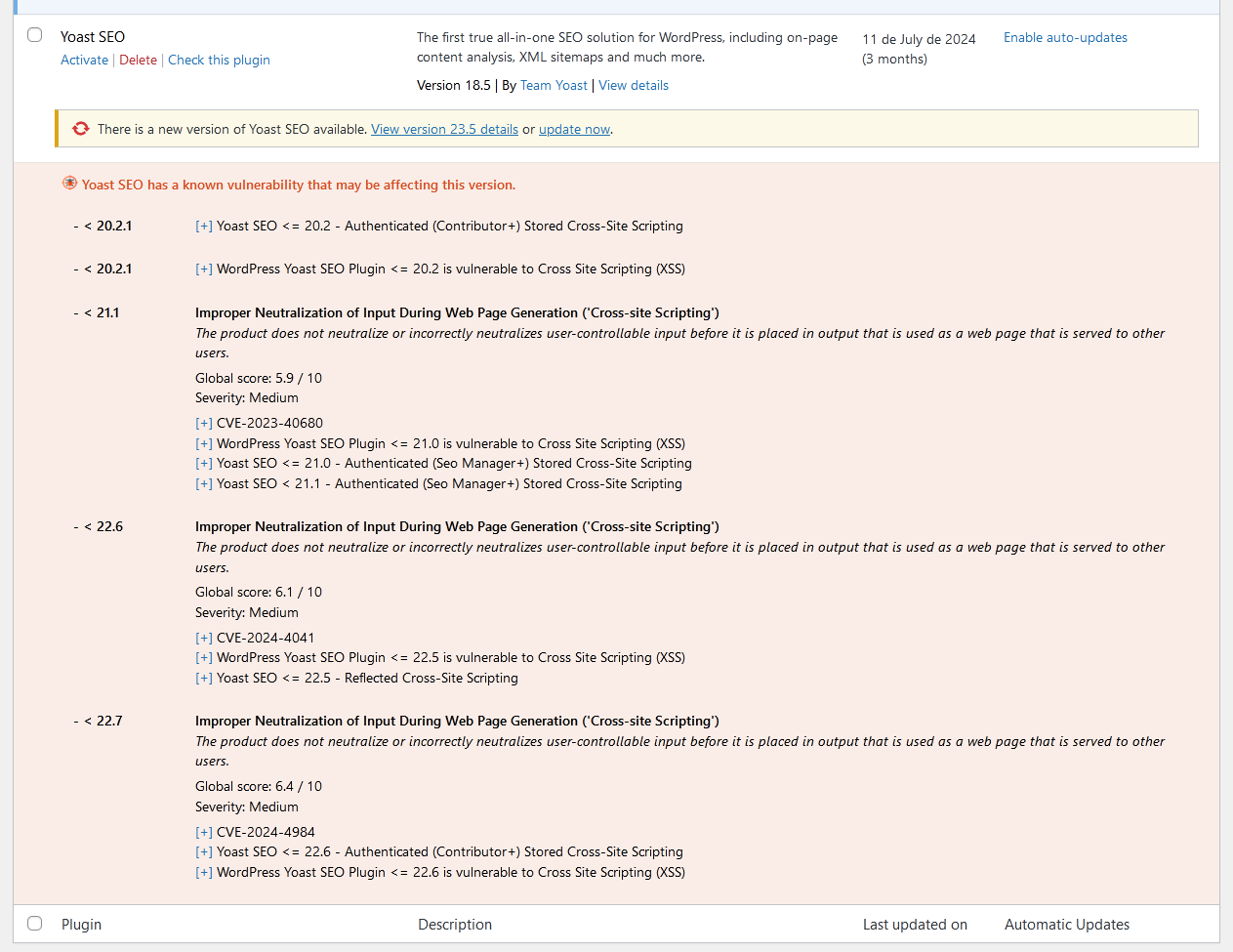
説明
This plugin integrates with the WPVulnerability API to provide real-time vulnerability assessments for your WordPress core, plugins, themes, PHP version, Apache HTTPD, nginx, MariaDB, MySQL, ImageMagick, curl, memcached, Redis, and SQLite.
It delivers detailed reports directly within your WordPress dashboard, helping you stay aware of potential security risks. Configure the plugin to send periodic notifications about your site’s security status, ensuring you remain informed without being overwhelmed. Designed for ease of use, it supports proactive security measures without storing or retrieving any personal data from your site.
