-
Notifications
You must be signed in to change notification settings - Fork 8.1k
Add AllowInsecureRedirect switch to Web cmdlets #18546
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Add AllowInsecureRedirect switch to Web cmdlets #18546
Conversation
AllowInsecureRedirect
Lines 1045 to 1049 in f5eede6
This says it is in GetResponse(). |
|
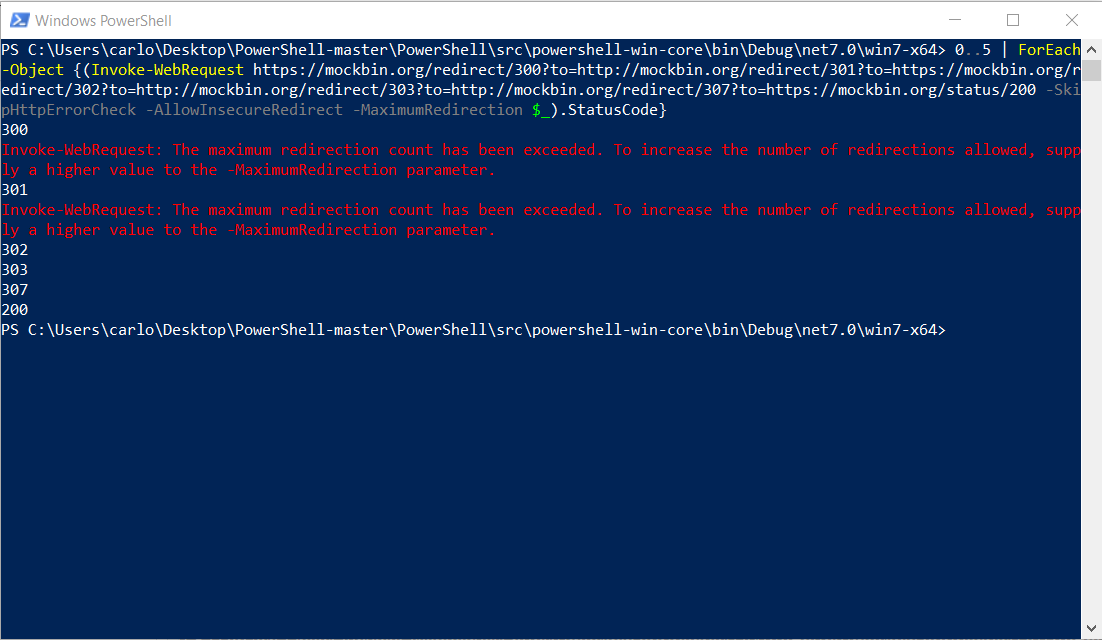
-AllowInsecureRedirect should now work with -MaximumRedirect. 0..5 | ForEach-Object {Invoke-WebRequest https://mockbin.org/redirect/300?to=http://mockbin.org/redirect/301?to=https://mockbin.org/redirect/302?to=http://mockbin.org/redirect/303?to=http://mockbin.org/redirect/307?to=https://mockbin.org/status/200 -SkipHttpErrorCheck -AllowInsecureRedirect -MaximumRedirection $_}
0..5 | ForEach-Object {Invoke-RestMethod https://mockbin.org/redirect/300?to=http://mockbin.org/redirect/301?to=https://mockbin.org/redirect/302?to=http://mockbin.org/redirect/303?to=http://mockbin.org/redirect/307?to=https://mockbin.org/status/200 -SkipHttpErrorCheck -AllowInsecureRedirect -MaximumRedirection $_}
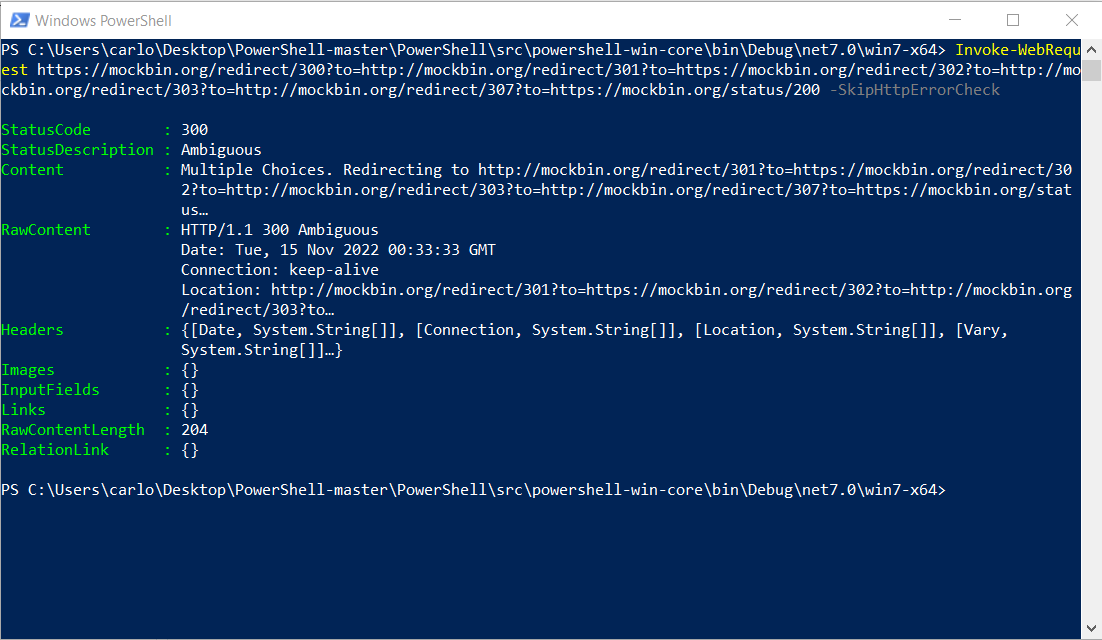
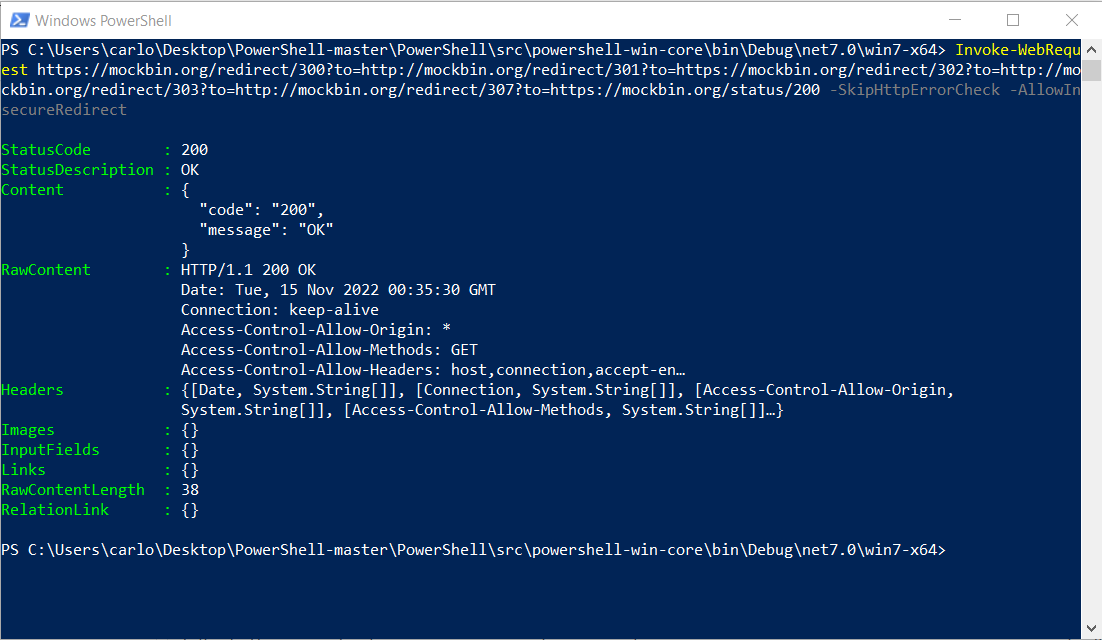
Invoke-WebRequest https://mockbin.org/redirect/300?to=http://mockbin.org/redirect/301?to=https://mockbin.org/redirect/302?to=http://mockbin.org/redirect/303?to=http://mockbin.org/redirect/307?to=https://mockbin.org/status/200 -SkipHttpErrorCheck -AllowInsecureRedirect
