations strengthen their SaaS security posture. By offering visibility into SaaS configurations, actionable recommendations, and centralized management, it enables organizations to identify risks and protect sensitive data.
Key features include:
- Security configuration assessments: Continuously evaluates the security posture of connected SaaS applications, providing actionable guidance to address risks and improve configurations.
- Microsoft security exposure management integration: Displays security recommendations and metrics from SaaS connectors, helping organizations prioritize remediation efforts. Recommendations are based on Microsoft benchmarks and updated automatically.
- Secure score recommendations: For environments where security exposure management is unavailable (e.g., US government clouds), Secure Score provides a consolidated view of SaaS security recommendations and remediation guidance.
- Customizable recommendations: Allows security teams to filter security recommendations by product or application instance.
- Step-by-step remediation guidance: Each recommendation includes a detailed implementation guide, helping security teams resolve issues.
Source: Microsoft
Conclusion
SSPM tools play a critical role in securing modern SaaS environments by providing continuous visibility, risk detection, and automated remediation capabilities. By addressing configuration issues, monitoring user activity, and ensuring compliance, these tools enable organizations to safeguard sensitive data and maintain a strong security posture across their SaaS ecosystems.
Related Posts
Looking for a powerful, cost effective XDR solution?
- Full-Featured XDR, EDR, and NGAV
- Anti-Ransomware & Threat Hunting
- 24×7 Managed Detection and Response