データの信頼性
データベースが提供する情報は、サードパーティによってレビューされたさまざまな情報から取得したものです。情報については、いかなる種類の責任も負いません。自己責任で行動してください。
Using the plugin
WP-CLI
You can use the following WP-CLI commands to manage and check vulnerabilities:
- Core:
wp wpvulnerability core - Plugins:
wp wpvulnerability plugins - Themes:
wp wpvulnerability themes - PHP:
wp wpvulnerability php - Apache HTTPD:
wp wpvulnerability apache - nginx:
wp wpvulnerability nginx - MariaDB:
wp wpvulnerability mariadb - MySQL:
wp wpvulnerability mysql - ImageMagick:
wp wpvulnerability imagemagick - curl:
wp wpvulnerability curl - memcached:
wp wpvulnerability memcached - Redis:
wp wpvulnerability redis - SQLite:
wp wpvulnerability sqlite
To configure the plugin you can use:
- Hide component:
wp wpvulnerability config hide <component> [on|off] - Notification email:
wp wpvulnerability config email <emails>(comma separatted) - Notification period:
wp wpvulnerability config period <never|daily|weekly> - Log retention:
wp wpvulnerability config log-retention <0|1|7|14|28>(in days) - Cache duration:
wp wpvulnerability config cache <1|6|12|24>(in hours)
All commands support the --format option to specify the output format:
--format=table: Displays the results in a table format (default).--format=json: Displays the results in JSON format.
Need help?
wp wpvulnerability --help: Displays help information for WPVulnerability commands.wp wpvulnerability [command] --help: Displays help information for a WPVulnerability command.
REST API
The WPVulnerability plugin provides several REST API endpoints to fetch vulnerability information for different components of your WordPress site.
- Core:
/wpvulnerability/v1/core - Plugins:
/wpvulnerability/v1/plugins - Themes:
/wpvulnerability/v1/themes - PHP:
/wpvulnerability/v1/php - Apache HTTPD:
/wpvulnerability/v1/apache - nginx:
/wpvulnerability/v1/nginx - MariaDB:
/wpvulnerability/v1/mariadb - MySQL:
/wpvulnerability/v1/mysql - ImageMagick:
/wpvulnerability/v1/imagemagick - curl:
/wpvulnerability/v1/curl - memcached:
/wpvulnerability/v1/memcached - Redis:
/wpvulnerability/v1/redis - SQLite:
/wpvulnerability/v1/sqlite
The WPVulnerability REST API uses Application Passwords for authentication. You need to include a valid Application Password in the Authorization header of your requests.
Example Request with Authentication
curl -X GET https://example.com/wp-json/wpvulnerability/v1/plugins -u username:application_password
Replace username with your WordPress username and application_password with your Application Password.
Extra Configurations
“From:” mail (since: 3.2.2)
If, for some reason, you need the emails sent by the plugin to have a From different from the site administrator, you can change it from the wp-config.php by adding a constant:
define( 'WPVULNERABILITY_MAIL', 'sender@example.com' );
If the constant is active, it will be visible in the configuration screen.
Force hiding checks (since: 4.1.0)
If you want to always hide a specific component, you can define a constant in wp-config.php. When set to true, the option will be checked automatically in the settings screen and the related analysis will be skipped.
Example:
define( 'WPVULNERABILITY_HIDE_APACHE', true );
Available constants: WPVULNERABILITY_HIDE_CORE, WPVULNERABILITY_HIDE_PLUGINS, WPVULNERABILITY_HIDE_THEMES, WPVULNERABILITY_HIDE_PHP, WPVULNERABILITY_HIDE_APACHE, WPVULNERABILITY_HIDE_NGINX, WPVULNERABILITY_HIDE_MARIADB, WPVULNERABILITY_HIDE_MYSQL, WPVULNERABILITY_HIDE_IMAGEMAGICK, WPVULNERABILITY_HIDE_CURL, WPVULNERABILITY_HIDE_MEMCACHED, WPVULNERABILITY_HIDE_REDIS, WPVULNERABILITY_HIDE_SQLITE.
Cache duration (since: 4.1.0)
By default, data from the API is cached for 12 hours.
define( 'WPVULNERABILITY_CACHE_HOURS', 24 );
To change this, define WPVULNERABILITY_CACHE_HOURS in wp-config.php with one of 1, 6, 12 or 24. This value overrides the setting screen and WP-CLI command.