Invoke-WebRequest https://mockbin.org/redirect/300?to=http://mockbin.org/redirect/301?to=https://mockbin.org/redirect/302?to=http://mockbin.org/redirect/303?to=http://mockbin.org/redirect/307?to=https://mockbin.org/status/200 -SkipHttpErrorCheckI still have to remove some commented code. |
Invoke-WebRequest https://mockbin.org/redirect/300?to=http://mockbin.org/redirect/301?to=https://mockbin.org/redirect/302?to=http://mockbin.org/redirect/303?to=http://mockbin.org/redirect/307?to=https://mockbin.org/status/200 -SkipHttpErrorCheckInvoke-WebRequest https://mockbin.org/redirect/300?to=http://mockbin.org/redirect/301?to=https://mockbin.org/redirect/302?to=http://mockbin.org/redirect/303?to=http://mockbin.org/redirect/307?to=https://mockbin.org/status/200 -SkipHttpErrorCheck -AllowInsecureRedirect0..5 | ForEach-Object {(Invoke-WebRequest https://mockbin.org/redirect/300?to=http://mockbin.org/redirect/301?to=https://mockbin.org/redirect/302?to=http://mockbin.org/redirect/303?to=http://mockbin.org/redirect/307?to=https://mockbin.org/status/200 -SkipHttpErrorCheck -AllowInsecureRedirect -MaximumRedirection $_).StatusCode}Some inconsistent behaviours (increase redirects errors, status code 308) are fixed by PR #18536. |
|
LGTM. |
|
@PaulHigin please review, thanks! |
|
This pull request has been automatically marked as Review Needed because it has been there has not been any activity for 7 days. |
|
Is something blocking this PR? |
Yes, holydays :-) |
|
This pull request has been automatically marked as Review Needed because it has been there has not been any activity for 7 days. |
|
I think that after this PR is merged I can work on fixing #14531, it should be similar. |
|
This PR has Quantification details
Why proper sizing of changes matters
Optimal pull request sizes drive a better predictable PR flow as they strike a
What can I do to optimize my changes
How to interpret the change counts in git diff output
Was this comment helpful? 👍 :ok_hand: :thumbsdown: (Email) |
|
@please open new issue in Docs repository and add reference in the PR description. |
|
|
🎉 Handy links: |

PR Summary
WebCmdlets add -AllowInsecureRedirect switch to enable HTTPS to HTTP redirect.
System.Net.Http.HttpClient disables insecure redirects, this PR bypasses the problem, unfortunately at the moment I can't find a way to make it honor the -MaximumRedirects flag, so I have disabled using both of them toghether.
I'm eager to receive your feedback on this feature and some input on how to fix and re-enable the -MaximumRedirect flag.
I'm going to add some tests to show what works and what doesn't work yet.
PR Context
Fixes #2896 and #18541
PR Checklist
.h,.cpp,.cs,.ps1and.psm1files have the correct copyright headerWIP:or[ WIP ]to the beginning of the title (theWIPbot will keep its status check atPendingwhile the prefix is present) and remove the prefix when the PR is ready.-AllowInsecureRedirectparameter MicrosoftDocs/PowerShell-Docs#9689(which runs in a different PS Host).