Log rotation (since: 4.2.0)
WPVulnerability stores the most recent API responses so you can review recent calls from the new log tab. Define WPVULNERABILITY_LOG_RETENTION_DAYS in wp-config.php to control how many days of entries are preserved. Supported values are 0, 1, 7, 14 or 28; using 0 disables logging entirely.
define( 'WPVULNERABILITY_LOG_RETENTION_DAYS', 14 );
When the constant is present its value is enforced in the settings UI and through WP-CLI, ensuring consistent log rotation across environments.
Compatibility
- WordPress: 4.7 – 6.9
- PHP: 5.6 – 8.4
- WP-CLI: 2.3.0 – 2.11.0
Security
This plugin adheres to the following security measures and review protocols for each version:
- WordPress Plugin Handbook
- WordPress Plugin Security
- WordPress APIs Security
- WordPress Coding Standards
- Plugin Check (PCP)
- SonarCloud Code Review
Privacy
- このプラグインおよび WordPress Vulnerability Database API は、サイト、ユーザー、プラグイン、テーマ、コンテンツに関する情報を収集しません。
Vulnerabilities
- No vulnerabilities have been published up to version 4.2.0.
Found a security vulnerability? Please report it to us privately at the WPVulnerability GitHub repository.
Contributors
このプラグインは、WPVulnerability GitHub リポジトリで貢献することができます。
インストール
自動ダウンロード
WordPress のプラグインセクションにアクセスし、[wpvulnerability] を検索して、プラグインをダウンロードしインストールしてください。
手動ダウンロード
ZIP を解凍し、/wp-content/plugins/wpvulnerability/ ディレクトリにアップロードします。 アップロードするとプラグインリストに表示されます。
FAQ
-
脆弱性情報はどこから取得していますか ?
-
WPVulnerability.com API を元にしています。この API に表示される脆弱性は、CVEs などのさまざまなソースから取得しています。
-
サイトのデータはどこかに送信されますか ?
-
いいえ、送信されません。ユーザーのプライバシーは私たちにとって非常に重要です。私たちはユーザーのデータを商品化しません。
-
どのような脆弱性を見つけますか ?
-
Vulnerabilities in WordPress Core, Plugins, Themes, PHP, Apache HTTPD, nginx, MariaDB, MySQL, ImageMagick, curl, memcached, Redis, and SQLite are documented.
-
サイトに脆弱性がある場合、どうすればいいのでしょうか ?
-
First of all, peace of mind. Investigate what the vulnerability is and, above all, check that you have the latest version of the compromised element. We actively recommend that you keep all your WordPress and its plugins up to date. Contact your hosting provider to patch non-WordPress vulnerabilities (like web server, databases, and other software).
評価
貢献者と開発者
WPVulnerability はオープンソースソフトウェアです。以下の人々がこのプラグインに貢献しています。
貢献者変更履歴
[4.2.0] – 2025-10-31
Added
- GUI reorganized with tabs.
- New log tab, listing API calls made in the last days.
- Added some tests to check email.
- Constant
WPVULNERABILITY_LOG_RETENTION_DAYSto enforce log rotation fromwp-config.php. - WP-CLI command to configure log retention from the terminal.
- Automated pruning of stored logs based on the configured retention window.
Updated
- New logo and assets.
- PHP syntax to avoid errors.
- Access level control in all the options.
- Uninstall deletes everything.
- POT (translations) file.
- Software versions detection.
- Documentation improvements.
- Improved the content for Slack and Microsoft Teams notifications (in a more old-fashion way).
- Fine-tuned settings labels to reflect enforced log retention values when the constant is present.
Fixed
- Mail unsubscription.
- Mail sending failed.
- Enforced the cache (a lot).
- Core versions (beta and RC) with invalid format.
- Normalize stored notification preferences to avoid stale values after upgrades.
Compatibility
- WordPress: 4.7 – 6.9
- PHP: 5.6 – 8.4
- WP-CLI: 2.3.0 – 2.11.0
Tests
- PHP Coding Standards: 3.13.4
- WordPress Coding Standards: 3.2.0
- Plugin Check (PCP): 1.6.0
- SonarCloud Code Review
- Amplify Code Check
Previous versions
If you want to see the full changelog, visit the changelog.txt file.